
- •About the Authors
- •Dedication
- •Contents at a Glance
- •Table of Contents
- •Introduction
- •About This Book
- •System Requirements
- •How This Book Is Organized
- •Part I: Wireless Networking Fundamentals
- •Part II: Making Plans
- •Part III: Installing a Wireless Network
- •Part IV: Using a Wireless Network
- •Part V: The Part of Tens
- •Icons Used in This Book
- •Where to Go from Here
- •Nothing but Net(work): Why You Need (Or Want) One
- •File sharing
- •Printer and peripheral sharing
- •Internet connection sharing
- •Home arcades and wireless to go
- •Wired versus Wireless
- •Installing wired home networks
- •Installing wireless home networks
- •Picking a Wireless Standard
- •Planning Your Wireless Home Network
- •Workstations and servers
- •Network infrastructure
- •Network interface adapters
- •Get the (Access) Point?
- •Industry Standards
- •Who or What Is Bluetooth?
- •Wi-Fi versus Bluetooth
- •Piconets, Masters, and Slaves
- •Wirelessly synching your PDAs
- •Wireless printing and data transfer
- •Integrating HPNA and HomePlug with Your Wireless Home Network
- •Home Phoning (ET Got It Backward!)
- •Network Power(line)!
- •Deciding What Is Connected to the Network
- •Counting network devices
- •Choosing wired or wireless
- •Choosing a wireless technology
- •Choosing an access point
- •Deciding where to install the AP
- •Adding printers
- •Adding entertainment and more
- •Connecting to the Internet
- •Budgeting for Your Wireless Network
- •Pricing access points
- •Pricing wireless network adapters
- •A sample budget
- •Planning Security
- •Selecting Access Points
- •Certification and Standards Support
- •Compatibility and Form Factor
- •DHCP servers
- •Gateways, NAT, and cable/DSL routers
- •Switches
- •Print servers
- •Operational Features
- •Security
- •Range and Coverage Issues
- •Manageability
- •Web-based configuration
- •Software programming
- •Telnetting to your device
- •Upgradeable firmware
- •Price
- •Warranties
- •Customer and Technical Support
- •Before Getting Started, Get Prepared
- •Setting Up the Access Point
- •Preparing to install a wireless AP
- •Installing the AP
- •Configuring AP parameters
- •Changing the AP Configuration
- •Installing device drivers and client software
- •PC Cards and mini-PCI cards
- •Compact Flash cards
- •PCI and ISA cards
- •USB adapters
- •Modifying Wireless Network Adapters
- •Synchronizing and Internet Access
- •Wireless Zero Configuration with XP
- •Easy installation
- •Automatic network connections
- •Tracking Your Network’s Performance
- •Apple AirPort Hardware
- •Pick an AirPort Card, any card
- •Apple AirPort Software Updates
- •AirPort 2.0 software
- •AirPort 2.0.4 software
- •AirPort 2.0.5 software
- •AirPort 2.1.1 software
- •OS 9 Wireless Networks
- •Installing AirPort software on Mac OS 9
- •Upgrading AirPort Base Station firmware on OS 9
- •OS X Wireless Networks
- •Installing the AirPort software on OS X
- •Upgrading AirPort Base Station firmware on OS X
- •Adding another computer to your AirPort network on OS X
- •Connection sharing
- •Routers and gateways
- •Sharing dialup Internet connections
- •Obtaining an IP Address Automatically
- •Windows 9x
- •Windows 2000
- •Windows XP
- •Setting Up Internet Connection Sharing
- •Windows 98 SE and Windows Me
- •Windows 2000
- •Windows XP
- •Mac OS X v. 10.2 (Jaguar)
- •Assessing the Risks
- •General Internet security
- •Airlink security
- •How about a bit more about WEP?
- •What’s wrong with WEP?
- •Clamping Down on Your Wireless Home Network’s Security
- •Getting rid of the defaults
- •Enabling WEP
- •Closing your network
- •Looking into the Crystal Ball
- •Waiting for WPA
- •The future: 802.11i
- •A Networking Review
- •Basic networking terminology
- •Setting up a workgroup
- •Will You Be My Neighbor?
- •Sharing a document or folder on Windows 95/98/Me
- •Enabling sharing on Windows 2000/XP
- •Setting permissions
- •Accessing shared files
- •Be Economical: Share Those Peripherals
- •Setting up a print server
- •Sharing other peripherals
- •PC Gaming Hardware Requirements
- •Networking Requirements for PC Gaming
- •Console online gaming services and equipment
- •Console wireless networking equipment
- •Dealing with Router Configurations
- •Getting an IP address
- •Dealing with port forwarding
- •Setting Up a Demilitarized Zone (DMZ)
- •Wireless Home Entertainment Gear
- •Expanding Your Home Entertainment Center with Wireless Adapters
- •The Home Media Player
- •The Home Theater PC
- •Internet Content for Your Media Players and HTPCs
- •Making a Connection to Your Car
- •Your car’s path to wireless enlightenment
- •Synching your car stereo with home
- •Getting online with your own car PC
- •Picking wireless gear for your car
- •Using your PDA as a remote control
- •Whole home 802.11-based IR coverage
- •See me, feel me, hear me, touch me
- •Discovering Bluetooth Basics
- •Bluetooth Mobile Phones
- •Bluetooth PDAs
- •Other Bluetooth Devices
- •Printers
- •Digital cameras
- •Keyboards and meeses (that’s plural for mouse!)
- •Bluetooth adapters
- •Discovering Public Hot Spots
- •Freenets and open access points
- •For-pay services
- •Using T-Mobile Hot Spots
- •Using Wayport Hot Spots
- •Using Boingo Hot Spots
- •Tools for Finding Hot Spots
- •Netstumbler.com
- •Boingo
- •Check the Obvious
- •Move the Access Point
- •Move the Antenna(s)
- •Change Channels
- •Check for Dual-Band Interference
- •Check for New Obstacles
- •Install Another Antenna
- •Add a Signal Booster
- •Add a Repeater or Bridge
- •Check Your Cordless Phone Frequencies
- •Your Bath
- •Your Car
- •Your Exercise Gear
- •Your Home Appliances
- •Your Musical Instruments
- •Your Pets
- •Your Phones
- •Your Robots
- •Your Wearing Apparel
- •CNET.com
- •802.11 Planet
- •Broadband Wireless Exchange Magazine
- •80211b.weblogger.com
- •PC Magazine
- •Electronic House Magazine
- •Home Automation Magazine
- •Practically Networked
- •ExtremeTech.com
- •Network World
- •Other Cool Sites
- •Index
Chapter 10: Securing Your Wireless Home Network 195
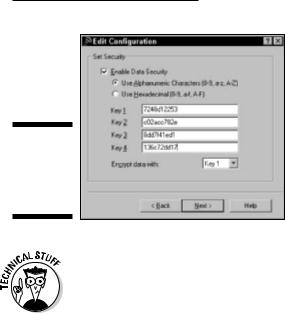
Figure 10-2:
Setting up
WEP on an
ORiNOCO
PC Card.
One area that is consistently confusing when setting up a WEP key — and often a real pain in the rear end — is the tendency of different vendors to use different formats for the keys. The most common way to format a key is to use hexadecimal (hex) characters. This format represents numbers and letters by using combinations of the numbers 0–9 and the letters A–F. (For example, the name of Pat’s dog, Opie, would be represented in hexadecimal as 4f 70 69 65.) A few other vendors use ASCII, which is simply the letters and numbers on your keyboard.
Although ASCII is an easier-to-understand system for entering WEP codes (it’s really just plain text), most systems make you use hexadecimal: It’s the standard. The easiest way to enter hex keys on your computers connecting to your access point is to use the pass phrase that we discuss previously. If your network adapter client software lets you do this, do it! If it doesn’t, try entering the WEP key itself that you wrote down when you generated it (it’s probably hexadecimal). If that doesn’t work either, you might have to dig into the user’s manual and see whether you need to add any special codes before or after the WEP key to make it work. Some software requires you to put the WEP key inside quotation marks; others might require you to put an 0h or 0x (that’s a zero and an h or an x character) before the key or an h after it (both without quotation marks).
Closing your network
The last step that we recommend you take in the process of securing your wireless home network (if your access point allows it) is to create a closed network — a network that allows only specific, pre-designated computers and devices onto it. You can do two things to close down your network, which makes it harder for strangers to find your network and gain access to it:

196 Part III: Installing a Wireless Network
Turn off SSID broadcast: By default, most access points broadcast their SSID out onto the airwaves. This makes it easier for users to find the network and associate with it. If the SSID is being broadcast and you’re in range, you should see the SSID on your computer’s network adapter client software and be able to select it and connect to it. That is, assuming that you have the right WEP key, if WEP is configured on that access point. When you create a closed network, you turn off this broadcast so that only people who know the exact name of the access point can connect to it.
You can find access points even if they’re not broadcasting their SSID (by observing other traffic on the network with a network sniffer program), so this is an imperfect security measure — and no substitute for enabling WEP. But it’s another layer of security for your network. Also, if you’re in an area where you will have a lot of people coming into your home and wanting to share your connection, you might not want to close off the network, thus balancing convenience for your friends against the small exposure of a more open network.
Set access control at the MAC layer: Every network adapter in the world has a unique number assigned to it known as a Media Access Controller (MAC) address. You can find the MAC address of your network adapter either by looking at it (it’s usually physically printed on the device) or using software on your computer:
•Open a DOS window and use the winipcnfg command in Windows 95/98/Me or the ipconfig/all command on Windows NT/2000/XP.
•Look in the Network Control Panel/System Preference on a Mac.
With some access points, you can type in the MAC addresses of all the devices that you want to connect to your access point and block connections from any other MAC addresses.
Again, if you support MAC layer filtering, you’ll make it harder for friends to log on to when visiting. If you’ve got some buddies who like to come over and mooch off your broadband connection, you’ll need to add their MAC addresses as well, or they won’t be able to get on your network. Luckily, you need to enter their MAC address only one time to get them “on the list,” so to speak, so you won’t need to do it every time they show up — at least until you have to reset the access point (which shouldn’t be that often).
Neither of these “closed” network approaches is absolutely secure. MAC addresses can be spoofed (imitated by a device with a different MAC address, for example), but both are good ways to add to your overall security strategy.
