
- •Warning and Disclaimer
- •Feedback Information
- •Trademark Acknowledgments
- •About the Author
- •About the Technical Reviewers
- •Dedication
- •Acknowledgments
- •Contents at a Glance
- •Contents
- •Icons Used in This Book
- •Command Syntax Conventions
- •Cisco’s Motivation: Certifying Partners
- •Format of the CCNA Exams
- •What’s on the CCNA Exams
- •ICND Exam Topics
- •Cross-Reference Between Exam Topics and Book Parts
- •CCNA Exam Topics
- •INTRO and ICND Course Outlines
- •Objectives and Methods
- •Book Features
- •How This Book Is Organized
- •Part I: LAN Switching
- •Part II: TCP/IP
- •Part III: Wide-Area Networks
- •Part IV: Network Security
- •Part V: Final Preparation
- •Part VI: Appendixes
- •How to Use These Books to Prepare for the CCNA Exam
- •For More Information
- •Part I: LAN Switching
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Brief Review of LAN Switching
- •The Forward-Versus-Filter Decision
- •How Switches Learn MAC Addresses
- •Forwarding Unknown Unicasts and Broadcasts
- •LAN Switch Logic Summary
- •Basic Switch Operation
- •Foundation Summary
- •Spanning Tree Protocol
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Spanning Tree Protocol
- •What IEEE 802.1d Spanning Tree Does
- •How Spanning Tree Works
- •Electing the Root and Discovering Root Ports and Designated Ports
- •Reacting to Changes in the Network
- •Spanning Tree Protocol Summary
- •Optional STP Features
- •EtherChannel
- •PortFast
- •Rapid Spanning Tree (IEEE 802.1w)
- •RSTP Link and Edge Types
- •RSTP Port States
- •RSTP Port Roles
- •RSTP Convergence
- •Edge-Type Behavior and PortFast
- •Link-Type Shared
- •Link-Type Point-to-Point
- •An Example of Speedy RSTP Convergence
- •Basic STP show Commands
- •Changing STP Port Costs and Bridge Priority
- •Foundation Summary
- •Foundation Summary
- •Virtual LANs and Trunking
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Review of Virtual LAN Concepts
- •Trunking with ISL and 802.1Q
- •ISL and 802.1Q Compared
- •VLAN Trunking Protocol (VTP)
- •How VTP Works
- •VTP Pruning
- •Foundation Summary
- •Part II: TCP/IP
- •IP Addressing and Subnetting
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •IP Addressing Review
- •IP Subnetting
- •Analyzing and Interpreting IP Addresses and Subnets
- •Math Operations Used to Answer Subnetting Questions
- •Converting IP Addresses from Decimal to Binary and Back Again
- •The Boolean AND Operation
- •How Many Hosts and How Many Subnets?
- •What Is the Subnet Number, and What Are the IP Addresses in the Subnet?
- •Finding the Subnet Number
- •Finding the Subnet Broadcast Address
- •Finding the Range of Valid IP Addresses in a Subnet
- •Finding the Answers Without Using Binary
- •Easier Math with Easy Masks
- •Which Subnet Masks Meet the Stated Design Requirements?
- •What Are the Other Subnet Numbers?
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Extended ping Command
- •Distance Vector Concepts
- •Distance Vector Loop-Avoidance Features
- •Route Poisoning
- •Split Horizon
- •Split Horizon with Poison Reverse
- •Hold-Down Timer
- •Triggered (Flash) Updates
- •RIP and IGRP
- •IGRP Metrics
- •Examination of RIP and IGRP debug and show Commands
- •Issues When Multiple Routes to the Same Subnet Exist
- •Administrative Distance
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Link-State Routing Protocol and OSPF Concepts
- •Steady-State Operation
- •Loop Avoidance
- •Scaling OSPF Through Hierarchical Design
- •OSPF Areas
- •Stub Areas
- •Summary: Comparing Link-State and OSPF to Distance Vector Protocols
- •Balanced Hybrid Routing Protocol and EIGRP Concepts
- •EIGRP Loop Avoidance
- •EIGRP Summary
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Route Summarization and Variable-Length Subnet Masks
- •Route Summarization Concepts
- •VLSM
- •Route Summarization Strategies
- •Sample “Best” Summary on Seville
- •Sample “Best” Summary on Yosemite
- •Classless Routing Protocols and Classless Routing
- •Classless and Classful Routing Protocols
- •Autosummarization
- •Classful and Classless Routing
- •Default Routes
- •Classless Routing
- •Foundation Summary
- •Advanced TCP/IP Topics
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Scaling the IP Address Space for the Internet
- •CIDR
- •Private Addressing
- •Network Address Translation
- •Static NAT
- •Dynamic NAT
- •Overloading NAT with Port Address Translation (PAT)
- •Translating Overlapping Addresses
- •Miscellaneous TCP/IP Topics
- •Internet Control Message Protocol (ICMP)
- •ICMP Echo Request and Echo Reply
- •Destination Unreachable ICMP Message
- •Time Exceeded ICMP Message
- •Redirect ICMP Message
- •Secondary IP Addressing
- •FTP and TFTP
- •TFTP
- •MTU and Fragmentation
- •Foundation Summary
- •Part III: Wide-Area Networks
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Review of WAN Basics
- •Physical Components of Point-to-Point Leased Lines
- •Data-Link Protocols for Point-to-Point Leased Lines
- •HDLC and PPP Compared
- •Looped Link Detection
- •Enhanced Error Detection
- •Authentication Over WAN Links
- •PAP and CHAP Authentication
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •ISDN Protocols and Design
- •Typical Uses of ISDN
- •ISDN Channels
- •ISDN Protocols
- •ISDN BRI Function Groups and Reference Points
- •ISDN PRI Function Groups and Reference Points
- •BRI and PRI Encoding and Framing
- •PRI Encoding
- •PRI Framing
- •BRI Framing and Encoding
- •DDR Step 1: Routing Packets Out the Interface to Be Dialed
- •DDR Step 2: Determining the Subset of the Packets That Trigger the Dialing Process
- •DDR Step 3: Dialing (Signaling)
- •DDR Step 4: Determining When the Connection Is Terminated
- •ISDN and DDR show and debug Commands
- •Multilink PPP
- •Foundation Summary
- •Frame Relay
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Frame Relay Protocols
- •Frame Relay Standards
- •Virtual Circuits
- •LMI and Encapsulation Types
- •DLCI Addressing Details
- •Network Layer Concerns with Frame Relay
- •Layer 3 Addressing with Frame Relay
- •Frame Relay Layer 3 Addressing: One Subnet Containing All Frame Relay DTEs
- •Frame Relay Layer 3 Addressing: One Subnet Per VC
- •Frame Relay Layer 3 Addressing: Hybrid Approach
- •Broadcast Handling
- •Frame Relay Service Interworking
- •A Fully-Meshed Network with One IP Subnet
- •Frame Relay Address Mapping
- •A Partially-Meshed Network with One IP Subnet Per VC
- •A Partially-Meshed Network with Some Fully-Meshed Parts
- •Foundation Summary
- •Part IV: Network Security
- •IP Access Control List Security
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Standard IP Access Control Lists
- •IP Standard ACL Concepts
- •Wildcard Masks
- •Standard IP ACL: Example 2
- •Extended IP Access Control Lists
- •Extended IP ACL Concepts
- •Extended IP Access Lists: Example 1
- •Extended IP Access Lists: Example 2
- •Miscellaneous ACL Topics
- •Named IP Access Lists
- •Controlling Telnet Access with ACLs
- •ACL Implementation Considerations
- •Foundation Summary
- •Part V: Final Preparation
- •Final Preparation
- •Suggestions for Final Preparation
- •Preparing for the Exam Experience
- •Final Lab Scenarios
- •Scenario 1
- •Scenario 1, Part A: Planning
- •Solutions to Scenario 1, Part A: Planning
- •Scenario 2
- •Scenario 2, Part A: Planning
- •Solutions to Scenario 2, Part A: Planning
- •Part VI: Appendixes
- •Glossary
- •Answers to the “Do I Know This Already?” Quizzes and Q&A Questions
- •Chapter 1
- •“Do I Know This Already?” Quiz
- •Chapter 2
- •“Do I Know This Already?” Quiz
- •Chapter 3
- •“Do I Know This Already?” Quiz
- •Chapter 4
- •“Do I Know This Already?” Quiz
- •Chapter 5
- •“Do I Know This Already?” Quiz
- •Chapter 6
- •“Do I Know This Already?” Quiz
- •Chapter 7
- •“Do I Know This Already?” Quiz
- •Chapter 8
- •“Do I Know This Already?” Quiz
- •Chapter 9
- •“Do I Know This Already?” Quiz
- •Chapter 10
- •“Do I Know This Already?” Quiz
- •Chapter 11
- •“Do I Know This Already?” Quiz
- •Chapter 12
- •“Do I Know This Already?” Quiz
- •Using the Simulation Software for the Hands-on Exercises
- •Accessing NetSim from the CD
- •Hands-on Exercises Available with NetSim
- •Scenarios
- •Labs
- •Listing of the Hands-on Exercises
- •How You Should Proceed with NetSim
- •Considerations When Using NetSim
- •Routing Protocol Overview
- •Comparing and Contrasting IP Routing Protocols
- •Routing Through the Internet with the Border Gateway Protocol
- •RIP Version 2
- •The Integrated IS-IS Link State Routing Protocol
- •Summary of Interior Routing Protocols
- •Numbering Ports (Interfaces)
Standard IP Access Control Lists 427
Foundation Topics
Standard IP Access Control Lists
IP access control lists (ACLs) cause a router to discard some packets based on criteria defined by the network engineer. The goal of these filters is to prevent unwanted traffic in the network—whether to prevent hackers from penetrating the network or just to prevent employees from using systems they should not be using. Access lists should simply be part of an organization’s security policy.
By the way, IP access lists can also be used to filter routing updates, to match packets for prioritization, to match packets for VPN tunneling, and to match packets for implementing quality of service features. So you will see ACLs in most of the other Cisco certification exams as you move on in your career.
This chapter covers two main categories of IOS IP ACLs—standard and extended. Standard ACLs use simpler logic, and extended ACLs use more-complex logic. The first section of this chapter covers standard IP ACLs, followed by a section on extended IP ACLs. Several sections related to both types of ACLs close the chapter.
IP Standard ACL Concepts
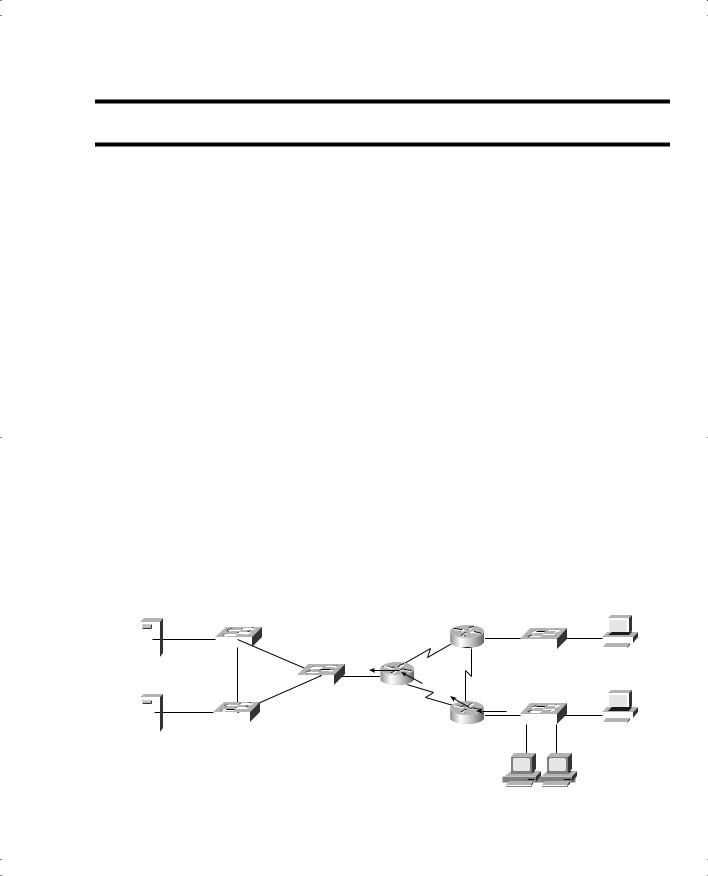
As soon as you know what needs to be filtered, the next step is to decide where to filter the traffic. Figure 12-1 serves as an example. In this case, imagine that Bob is not allowed to access Server1, but Larry is.
Figure 12-1 Locations Where Access List Logic Can Be Applied in the Network
Server1 |
|
|
|
|
|
|
|
|
|
|
Larry |
||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
S0 R2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
SW2 |
|
|
|
E0 |
SW12 |
|
|
|
|
|
||
|
|
|
|
|
|
|
|
||||||||
|
|
|
|
|
|
|
S0 |
S1 |
|
|
172.16.2.10 |
||||
172.16.1.100 |
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
E0 R1 |
|
|
|
|
|
|
|
|
Server2 |
|
|
|
SW1 |
|
|
|
|
|
Bob |
|||||
|
|
|
|
S1 |
S1 |
|
|
|
|
||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
S0 |
|
|
|
|
|
|
|
|
|
|
SW3 |
|
|
|
|
R3 |
E0 |
SW13 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||
|
|
|
|
|
|
|
|
|
|||||||
|
|
|
|
|
|
|
|
172.16.3.10 |
|||||||
|
|
|
|
|
|
|
|
|
|
||||||
172.16.1.102
Jimmy Jerry
172.16.3.8 172.16.3.9
428 Chapter 12: IP Access Control List Security
Filtering logic could be configured on any of the three routers and on any of their interfaces. The dotted arrowed lines in the figure show the most appropriate points at which to apply the filtering logic in an ACL. Because Bob’s traffic is the only traffic that needs to be filtered, and the goal is to stop access to Server1, the access list could be applied at either R1 or R3. And because Bob’s attempted traffic to Server1 would not need to go through R2, R2 would not be a good place to put the access list logic. For the sake of discussion, assume that R1 should have the access list applied.
Cisco IOS software applies the filtering logic of an ACL either as a packet enters an interface or as it exits the interface. In other words, IOS associates an ACL with an interface, and specifically for traffic either entering or exiting the interface. After you have chosen the router on which you want to place the access list, you must choose the interface on which to apply the access logic, as well as whether to apply the logic for inbound or outbound packets.
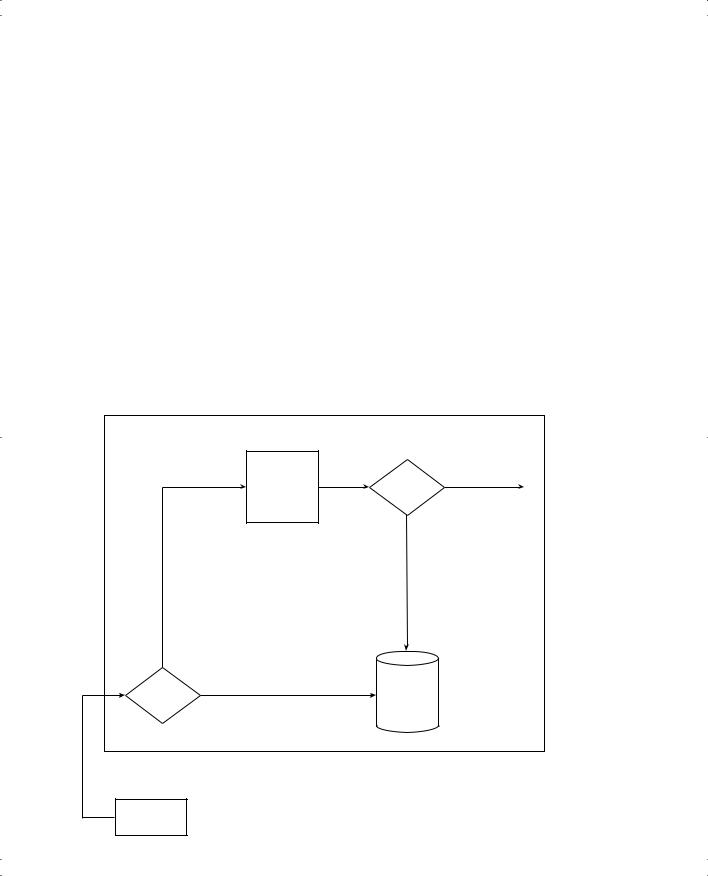
For instance, imagine that you want to filter Bob’s packets sent to Server1. Figure 12-2 shows the options for filtering the packet.
Figure 12-2 Internal Processing in R1 in Relation to Where R1 Can Filter Packets
Router R1
|
|
Permit |
Routing |
Outbound |
Permit |
E0 |
|
|
|
Logic |
|
||
|
|
|
ACL |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Deny |
|
|
S1 |
Inbound |
Deny |
|
Bit |
|
|
|
|
|
|
|
||
|
ACL |
|
|
Bucket |
|
|
IP Packet

Standard IP Access Control Lists 429
Filtering logic can be applied to packets entering S1 or to packets exiting E0 on R1 to match the packet sent by Bob to Server1. In general, you can filter packets by creating and enabling access lists for both incoming and outgoing packets on each interface. Here are some key features of Cisco access lists:
■Packets can be filtered as they enter an interface, before the routing decision.
■Packets can be filtered before they exit an interface, after the routing decision.
■Deny is the term used in Cisco IOS software to imply that the packet will be filtered.
■Permit is the term used in Cisco IOS software to imply that the packet will not be filtered.
■The filtering logic is configured in the access list.
■At the end of every access list is an implied “deny all traffic” statement. Therefore, if a packet does not match any of your access list statements, it is blocked.
For example, you might create an access list in R1 and enable it on R1’s S1 interface. The access list would look for packets that came from Bob. Therefore, the access list would need to be enabled for inbound packets, because in this network, packets from Bob enter S1, and packets to Bob exit S1.
Access lists have two major steps in their logic: matching and action. Matching logic examines each packet and determines whether it matches the access-list statement. For instance, Bob’s IP address would be used to match packets sent from Bob.
IP ACLs tell the router to take one of two actions when a statement is matched: deny or permit. Deny means to discard the packet, and permit implies that the packet should continue on its way.
So the access list for preventing Bob’s traffic to the server might go something like this:
Look for packets with Bob’s source IP address and Server1’s destination IP address. When you see them, discard them. If you see any other packets, do not discard them.
Not surprisingly, IP ACLs can get a lot more difficult than that in real life. Even a short list of matching criteria can create complicated access lists on a variety of interfaces in a variety of routers. I’ve even heard of a couple of large networks with a few full-time people who do nothing but plan and implement access lists!
Cisco calls its packet-filtering features “Access Control Lists” in part because the logic is created with multiple configuration commands that are considered to be in the same list. When an access list has multiple entries, IOS searches the list sequentially until the first

430 Chapter 12: IP Access Control List Security
statement is matched. The matched statement determines the action to be taken. The two diamond shapes in Figure 12-2 represent the application of access list logic.
The logic that IOS uses with a multiple-entry ACL can be summarized as follows:
1.The matching parameters of the access-list statement are compared to the packet.
2.If a match is made, the action defined in this access-list statement (permit or deny) is performed.
3.If a match is not made in Step 2, repeat Steps 1 and 2 using each successive statement in the ACL until a match is made.
4.If no match is made with an entry in the access list, the deny action is performed.
Wildcard Masks
IOS IP ACLs match packets by looking at the IP, TCP, and UDP headers in the packet.
Extended access lists can check source and destination IP addresses, as well as source and destination port numbers, along with several other fields. However, standard IP access lists can examine only the source IP address.
Regardless of whether you use standard or extended IP ACLs, you can tell the router to match based on the entire IP address or just a part of the IP address. For instance, if you wanted to stop Bob from sending packets to Server1, you would look at the entire IP address of Bob and Server1 in the access list. But what if the criteria were to stop all hosts in Bob’s subnet from getting to Server1? Because all hosts in Bob’s subnet have the same numbers in their first three octets, the access list could just check the first three octets of the address to match all packets with a single access-list command.
Cisco wildcard masks define the portion of the IP address that should be examined. When defining the ACL statements, as you’ll see in the next section of this chapter, you can define a wildcard mask along with the IP address. The wildcard mask tells the router which part of the IP address in the configuration statement must be compared with the packet header.
For example, suppose that one mask implies that the whole packet should be checked and another implies that only the first three octets of the address need to be examined. (You might choose to do that to match all IP hosts in the same subnet when using a subnet mask of 255.255.255.0.) To perform this matching, Cisco access lists use wildcard masks.
Wildcard masks look similar to subnet masks, but they are not the same. Wildcard masks represent a 32-bit number, as do subnet masks. However, the wildcard mask’s 0 bits tell the

Standard IP Access Control Lists 431
router that those corresponding bits in the address must be compared when performing the matching logic. The binary 1s in the wildcard mask tell the router that those bits do not need to be compared. In fact, many people call these bits the “don’t care” bits.
To get a sense of the idea behind a wildcard mask, Table 12-2 lists some of the more popular wildcard masks, along with their meanings.
Table 12-2 Sample Access List Wildcard Masks
Wildcard Mask |
Binary Version of the Mask |
Description |
|
|
|
0.0.0.0 |
00000000.00000000.00000000.00000000 |
The entire IP address |
|
|
must match. |
|
|
|
0.0.0.255 |
00000000.00000000.00000000.11111111 |
Just the first 24 bits |
|
|
must match. |
|
|
|
0.0.255.255 |
00000000.00000000.11111111.11111111 |
Just the first 16 bits |
|
|
must match. |
|
|
|
0.255.255.255 |
00000000.11111111.11111111.11111111 |
Just the first 8 bits |
|
|
must match. |
|
|
|
255.255.255.255 |
11111111.11111111.11111111.11111111 |
Don’t even bother to |
|
|
compare; it’s |
|
|
automatically |
|
|
considered to match |
|
|
(all 32 bits are “don’t |
|
|
care” bits). |
|
|
|
0.0.15.255 |
00000000.00000000.00001111.11111111 |
Just the first 20 bits |
|
|
must match. |
|
|
|
0.0.3.255 |
00000000.00000000.00000011.11111111 |
Just the first 22 bits |
|
|
must match. |
|
|
|
The first several examples show typical uses of the wildcard mask. As you can see, it is not a subnet mask. A wildcard of 0.0.0.0 means that the entire IP address must be examined, and be equal, to be considered a match. 0.0.0.255 means that the last octet automatically matches, but the first three must be examined, and so on. More generally, the wildcard mask means the following:
Bit positions of binary 0 mean that the access list compares the corresponding bit position in the IP address and makes sure it is equal to the same bit position in the address configured in the access-list statement. Bit positions of binary 1 are “don’t care” bits—those bit positions are immediately considered to be a match.
The next two rows of Table 12-2 show two reasonable, but not obvious, wildcard masks. 0.0.15.255 in binary is 20 0s followed by 12 1s. This means that the first 20 bits must match.

432 Chapter 12: IP Access Control List Security
Similarly, 0.0.3.255 means that the first 22 bits must be examined to find out if they match. Why are these useful? If the subnet mask is 255.255.240.0, and you want to match all hosts in the same subnet, the 0.0.15.255 wildcard means that all network and subnet bits must be matched, and all host bits are automatically considered to match. Likewise, if you want to filter all hosts in a subnet that uses subnet mask 255.255.252.0, the wildcard mask 0.0.3.255 matches the network and subnet bits. In general, if you want a wildcard mask that helps you match all hosts in a subnet, invert the subnet mask, and you have the correct wildcard mask.
NOTE In real jobs, you might want to match all the hosts in a single subnet. If you already know the subnet mask, and you want to use a wildcard mask that matches the same set of addresses, you can easily find the wildcard mask with a math trick. One octet at a time, in decimal, subtract the subnet mask from 255.255.255.255. The result is the
“right” wildcard mask. For instance, a subnet mask of 255.255.255.0 subtracted from 255.255.255.255 gives you 0.0.0.255 as a wildcard mask. This mask checks only the first 24 bits, which in this case are the network and subnet parts of the address. Similarly, if the subnet mask is 255.255.240.0, subtracting from 255.255.255.255 gives you 0.0.15.255. This is the same wildcard mask as one of the examples mentioned in Table 12-2.
Standard IP Access List Configuration
Before diving into the configuration, here’s a quick review of how standard IP ACLs work:
If statement 1 is matched, carry out the action defined in that statement. If it isn’t matched, examine the next statement. If it matches, carry out the action it defines. Continue looping through the list until a statement is matched or until the last statement in the list is not matched. If none of the statements is matched, the packet is discarded.
A standard access list is used to match a packet and then take the directed action. Each standard ACL can match all, or only part, of the packet’s source IP address. The only two actions taken when an access-list statement is matched are to either deny (discard) or permit (forward) the packet.
Table 12-3 lists the configuration commands related to standard IP access lists. Table 12-4 lists the related EXEC commands. Several examples follow these lists of commands.
Table 12-3 Standard IP Access List Configuration Commands
Command |
Configuration Mode and Description |
|
|
access-list access-list-number {deny | permit} source |
Global command for standard numbered |
[source-wildcard] [log] |
access lists. Use a number between 1 and |
|
99 or 1300 and 1999, inclusive. |
|
|
access-list access-list-number remark text |
Defines a remark that helps you |
|
remember what the ACL is supposed to |
|
do. |
|
|

|
|
|
Standard IP Access Control Lists 433 |
Table 12-3 Standard IP Access List Configuration Commands (Continued) |
|||
|
|
|
|
|
Command |
|
Configuration Mode and Description |
|
|
|
|
|
ip access-group {number | name [in | out]} |
|
Interface subcommand to enable access |
|
|
|
lists. |
|
|
|
|
|
access-class number | name [in | out] |
|
Line subcommand to enable either |
|
|
|
standard or extended access lists. |
|
|
|
|
Table 12-4 Standard IP Access List EXEC Commands |
|||
|
|
|
|
|
Command |
Description |
|
|
|
|
|
|
show ip interface [type number] |
Includes a reference to the access lists enabled on |
|
|
|
the interface. |
|
|
|
|
|
|
show access-lists [access-list-number | |
Shows details of configured access lists for all |
|
|
access-list-name] |
protocols. |
|
|
|
|
|
|
show ip access-list [access-list-number | |
Shows IP access lists. |
|
|
access-list-name] |
|
|
|
|
|
|
Example 12-1 attempts to stop Bob’s traffic to Server1. As shown in Figure 12-1, Bob is not allowed to access Server1. In Example 12-1, the configuration enables an ACL for all packets going out R1’s Ethernet0 interface. The ACL matches the source address in the packet— Bob’s IP address. Example 12-1 shows the configuration on R1.
Example 12-1 Standard Access List on R1 Stopping Bob from Reaching Server1
interface Ethernet0
ip address 172.16.1.1 255.255.255.0 ip access-group 1 out
access-list 1 remark stop all traffic whose source IP is Bob access-list 1 deny 172.16.3.10 0.0.0.0
access-list 1 permit 0.0.0.0 255.255.255.255
First, focus on the basic syntax of the commands. Standard IP access lists use a number in the range of 1 to 99 or 1300 to 1999. I used number 1 versus the other available numbers for no particular reason. (There is absolutely no difference in using one number or another, as long as it is in the correct range. In other words, list 1 is no better or worse than list 99.) The access-list commands, under which the matching and action logic are defined, are global configuration commands. To enable the ACL on an interface and define the direction of packets to which the ACL is applied, the ip access-group command is used. In this case, it enables the logic for ACL 1 on Ethernet0 for packets going out the interface.
