
- •VOLUME 4
- •CONTRIBUTOR LIST
- •PREFACE
- •LIST OF ARTICLES
- •ABBREVIATIONS AND ACRONYMS
- •CONVERSION FACTORS AND UNIT SYMBOLS
- •HYDROCEPHALUS, TOOLS FOR DIAGNOSIS AND TREATMENT OF
- •HYPERALIMENTATION.
- •HYPERBARIC MEDICINE
- •HYPERBARIC OXYGENATION
- •HYPERTENSION.
- •HYPERTHERMIA, INTERSTITIAL
- •HYPERTHERMIA, SYSTEMIC
- •HYPERTHERMIA, ULTRASONIC
- •HYPOTHERMIA.
- •IABP.
- •IMAGE INTENSIFIERS AND FLUOROSCOPY
- •IMAGING, CELLULAR.
- •IMAGING DEVICES
- •IMMUNOLOGICALLY SENSITIVE FIELD–EFFECT TRANSISTORS
- •IMMUNOTHERAPY
- •IMPEDANCE PLETHYSMOGRAPHY
- •IMPEDANCE SPECTROSCOPY
- •IMPLANT, COCHLEAR.
- •INCUBATORS, INFANTS
- •INFANT INCUBATORS.
- •INFUSION PUMPS.
- •INTEGRATED CIRCUIT TEMPERATURE SENSOR
- •INTERFERONS.
- •INTERSTITIAL HYPERTHERMIA.
- •INTRAAORTIC BALLOON PUMP
- •INTRACRANIAL PRESSURE MONITORING.
- •INTRAOCULAR LENSES.
- •INTRAOPERATIVE RADIOTHERAPY.
- •INTRAUTERINE DEVICES (IUDS).
- •INTRAUTERINE SURGICAL TECHNIQUES
- •ION-EXCHANGE CHROMATOGRAPHY.
- •IONIZING RADIATION, BIOLOGICAL EFFECTS OF
- •ION-PAIR CHROMATOGRAPHY.
- •ION–SENSITIVE FIELD-EFFECT TRANSISTORS
- •ISFET.
- •JOINTS, BIOMECHANICS OF
- •JOINT REPLACEMENT.
- •LAPARASCOPIC SURGERY.
- •LARYNGEAL PROSTHETIC DEVICES
- •LASER SURGERY.
- •LASERS, IN MEDICINE.
- •LENSES, CONTACT.
- •LENSES, INTRAOCULAR
- •LIFE SUPPORT.
- •LIGAMENT AND TENDON, PROPERTIES OF
- •LINEAR VARIABLE DIFFERENTIAL TRANSFORMERS
- •LITERATURE, MEDICAL PHYSICS.
- •LITHOTRIPSY
- •LIVER TRANSPLANTATION
- •LONG BONE FRACTURE.
- •LUNG MECHANICS.
- •LUNG PHYSIOLOGY.
- •LUNG SOUNDS
- •LVDT.
- •MAGNETIC RESONANCE IMAGING
- •MAGNETOCARDIOGRAPHY.
- •MANOMETRY, ANORECTAL.
- •MANOMETRY, ESOPHAGEAL.
- •MAMMOGRAPHY
- •MATERIALS, BIOCOMPATIBILITY OF.
- •MATERIALS, PHANTOM, IN RADIOLOGY.
- •MATERIALS, POLYMERIC.
- •MATERIALS, POROUS.
- •MEDICAL EDUCATION, COMPUTERS IN
- •MEDICAL ENGINEERING SOCIETIES AND ORGANIZATIONS
- •MEDICAL GAS ANALYZERS
- •MEDICAL PHOTOGRAPHY.
- •MEDICAL PHYSICS LITERATURE
- •MEDICAL RECORDS, COMPUTERS IN
- •MICROARRAYS
- •MICROBIAL DETECTION SYSTEMS
- •MICROBIOREACTORS
- •MICRODIALYSIS SAMPLING
- •MICROFLUIDICS
- •MICROPOWER FOR MEDICAL APPLICATIONS
- •MICROSCOPY AND SPECTROSCOPY, NEAR-FIELD
- •MICROSCOPY, CONFOCAL
- •MICROSCOPY, ELECTRON
- •MICROSCOPY, FLUORESCENCE
- •MICROSCOPY, SCANNING FORCE
- •MICROSCOPY, SCANNING TUNNELING
- •MICROSURGERY
- •MINIMALLY INVASIVE SURGICAL TECHNOLOGY
- •MOBILITY AIDS
- •MODELS, KINETIC.
- •MONITORING IN ANESTHESIA
- •MONITORING, AMBULATORY.
- •MONITORING, FETAL.
- •MONITORING, HEMODYNAMIC
- •MONITORING, INTRACRANIAL PRESSURE
- •MONITORING, NEONATAL.
- •MONITORING, UMBILICAL ARTERY AND VEIN
- •MONOCLONAL ANTIBODIES
- •MOSFET.
- •MUSCLE ELECTRICAL ACTIVITY.
- •MUSCLE TESTING, REHABILITATION AND.
- •MUSCULOSKELETAL DISABILITIES.
American Roentgen Ray Society, 44211 Slatestone Court, Leesburg, VA 20176-5109 (http://www.arrs.org).
American Society for Therapeutic Radiology and Oncology, 12500 Fair Lakes Circle, Suite 375, Fairfax, VA 22033-3882 (http://www.astro.org).
British Institute of Radiology, 36 Portland Place, London, W1B 1AT, (http://www.bir.org.uk).
Health Physics Society, 1313 Dolley Madison Boulevard, Suite 402, McLean, Virginia 22101 (http://hps.org).
Institute of Physics and Engineering in Medicine (IPEM), Fairmount House, 230 Tadcaster Road, York, YO24 1ES, UK (http://www.ipem.ac.uk).
International Atomic Energy Agency, P.O. Box 100, Wagramer Strasse 5, A-1400 Vienna, Austria (http://www.iaea.org).
International Commission on Radiation Units and Measurements, Inc., ICRU, 7910 Woodmont Avenue, Suite 400, Bethesda, MD 20814-3095, USA (http:// www.icru.org).
International Commission on Radiological Protection, SE-171 16 Stockholm Sweden (Elsevier).
International Society for Magnetic Resonance in Medicine, 2118 Milvia Street, Suite 201, Berkeley, CA 94704, USA (http://www.ismrm.org).
International Society for Optical Engineering (SPIE), PO Box 10, Bellingham WA 98227-0010 USA (http:// spie.org).
National Council on Radiation Protection and Measurements, 7910 Woodmont Avenue, Suite 400, Bethesda, MD 20814-3095 (http://www.ncrponline. org).
Radiation Research Society, 10105 Cottesmore Court, Great Falls, VA 22066 (http://www.radres.org).
Radiological Society of North America, Inc., 820 Jorie Boulevard, Oak Brook, IL 60523-2251 (http://rsna.org).
Society of Nuclear Medicine, 1850 Samuel Morse Dr. Reston, VA 20190 (http://snm.org).
See also BIOMEDICAL ENGINEERING EDUCATION; MEDICAL EDUCATION,
COMPUTERS IN; MEDICAL ENGINEERING SOCIETIES AND ORGANIZATIONS.
MEDICAL RECORDS, COMPUTERS IN
YESHWANTH SRINIVASAN
BRIAN NUTTER
Texas Tech University
Lubbock, Texas
INTRODUCTION
Computers play a vital role in almost every aspect of modern medical science. If we begin with a primitive definition of a computer, as a system with a processor unit capable of performing arithmetic and logical operations and a memory unit to store programs and data, then almost every sophisticated piece of modern medical equipment comes with a computer. Most standard medical procedures [e.g., magnetic resonance imaging (MRI), computed tomo-
MEDICAL RECORDS, COMPUTERS IN |
351 |
graphy (CT), positron emission tomography (PET), ultrasonography] use computers to record and to process data. Computer-based medical records would seem a natural choice for documentation of the recorded data. Moreover, the association of this data with computers presents numerous advantages including easy and random access to the data by multiple distributed users, globally searchable databases, and automated batch processing. However, the use of computer-based medical records is not as prevalent in today’s medical community as one would expect. In this article, we explain the reasons for this anomaly, and we present methods to circumvent the problems associated with computer-based medical records and to allow medical practitioners to achieve the real potential of computerbased systems.
PAPER-BASED MEDICAL RECORD SYSTEMS
Medical records chronicle the transactions between healthcare professionals and their patients. They record every detail of a patient’s visit to a hospital, clinic, or office from the time of the patient’s arrival to the time the patient is discharged. Details recorded include the condition of the patient at the time of examination, procedures and medications administered to the patient, symptoms and observations, diagnoses and test results, together with the exact time of each relevant activity.
Traditionally, medical records have consisted of handwritten documents called charts. This remains the most prevalent form of recording patient information, especially in small hospitals and clinics. These charts typically record every piece of information that is judged potentially relevant to a patient’s case. When a patient visits a hospital or a primary care physician for the first time, a new chart is made, and the patient name and contact information are recorded on it. When the patient is discharged from the hospital, a discharge note is made on the chart. During subsequent visits, new charts are added. All patient charts are maintained in a labeled file bearing the patient’s name and other information to enable easy identification and retrieval.
However, paper-based records exhibit shortcomings in six important areas that are necessary to ensure adequate long-term care to patients and easy preservation of treatments administered.
1.Accessibility: Accessibility refers to the immediate availability of patient-related information at all times to all parties with a need to know. It is important to review a patient’s medical history before commencing any new treatment. If a patient decides to visit a specialist, emergency room, clinic, or hospital other than the primary care physician, a request may be made for the patient’s medical history to be faxed or couriered to the second facility. This information transfer may take between hours to days to complete, depending on the distance and arrangements between the two locations, available modes of communication, availability of authorized personnel to promptly respond to the request, and so on. During
352 MEDICAL RECORDS, COMPUTERS IN
emergencies, a delay of just a few minutes in administering the correct treatment to a patient could have very serious ramifications. A situation in which adverse reactions to particular medications known by a primary care physician simply are not made available in a timely fashion to emergency room personnel is all easy to imagine. The delay in disseminating accurate detailed background information is perhaps the biggest drawback of paper-based medical record systems.
2.Legibility: Paper-based records are generally handwritten documents, and one person’s handwriting is often not readily understood by another. The fact that entries may be made by many different people makes understanding a chart even more difficult. Furthermore, paper-based records are subject to wear and tear, accidental immersion in water or other liquids due to leaks, misfortune or negligence, smudging of ink, and so on. These factors lead to reduced legibility of the entries on the charts and consequently make interpreting the charts more subjective.
3.Bulkiness: Paper-based records for a single patient initially consist of just a few charts, but they can quickly become a thick file with subsequent visits. Assuming that a small clinic sees 10 new patients daily, that the physicians in the clinic take rotating holidays and that it is not a leap year, 3650 new files will be added over a period of 1 year. The files of many of the existing patients also become bulkier and subsequently occupy more space. All of this paper forces the addition of storage space in the clinic for these new records, even though the space could often be better utilized for clinical purposes through the addition of much more profitable and useful treatment or diagnostic capabilities.
4.Data Dimensionality: Data dimensionality refers to the ability to interpret the available information in multiple, complementary fashions. The data contained in paper-based records simply provide information about the medical history of a particular patient. In order to obtain trends, distributions or statistical patterns about a particular patient or even groups of people in a geographical area, the required information has to be manually compiled from each record. This can be extremely laborious and time consuming. Furthermore, even a simple text search for a particular word or phrase can take impractically long if the search must be conducted visually through paperbased handwritten records.
5.Integrity: A patient will have multiple medical files, maintained simultaneously at every hospital or clinic ever visited, yet none of these records contain the complete medical history of the patient. Usually, the patient’s primary care physician is the one who has the records that will provide the most accurate long-term information, and during times of emergency the primary care physician will frequently be the first one contacted for patient records. However, medical facilities rarely have in place any mechanism to update the primary care physician. If, for example, during a visit
to a specialist it was found that a patient was allergic to a particular class of medications, the primary care physician’s records will often not be updated to show this information. Even if the patient records from multiple sources were summoned, there will still remain a very realistic chance of missing one or more sources, leaving the completeness of paper-based records questionable. Paper-based systems also risk inadvertent loss or misfile of complete pages in copying, transporting, photocopying, faxing, and handling of records.
6.Replication: Paper-based medical records are prone to destruction by natural disasters, fires, leaks, and pests in storage areas. Because paper-based records are bulky, it is both expensive and tedious to replicate them and store back-up copies. Hence, if they are destroyed, patient medical histories can be completely lost.
Several research papers have been devoted to explaining the shortcomings of paper-based medical records (1,2). Nevertheless, paper-based records are still the most widely used method for maintaining patient information. The process of recording information in charts is a natural process of making notes, and it requires little specialized training. Once recorded, the information is relatively permanent and cannot be distorted easily. Furthermore, the chart often bears the signatures of both the patient and the appropriate medical personnel who treated the patient, which may be an important legal requirement. Such legal issues are a significant reason that many organizations resist wholesale changes to their paper-based record systems.
COMPUTER-BASED MEDICAL RECORD SYSTEMS
Paper-based records were the only method of storing patient medical information in use until 25 years ago. Since that time, computer technology has experienced exponential growth, creating endless possibilities for developments within allied fields. The fields of medicine in general and medical records in particular have been no exception. Computer-based records were introduced to overcome the inherent limitations and problems of paper-based records and to alter patient medical record keeping in order to incorporate advancements in computer technology. The computer-based medical record is commonly given several names within differing environments, including Computer-based Patient Record (CPR), Electronic Health Record (EHR), and Electronic Medical Record (EMR). Throughout this article, we will use the name computer-based patient record and the abbreviation CPR to refer to computer-based medical records. The CPRs are fundamental to the role of computers in medical records, and a significant portion of this article deals with them.
A CPR is an electronic patient record that resides in a computer-based information system. Such systems are often specifically designed to augment medical practitioners by providing accessibility to complete and accurate long-term data, alerts, reminders, clinical decision support
systems, links to medical knowledge databases, and other aids (3,4). The CPRs are essentially digital equivalents of paper-based records. Because this patient information is stored digitally, the enormous information processing and networking capabilities of computers can be utilized to drastically increase the efficacy of patient treatment. They easily overcome the shortcomings of paper-based records on the six key issues outlined in the previous section, and they provide several other fascinating features exclusive to them.
1.Accessibility: With the advent of the Internet and the World Wide Web, information on virtually any topic can be quickly and easily obtained. CPR databases can be stored in networked servers, which can be searched from any properly networked location. With properly designed databases and network systems, the complete medical history of a patient can be retrieved in a matter of seconds. This helps in ensuring the most prompt and accurate treatment possible, which is one of the fundamental reasons for maintaining a medical record.
2.Legibility: The information recorded on CPRs is presented using digitally reproduced fonts, which are then independent of the handwriting of the person entering the data into the system. Anytime patient information is required, it can be readily visualized on a viewing device, such as a CRT monitor or PDA, which does not introduce any wear and tear in the record itself. If a paper copy of a patient record is required for a particular activity, a new printout can be generated every time. Thus there is no subjective element in understanding the information.
3.Bulkiness: CPRs can be stored on a variety of media, including Compact Disc (CD), Digital Versatile Disc (DVD), and Hard Disk Drive (HDD). A single CD, 11.4 cm in diameter and weighing 15 g, can store 700 megabytes (MB) of data. This translates into >100,000 pages of raw text or two hundred 500-page books, which would occupy >10 m of shelf space. The DVDs have >10 times the density of CDs, and HDDs offer >100 times the information content of a CD. This means that with proper database design, all of the medical records of all of 1 year’s new patients at the aforementioned small clinic can now be stored on a single CD, and several years of patient data for all ongoing patient activities can be stored on just one DVD.
4.Data Dimensionality: Data on CPRs can be exploited and interpreted in many more ways than can a simple paper-based record. Entire databases can be subjected to automated search, and specific information from a single record or a collection of records can be retrieved in a matter of seconds. Trends and patterns in disease occurrence and treatment administration and effectiveness can readily be extracted and processed for limited or wide-ranging populations. Database Management System (DBMS) software can be used to plot the available information on graphs and pie charts, which greatly simplify the
MEDICAL RECORDS, COMPUTERS IN |
353 |
contents of medical records into a form that can be interpreted by laymen. All these operations can be done automatically using state-of-the-art software and require little, if any, human intervention. Techniques in data mining, for example, allow automated determination and analysis of data correlations among very large numbers of variables.
5.Integrity: CPRs are generally stored on local systems within hospitals, clinics, and physician offices, which means that medical records of a particular patient could be distributed across many systems throughout the world. Using modern networking techniques, these systems can be easily yet securely networked, and widely dispersed CPRs can be located and made available for inclusion in patient diagnosis and treatment. It would also be practical to develop a system in which all patient records are stored in a central repository, and any time new records of the patient are created or updated, they can be added to this central repository. Using either of these methods in a well-designed system, the complete medical history of a patient can be very rapidly retrieved from any of the authorized locations connected to the network.
6.Replication: Due to the high densities for computerized storage of data, CPRs occupy very little space when compared to paper-based systems. It is very easy and inexpensive to create back-up copies and to store these copies in geographically diverse locations. In a well-designed computer-based system with automated, networked backup, the complete medical history of every patient can still be retrieved even if a record storage facility is completely destroyed.
Exclusive Features of CPR
With considerable manual effort, the performance of paperbased records can be made comparable to that of CPRs within the six major requirements of a medical record outlined above. The efficiency advantages of computerbased medical record systems will nevertheless offer significant cost advantages over paper-based systems in achieving comparable performance levels. Significant improvements in patient treatment can result when CPRs are incorporated into expert systems and DBMS frameworks that engender an entirely new set of features for medical records.
1.Content-Based Data Retrieval: If a large hospital system is informed that a popular drug has been determined to cause serious side effects and that the manufacturer has consequently issued an immediate recall, the hospital system may hesitate to issue a broad public warning, because that action would lead to unnecessary panic and to patients flooding the system seeking confirmation on their prescriptions, even when their medications are completely unrelated to the recall. If the hospital maintained only paper-based records, it would take weeks to pore through patient charts to obtain the names
354 MEDICAL RECORDS, COMPUTERS IN
and locations of the patients to whom the drug was prescribed. Such a situation presents a perfect case for content-based data retrieval. With properly constructed CPRs, the same information can be much more rapidly retrieved through querying the database to fetch all patient records with the name of the recalled drug in the ‘Drugs Prescribed’ field. Then, only the patients who actually have been prescribed the recalled medication can be individually contacted with explicit instructions by a qualified staff member. This data search technique is known as ContentBased Data Retrieval (CBDR).
2.Automatic Scheduling: With CPR-based systems, routine periodic check-up or follow-up visits can be automatically scheduled, and e-mail reminders or automated telephone recordings can be sent directly to the patients. This automation will relieve healthcare professionals of a significant administrative burden.
3.Knowledge-Based Systems: Every physician attempts to solve a particular condition to the best of his limited knowledge (5). It is reported that there are >5,000,000 medical facts, which are constantly being appended, updated and questioned by over 30,000 medical journal publications each year (6). It is humanly impossible to remember all of these facts and to reproduce them accurately as needed. However, CPR databases all over the world can be rapidly and effectively searched in order to find information about patients who were previously diagnosed with the same condition, how they were treated and the end result. While the presiding doctor still makes the decisions and retains responsibility, he can have experimental evidence and experiential knowledge from other experts to assist his analysis (7). Diagnostic decision support systems like Quick Medical Reference (QMR) and Massachusetts General Hospital’s DXplain provide instant access to knowledge bases of diseases, diagnoses, findings, disease associations and lab information.
4.Expert Systems: Human errors in recording information can be greatly reduced by programming the data-entry interface to reject anomalous values
and to restrict the input to a finite set of possible choices. For example, a pulse rate of 300 beats min 1 would be highly unlikely. Potentially dangerous spelling mistakes in generating a prescription can be identified. Dates for follow-up activities can be checked against reasonable parameters. A welldesigned interface would prompt a message to recheck such entries.
5.In situ Data Access: A medical records system in which a physician accesses a wireless PDA while conversing with a patient could allow direct bidirectional communication between a physician and a pharmacy, a laboratory, or a specialist. Collaborators on a complex case can simultaneously access each other’s progress, even when the collaborators are geographically separated.
In 1991, the United States Institute Of Medicine (IOM) conducted a study on the advantages and disadvantages of CPRs and published its findings (3). The IOM concluded that CPRs greatly enhance the health of citizens and greatly reduce costs of care, and it called for widespread implementation of CPRs by 2001. However, 4 years past that deadline, widespread implementation still remains only a concept. Figures for CPR adoption rates in hospitals range from 3% to 21%, while CPR adoption rates for physician offices range from 20% to 25% (8). It is safe to say that these figures are not representative of the popularity that one would reasonably expect from the benefits of CPRs. The following section is devoted to explaining this anomaly.
ROADBLOCKS IN CPR IMPLEMENTATION
Recording and processing of information with CPRs requires installation of computer systems and software, and, in general, more training of healthcare professionals is required to get them acquainted with CPR systems than with paper-based record systems. Furthermore, realizing the full potential of CPR systems requires not only that patient records issued in the future should be CPRs but also that previously taken paper-based records should be converted into CPRs. Some of the important factors affecting this onerous large-scale conversion will now be discussed.
1.Cost: Expense is usually the major obstacle to the full-fledged incorporation of CPRs. Depending on whether the application is for the office of a single physician or for a large hospital, the basic infrastructure needed to establish a CPR system could vary from a single PC to a complete network of workstations and servers loaded with expensive network, database and records management software. Both hardware and software computer technologies become outmoded very quickly, and these technologies require constant update, increasing maintenance and operation costs. There is also a significant cost factor involved in hiring data-entry operators to convert existing paper-based records to CPRs and in training healthcare professionals to then operate the new systems and software. Although several studies have shown that CPRs are effective in the long run (9,10), both hospitals and physician offices remain apprehensive about investing many thousands of dollars on a new technology while the tried and tested paper-based records work reasonably effectively.
2.Abundance of Choices and Lack of Standards: There are > 100 CPR management software systems available in the market today, and additional entries arrive in the marketplace annually. Each software approach will have its advantages and disadvantages, and it is never easy to decide which one is best suited for a particular application. Furthermore, different software interfaces use different templates for the patient record, recording slightly different patient data within very different structures. A
standardized CPR format independent of the specific hardware and software running on a particular system is yet to be developed. This lack of standardization in CPR formats severely cripples cross-system interaction and comprehensive integration of CPR systems. The marketplace has, to date, failed to produce a clear market leader or an industrial body with the ability to enforce such standards. A customer contemplating a purchase and the subsequent investments in training and maintenance may have serious reservations concerning the ability to change from the products of one manufacturer to another.
3.Confidentiality: The United States government passed the Health Insurance Portability and Accountability Act (HIPAA) in 1996, protecting a patient’s right to confidentiality and specifying the information on a medical record that can be shared and the information that must be considered confidential. A record can be made available only on a ‘‘need to know’’ basis, wherein only personnel who absolutely need to know the data are granted access. For example, physicians participating in the diagnosis and treatment process of a specific patient are granted complete access to the entire medical record, while health agencies involved in conducting demographic studies are granted access only to information that does not and can not reveal the identity of the patient.
4.Security: In the case of paper-based records, it is relatively easy to control access and to ensure security by keeping those records under lock and key. The security of CPRs will be constantly threatened by hackers, trying to break into a system in order to retrieve confidential patient information. Unless properly protected, CPRs are also vulnerable to being compromised during transmission across a network. Unlike paper-based records, CPRs can be easily manipulated, intentionally or unintentionally, in fashions that do not appear obvious. These vulnerabilities represent an enormous security problem, and effective solutions are required before CPRs can be put to widespread use. Furthermore, efforts to provide network security have significant costs, requiring manpower, equipment, and frequent software upgrades.
5.Apprehension Among Patients: Even in developed countries like the United States, considerable uneasiness exists among patients about the use of computers to maintain patient medical records. While some of this phenomenon can be ascribed to the reluctance of the older generation in accepting new technology, the most important reason for this apprehension is the lack of clear understanding by patients about the benefits of CPRs. One of the easiest ways to overcome this fear is for healthcare professionals to directly reach out to the patients and explain the long-term advantages of CPRs.
6.Legal Issues: The validity of CPRs in a court of law is still questionable. The Millennium Digital Commerce Act, otherwise known as the Electronic Signature Act, was passed in 2000 (although the portion
MEDICAL RECORDS, COMPUTERS IN |
355 |
relating to records retention was passed in 2001). The act established that the electronic signature and electronic records cannot be denied legal effect simply because they are electronic and are not signed in ink on paper. However, legal implications in CPR transactions extend far beyond this act. For example, if it is found that the software system used to manage CPRs does not comply with stipulated security requirements, the validity of a CPR can be questioned in court, even if no indication of tampering can be identified. The CPR systems are also prone to computer viruses, worms and Trojans, which exploit loopholes in the computer security defenses to gain unauthorized access to sensitive data and/or to maliciously corrupt the information.
Despite significant progress toward overcoming these hurdles, complete transition from paper-based records to CPRs is a time-consuming and capital-intensive process, and during the midst of this transition, the benefits are unlikely to be immediately apparent. In the following section, some of the options available to healthcare professionals in implementing a CPR system, and several technologies available to ensure secure storage and transmission of confidential medical information are reviewed.
FEATURES OF CPR SYSTEMS
A complete CPR system can consist of individual workstations, data input devices (keyboards, mice, light pens, scanners, cameras), output devices (printers, plotters, and display monitors), Database Management System (DBMS) software, text, image and video processing hardware and software, and the networking infrastructure for intraand intersystem communication. The security and reliability requirements of these systems should never be understated. With so many factors involved, there is always room for improvement, and a universally perfect combination has yet to be implemented. Nevertheless, a wide variety of CPR systems have been successfully implemented, tested and put to everyday use, with most such systems working successfully in the environment for which they were designed. We will now explore some of the general features of CPR systems and their components, and we will present advantages and disadvantages of the choices available.
System Architecture
A fundamental decision that must be made before implementing a CPR system is the choice of the system architecture to be used. There are two broad choices, which we now discuss.
1.Centralized Architecture: A block schematic of a centralized architecture as implemented in CPR systems is shown in Fig. 1. A CPR system based on the centralized architecture has a central server that contains complete medical records of all patients in the system. Any modification to a record must be
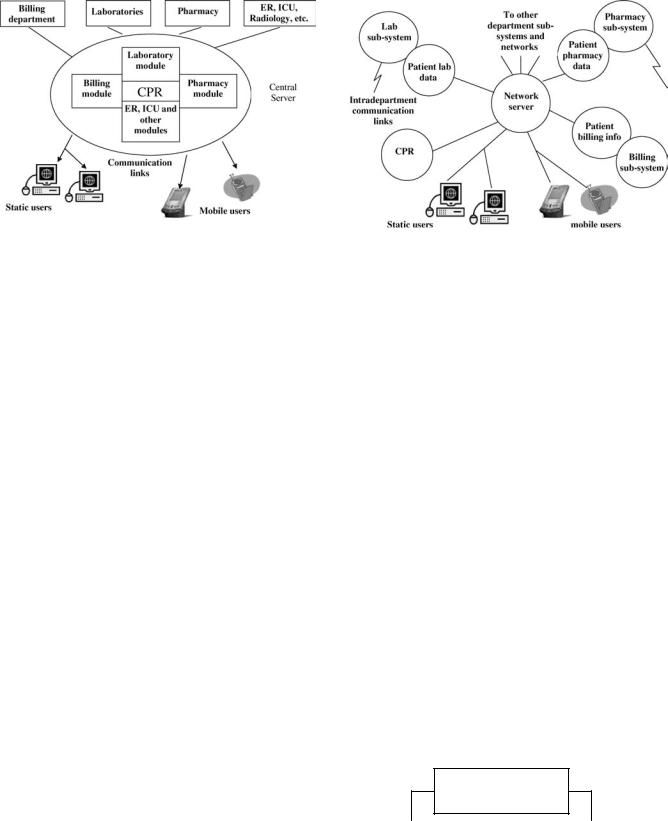
356 MEDICAL RECORDS, COMPUTERS IN
Figure 1. Centralized Architecture (Reprinted with permission from (The Computer-Based Patient Record: An Essential Technology for Health Care, Revised Edition) # (1997) by the National Academy of Sciences, courtesy of the National Academies Press, Washington, D.C.)
done to the CPR stored in this central repository to have any lasting effect. Communication links may be provided to other departments that will immediately communicate any new information to the server, thereby keeping the CPR on the central server fully updated. The principal advantage of this architecture lies in the immediate availability of the complete record for use elsewhere within the system. It is also easier to manage and to maintain the resources of the system, because they are located in one single location. However, a poorly designed system can be prone to server overloading, leading to delayed responses. Server or network failures can bring the system to a complete standstill, and if the data on the server is corrupted or destroyed, the medical record activity subsequent to system backup may be completely lost. These issues can be resolved, but the solutions can be expensive.
2.Distributed Architecture: The alternative to the centralized approach is the distributed architecture. A block schematic is shown in Fig. 2. In this approach, the load of the server is distributed among smaller subsystems, distributed through many departments. No department contains the complete medical record of all patients. The records are completed ‘‘on demand’’, that is, when a user at a system workstation must obtain complete information, the workstation sends requests to each individual subsystem, receives data back from them, and arranges them into a record. This system continues to function even if one or more of the subsystems become inoperative. However, the response time, defined as the time elapsed between the user request to fetch a record and the arrival of the complete record back to the requesting workstation, might become significant if even one of the subsystems is overloaded. The architecture also provides more opportunities for security breaches than the centralized approach. There may
Figure 2. Distributed Architecture (Reprinted with permission from (The Computer-Based Patient Record: An Essential Technology for Health Care, Revised Edition) # (1997) by the National Academy of Sciences, courtesy of the National Academies Press, Washington, D.C.)
also be difficulties related to each subsystem using different data structures to manage and to store records, making the design of an effective DBMS potentially quite complex. These issues have been successfully addressed in specific implementations of distributed CPR systems.
DBMS and Media Processing
The general components of a CPR are shown in Fig. 3. An ideal DBMS would be able to seamlessly integrate different media formats (text, images, three-dimensional (3D) models, audio and video). Four important types of DBMS commercially available are hierarchical, relational, textand object oriented. Each of these is better suited for one or more different media and system architectures than the others. Many modern CPR systems, especially those based on a distributed architecture, use a combination of commercial DBMSs or utilize a custom DBMS.
External information – data |
|
Non-text media – Electronic |
|
images, pictorials, video and |
|
generated outside the hospital (lab |
|
|
|
audio data |
|
measurements, referral letters |
|
|
|
(scanned documents, X-ray, CT, |
|
and ECG measurements) |
|
|
|
MRI, audio notes) |
|
|
|
|
|
|
|
CPR
Locally generated information – data generated in various departments of the hospital
Unformatted text – free text |
|
Formatted text – organized text |
(plans, findings and conclusions) |
|
(data in objective type fields) |
|
|
|
Figure 3. Components of a CPR.
An important aspect of a DBMS is the mechanism that it uses for data retrieval. The details of record construction can play a significant role in creation of databases that can be efficiently and accurately searched. Entries in formatted fields can be searched much more easily than scanned documents, images or nonformatted text. A DBMS should also provide organization of the data in a manner that is sensible and easy to comprehend. Well-organized databases will prove easier to manage and faster to search.
Security and Legal Issues
A core issue in the design of CPR systems is security. A single security breach could be used to access thousands of complete CPRs, which are then vulnerable to many malicious activities. Thus, it is extremely critical to protect individual CPRs from unauthorized access, as well as to protect the CPR system itself from hackers attempting to access the system or attempting to cause it to fail. In addition, the CPR data must be protected before it can be sent across a network, due to potential communication leaks that can land sensitive information in the wrong hands. Tools such as network packet sniffers are extremely powerful if an unauthorized party can achieve physical access to network interconnection hardware or cabling. In general, five conditions must be satisfied before patients or health care personnel are granted access to the records on a network (11):
1.The patient must not have recorded an explicit prohibition of CPR transmission across the network.
2.The patient must have consented to the transfer of the partial or complete CPR to the recipient institution.
3.The identity of the patient must be accurately verified and authenticated.
4. The |
identities |
of the healthcare provider and |
the |
recipient |
institution must be accurately |
verified. |
|
|
5.It must be verified that the patient is mentally competent. If the patient is found to be mentally incompetent, then the need for the patient record must be sufficiently urgent that if it is not made available immediately, serious harm could result to the patient’s health.
For a CPR produced by a CPR system to be a legally valid document, the CPR should be able to answer the following questions (12).
1.Who Wrote It? A single CPR is frequently handled by many different people, with several healthcare providers entering, updating, or removing information. A CPR must include the identities of all the people who have modified the record, together with the information that they have modified. This involves secure access control using smart cards, PINs, fingerprints, passwords, etc. to verify the identity of requestors before they will be allowed to access or to modify the information on the records.
MEDICAL RECORDS, COMPUTERS IN |
357 |
2.When Was It Written? Time and date information is maintained by automatically attaching timestamps to the CPRs. The system must be designed to ensure that unauthorized personnel cannot change the system time or any timestamp in any CPR.
3.What Does It Say? Computer technology is reinvented roughly every 5 years. Data storage and retrieval media become obsolete very quickly. For example, the magnetic tapes that were very popular 25 years ago can be found only in museums today. It is thus important for CPR systems to incorporate these technological developments, and yet not become outmoded too quickly, so that the contents of current CPRs and archived CPRs can both be read and processed to obtain the same information.
4.Has the Information Been Altered? Undocumented alteration of information will prove to be the most important legal issue, and hence, the most difficult one to solve. A CPR system must be designed to allow determination of whether the information is indeed as originally recorded or whether it has been subsequently modified in a manner that would affect possible legal proceedings. Several effective solutions, based on cryptographic techniques, exist.
A very reliable solution to ensure that a particular CPR provides answers to all of these four questions is to attach digital signatures to them. Just as an ink-based signature provides legal acceptability for paper-based records, digital signatures can ensure the legal acceptability of a CPR. Digital signatures offer both signatory and document authentication, and they have been proven to be more effective than the ink-based signature (13). Signer authentication provides the capability to identify the person who signed the document, while document authentication offers the capability to determine whether a document was altered after it was signed.
Digital signatures use public-key encryption schemes to provide this functionality. In public-key encryption schemes (14), every user gets a pair of keys: a public key, which everybody is allowed to know, and a private key, which is kept as a secret known only by the individual and the authority that issues and verifies the keys. A digital signature is computed using the data bytes of the document and both the private and public keys and attached to the document. Consider that person A creates a CPR and attaches a digital signature to it using his public and private keys. Anybody with access to A’s public key can verify that the CPR was actually created by A using the CPR, the digital signature and A’s public key. If the result is correct, according to a straightforward mathematical relationship, A is authenticated as the signatory of the CPR, and the CPR is authenticated as accurate. Any alteration of the CPR after the calculation and attachment of the digital signature would corrupt the digital signature and would then cause the CPR to be identifiable as modified. In this case, the CPR would be considered fraudulent, although the source of the fraud would not necessarily be identifiable.
358 MEDICAL RECORDS, COMPUTERS IN
Public-key encryption can also be used to secure CPRs before transmitting them across a network. Consider that person A desires to send a CPR to person B. Person A looks up the public key of B and encrypts the CPR using B’s public key. The CPR can only be decrypted using B’s private key. Since only B has access to his private key, only he can decrypt the CPR. The principle of public-key encryption can be extended to CPRs to protect the authenticity of the information, to identify malicious alterations of the CPR, and to secure transmission across a network.
POINTERS TO THE FUTURE
Much of this article has been devoted to explaining the benefits of the CPRs and the factors hindering their widespread implementation. Despite their tremendous potential, the development of commercial CPR systems has not reflected the progress made in many related fields in computer technology. In this section, some of these related technologies that, in the future, the authors feel will have great potential to broaden the range of advantages of computer-based medical record services and to make them sufficiently secure are presented.
Radio Frequency Identification Tags
Radio Frequency (RF) identification (RFID) refers to an automatic ID system that uses small RF devices to identify and to track individual people, pets, livestock, and commercial products. These systems are used to automatically collect highway tolls and to control access to buildings, offices and other nonpublic sites. An RFID tagging system includes the tags themselves, a device to write information to the tags, one or more devices to read the data from the tags, and a computer system with appropriate software to collect and to process information from the tag. Many applications can use the same devices to both read and write the RFID tags. While the physical layout of the tag may vary according to the application, its basic components will include an intelligent controller chip with some memory and an antenna to transmit and receive information. According to its power requirements, an RFID tag will be classified into one of two types. Active tags have their own power source and hence provide greater range. Passive tags will be powered by RF pulses from the tag reader (or writer) and thus exhibit no shelf life issues due to battery exhaustion.
While plans are underway to replace bar codes with RFID tags on virtually every single commercial product, the field of medical informatics has found some unique applications for RFID tags. The U.S. Food and Drug Administration (FDA) recently approved the implantation of RFID tags on humans (15). These tags are similar to the tags being used on animals, and they are implanted under the skin in the triceps area. The chip contains a 16-digit number that can be readily traced back to a database containing the patient’s information. One such chip made by VeriChip costs $125, exclusive of the cost of implantation. This technology is expected to be a boon to individuals with life-threatening medical conditions and to lower medical costs by reducing errors in medical treatment.
Testing of replacement of bar codes with RFID tags in patient bracelets is ongoing. Unlike bar codes, RFID tags do not require clear line of sight between the bar code and the bar code reader, nor do they require active operator intervention. This ensures that healthcare workers will not fail to scan a patient ID bracelet. One such successfully tested system is Exavera’s eShepherd, which combines RFID tags with Wireless Fidelity (Wi-Fi) networks and Voice over IP (VoIP) to implement a single system that will track patients, staff and hospital assets (16). The Wi-Fi routers can deliver patient information directly to a physician’s handheld PDA every time any RFID transceiver detects a patient. Physicians and hospital staff can have the patient information whenever and wherever they want, and they do not have to refer repeatedly to a secure physical filing area to retrieve patient records.
A major factor impeding widespread implementation of RFID tags is the legal and ethical issue of keeping such detailed records of people, their activities, and all the things they buy and use, without their consent. However, once this issue has been resolved, RFID tags will change the way patient records are processed.
Biometrics
Biometrics refers to automatic recognition of people based on their distinctive anatomical and behavioral characteristics including facial structure, fingerprint, iris, retina, DNA, hand geometry, signature, gait and even the chemical composition of sweat (17). Biometric systems have been used in wide ranging applications like user authentication before entry into buildings and offices, criminal investigation, and identification of human remains.
Biometric systems will also find an excellent application in management of medical records. Individual traits of people who are authorized to access the record can be stored along with the record. When the system receives a request from a user to retrieve the record, the system will attempt to match the biometrics of the user to the database of biometrics of all the people who are authorized to access the record. The record is fetched only if the match is positive. In this manner, a CPR can be viewed and modified only by authorized personnel. This is potentially an effective application for biometric systems, because the system can be trained with as many samples as needed from authorized personnel. Biometric system applications where a strong need exists to verify the authenticity of claimed membership in a preidentified population have been successfully tested with almost 100% accuracy. Such systems also offer a deterrent to would-be intruders because the biometric information associated with an unsuccessful access attempt can be retained and used to identify the intruder.
Generally, the biometric information of a user is encoded on a smart card that the user must use to gain access into the system. This provides a far better authentication solution than using just a user name and a password, because both of these can be forged fairly easily. Most current biometric systems are based on the uniqueness of human fingerprints, and systems based on more complicated biometric features are currently undergoing
investigation. The development of superior biometric systems holds the key to more secure CPR authentication.
Content-Based Image Retrieval
Content-Based Image Retrieval (CBIR) is the process of retrieving images from a database based on the degree of similarity in content between an example image (the query image) and the various images contained in the database. Traditional non-CBIR data retrieval mechanisms apply text-based methods, in which a string query is matched to user-generated descriptions of documents or to contents of specific fields in a record. When patient images are integrated into patient records, simple text-based searches will not serve the same purpose. Text descriptions of images are very subjective and require data entry by a knowledgeable user. If that same image is to be added to a different database, the accompanying description also must be added if the image is to be retrievable.
These techniques utilize both global properties, such as image statistics and color distributions, and local properties, such as position and texture, to retrieve images that appear ‘‘similar’’ to the query image. This is a powerful tool for physicians, because CBIR enables them to compare the image of a current patient (query image) to similar images of other patients in the database, to examine descriptions attached to those images in their corresponding CPRs, and to study the treatment administered in those cases, all in a matter of seconds.
More and more frequently, scanned documents such as referral letters and scanned paper-based records are being added to CPRs. These documents can be treated as images, and CBIR systems based on character recognition technologies can search for text descriptions on these documents, making these documents compatible with text-based searches. This technology can save a great deal of time, money and errors in converting historical or ongoing paper-based records to CPRs, because the records can simply be scanned and need not be entered again into the CPR system. As more and more visual aids are added to medical diagnostics, CBIR will become indispensable to CPR management.
Steganography and Watermarking
Steganography and cryptography are related but distinct methods that are used to ensure secure transmission and secure archival of information. In cryptography, messages are encrypted in such a manner that unauthorized recipients may not decrypt the messages easily, using long, secure passwords and complex mathematical algorithms to drastically alter the data. Often, however, the encrypted messages themselves may be obtained fairly easily, because they are transmitted over insecure networks and archived on insecure servers. In steganography, the very presence of secure information is masked by hiding that information inside a much larger block of data, typically an image.
If an oncologist wishes to get a second opinion from a gynecological specialist concerning a diagnosis of cervical cancer, he might elect to send a digital image of the cervix of the patient. He would also include his diagnosis, relevant
MEDICAL RECORDS, COMPUTERS IN |
359 |
patient details including other complications the patient may have, and a referral letter, all of which are sensitive and confidential information. The traditional method to send the supplemental information electronically would be to encrypt the information using public-key encryption techniques and to transmit it as separate files together with the image. If the transmission is intercepted by a malicious party seeking private data, the transmission would garner interest, because it would be quite obvious that any encrypted information following the image information would likely be related to that image. The data thief must still work to decrypt the transmission and to reveal the confidential information. Decryption itself is difficult without extensive computational capacity, but data thieves will often find getting the necessary password to be a much easier method to access the data. The disadvantage of encryption is that the data thief knows what to try.
An alternate data transmission method would use steganography. The sensitive information can be embedded in inconspicuous areas of the image (18). Thus, no additional information or files are transmitted, and the image will raise less suspicion that associated sensitive data can be located. Although the embedded data is computationally easier to decode than the encrypted messages, it will only be decoded by people with foreknowledge that there is information embedded in the image. Furthermore, the embedded data can be encrypted before it is embedded, so that the data thief has another level of barrier. The information is much more difficult to locate, and the thief still has to decrypt or to steal the password.
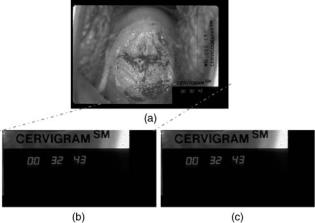
Usually, the clinically important sections of the image will be identified, and only the remaining regions will be used for embedding the secret information. Several sophisticated steganography techniques, like BPCS, ABCDE, and modified ABCDE (19–21) have been successfully implemented. These methods can hide significant amounts of information without clinically altering the image, although hiding too much data leaves evidence that can be detected mathematically using tools from the field of steganalysis. Figure 4 shows an example of data hiding using the
Figure 4. Steganography. (a) Original digital image of the cervix.
(b) Section of clinically unimportant segment of image in a. (c) Section in b encoded with secret information.
360 MEDICAL RECORDS, COMPUTERS IN
modified ABCDE scheme. Figure 4a is a digital image of a cervix, and Fig. 4b shows the bottom right section of this image, which contains no clinically important information. This section forms an 864 432 RGB image, which requires 1,119,744 bytes to represent directly or 295,727 bytes to represent when losslessly compressed to PNG format. Figure 4c is the section in Fig. 4b after 216,326 bytes of sensitive information have been embedded. This hidden data corresponds to >40 pages of pure text, at 5000 characters per page. Figure 4c visually appears very similar to the section in Fig. 4b, even with this extensive additional data embedded. An even more secure solution would encrypt the sensitive information before embedding it inside the carrier image. This way, even if steganalysis methods detected that the carrier image contains embedded information, the decryption problem still remains.
Watermarking techniques are similar to digital signatures in the sense that they can provide owner and document authentication for digital media. They are usually nonvisibly detectable signals embedded into the media that can be checked, by authorized personnel, to verify the validity of the media and to trace its copyright holders. Watermarking and steganography techniques can also be used to identify times, dates, locations, and information that could be used to cross-reference to a patient, so that misidentification or misfiling of image data under the wrong patient file can be detected and corrected. It is the opinion of the authors that both these technologies will provide valuable solutions for secure CPR systems.
CONCLUDING REMARKS
This article attempted to provide a brief overview of the applications of computers in medical records, the benefits of computerization, and issues concerning widespread deployment of computer-based medical record systems. The computerization of medical records is a vast area of research, employing many people from diverse fields of medicine, science and engineering. While we have attempted to summarize and present the material from our own perspective, the topic itself is explored in great detail by several worthy publications. There are literally thousands of publications that attempt to explain or to solve one or more of the issues presented in this article and to provide much greater detail than is possible in this article. Thus, the authors felt it appropriate to leave the reader with a few resources, both in print and on the World Wide Web (WWW), to obtain more information about computers in medical records.
Much of the material in this article has been inspired from the extensive discussions in Refs. 3 and 22. These books provide interesting observations and refer to a wealth of references that pioneered the computer revolution in the medical field. Two more recent books, (23 and 24), also provide excellent insight into the various aspects of using computers to manage medical records. The WWW contains many websites that provide solid insight into various aspects of medical records management. Ref. 6 is one such site that is constantly updated with information
about upgrading to CPR systems, cost benefit calculators, software vendor surveys, and from basic tutorials on every aspect of CPR management. Refs. 25 and 26 provide excellent evaluations of commercially available software for CPR management.
ACKNOWLEDGMENT
The authors would like to thank Mr. Rodney Long at the U.S. National Library of Medicine, Bethesda, Maryland, for providing the images of the cervix used in the example on steganography.
BIBLIOGRAPHY
1.Shortliffe EH. The evolution of electronic medical records. Acad Med 1999;74(4):414–419.
2.Burnum JF. The misinformation era: The fall of the medical record. Ann Intern Med 1989;110:482–484.
3.Dick RS, Steen EB, Detmer DE, editors. Institute of Medicine. The Computer-Based Patient Record—An Essential Technology for Health Care. Washington (DC): National Academy Press; 1997.
4.Shortliffe EH, Perreault LE, Fagan LM, Wiederhold G. Medical Informatics Computer Applications in Health Care and Biomedicine. 2nd ed. New York: Springer-Verlag; 2000.
5.Covell DG, Uman GC, Manning PR. Information needs in office practice: Are they being met? Ann Intern Med 1985; 103:596–599.
6.Voelker KG. (None). Electronic Medical Records [online]. http://www.emrupdate.com. Accessed 2005, April 10.
7.Weed LL. Medical records that guide and teach. New Engl J Med 278(11):593–600 and 278(12):652–657.
8.Brailer DJ, Terasawa EL. Use and adoption of computerbased patient records, California Healthcare Foundation report, Oct. 2003, ISBN 1-932064-54-0.
9.Wang SJ, et al. A cost-benefit analysis of electronic medical records in primary care. Am J Med Apr 1 2003;114(5):397–403.
10.Classen DC, Pestonik SL, Evans RS, Burke JP. Computerized surveillance of adverse drug events in hospital patients. J Am Med Assoc 1991;266:2847–2851.
11.David MR, et al. Maintaining the confidentiality of medical records shared over the Internet and the World Wide Web. Ann Intern Med 1992;127(2):138–141.
12.Cheong I. The legal acceptability of an electronic medical record. Aust Fam Phys Jan. 1997;26(1).
13.Askew RA. Understanding Electronic Signatures [online]. Real Legal. Available at http://www.reallegal.com/downloads/pdf/ ESigAskewWhitePaper.pdf. Accessed 2005. April 10.
14.Dent AW, Mitchell CJ. User’s Guide to Cryptography and Standards. Boston: Artech House; 2004.
15.Sullivan L. FDA approves RFID tags for humans. Inform Week Oct. 2004.
16.Collins J. RFID remedy for medical errors. RFID J May 2004.
17.Jain AK, et al. Biometric: A grand challenge. IEEE Conference on Pattern Recognition, Vol. 2; Aug. 2004. pp 935–26.
18.Johnson NF, Duric Z, Jajodia S. Information hiding: Steganography and Watermarking—Attacks and Countermeasures. Norwell (MA): Kluwer Academic; 2001.
19.Kawaguchi E, Eason RO. Principle and Applications of BPCS-Steganography. Proc SPIE Int Symp Voice, Video Data Communications; 1998.
20.Hirohisa H. A Data Embedding Method Using BPCS Principle With New Complexity Measures. Proc Pacific Rim Workshop on Digital Steganography. July 2002; p 30–47.
