
- •Warning and Disclaimer
- •Feedback Information
- •Trademark Acknowledgments
- •About the Author
- •About the Technical Reviewers
- •Dedication
- •Acknowledgments
- •Contents at a Glance
- •Contents
- •Icons Used in This Book
- •Command Syntax Conventions
- •Cisco’s Motivation: Certifying Partners
- •Format of the CCNA Exams
- •What’s on the CCNA Exams
- •ICND Exam Topics
- •Cross-Reference Between Exam Topics and Book Parts
- •CCNA Exam Topics
- •INTRO and ICND Course Outlines
- •Objectives and Methods
- •Book Features
- •How This Book Is Organized
- •Part I: LAN Switching
- •Part II: TCP/IP
- •Part III: Wide-Area Networks
- •Part IV: Network Security
- •Part V: Final Preparation
- •Part VI: Appendixes
- •How to Use These Books to Prepare for the CCNA Exam
- •For More Information
- •Part I: LAN Switching
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Brief Review of LAN Switching
- •The Forward-Versus-Filter Decision
- •How Switches Learn MAC Addresses
- •Forwarding Unknown Unicasts and Broadcasts
- •LAN Switch Logic Summary
- •Basic Switch Operation
- •Foundation Summary
- •Spanning Tree Protocol
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Spanning Tree Protocol
- •What IEEE 802.1d Spanning Tree Does
- •How Spanning Tree Works
- •Electing the Root and Discovering Root Ports and Designated Ports
- •Reacting to Changes in the Network
- •Spanning Tree Protocol Summary
- •Optional STP Features
- •EtherChannel
- •PortFast
- •Rapid Spanning Tree (IEEE 802.1w)
- •RSTP Link and Edge Types
- •RSTP Port States
- •RSTP Port Roles
- •RSTP Convergence
- •Edge-Type Behavior and PortFast
- •Link-Type Shared
- •Link-Type Point-to-Point
- •An Example of Speedy RSTP Convergence
- •Basic STP show Commands
- •Changing STP Port Costs and Bridge Priority
- •Foundation Summary
- •Foundation Summary
- •Virtual LANs and Trunking
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Review of Virtual LAN Concepts
- •Trunking with ISL and 802.1Q
- •ISL and 802.1Q Compared
- •VLAN Trunking Protocol (VTP)
- •How VTP Works
- •VTP Pruning
- •Foundation Summary
- •Part II: TCP/IP
- •IP Addressing and Subnetting
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •IP Addressing Review
- •IP Subnetting
- •Analyzing and Interpreting IP Addresses and Subnets
- •Math Operations Used to Answer Subnetting Questions
- •Converting IP Addresses from Decimal to Binary and Back Again
- •The Boolean AND Operation
- •How Many Hosts and How Many Subnets?
- •What Is the Subnet Number, and What Are the IP Addresses in the Subnet?
- •Finding the Subnet Number
- •Finding the Subnet Broadcast Address
- •Finding the Range of Valid IP Addresses in a Subnet
- •Finding the Answers Without Using Binary
- •Easier Math with Easy Masks
- •Which Subnet Masks Meet the Stated Design Requirements?
- •What Are the Other Subnet Numbers?
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Extended ping Command
- •Distance Vector Concepts
- •Distance Vector Loop-Avoidance Features
- •Route Poisoning
- •Split Horizon
- •Split Horizon with Poison Reverse
- •Hold-Down Timer
- •Triggered (Flash) Updates
- •RIP and IGRP
- •IGRP Metrics
- •Examination of RIP and IGRP debug and show Commands
- •Issues When Multiple Routes to the Same Subnet Exist
- •Administrative Distance
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Link-State Routing Protocol and OSPF Concepts
- •Steady-State Operation
- •Loop Avoidance
- •Scaling OSPF Through Hierarchical Design
- •OSPF Areas
- •Stub Areas
- •Summary: Comparing Link-State and OSPF to Distance Vector Protocols
- •Balanced Hybrid Routing Protocol and EIGRP Concepts
- •EIGRP Loop Avoidance
- •EIGRP Summary
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Route Summarization and Variable-Length Subnet Masks
- •Route Summarization Concepts
- •VLSM
- •Route Summarization Strategies
- •Sample “Best” Summary on Seville
- •Sample “Best” Summary on Yosemite
- •Classless Routing Protocols and Classless Routing
- •Classless and Classful Routing Protocols
- •Autosummarization
- •Classful and Classless Routing
- •Default Routes
- •Classless Routing
- •Foundation Summary
- •Advanced TCP/IP Topics
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Scaling the IP Address Space for the Internet
- •CIDR
- •Private Addressing
- •Network Address Translation
- •Static NAT
- •Dynamic NAT
- •Overloading NAT with Port Address Translation (PAT)
- •Translating Overlapping Addresses
- •Miscellaneous TCP/IP Topics
- •Internet Control Message Protocol (ICMP)
- •ICMP Echo Request and Echo Reply
- •Destination Unreachable ICMP Message
- •Time Exceeded ICMP Message
- •Redirect ICMP Message
- •Secondary IP Addressing
- •FTP and TFTP
- •TFTP
- •MTU and Fragmentation
- •Foundation Summary
- •Part III: Wide-Area Networks
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Review of WAN Basics
- •Physical Components of Point-to-Point Leased Lines
- •Data-Link Protocols for Point-to-Point Leased Lines
- •HDLC and PPP Compared
- •Looped Link Detection
- •Enhanced Error Detection
- •Authentication Over WAN Links
- •PAP and CHAP Authentication
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •ISDN Protocols and Design
- •Typical Uses of ISDN
- •ISDN Channels
- •ISDN Protocols
- •ISDN BRI Function Groups and Reference Points
- •ISDN PRI Function Groups and Reference Points
- •BRI and PRI Encoding and Framing
- •PRI Encoding
- •PRI Framing
- •BRI Framing and Encoding
- •DDR Step 1: Routing Packets Out the Interface to Be Dialed
- •DDR Step 2: Determining the Subset of the Packets That Trigger the Dialing Process
- •DDR Step 3: Dialing (Signaling)
- •DDR Step 4: Determining When the Connection Is Terminated
- •ISDN and DDR show and debug Commands
- •Multilink PPP
- •Foundation Summary
- •Frame Relay
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Frame Relay Protocols
- •Frame Relay Standards
- •Virtual Circuits
- •LMI and Encapsulation Types
- •DLCI Addressing Details
- •Network Layer Concerns with Frame Relay
- •Layer 3 Addressing with Frame Relay
- •Frame Relay Layer 3 Addressing: One Subnet Containing All Frame Relay DTEs
- •Frame Relay Layer 3 Addressing: One Subnet Per VC
- •Frame Relay Layer 3 Addressing: Hybrid Approach
- •Broadcast Handling
- •Frame Relay Service Interworking
- •A Fully-Meshed Network with One IP Subnet
- •Frame Relay Address Mapping
- •A Partially-Meshed Network with One IP Subnet Per VC
- •A Partially-Meshed Network with Some Fully-Meshed Parts
- •Foundation Summary
- •Part IV: Network Security
- •IP Access Control List Security
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Standard IP Access Control Lists
- •IP Standard ACL Concepts
- •Wildcard Masks
- •Standard IP ACL: Example 2
- •Extended IP Access Control Lists
- •Extended IP ACL Concepts
- •Extended IP Access Lists: Example 1
- •Extended IP Access Lists: Example 2
- •Miscellaneous ACL Topics
- •Named IP Access Lists
- •Controlling Telnet Access with ACLs
- •ACL Implementation Considerations
- •Foundation Summary
- •Part V: Final Preparation
- •Final Preparation
- •Suggestions for Final Preparation
- •Preparing for the Exam Experience
- •Final Lab Scenarios
- •Scenario 1
- •Scenario 1, Part A: Planning
- •Solutions to Scenario 1, Part A: Planning
- •Scenario 2
- •Scenario 2, Part A: Planning
- •Solutions to Scenario 2, Part A: Planning
- •Part VI: Appendixes
- •Glossary
- •Answers to the “Do I Know This Already?” Quizzes and Q&A Questions
- •Chapter 1
- •“Do I Know This Already?” Quiz
- •Chapter 2
- •“Do I Know This Already?” Quiz
- •Chapter 3
- •“Do I Know This Already?” Quiz
- •Chapter 4
- •“Do I Know This Already?” Quiz
- •Chapter 5
- •“Do I Know This Already?” Quiz
- •Chapter 6
- •“Do I Know This Already?” Quiz
- •Chapter 7
- •“Do I Know This Already?” Quiz
- •Chapter 8
- •“Do I Know This Already?” Quiz
- •Chapter 9
- •“Do I Know This Already?” Quiz
- •Chapter 10
- •“Do I Know This Already?” Quiz
- •Chapter 11
- •“Do I Know This Already?” Quiz
- •Chapter 12
- •“Do I Know This Already?” Quiz
- •Using the Simulation Software for the Hands-on Exercises
- •Accessing NetSim from the CD
- •Hands-on Exercises Available with NetSim
- •Scenarios
- •Labs
- •Listing of the Hands-on Exercises
- •How You Should Proceed with NetSim
- •Considerations When Using NetSim
- •Routing Protocol Overview
- •Comparing and Contrasting IP Routing Protocols
- •Routing Through the Internet with the Border Gateway Protocol
- •RIP Version 2
- •The Integrated IS-IS Link State Routing Protocol
- •Summary of Interior Routing Protocols
- •Numbering Ports (Interfaces)

Chapter 8 527
19.What command switches a router from classless routing to classful routing?
Answer: The no ip classless global configuration command disables classless routing, thereby enabling classful routing.
Chapter 8
“Do I Know This Already?” Quiz
1.What does CIDR stand for?
Answer: F
2.Which of the following summarized subnets are valid routes according to the main purpose of CIDR?
Answer: D. CIDR’s original intent was to allow the summarization of multiple Class A, B, and C networks to reduce the size of Internet routing tables. Only answer D summarizes multiple networks.
3.Which of the following are not private addresses according to RFC 1918?
Answer: B, E. RFC 1918 identifies private network numbers. It includes Class A network 10.0.0.0, Class B networks 172.16.0.0 through 172.31.0.0, and 192.168.0.0 through 192.168.255.0.
4.With static NAT, performing translation for inside addresses only, what causes NAT table entries to be created?
Answer: C. With static NAT, the entries are statically configured. Because the question mentions translation for inside addresses, the inside keyword is needed on the command.
5.With dynamic NAT, performing translation for inside addresses only, what causes NAT table entries to be created?
Answer: A. With dynamic NAT, the entries are created as a result of the first packet flow from the inside network.
6.Which of the following commands identifies the inside local IP addresses when using dynamic NAT to translate only the source addresses of packets from a private network number?
Answer: A. The list 1 parameter references an IP ACL, which matches packets, identifying the inside local addresses.

528Appendix A: Answers to the “Do I Know This Already?” Quizzes and Q&A Questions
7.Which of the following commands identifies the outside local IP addresses when using dynamic NAT to translate only the source addresses of packets from a private network number?
Answer: E. The outside local IP address is not changed when only the source address of packets from a private network are translated.
8.Imagine that an Ethernet interface on a router has already been configured with IP address 10.1.1.1, mask 255.255.255.0. Which of the following commands adds a secondary IP address to the interface?
Answer: G. The ip address command is used, but with the secondary keyword at the end. Without the secondary keyword, the IP address would replace the original IP address.
9.Which of the following file transfer protocols, defined in various Internet RFCs, provides the most features?
Answer: A. Only FTP and TFTP are file transfer protocols defined in RFCs. FTP is easily the more feature-filled protocol, as compared to TFTP.
10.Imagine that Fred is a PC attached to an Ethernet, and that its default router, R1, is attached to the same Ethernet. R1 has a point-to-point serial link to R2, which has an Ethernet attached, to which PC Barney is attached. The MTU of each Ethernet has the default value. What must be true for R1 to fragment packets sent from Fred to Barney?
Answer: A. Ethernet interfaces default to an MTU of 1500. So the serial link would need an MTU lower than 1500 to cause fragmentation. Otherwise, R1 would never receive an IP packet from Fred that needed to be fragmented.
11.Router1 has a FastEthernet interface 0/0 with IP address 10.1.1.1. The interface is connected to a switch. This connection is then migrated to ISL. Which of the following commands could be useful to configure Router1 for ISL?
Answer: A, G
12.What is the meaning of “.” in the output of a ping command?
Answer: C. The “.” implies that the ping command sent the request, and waited, but did not receive a reply.

Chapter 8 529
13.What is the meaning of “U” in the output of a ping command?
Answer: E. The “U” designation implies that the ping command received an ICMP unreachable message, which might mean that the router had no route to the subnet to which the packet was sent.
14.What ICMP message code(s) does the trace command rely on?
Answer: C. The trace command sends packets with TTL = 1, and then TTL = 2, and so on. By receiving TTL Exceeded messages from the various routers in the route, the trace command can identify the routers.
Q&A
1.Define private addressing as defined in RFC 1918.
Answer: Some hosts will never need to communicate with other hosts across the Internet. For such hosts, assigning IP addresses from registered networks wastes IP addresses. To conserve IP addresses, a set of network numbers, called private addresses, has been reserved and can be used in these cases to help conserve IP addresses for use over the Internet.
2.List the range of private networks defined in RFC 1918.
Answer: Class A network 10.0.0.0, Class B networks 172.16.0.0 to 172.31.0.0, and Class C networks 192.168.0.0 to 192.168.255.0.
3.Does CIDR affect the size of Internet routing tables? If so, what does it do to those routing tables?
Answer: CIDR allows ISPs to summarize multiple Class A, B, or C networks, typically Class C networks, into summary routes. It shortens the length of the IP routing table, improving Internet routing performance.
4.Define NAT and explain the basics of its operation.
Answer: Network Address Translation is a mechanism for allowing hosts with private addresses or addresses that conflict with IP addresses from a registered network to communicate with hosts over the Internet. The basic operation involves the NAT router’s changing the IP addresses in packets to and from these hosts so that only legitimately registered IP addresses are used in flows through the Internet.
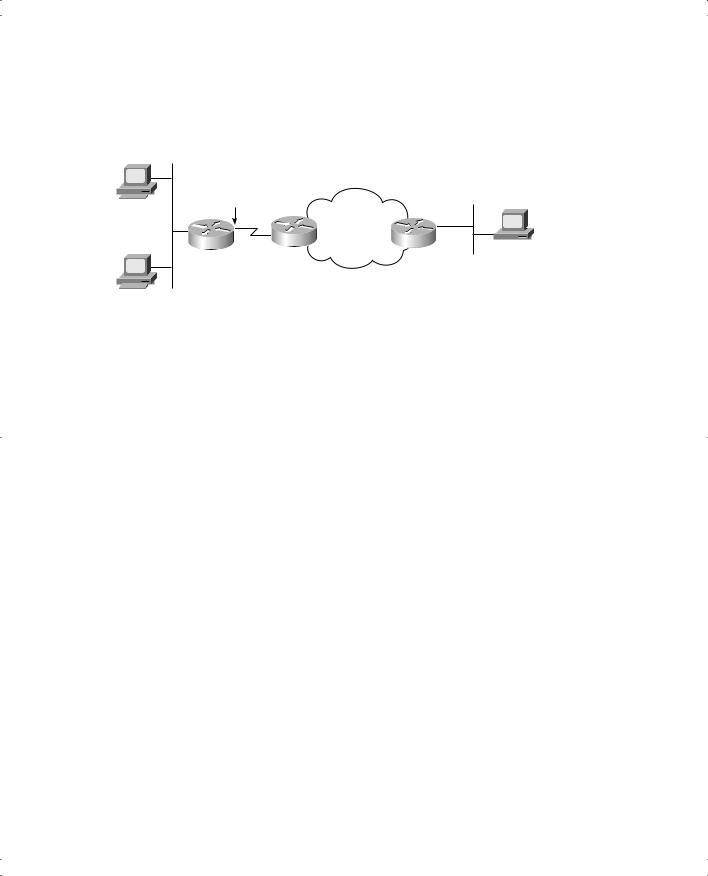
530 Appendix A: Answers to the “Do I Know This Already?” Quizzes and Q&A Questions
5.Define the term inside local address in relation to NAT. Use Figure A-2 to describe the answer.
Figure A-2 Network for Use in Answering NAT Questions
10.1.1.1 |
200.1.1.1 |
Server |
|
|
Internet
NAT  170.1.1.1
170.1.1.1
10.1.1.2
Answer: The inside network is the enterprise network on the left in Figure A-2. The private IP addresses reside in this network. Inside local refers to the IP address actually assigned to the computer. For instance, 10.1.1.1 is an inside local address in this figure.
6.Define the term inside global address in relation to NAT. Use Figure A-2 to describe the answer.
Answer: The inside network is the enterprise network on the left in Figure A-2. The inside global address is the address in the public Internet that represents the inside local address. 200.1.1.0 would be a likely candidate for an inside global IP address in this example.
7.Create a configuration for NAT overload to a single IP address for the router shown in Figure A-2.
Answer:
interface Ethernet0/0
ip address 10.1.1.3 255.255.255.0 ip nat inside
!
interface Serial0/0
ip address 200.1.1.1 255.255.255.252 ip nat outside
!
ip nat inside source list 1 interface Serial0/0 overload
!
access-list 1 permit 10.1.1.2 access-list 1 permit 10.1.1.1

Chapter 8 531
8.Create a configuration for static NAT, mapping host 10.1.1.1 to 200.1.1.11, for the router shown in Figure A-2.
Answer:
interface Ethernet0/0
ip address 10.1.1.3 255.255.255.0 ip nat inside
!
interface Serial0/0
ip address 200.1.1.1 255.255.255.252 ip nat outside
!
ip nat inside source static 10.1.1.1 200.1.1.11
9.Which requires more lines of source code, FTP or TFTP? Explain your answer.
Answer: FTP requires more code. TFTP was designed to be simple (that is, trivial). The small amount of memory needed to load its code is one of its advantages. FTP is much more robust, with many more features and code.
10.Does FTP or TFTP perform error recovery? If so, describe the basics of how this occurs.
Answer: Both FTP and TFTP perform error recovery. FTP relies on TCP, whereas TFTP performs application layer recovery one block of data at a time.
11.Describe the process used by IP routers to perform fragmentation and reassembly of packets.
Answer: When a packet must be forwarded, but the packet is larger than the maximum transmission unit (MTU) size for the outgoing interface, the router fragments the packet as long as the Don’t Fragment bit is not set in the packet header. No IP router reassembles the fragments; fragments are reassembled at the final destination host.
12.How many Class B-style networks are reserved by RFC 1918 private addressing?
Answer: Sixteen Class B networks are reserved for use as private networks in RFC 1918—networks 172.16.0.0 to 172.31.0.0.
13.Describe why ARP requests use an Ethernet broadcast address instead of an Ethernet unicast address.
Answer: Hosts use ARP when they need to learn the MAC address of another IP host. Because the host does not know the MAC address, it would be impossible to use an Ethernet unicast, because the host would not know the right MAC address to put in the destination address field in the Ethernet frame.
