
- •QoS Overview
- •“Do I Know This Already?” Quiz
- •QoS: Tuning Bandwidth, Delay, Jitter, and Loss Questions
- •Foundation Topics
- •QoS: Tuning Bandwidth, Delay, Jitter, and Loss
- •Bandwidth
- •The clock rate Command Versus the bandwidth Command
- •QoS Tools That Affect Bandwidth
- •Delay
- •Serialization Delay
- •Propagation Delay
- •Queuing Delay
- •Forwarding Delay
- •Shaping Delay
- •Network Delay
- •Delay Summary
- •QoS Tools That Affect Delay
- •Jitter
- •QoS Tools That Affect Jitter
- •Loss
- •QoS Tools That Affect Loss
- •Summary: QoS Characteristics: Bandwidth, Delay, Jitter, and Loss
- •Voice Basics
- •Voice Bandwidth Considerations
- •Voice Delay Considerations
- •Voice Jitter Considerations
- •Voice Loss Considerations
- •Video Basics
- •Video Bandwidth Considerations
- •Video Delay Considerations
- •Video Jitter Considerations
- •Video Loss Considerations
- •Comparing Voice and Video: Summary
- •IP Data Basics
- •Data Bandwidth Considerations
- •Data Delay Considerations
- •Data Jitter Considerations
- •Data Loss Considerations
- •Comparing Voice, Video, and Data: Summary
- •Foundation Summary
- •QoS Tools and Architectures
- •“Do I Know This Already?” Quiz
- •QoS Tools Questions
- •Differentiated Services Questions
- •Integrated Services Questions
- •Foundation Topics
- •Introduction to IOS QoS Tools
- •Queuing
- •Queuing Tools
- •Shaping and Policing
- •Shaping and Policing Tools
- •Congestion Avoidance
- •Congestion-Avoidance Tools
- •Call Admission Control and RSVP
- •CAC Tools
- •Management Tools
- •Summary
- •The Good-Old Common Sense QoS Model
- •GOCS Flow-Based QoS
- •GOCS Class-Based QoS
- •The Differentiated Services QoS Model
- •DiffServ Per-Hop Behaviors
- •The Class Selector PHB and DSCP Values
- •The Assured Forwarding PHB and DSCP Values
- •The Expedited Forwarding PHB and DSCP Values
- •The Integrated Services QoS Model
- •Foundation Summary
- •“Do I Know This Already?” Quiz Questions
- •CAR, PBR, and CB Marking Questions
- •Foundation Topics
- •Marking
- •IP Header QoS Fields: Precedence and DSCP
- •LAN Class of Service (CoS)
- •Other Marking Fields
- •Summary of Marking Fields
- •Class-Based Marking (CB Marking)
- •Network-Based Application Recognition (NBAR)
- •CB Marking show Commands
- •CB Marking Summary
- •Committed Access Rate (CAR)
- •CAR Marking Summary
- •Policy-Based Routing (PBR)
- •PBR Marking Summary
- •VoIP Dial Peer
- •VoIP Dial-Peer Summary
- •Foundation Summary
- •Congestion Management
- •“Do I Know This Already?” Quiz
- •Queuing Concepts Questions
- •WFQ and IP RTP Priority Questions
- •CBWFQ and LLQ Questions
- •Comparing Queuing Options Questions
- •Foundation Topics
- •Queuing Concepts
- •Output Queues, TX Rings, and TX Queues
- •Queuing on Interfaces Versus Subinterfaces and Virtual Circuits (VCs)
- •Summary of Queuing Concepts
- •Queuing Tools
- •FIFO Queuing
- •Priority Queuing
- •Custom Queuing
- •Weighted Fair Queuing (WFQ)
- •WFQ Scheduler: The Net Effect
- •WFQ Scheduling: The Process
- •WFQ Drop Policy, Number of Queues, and Queue Lengths
- •WFQ Summary
- •Class-Based WFQ (CBWFQ)
- •CBWFQ Summary
- •Low Latency Queuing (LLQ)
- •LLQ with More Than One Priority Queue
- •IP RTP Priority
- •Summary of Queuing Tool Features
- •Foundation Summary
- •Conceptual Questions
- •Priority Queuing and Custom Queuing
- •CBWFQ, LLQ, IP RTP Priority
- •Comparing Queuing Tool Options
- •“Do I Know This Already?” Quiz
- •Shaping and Policing Concepts Questions
- •Policing with CAR and CB Policer Questions
- •Shaping with FRTS, GTS, DTS, and CB Shaping
- •Foundation Topics
- •When and Where to Use Shaping and Policing
- •How Shaping Works
- •Where to Shape: Interfaces, Subinterfaces, and VCs
- •How Policing Works
- •CAR Internals
- •CB Policing Internals
- •Policing, but Not Discarding
- •Foundation Summary
- •Shaping and Policing Concepts
- •“Do I Know This Already?” Quiz
- •Congestion-Avoidance Concepts and RED Questions
- •WRED Questions
- •FRED Questions
- •Foundation Topics
- •TCP and UDP Reactions to Packet Loss
- •Tail Drop, Global Synchronization, and TCP Starvation
- •Random Early Detection (RED)
- •Weighted RED (WRED)
- •How WRED Weights Packets
- •WRED and Queuing
- •WRED Summary
- •Flow-Based WRED (FRED)
- •Foundation Summary
- •Congestion-Avoidance Concepts and Random Early Detection (RED)
- •Weighted RED (WRED)
- •Flow-Based WRED (FRED)
- •“Do I Know This Already?” Quiz
- •Compression Questions
- •Link Fragmentation and Interleave Questions
- •Foundation Topics
- •Payload and Header Compression
- •Payload Compression
- •Header Compression
- •Link Fragmentation and Interleaving
- •Multilink PPP LFI
- •Maximum Serialization Delay and Optimum Fragment Sizes
- •Frame Relay LFI Using FRF.12
- •Choosing Fragment Sizes for Frame Relay
- •Fragmentation with More Than One VC on a Single Access Link
- •FRF.11-C and FRF.12 Comparison
- •Foundation Summary
- •Compression Tools
- •LFI Tools
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Call Admission Control Overview
- •Call Rerouting Alternatives
- •Bandwidth Engineering
- •CAC Mechanisms
- •CAC Mechanism Evaluation Criteria
- •Local Voice CAC
- •Physical DS0 Limitation
- •Max-Connections
- •Voice over Frame Relay—Voice Bandwidth
- •Trunk Conditioning
- •Local Voice Busyout
- •Measurement-Based Voice CAC
- •Service Assurance Agents
- •SAA Probes Versus Pings
- •SAA Service
- •Calculated Planning Impairment Factor
- •Advanced Voice Busyout
- •PSTN Fallback
- •SAA Probes Used for PSTN Fallback
- •IP Destination Caching
- •SAA Probe Format
- •PSTN Fallback Scalability
- •PSTN Fallback Summary
- •Resource-Based CAC
- •Resource Availability Indication
- •Gateway Calculation of Resources
- •RAI in Service Provider Networks
- •RAI in Enterprise Networks
- •RAI Operation
- •RAI Platform Support
- •Cisco CallManager Resource-Based CAC
- •Location-Based CAC Operation
- •Locations and Regions
- •Calculation of Resources
- •Automatic Alternate Routing
- •Location-Based CAC Summary
- •Gatekeeper Zone Bandwidth
- •Gatekeeper Zone Bandwidth Operation
- •Single-Zone Topology
- •Multizone Topology
- •Zone-per-Gateway Design
- •Gatekeeper in CallManager Networks
- •Zone Bandwidth Calculation
- •Gatekeeper Zone Bandwidth Summary
- •Integrated Services / Resource Reservation Protocol
- •RSVP Levels of Service
- •RSVP Operation
- •RSVP/H.323 Synchronization
- •Bandwidth per Codec
- •Subnet Bandwidth Management
- •Monitoring and Troubleshooting RSVP
- •RSVP CAC Summary
- •Foundation Summary
- •Call Admission Control Concepts
- •Local-Based CAC
- •Measurement-Based CAC
- •Resources-Based CAC
- •“Do I Know This Already?” Quiz
- •QoS Management Tools Questions
- •QoS Design Questions
- •Foundation Topics
- •QoS Management Tools
- •QoS Device Manager
- •QoS Policy Manager
- •Service Assurance Agent
- •Internetwork Performance Monitor
- •Service Management Solution
- •QoS Management Tool Summary
- •QoS Design for the Cisco QoS Exams
- •Four-Step QoS Design Process
- •Step 1: Determine Customer Priorities/QoS Policy
- •Step 2: Characterize the Network
- •Step 3: Implement the Policy
- •Step 4: Monitor the Network
- •QoS Design Guidelines for Voice and Video
- •Voice and Video: Bandwidth, Delay, Jitter, and Loss Requirements
- •Voice and Video QoS Design Recommendations
- •Foundation Summary
- •QoS Management
- •QoS Design
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •The Need for QoS on the LAN
- •Layer 2 Queues
- •Drop Thresholds
- •Trust Boundries
- •Cisco Catalyst Switch QoS Features
- •Catalyst 6500 QoS Features
- •Supervisor and Switching Engine
- •Policy Feature Card
- •Ethernet Interfaces
- •QoS Flow on the Catalyst 6500
- •Ingress Queue Scheduling
- •Layer 2 Switching Engine QoS Frame Flow
- •Layer 3 Switching Engine QoS Packet Flow
- •Egress Queue Scheduling
- •Catalyst 6500 QoS Summary
- •Cisco Catalyst 4500/4000 QoS Features
- •Supervisor Engine I and II
- •Supervisor Engine III and IV
- •Cisco Catalyst 3550 QoS Features
- •Cisco Catalyst 3524 QoS Features
- •CoS-to-Egress Queue Mapping for the Catalyst OS Switch
- •Layer-2-to-Layer 3 Mapping
- •Connecting a Catalyst OS Switch to WAN Segments
- •Displaying QoS Settings for the Catalyst OS Switch
- •Enabling QoS for the Catalyst IOS Switch
- •Enabling Priority Queuing for the Catalyst IOS Switch
- •CoS-to-Egress Queue Mapping for the Catalyst IOS Switch
- •Layer 2-to-Layer 3 Mapping
- •Connecting a Catalyst IOS Switch to Distribution Switches or WAN Segments
- •Displaying QoS Settings for the Catalyst IOS Switch
- •Foundation Summary
- •LAN QoS Concepts
- •Catalyst 6500 Series of Switches
- •Catalyst 4500/4000 Series of Switches
- •Catalyst 3550/3524 Series of Switches
- •QoS: Tuning Bandwidth, Delay, Jitter, and Loss
- •QoS Tools
- •Differentiated Services
- •Integrated Services
- •CAR, PBR, and CB Marking
- •Queuing Concepts
- •WFQ and IP RTP Priority
- •CBWFQ and LLQ
- •Comparing Queuing Options
- •Conceptual Questions
- •Priority Queuing and Custom Queuing
- •CBWFQ, LLQ, IP RTP Priority
- •Comparing Queuing Tool Options
- •Shaping and Policing Concepts
- •Policing with CAR and CB Policer
- •Shaping with FRTS, GTS, DTS, and CB Shaping
- •Shaping and Policing Concepts
- •Congestion-Avoidance Concepts and RED
- •WRED
- •FRED
- •Congestion-Avoidance Concepts and Random Early Detection (RED)
- •Weighted RED (WRED)
- •Flow-Based WRED (FRED)
- •Compression
- •Link Fragmentation and Interleave
- •Compression Tools
- •LFI Tools
- •Call Admission Control Concepts
- •Local-Based CAC
- •Measurement-Based CAC
- •Resources-Based CAC
- •QoS Management Tools
- •QoS Design
- •QoS Management
- •QoS Design
- •LAN QoS Concepts
- •Catalyst 6500 Series of Switches
- •Catalyst 4500/4000 Series of Switches
- •Catalyst 3550/3524 Series of Switches
- •Foundation Topics
- •QPPB Route Marking: Step 1
- •QPPB Per-Packet Marking: Step 2
- •QPPB: The Hidden Details
- •QPPB Summary
- •Flow-Based dWFQ
- •ToS-Based dWFQ
- •Distributed QoS Group–Based WFQ
- •Summary: dWFQ Options
Foundation Summary 405
Foundation Summary
The “Foundation Summary” is a collection of tables and figures that provide a convenient review of many key concepts in this chapter. For those of you already comfortable with the topics in this chapter, this summary could help you recall a few details. For those of you who just read this chapter, this review should help solidify some key facts. For any of you doing your final prep before the exam, these tables and figures are a convenient way to review the day before the exam.
ISPs make the business choice of whether to police, and how aggressively to police. The options reduce to the following three basic options:
•Do not police. To support the traffic, build the network to support the traffic as if all customers will send and receive data at the clock rate of the access link. From a sales perspective, close deals by claiming that no policing will be done, but encourage customers who exceed their contracts to pay for more bandwidth.
•Police at the contracted rate. To support these traffic levels, the network only needs to be built to support the collective contracted rates, although the core would be overbuilt to support new customers. From a sales perspective, encourage customers that are beginning to exceed their contracts to upgrade, and give incentives.
•Police somewhere in between the contracted rate and the access-link clock rate. For instance, ISP1 might police PB Tents at 5 Mbps, when the contract reads 2 Mbps. The network can be built to support the collective policed rates. The sales team can encourage customers to buy a larger contracted rate when they consistently exceed the contracted rate, but keep customer satisfaction higher by pointing out their generosity by only policing at rates much higher than the contracted rates.
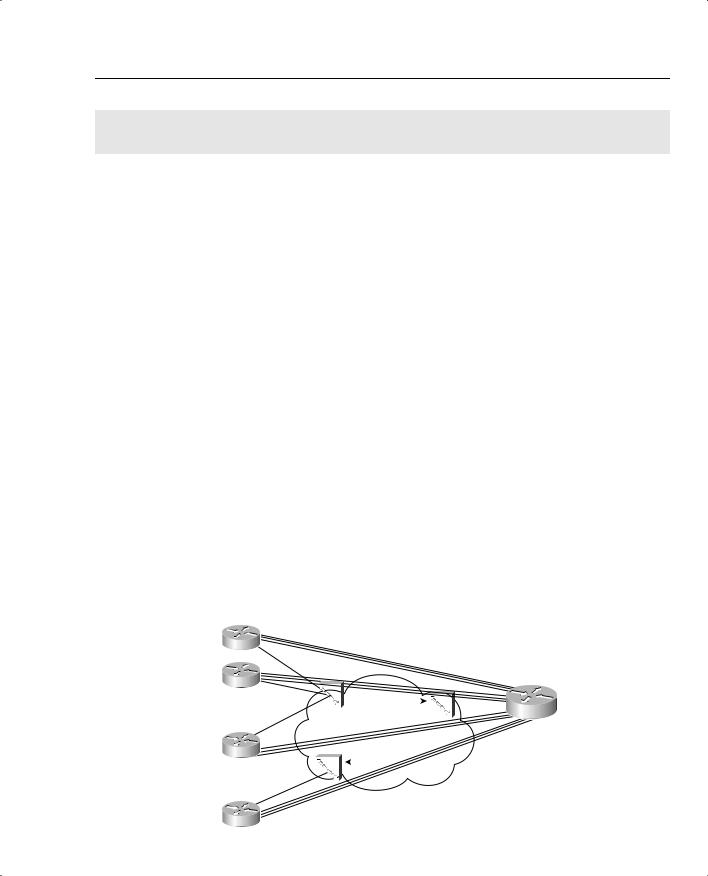
Figure 5-24 points out two cases of egress blocking, using a Frame Relay network as an example.
Figure 5-24 PB Tents Network, Egress Blocking
|
|
|
|
|
|
All VCs 64 kbps CIR |
|
|
|
||||
|
|
|
|
|
|
Cumulative Traffic Can Be |
|
|
|
||||
R1 |
|
|
|
|
24 * 128 kbps = 3.0 Mbps |
|
|
|
|||||
|
|
|
|
|
|
|
|
|
|
|
|
||
|
AR 128 kbps |
|
|
|
|
|
|
|
|
|
|
||
R2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
AR 128 kbps |
|
|
|
|
|
|
|
|
|
|
|
Main |
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
AR 128 kbps |
FRS1 |
|
|
FRS2 |
|
|
AR 1.5 Mbps |
||||||
|
|
|
|
|
|
||||||||
|
|
|
|||||||||||
R3 |
|
|
FRS3 |
|
|
|
|||||||
.. |
AR 128 kbps |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Speed Mismatch Between Main (1.5 Mbps) |
|||||||
R24 |
|
|
|
|
and R24 Access Rate (128 kbps) Causes Blocking |
||||||||

406 Chapter 5: Traffic Policing and Shaping
Table 5-27 summarizes some of the key points about when and where you should consider using policing and shaping.
Table 5-27 Policing and Shaping: When to Use Them, and Where
Topic |
Rationale |
|
|
Why police? |
If a neighboring network can send more traffic than the traffic contract specifies, |
|
policing can be used to enforce the contract, protecting the network from being |
|
overrun with too much traffic. |
|
|
Where to police? |
Typically, policing is performed as packets enter the first device in a network. |
|
Egress policing is also supported, although it is less typical. |
|
|
Why shape? |
The first of two reasons for shaping is when the neighboring network is policing. |
|
Instead of waiting for the neighboring policer to discard traffic, a shaper can |
|
instead delay traffic so that it will not be dropped. |
|
The second reason has to do with the effects of egress blocking. By shaping, |
|
egress blocking can be avoided, or minimized, essentially moving the queues |
|
from inside the service provider cloud, and back into the enterprise routers. By |
|
doing so, the router queuing tools can selectively give better QoS performance to |
|
particular types of traffic. |
|
|
Where to shape? |
Shaping is always an egress function. Typically, shaping is performed on packets |
|
exiting a router, going into another network. This may be the edge between a |
|
router and a multiaccess WAN, or possibly just a link to an ISP. |
|
|
Traffic shaping implements this basic logic by defining a measurement interval, and a number of bits that can be sent in that interval, so that the overall shaped rate is not exceeded. Table 5-28 lists some related definitions.
Table 5-28 Shaping Terminology
Term |
Definition |
|
|
Tc |
Time interval, measured in milliseconds, over which the committed burst (Bc) can be |
|
sent. With many shaping tools, Tc = Bc/CIR. |
|
|
Bc |
Committed burst size, measured in bits. This is the amount of traffic that can be sent |
|
over the interval Tc. Typically also defined in the traffic contract. |
|
|
CIR |
Committed information rate, in bits per second, defines the rate defined in the traffic |
|
contract. |
|
|
Shaped Rate |
The rate, in bits per second, to which a particular configuration wants to shape the |
|
traffic. In some cases, the shaped rate is set to the same value as CIR; in others, |
|
the shaped rate is set to a larger value, with the hope of sending more traffic through |
|
the network. |
|
|
Be |
Excess burst size, in bits. This is the number of bits beyond Bc that can be sent after a |
|
period of inactivity. |
|
|
Foundation Summary 407
The formulas IOS uses to calculate Tc when you configure both the shaping rate and the Bc are as follows:
Tc = Bc/CIR
Or
Tc = Bc/Shaped rate
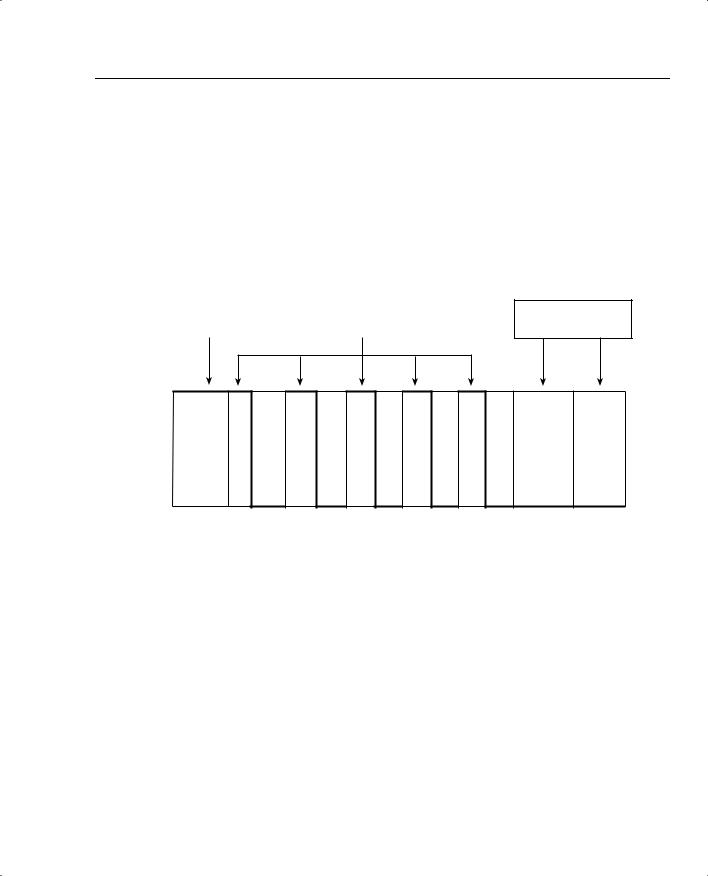
Figure 5-25 lists the overall process used by shaping, in terms of Tc, Bc, and Be.
Figure 5-25 Bc and Be, After a Period of Inactivity (Both Buckets Full)
|
|
Bc = 8000, Be = 0 |
|
|
|
Send 16,000 bits in each |
|
Bc = 8000, Be = 8000 |
|||
|
interval, until Be can |
||
Send 16,000 bits in first interval |
|
||
|
accumulate |
||
|
|
Period of inactivity — Be re-fills in 1 single totally dormant Tc
Sending Rate
128 kbps
0 kbps
0 125 250 375 500 625 750 875 1000 Time
(Ms)
In summary, most QoS policies call for shaping on each VC. The number of VCs, and how they are configured, dictates where the shaping tool needs to be enabled. Table 5-29 summarizes the options.
Table 5-29 Options of How to Enable Shaping for per-VC Shaping
Location |
Requirements for Shaping per VC |
|
|
No VCs |
Shape on the main interface. Shaping occurs for all |
|
traffic on interface. |
|
|
Physical interface, 1 VC, no subinterfaces |
Shaping shapes the individual VC associated with this |
|
interface. Shaping is enabled on the physical interface. |
|
|
Physical interface, 1 VC, 1 subinterface |
Shaping shapes the individual VC associated with this |
|
interface. Shaping can be enabled on the physical |
|
interface, the subinterface, or the VC (DLCI). |
|
|
continues
408 Chapter 5: Traffic Policing and Shaping
Table 5-29 Options of How to Enable Shaping for per-VC Shaping (Continued)
Location |
Requirements for Shaping per VC |
|
|
Multiple VCs on 1 interface, point-to-point |
Shaping can be enabled on the subinterface, or per |
subinterfaces only |
DLCI. Both methods work identically. |
|
|
Multiple VCs on 1 interface, some |
Must enable shaping on each DLCI to shape per VC. |
multipoint subinterfaces with > 1 VC per |
|
subinterface |
|
|
|
Table 5-30 lists the traffic-shaping tools, and the queuing tools supported by each for the shaping queues.
Table 5-30 Options for Queuing in Traffic-Shaping Tools
Shaping Tool |
Queuing Tools Supported for the Shaping Queue(s) |
|
|
GTS |
WFQ |
|
|
CB shaping |
FIFO, WFQ, CBWFQ, LLQ |
|
|
DTS |
FIFO, WFQ, CBWFQ, LLQ |
|
|
FRTS |
FIFO, WFQ, CBWFQ, LLQ, PQ, CQ, |
|
|
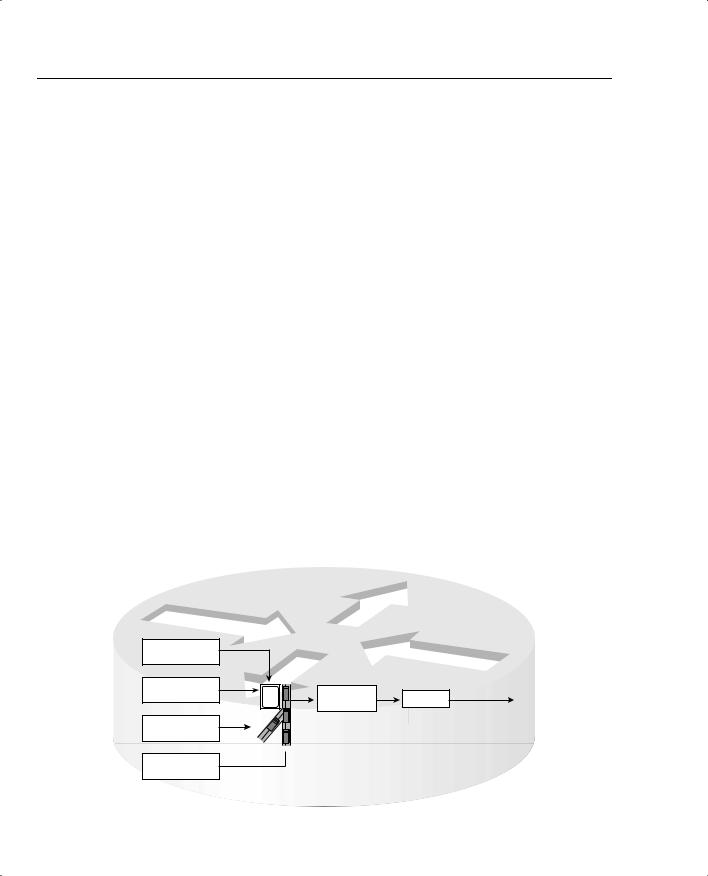
When a shaper uses a queuing tool, instead of having a single shaping queue, multiple shaping queues exist. If FRTS were configured to use PQ, for example, up to four queues could be created for shaping. Figure 5-26 shows the basic idea, with shaping enabled on the physical interface, FIFO Queuing on the physical interface, and PQ configured for the shaping queue.
Figure 5-26 FIFO Queuing for the Physical Interface, Plus PQ for the Shaping Queue
Shaping Queues for a Single VC
PQ High –
Shaping Queue
PQ Medium –
Shaping Queue
PQ Normal –
Shaping Queue
|
Bit Rate |
Interface |
|
|
Limit |
TX Ring |
|
|
x bps |
Output Queue |
|
|
AR 128 kbps |
||
|
Down |
|
|
Slow |
|
|
|
|
|
|
Shape to  PQ Low – 96 kbps Shaping Queue
PQ Low – 96 kbps Shaping Queue
Foundation Summary 409
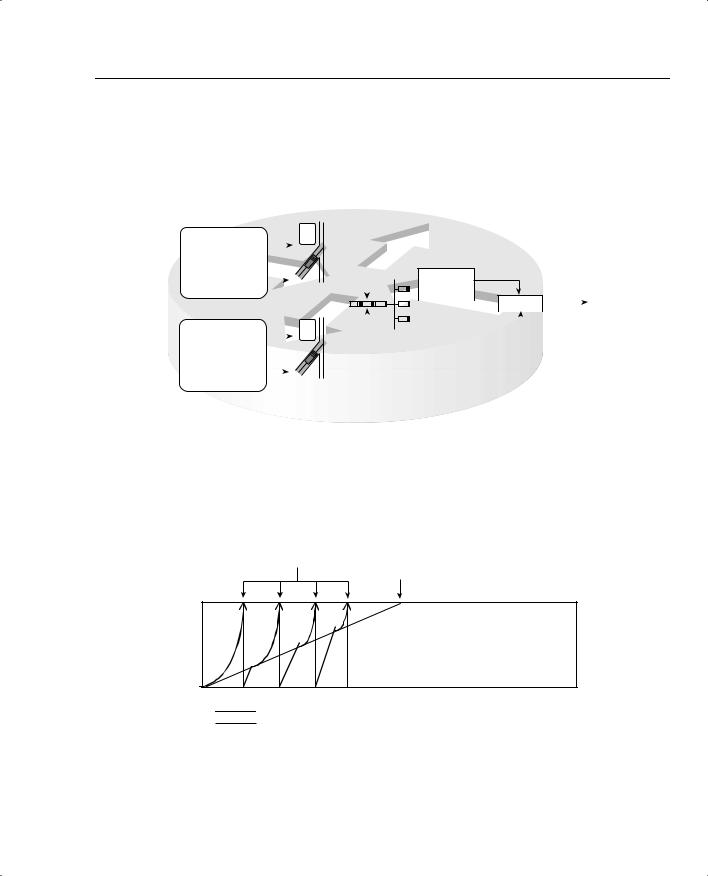
Many QoS designs call for shaping per VC. For the same router, with two 64-kbps CIR VCs (each configured on a separate point-to-point subinterface) shaping queues are created for each subinterface, with the familiar output queues as well. Figure 5-27 depicts the overall idea.
Figure 5-27 Fancy Queuing for the Physical Interface as well as for Two Sets of Shaping Queues
Shaping Queues for Subinterface 1
|
|
|
|
Bit Rate |
|
|
|
|
|
|
|
|
|
|
|
|
Limit |
|
|
|
|
|
|
|
|
|
Subint #1 |
|
|
x bps |
|
|
|
|
|
|
|
|
|
Shaping Queue1 |
|
Slow |
Down |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
Subint #1 |
|
|
|
|
|
|
|
|
|
|
|
|
Shaping Queue2 |
|
Shape |
to |
|
|
|
|
||||
|
|
|
|
|||||||||
|
|
|
96 kbps |
|
|
|
||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
Shaping Queues for Subinterface 2 |
|
|
|
|||||||||
|
|
|
|
Bit Rate |
|
|
|
|
|
|
|
|
|
|
|
|
Limit |
|
|
|
|
|
|
|
|
|
Subint #2 |
|
|
|
|
|||||||
|
Shaping Queue1 |
|
|
x bps |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Slow |
Down |
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||||
|
|
|
|
|
|
|
|
|
|
|||
|
Subint #2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
Shaping Queue2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
Shape to |
|
|
||||||||
|
|
|
|
|
||||||||
|
|
|
|
|||||||||
|
|
|
64 kbps |
|
|
|||||||
Interface
Output
Queue#1
|
|
TX Ring |
|
|
||
|
|
AR 128 kbps |
||||
Interface |
|
|
|
|
||
|
|
|||||
Output |
|
|
|
|
|
|
|
|
|
|
|
|
|
Queue#2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
One goal of policing when Be is being used is to discard some packets, hoping to avoid the point where all packets are discarded. Figure 5-28 shows the general idea of how policers accomplish that goal, using Da and Dc values.
Figure 5-28 Actual Debt and Compounded Debt with Policing
Point at Which Dc Caused Single
Packet Drop When Dc > Be Point at Which Be Has Been
Consumed; All Packets Dropped
Be
Dc |
Da |
|
0
Dc
Da
Tables 5-31 and 5-32 list the configuration and show commands pertinent to GTS.

410 Chapter 5: Traffic Policing and Shaping
Table 5-31 Command Reference for Generic Traffic Shaping
|
Command |
Mode and Function |
|
|
|
|
traffic-shape rate bit-rate [burst-size |
Interface configuration mode; enables GTS for a shaped |
|
[excess-burst-size]] |
rate, with optional Bc and Be settings, in bits |
|
|
|
|
traffic-shape group access-list bit-rate |
Interface configuration mode; enables GTS for a shaped |
|
[burst-size [excess-burst-size]] |
rate, only for traffic permitted by the referenced ACL, with |
|
|
optional Bc and Be settings, in bits |
|
|
|
|
traffic-shape adaptive bit-rate |
Interface configuration mode; enables adaptive shaping, |
|
|
and sets the minimum shaped rate |
|
|
|
|
traffic-shape fecn-adapt |
Interface configuration mode; enables the reflection of |
|
|
BECN signals upon receipt of an FECN |
|
|
|
Table 5-32 Exec Command Reference for Generic Traffic Shaping |
||
|
|
|
|
Command |
Function |
|
|
|
|
show traffic-shape [interface-type |
Lists information about the configuration details |
|
interface-number] |
|
|
|
|
|
show traffic-shape queue [interface- |
Lists statistics about the queuing tool used on the shaping |
|
number [dlci dlci-number]] |
queue |
|
|
|
|
show traffic-shape statistics [interface- |
Lists statistics about shaping operation |
|
type interface-number] |
|
|
|
|
Tables 5-33 and 5-34 list the configuration and show commands pertinent to CB shaping.
Table 5-33 Command Reference for Class-Based Shaping
Command |
Mode and Function |
|
|
shape [average | peak] mean-rate [[burst- |
Policy-map class configuration mode; enables shaping |
size] [excess-burst-size]] |
for the class, setting the shaping rate, and optionally |
|
Bc and Be. The average option causes shaping as nor- |
|
mal; the peak option causes Bc + Be to be sent per Tc. |
|
|
Shape adaptive min-rate |
Policy-map class configuration mode; enables the |
|
minimum rate for adaptive shaping. The maximum |
|
rate is configured with the shape average or shape |
|
peak command. |
|
|
Shape fecn-adapt |
Policy-map class configuration mode; enables |
|
reflection of BECN signals upon receipt of an FECN. |
|
|
service-policy {input | output} policy-map- |
Interface or subinterface configuration mode; enables |
name |
CB shaping on the interface. |
|
|

Foundation Summary 411
Table 5-33 Command Reference for Class-Based Shaping (Continued)
Command |
Mode and Function |
|
|
class-map class-map-name |
Global config; names a class map, where classification |
|
options are configured. |
|
|
Match . . . |
class-map subcommand; defines specific classification |
|
parameters. |
|
|
match access-group {access-group | name |
class-map subcommand; references either numbered |
access-group-name} |
or named ACL. |
|
|
match source-address mac address |
class-map subcommand; references the source MAC |
|
address that forwarded the packet to this router, |
|
typically the previous-hop router. |
|
|
match ip precedence ip-precedence-value |
class-map subcommand; references one or more IP |
[ip-precedence-value ip-precedence-value ip- |
precedence values. A packet with any of the listed |
precedence-value] |
values matches. |
|
|
match mpls experimental number |
class-map subcommand; references MPLS |
|
Experimental bits. |
|
|
match cos cos-value [cos-value cos-value |
class-map subcommand; references one or more class |
cos-value] |
of service (CoS) values. A packet with any of the listed |
|
values matches. |
|
|
match destination-address mac address |
class-map subcommand; references the destination |
|
MAC address of the device to which the packet will be |
|
forwarded next. |
|
|
match input-interface interface-name |
class-map subcommand; matches based on the inter- |
|
face in which the packet was received. |
|
|
match ip dscp ip-dscp-value [ip-dscp-value |
class-map subcommand; references one or more IP |
ip-dscp-value ip-dscp-value ip-dscp-value ip- |
DSCP values. A packet with any of the listed values |
dscp-value ip-dscp-value ip-dscp-value] |
matches. |
|
|
match ip rtp starting-port-number port- |
class-map subcommand; references a range of UDP |
range |
ports, only matching the even numbered ports, which |
|
carry voice payload. |
|
|
match qos-group qos-group-value |
class-map subcommand; matches based on QoS |
|
group. |
|
|
match protocol protocol-name |
class-map subcommand; matches based on NBAR- |
|
defined protocol types. |
|
|
match protocol citrix [app application- |
class-map subcommand; matches based on NBAR- |
name-string]. |
defined Citrix application types. |
|
|
match protocol http [url url-string | host |
class-map subcommand; matches based on NBAR- |
hostname-string | mime MIME-type] |
discovered details inside the host name or URL string. |
|
|
continues

412 Chapter 5: Traffic Policing and Shaping
Table 5-33 Command Reference for Class-Based Shaping (Continued)
|
Command |
Mode and Function |
|
|
|
|
match any |
class-map subcommand; matches all packets. |
|
|
|
|
policy-map policy-map-name |
Global config; names a policy, which is a set of actions |
|
|
to perform. |
|
|
|
|
class name |
policy-map subcommand; identifies which packets on |
|
|
which to perform some action by referring to the |
|
|
classification logic in a class map. |
|
|
|
Table 5-34 Exec Command Reference for Class-Based Shaping |
||
|
|
|
|
Command |
Function |
|
|
|
|
show policy-map policy-map-name |
Lists configuration information about all MQC-based |
|
|
QoS tools |
|
|
|
|
show policy-map interface-spec [input | |
Lists statistical information about the behavior of all |
|
output] [class class-name] |
MQC-based QoS tools |
|
|
|
Tables 5-35 and 5-36 list the configuration and show commands pertinent to FRTS.
Table 5-35 Command Reference for Frame Relay Traffic Shaping
Command |
Mode and Function |
|
|
frame-relay traffic-shaping |
Interface subcommand; enables FRTS on the interface. |
|
|
class name |
Interface DLCI subcommand; enables a specific FRTS |
|
map class for the DLCI. |
|
|
frame-relay class name |
Interface or subinterface command; enables a specific |
|
FRTS map class for the interface or subinterface. |
|
|
map-class frame-relay map-class-name |
Global configuration mode; names a map class, and |
|
places CLI into map-class configuration mode |
|
|
frame-relay priority-group list-number |
Map-class configuration mode; enables PQ for the |
|
shaping queues associated with this map class |
|
|
frame-relay custom-queue-list list-number |
Map-class configuration mode; enables CQ for the |
|
shaping queues associated with this map class |
|
|
frame-relay fair-queue |
Map-class configuration mode; enables WFQ for the |
[congestive_discard_threshold |
shaping queues associated with this map class |
[number_dynamic_conversation_queues |
|
[number_reservable_conversation_queues |
|
[max_buffer_size_for_fair_queues]]]] |
|
|
|

Foundation Summary 413
Table 5-35 Command Reference for Frame Relay Traffic Shaping (Continued)
Command |
Mode and Function |
|
|
service-policy {input | output} policy-map- |
Map-class configuration mode; enables LLQ or |
name |
CBWFQ on the shaping queues associated with the |
|
map class. |
|
|
frame-relay traffic-rate average [peak] |
Map-class configuration mode; sets the shaped rate, |
|
and the EIR*. Bc and Be are calculated from these, |
|
based on Tc of 125ms. |
|
|
frame-relay bc {in | out} bits |
Map-class configuration mode; sets the Bc value. |
|
Alternative configuration option to frame-relay |
|
traffic-rate. |
|
|
frame-relay be {in | out} bits |
Map-class configuration mode; sets the Be value. |
|
Alternative configuration option to frame-relay |
|
traffic-rate. |
|
|
frame-relay cir {in | out} bps |
Map-class configuration mode; sets the CIR value. |
|
Alternative configuration option to frame-relay |
|
traffic-rate. |
|
|
frame-relay adaptive-shaping {becn | |
Map-class configuration mode; enables adaptive |
foresight} |
shaping, specifying either BECN or Foresight for |
|
signaling. |
|
|
frame-relay mincir {in | out} bps |
Map-class configuration mode; sets the minimum CIR |
|
used for adaptive shaping. |
|
|
frame-relay tc milliseconds |
Map-class configuration mode; for 0 CIR VCs, sets the |
|
Tc value. |
|
|
frame-relay qos-autosense |
Interface configuration mode; uses ELMI to automati- |
|
cally discover CIR, Bc, and Be settings for each VC. |
|
|
*EIR = excess information rate
Table 5-36 Exec Command Reference for Frame Relay Traffic Shaping
Command |
Function |
|
|
show frame-relay pvc [interface interface] |
Shows PVC statistics, including shaping statistics |
[dlci] |
|
|
|
show traffic-shape [interface-type interface- |
Shows information about FRTS configuration per VC |
number] |
|
|
|
show traffic-shape queue [interface-number |
Shows information about the queuing tool used with |
[dlci dlci-number]] |
the shaping queue |
|
|
show traffic-shape statistics [interface-type |
Shows traffic-shaping statistics |
interface-number] |
|
|
|
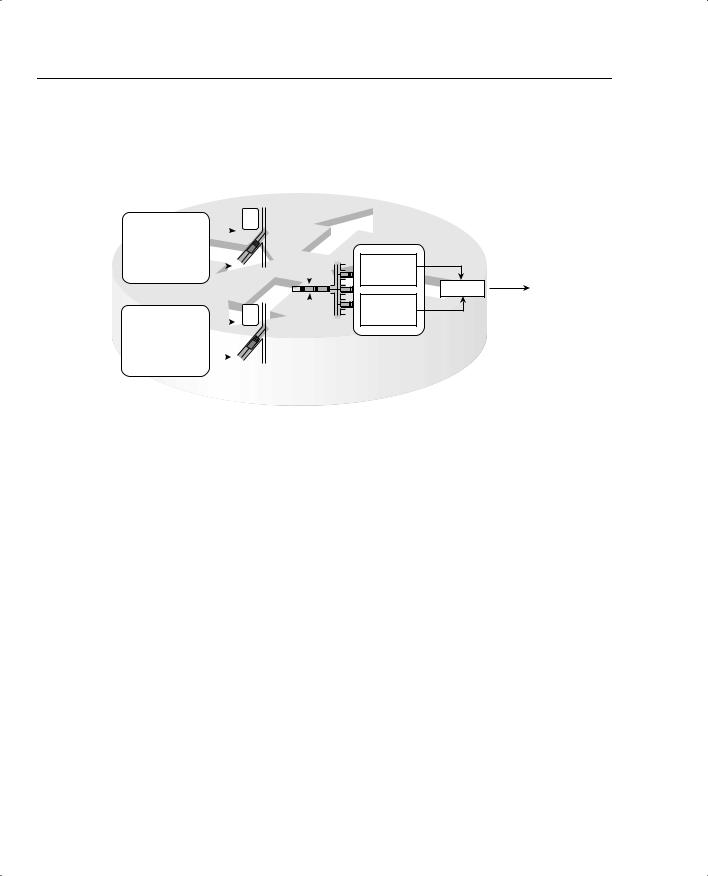
414 Chapter 5: Traffic Policing and Shaping
Frame Relay fragmentation (FRF) can be used with FRTS. Figure 5-29 outlines the basic idea, with FRTS on two subinterfaces.
Figure 5-29 Interaction Between Shaping Queues and Frame Relay Fragmentation Queues
Shaping Queues for Subinterface 1
|
|
|
|
Bit Rate |
|
|
|
|
|
|
|
|
|
Limit |
|
|
|
|
|
|
Subint #1 |
|
|
x bps |
|
|
|
|
|
|
Shaping Queue1 |
|
Slow |
Down |
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
Subint #1 |
|
|
|
|
|
|
|
|
|
Shaping Queue2 |
|
|
|
|
|
|
|
|
|
|
Shape |
to |
|
|
||||
|
|
|
|
96 kbps |
|
|
|||
|
|
|
|
||||||
Shaping Queues for Subinterface 2 |
|
|
|||||||
|
|
|
|
Bit Rate |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
Subint #2 |
|
|
Limit |
|
|
|
|
|
|
Shaping Queue1 |
|
|
x bps |
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
Slow |
Down |
|
|
|
|
|
|
|
|
|
|
|||||
|
|
|
|
|
|
|
|||
|
Subint #2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
Shaping Queue2 |
|
|
|
|
|
|
|
|
|
|
Shape to |
|
|
|||||
|
|
|
|
|
|||||
|
|
|
|
||||||
|
|
|
64 kbps |
|
|
||||
Dual FIFO Interface Queues
Unfragmented
Frames; PQ-
Like Service
TX Ring
AR 128 kbps
Fragmented
Frames
Table 5-37 summaries the key points for comparison between the various traffic-shaping tools.
Table 5-37 Comparison of Traffic Shaping Tools: GTS, CB Shaping, DTS, and FRTS
Feature |
GTS |
CB Shaping |
DTS |
FRTS |
|
|
|
|
|
Supports ATM, FR, HDLC, PPP, LAN |
Yes |
Yes |
Yes |
No |
interfaces |
|
|
|
|
|
|
|
|
|
Can be enabled on interfaces and |
Yes |
Yes |
Yes |
Yes |
subinterfaces |
|
|
|
|
|
|
|
|
|
Can be enabled per Frame Relay DLCI |
No |
No |
No |
Yes |
to support per-VC shaping on multipoint |
|
|
|
|
interfaces |
|
|
|
|
|
|
|
|
|
Supports adaptive shaping |
Yes |
Yes |
Yes |
Yes |
|
|
|
|
|
Supports concurrent FRF.12 Frame |
No |
No |
No |
Yes |
Relay fragmentation |
|
|
|
|
|
|
|
|
|
Queuing methods in shaping queue |
WFQ |
FIFO, WFQ, |
FIFO, WFQ, |
FIFO, WFQ, |
|
|
CBWFQ, |
CBWFQ, |
CBWFQ, |
|
|
LLQ |
LLQ |
LLQ, PQ, CQ |
|
|
|
|
|
Concurrent queuing methods on |
All |
All |
All |
FIFO, FRF* |
Physical interface |
|
|
|
|
|
|
|
|
|

Foundation Summary 415
Table 5-37 Comparison of Traffic Shaping Tools: GTS, CB Shaping, DTS, and FRTS (Continued)
Feature |
GTS |
CB Shaping |
DTS |
FRTS |
|
|
|
|
|
Can be configured using MQC |
No |
Yes |
Yes |
No |
commands |
|
|
|
|
|
|
|
|
|
Can classify traffic to shape a subset of |
Yes |
Yes |
Yes |
No |
the traffic on an interface/VC |
|
|
|
|
|
|
|
|
|
Default Tc |
Variable |
125 ms |
125 ms |
125 ms |
|
|
|
|
|
Distributes shaping processing to VIPs |
No |
No |
Yes |
No |
in 7500 series routers |
|
|
|
|
|
|
|
|
|
*The Cisco QoS course claims WFQ is supported on the physical interface. In addition, FRF is not technically a queuing tool, although its feature of using two queues does achieve the same effect.
Table 5-38 lists the matchable fields for classification for CB policing and CAR.
Table 5-38 Classification Fields Used by CAR and CB Policing
Field |
Tool |
Comments |
|
|
|
Anything matched with an |
CAR, CB policing |
N/A |
IP ACL |
|
|
|
|
|
Source MAC Address |
CAR, CB policing |
CAR uses a special access-rate ACL; CB |
|
|
marking uses the match command. |
|
|
|
IP Precedence |
CAR, CB policing |
CAR uses a special access-rate ACL specific to |
|
|
CAR; CB marking uses the match command; |
|
|
Both can match a subset of values. |
|
|
|
MPLS Experimental |
CAR, CB policing |
CAR uses a special access-rate ACL specific to |
|
|
CAR; CB marking uses the match command. |
|
|
Both can match a subset of values. |
|
|
|
IP DSCP |
CAR, CB policing |
Can check for multiple values using multiple |
|
|
match commands. |
|
|
|
QoS Group |
CAR, CB policing |
The QoS Group field is used to tag packets |
|
|
internal to a single router. |
|
|
|
Class of Service (CoS) |
CB policing |
Checks incoming ISL/802.1P CoS bits. Can |
|
|
match multiple values. |
|
|
|
Destination MAC Address |
CB policing |
N/A |
|
|
|
Input interface |
CB policing |
N/A |
|
|
|
continues

416 Chapter 5: Traffic Policing and Shaping
Table 5-38 Classification Fields Used by CAR and CB Policing (Continued)
Field |
Tool |
Comments |
|
|
|
RTP’s UDP port-number |
CB policing |
RTP uses even numbered UDP ports from |
range |
|
16384–32767 for voice payload. This matching |
|
|
option allows matching a subset of the port |
|
|
numbers, and it matches only the even-numbered |
|
|
ports. |
|
|
|
NBAR protocol types |
CB policing |
Refer to the coverage in Chapter 3 for more |
|
|
details. |
|
|
|
NBAR Citrix applications |
CB policing |
NBAR can recognize different types of Citrix |
|
|
applications; CB marking can use NBAR to |
|
|
classify based on these application types. |
|
|
|
Host Name and URL string |
CB policing |
NBAR can match URL strings using regular |
|
|
expressions, including the host name. CB |
|
|
marking can use NBAR to match these strings |
|
|
for classification. |
|
|
|
Table 5-39 lists the various actions associated with CB policing and CAR.
Table 5-39 Policing Actions Used by CAR and CB Policing
|
|
|
CB |
Action Keyword |
Meaning |
CAR? |
Policer? |
|
|
|
|
drop |
Discards the packet |
Yes |
Yes |
|
|
|
|
transmit |
Forwards the packet |
Yes |
Yes |
|
|
|
|
set-prec-transmit |
Forwards the packet after marking the IP precedence |
Yes |
Yes |
|
value. |
|
|
|
|
|
|
set-qos-transmit |
Forwards the packet after marking the QoS group |
Yes |
Yes |
|
|
|
|
set-dscp-transmit |
Forwards the packet after marking the IP DSCP value |
Yes |
Yes |
|
|
|
|
set-mpls-exp-transmit |
Forwards the packet after marking the MPLS |
Yes |
Yes |
|
Experimental bits |
|
|
|
|
|
|
set-frde-transmit |
Forwards the packet after marking the Frame Relay |
No |
Yes |
|
discard eligibility (DE) bit |
|
|
|
|
|
|
set-clp-transmit |
Forwards the packet after marking the ATM cell loss |
No |
Yes |
|
priority (CLP) bit |
|
|
|
|
|
|
set-prec-continue |
Marks the IP precedence value, and continues to the |
Yes |
No |
|
next nested (cascaded) CAR command |
|
|
|
|
|
|
set-dscp-continue |
Marks the QoS group, and continues to the next |
Yes |
No |
|
nested (cascaded) CAR command |
|
|
|
|
|
|

Foundation Summary 417
Table 5-39 Policing Actions Used by CAR and CB Policing (Continued)
|
|
|
CB |
Action Keyword |
Meaning |
CAR? |
Policer? |
|
|
|
|
set-mpls-exp-continue |
Marks the IP precedence value, and continues to the |
Yes |
No |
|
next nested (cascaded) CAR command |
|
|
|
|
|
|
set-qos-continue |
Marks the QoS group, and continues to the next |
Yes |
No |
|
nested (cascaded) CAR command |
|
|
|
|
|
|
continue |
Just continues to the next nested (cascaded) CAR |
Yes |
No |
|
command |
|
|
|
|
|
|
Tables 5-40 and 5-41 list the CB policing configuration and show commands, respectively.
Table 5-40 Command Reference for Class-Based Policing
Command |
Mode and Function |
|
|
police bps burst-normal burst-max |
Policy-map class subcommand; enables policing for the |
conform-action action exceed-action |
class, setting the police rate, Bc, and Bc + Be values, |
action [violate-action action] |
and actions taken. Actions are drop, set-clp-transmit, |
|
set-dscp-transmit, set-prec-transmit, set-qos- |
|
transmit, transmit. |
|
|
service-policy {input | output} policy- |
Interface or subinterface configuration mode; enables |
map-name |
CB shaping on the interface. |
|
|
class-map class-map-name |
Global config; names a class map, where classification |
|
options are configured. |
|
|
Match … |
Class-map subcommand; defines specific classification |
|
parameters. |
|
|
match access-group {access-group | name |
Access-control list (ACL). |
access-group-name} |
|
|
|
match source-address mac address- |
Source MAC address. |
destination |
|
|
|
match ip precedence ip-precedence-value |
IP precedence. |
[ip-precedence-value ip-precedence-value |
|
ip-precedence-value] |
|
|
|
match mpls experimental number |
MPLS Experimental. |
|
|
match cos cos-value [cos-value cos-value |
CoS. |
cos-value] |
|
|
|
match destination-address mac address |
Destination MAC address. |
|
|
match input-interface interface-name |
Input interface. |
|
|
continues

418 Chapter 5: Traffic Policing and Shaping
Table 5-40 Command Reference for Class-Based Policing (Continued)
|
Command |
Mode and Function |
|
|
|
|
match ip dscp ip-dscp-value [ip-dscp- |
IP DSCP. |
|
value ip-dscp-value ip-dscp-value ip-dscp- |
|
|
value ip-dscp-value ip-dscp-value ip-dscp- |
|
|
value] |
|
|
|
|
|
match ip rtp starting-port-number port- |
RTP’s UDP port-number range. |
|
range |
|
|
|
|
|
match qos-group qos-group-value |
QoS group. |
|
|
|
|
match protocol protocol-name |
NBAR protocol types. |
|
|
|
|
match protocol citrix [app application- |
NBAR Citrix applications. |
|
name-string]. |
|
|
|
|
|
match protocol http [url url-string | host |
Host name and URL string. |
|
hostname-string | mime MIME-type] |
|
|
|
|
|
match any |
All packets. |
|
|
|
|
policy-map policy-map-name |
Global config; names a policy, which is a set of actions |
|
|
to perform. |
|
|
|
|
class name |
policy-map subcommand; identifies which packets on |
|
|
which to perform some action by referring to the |
|
|
classification logic in a class map. |
|
|
|
Table 5-41 Exec Command Reference for Class-Based Policing |
||
|
|
|
|
Command |
Function |
|
|
|
|
show policy-map policy-map-name |
Lists configuration information about all MQC-based |
|
|
QoS tools |
|
|
|
|
show policy-map interface-spec [input | |
Lists statistical information about the behavior of all |
|
output] [class class-name] |
MQC-based QoS tools |
|
|
|
Tables 5-42 and 5-43 list the CAR configuration and show commands, respectively.

|
|
Foundation Summary 419 |
|
|
|
Table 5-42 Configuration Command Reference for CAR |
|
|
|
|
|
|
Command |
Mode and Function |
|
|
|
|
rate-limit {input | output} [access-group |
Interface mode; configures classification, marking, |
|
[rate-limit] acl-index] bps burst-normal |
policing, and enables CAR on the interface |
|
burst-max conform-action conform-action |
|
|
exceed-action exceed-action |
|
|
|
|
|
access-list rate-limit acl-index |
Global mode; creates a CAR ACL, which can match IP |
|
{precedence | mac-address | exp mask |
precedence, MAC addresses, and MPLS Experimental |
|
mask} |
bits |
|
|
|
|
The remaining entries describe the possible actions in the rate-limit command: |
|
|
|
|
|
continue |
Evaluates the next rate-limit command |
|
|
|
|
drop |
Drops the packet |
|
|
|
|
set-dscp-continue |
Sets the differentiated services code point (DSCP) |
|
|
(0 to 63) and evaluates the next rate-limit command. |
|
|
|
|
set-dscp-transmit |
Sends the DSCP and transmits the packet |
|
|
|
|
set-mpls-exp-continue |
Sets the MPLS Experimental bits (0 to 7) and evaluates |
|
|
the next rate-limit command |
|
|
|
|
set-mpls-exp-transmit |
Sets the MPLS Experimental bits (0 to 7) and sends the |
|
|
packet |
|
|
|
|
set-prec-continue |
Sets the IP precedence (0 to 7) and evaluates the next |
|
|
rate-limit command |
|
|
|
|
set-prec-transmit |
Sets the IP precedence (0 to 7) and sends the packet. |
|
|
|
|
set-qos-continue |
Sets the QoS group ID (1 to 99) and evaluates the next |
|
|
rate-limit command |
|
|
|
|
set-qos-transmit |
Sets the QoS group ID (1 to 99) and sends the packet |
|
|
|
|
transmit |
Sends the packet |
|
|
|
Table 5-43 Exec Command Reference for CAR |
|
|
|
|
|
|
Command |
Function |
|
|
|
|
show interfaces [interface-type interface- |
Displays CAR statistics on the interface specified, or on |
|
number] rate-limit |
all interfaces if the interface is not specified |
|
|
|
|
show access-lists rate-limit [acl-index] |
Lists information about the configuration of rate-limit |
|
|
ACLs |
|
|
|

420 Chapter 5: Traffic Policing and Shaping
Table 5-44 summarizes the CAR features, comparing them with CB policing.
Table 5-44 CAR and CB Policing Features Compared
Feature |
CB Policing |
CAR |
|
|
|
Allows conform and exceed action categories |
Yes |
Yes |
|
|
|
Allows violate action category |
Yes |
No |
|
|
|
Polices either all traffic, or a subset through |
Yes |
Yes |
classification |
|
|
|
|
|
Uses MQC for configuration |
Yes |
No |
|
|
|
Allows nested or cascaded policing logic |
No |
Yes |
|
|
|
Can be enabled per subinterface |
Yes |
Yes |
|
|
|
Can be enabled per DLCI on multipoint |
No |
No |
subinterfaces |
|
|
|
|
|
Can set ATM CLP bit |
Yes |
No |
|
|
|
Can set FR DE bit |
Yes |
No |
|
|
|
