
- •Acknowledgments
- •Introduction
- •Assessment Test
- •Answers to Assessment Test
- •Service Provider Networks
- •Scalability
- •Traffic Engineering
- •Quality of Service
- •MPLS Label Stack
- •Shim Header
- •MPLS Architecture
- •Control
- •Forwarding
- •MPLS Label Switching
- •MPLS Network Components
- •Device Output
- •Label-Switched Paths
- •MPLS Applications
- •MPLS and ATM
- •Overlay
- •Quality of Service
- •Traffic Engineering
- •Summary
- •Exam Essentials
- •Key Terms
- •Review Questions
- •Answers to Review Questions
- •Routing Review
- •Frame-Mode MPLS Working Example
- •Network Routing Protocol Examples
- •MPLS Step by Step
- •Label Distribution
- •Assigning Labels
- •Troubleshooting and Verification
- •Device Configuration
- •IGP Verification
- •CEF Verification
- •MPLS Verification
- •Label Distribution and Bindings
- •Binding Verification
- •Troubleshooting the Network
- •Hiding Service Provider Devices
- •Summary
- •Exam Essentials
- •Key Terms
- •Review Questions
- •Answers to Review Questions
- •Frame-Mode MPLS and ATM
- •Frame-Mode MPLS and ATM Configuration
- •Cell-Mode MPLS
- •Label Binding with ATM
- •Cell-Mode Label Switching
- •VC Merge
- •Loop Prevention
- •Cell-Mode MPLS Configuration
- •Summary
- •Exam Essentials
- •Key Terms
- •Review Questions
- •Answers to Review Questions
- •VPNs 101
- •Point-to-Point Connections
- •Virtual Private Networks
- •Categories of VPNs
- •VPN Routing
- •Peer-to-Peer VPNs
- •Optimal Routing
- •Peer-to-Peer Security
- •Peer-to-Peer VPN Routing
- •Summary
- •Exam Essentials
- •Key Terms
- •Review Questions
- •Answers to Review Questions
- •Service Provider Configuration
- •MPLS VPNs
- •Virtual Router
- •Virtual Routing and Forwarding Tables
- •MPLS Operational Overview
- •MP-BGP Configuration
- •An MPLS VPN Example
- •Route Distinguisher
- •MP-IBGP Configuration Example
- •Initial Network Configuration
- •MP-IBGP Configuration
- •Verification
- •Summary
- •Exam Essentials
- •Key Terms
- •Review Questions
- •Answers to Review Questions
- •A Review of VPNs
- •Configuring a Simple MPLS VPN
- •Configuring VRF Interfaces
- •Running RIP in an MPLS VPN
- •Configuring RIPv2 with Address-Family ipv4
- •Configuring Redistribution
- •Route Targets
- •Configuring Route Targets
- •A Review of Simple VPN Configuration
- •Configuring MPLS in the Service Provider Network
- •Simple VPN Configuration
- •Configuring the PE-CE Routing Protocol
- •Lab: Configuring an MPLS VPN
- •Configuring POP Routers
- •VPN Configuration
- •Raleigh Running-Config
- •Atlanta Running-Config
- •Peer 1 Running-Config
- •Peer 2 Running-Config
- •Verification with Ping
- •Routing Table Isolation
- •Verifying VRF Routes
- •Summary
- •Exam Essentials
- •Key Terms
- •Review Questions
- •Answers to Review Questions
- •MP-BGP and OSPF
- •A Review of OSPF
- •OSPF Router Types
- •Link State Advertisements
- •OSPF for MPLS VPNs
- •OSPF Super-Backbone
- •Preventing Routing Loops
- •Path Selection
- •MPLS VPN OSPF Lab
- •Summary
- •Exam Essentials
- •Key Terms
- •Review Questions
- •Answers to Review Questions
- •Static Routing
- •Device Configuration
- •VPN Configuration
- •Raleigh Running-Config
- •Atlanta Running-Config
- •Peer Router Configuration
- •Verification with Ping
- •Verifying Static VRF Routes
- •E-BGP and MPLS VPNs
- •Device Configuration
- •E-BGP Operation
- •AS-Override
- •VPN Configuration
- •Raleigh Running-Config
- •Atlanta Running-Config
- •Peer Router Configuration
- •Peer 1 Running-Config
- •Peer 2 Running-Config
- •Verification with Ping
- •Advanced MPLS VPN Topologies
- •Simple VPNs
- •Central Services MPLS VPN Topology
- •Overlay MPLS VPN Topology
- •Summary
- •Exam Essentials
- •Key Terms
- •Review Questions
- •Answers to Review Questions
- •Challenge Lab 1
- •MPLS
- •MP-IBGP
- •Answer to Lab 1.1
- •Answer to Lab 1.2
- •Answer to Lab 1.3
- •Challenge Lab 2
- •Tag Switching
- •MP-IBGP
- •Answer to Lab 2.1
- •Answer to Lab 2.2
- •Answer to Lab 2.3
- •Challenge Lab 3
- •VRF Configuration
- •RIPv2
- •Redistribution
- •Answer to Lab 3.1
- •Answer to Lab 3.2
- •Answer to Lab 3.3
- •Challenge Lab 4
- •VRF Configuration
- •OSPF
- •Redistribution
- •Answer to Lab 4.1
- •Answer to Lab 4.2
- •Answer to Lab 4.3
- •Challenge Lab 5
- •VRF Configuration
- •Static Routes and Redistribution
- •Answer to Lab 5.1
- •Answer to Lab 5.2
- •Challenge Lab 6
- •VRF Configuration
- •E-BGP Configuration
- •Answer to Lab 6.1
- •Answer to Lab 6.2
- •Service Provider Network Configuration with OSPF
- •Router Configuration
- •Routing Tables
- •Tags
- •Service Provider Network Configuration with IS-IS
- •Router Configuration
- •Routing Tables
- •Tag Switching Forwarding Tables
- •Glossary
168 Chapter 5 MPLS VPNs
An MPLS VPN Example
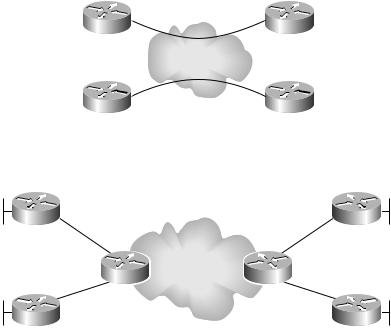
As with everything in MPLS, the best way to understand MPLS VPNs is with an example. Let’s begin with a business scenario. Customer A has one location in Atlanta and a second location in Raleigh. Customer B also has one location in Atlanta and a second location in Raleigh. Currently, both Customer A and Customer B have their sites connected with an overlay VPN, as illustrated in Figure 5.8. Note on this figure that Customer A1 refers to Customer A’s site in Atlanta, Customer B1 refers to Customer B’s site in Atlanta, Customer A2 refers to Customer A’s site in Raleigh, and Customer B2 represents Customer B’s site in Raleigh.
Customer A has requested an MPLS VPN to connect its two sites. Customer B has also requested an MPLS VPN. Figure 5.9 illustrates the new topology for both Customer A and Customer B.
F I G U R E |
5 . 8 |
Customer A and Customer B sites connected with an overlay VPN |
||||||
|
|
|
Customer A1 |
|
Customer A2 |
|||
|
|
10.1.0.0/16 |
|
|
Virtual circuit (VC) |
|
|
10.2.0.0/16 |
|
|
|
|
|
|
|||
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Customer B1 |
Virtual circuit (VC) |
Customer B2 |
|||
F I G U R E |
5 . 9 |
10.1.0.0/16 |
|
|
|
|
|
10.2.0.0/16 |
|
|
|
|
|
||||
|
|
|
|
|
||||
|
|
|
|
|
||||
New topology for an MPLS VPN for Customer A and Customer B |
||||||||
|
|
10.1.0.0/16 |
|
|
|
10.2.0.0/16 |
||
|
|
Customer A1 |
|
|
Customer A2 |
|||
|
|
|
Atlanta |
|
|
Raleigh |
||
|
|
10.1.0.0/16 |
|
|
|
10.2.0.0/16 |
||
|
|
Customer B1 |
|
|
Customer B2 |
|||
Notice in Figure 5.9 how this new topology looks like a shared router peer-to-peer VPN.
Copyright ©2002 SYBEX, Inc., Alameda, CA |
www.sybex.com |

An MPLS VPN Example 169
VRF
On the Atlanta and Raleigh PE routers in Figure 5.9, the first requirement in configuring an MPLS VPN is to create a VRF for each customer. VRF names are case-sensitive and are somewhat complex to manage in large environments. For simplicity, we’ll create a VRF for Customer A and call it VPN_A. For Customer B, we’ll use the name VPN_B. From global configuration mode, the ip vrf vpn_name command will be used. Notice after the execution of the ip vrf vpn_name command how the prompt changes:
Atlanta#config t
Atlanta(config)#ip vrf VPN_A
Atlanta(config-vrf)#
Route Distinguisher
The next thing you must configure for VRF VPN_A is a mandatory parameter called the route distinguisher (RD). A route distinguisher is a 64-bit value that is used to keep possibly overlapping addresses from actually doing so in MP-IBGP. Whenever a route is redistributed from the VRF into MP-IBGP, the route distinguisher is pre-pended to the 32-bit Network Layer Reachability Information (NLRI), producing a new 96-bit VPNv4 address.
If the route distinguisher has not been configured, the newly created VRF will
not be saved in the running configuration.
When configuring the route distinguisher, it’s important to note that the first 16 bits (called the high-order bits) are reserved to specify the extended BGP community type. Therefore, there are 48 bits that you use to specify the route distinguisher. The route distinguisher can be entered in two ways: 16-bit:32-bit or 32-bit:16-bit.
Although both formats are valid, the official recommendation is to use the 16-bit:32-bit method. The first 16 bits should be the service provider autonomous system (AS) number, and the second 32 bits should be a significant number of the service provider’s choosing. If the 32-bit:16-bit method is used, the first 32 bits should be an IP address, and the remaining 16 bits should be a significant number of the service provider’s choosing.
To configure the route distinguisher, use the rd command as follows:
Atlanta(config-vrf)#rd #:#
Copyright ©2002 SYBEX, Inc., Alameda, CA |
www.sybex.com |

170 Chapter 5 MPLS VPNs
To illustrate the importance of the route distinguisher, suppose the networks for Customer A and Customer B were set up by the same consultant, and the consultant used the 10.0.0.0 private address space for each customer. Both Customer A and Customer B use the same 10.1.0.0 /16 addresses in Atlanta. In Raleigh, both customers use the address 10.2.0.0 /16. With an overlay VPN, overlapping customer addresses were not an issue for the service provider. However, with the advent of peer-to-peer routing and MPLS VPNs, overlapping customer addresses are carried by the service provider and can cause routing problems. The route distinguisher fixes this problem.
As you can see in Table 5.3, without a route distinguisher, these routes would overlap in MP-BGP.
T A B L E 5 . 3 Overlapping Addresses
Atlanta |
Customer A |
10.1.0.0 /16 |
Atlanta |
Customer B |
10.1.0.0 /16 |
Raleigh |
Customer A |
10.2.0.0 /16 |
Raleigh |
Customer B |
10.2.0.0 /16 |
|
|
|
Let’s resume the configuration of the VRF using the following commands:
Atlanta#config t
Atlanta(config)#ip vrf VPN_A
Atlanta(config-vrf)#rd 1:1
Atlanta(config-vrf)#exit
Atlanta(config)#ip vrf VPN_B
Atlanta(config-vrf)rd 1:2
Raleigh#config t
Raleigh(config)#ip vrf VPN_A
Raleigh(config-vrf)#rd 1:1
Raleigh(config-vrf)#exit
Raleigh(config)#ip vrf VPN_B
Raleigh(config-vrf)rd 1:2
With the route distinguishers configured, the addresses will not overlap in MP-BGP. When customer routes are redistributed into MP-BGP to transit
Copyright ©2002 SYBEX, Inc., Alameda, CA |
www.sybex.com |

An MPLS VPN Example 171
the service provider backbone, the route distinguisher value is prepended to the NLRI, as you can see in Table 5.4.
T A B L E 5 . 4 Overlapping Addresses with Route Distinguisher
Atlanta |
Customer A |
1:1:10.1.0.0 /16 |
Atlanta |
Customer B |
1:2:10.1.0.0 /16 |
Raleigh |
Customer A |
1:1:10.2.0.0 /16 |
Raleigh |
Customer B |
1:2:10.2.0.0 /16 |
|
|
|
Now let’s add a little more detail. As mentioned earlier, VRF names are casesensitive. The following configuration is possible but not recommended:
Atlanta#config t
Atlanta(config)#ip vrf VPN_A
Atlanta(config-vrf)#rd 1:1
Atlanta(config-vrf)#exit
Atlanta(config)#ip vrf VPN_B
Atlanta(config-vrf)rd 1:2
Raleigh#config t
Raleigh(config)#ip vrf vpn_a
Raleigh(config-vrf)#rd 1:1
Raleigh(config-vrf)#exit
Raleigh(config)#ip vrf vpn_b
Raleigh(config-vrf)rd 1:2
As you see in the preceding example, the VRF names in Raleigh and Atlanta are different (VRF names are case-sensitive), but everything works just fine. This is because VRF names are only locally significant (the VRF names are only applicable on the router they’re configured on). It is important not to give the VRF name too much weight because it is just a name. For example, the following configuration works as well:
Atlanta#config t
Atlanta(config)#ip vrf VPN_A
Atlanta(config-vrf)#rd 1:1
Atlanta(config-vrf)#exit
Copyright ©2002 SYBEX, Inc., Alameda, CA |
www.sybex.com |

172 Chapter 5 MPLS VPNs
Atlanta(config)#ip vrf VPN_B
Atlanta(config-vrf)rd 1:2
Raleigh#config t
Raleigh(config)#ip vrf VPN_1
Raleigh(config-vrf)#rd 1:1
Raleigh(config-vrf)#exit
Raleigh(config)#ip vrf VPN_2
Raleigh(config-vrf)rd 1:2
Since this is such an important concept, let’s look at one more example just to make sure you understand the use of the VRF name:
Atlanta#config t
Atlanta(config)#ip vrf VPN_A
Atlanta(config-vrf)#rd 1:1
Atlanta(config-vrf)#exit
Atlanta(config)#ip vrf VPN_B
Atlanta(config-vrf)rd 1:2
Raleigh#config t
Raleigh(config)#ip vrf JAMES
Raleigh(config-vrf)#rd 1:1
Raleigh(config-vrf)#exit
Raleigh(config)#ip vrf KEVIN
Raleigh(config-vrf)rd 1:2
All that the ip vrf vpn_name command does is create a VRF for the customer. It’s important to have a naming convention (that takes into account case-sensitivity) to make management easier as more VRFs are added to support more VPNs.
VRF names are case-sensitive and locally significant. Don’t read too much into
them; it’s only a name.
Now that you understand VRF naming, you need to learn more about the route distinguisher. The purpose of a route distinguisher is to keep possibly overlapping addresses from doing so in global MP-IBGP.
Copyright ©2002 SYBEX, Inc., Alameda, CA |
www.sybex.com |

An MPLS VPN Example 173
Will the following configuration work?
Atlanta#config t
Atlanta(config)#ip vrf VPN_A
Atlanta(config-vrf)#rd 1:1
Atlanta(config-vrf)#exit
Atlanta(config)#ip vrf VPN_B
Atlanta(config-vrf)rd 1:2
Raleigh#config t
Raleigh(config)#ip vrf vpn_a
Raleigh(config-vrf)#rd 1:3
Raleigh(config-vrf)#exit
Raleigh(config)#ip vrf vpn_b
Raleigh(config-vrf)rd 1:4
Before you answer the question, let’s discuss it further. The only thing a route distinguisher does is keep customer routes unique in MP-IBGP. Look at Table 5.5. Do the routes overlap in global MP-BGP? The answer is No. (Remember, No is good; you don’t want overlapping addresses in MP-BGP.) This configuration is valid.
T A B L E 5 . 5 Addresses with Route Distinguisher
Atlanta |
Customer A |
1:1:10.1.0.0 /16 |
Atlanta |
Customer B |
1:2:10.1.0.0 /16 |
Raleigh |
Customer A |
1:3:10.2.0.0 /16 |
Raleigh |
Customer B |
1:4:10.2.0.0 /16 |
|
|
|
A route distinguisher is the closest thing to a VPN identifier that exists. When configuring a VRF, it does not become active nor does it stay in configuration until a route distinguisher is configured.
Let’s look at one more example. Does the following configuration work?
Atlanta#config t
Atlanta(config)#ip vrf VPN_A
Atlanta(config-vrf)#rd 1:1
Atlanta(config-vrf)#exit
Copyright ©2002 SYBEX, Inc., Alameda, CA |
www.sybex.com |

174 Chapter 5 MPLS VPNs
Atlanta(config)#ip vrf VPN_B
Atlanta(config-vrf)rd 1:2
Raleigh#config t
Raleigh(config)#ip vrf vpn_a
Raleigh(config-vrf)#rd 1:2
Raleigh(config-vrf)#exit
Raleigh(config)#ip vrf vpn_b
Raleigh(config-vrf)rd 1:1
Although your first reaction might be that it does not work, consider this question in further detail: What is the purpose of a route distinguisher? To keep possible overlapping IP address from doing so in MP-IBGP. Look at Table 5.6. Do the addresses overlap in MP-IBGP? The answer is No.
(Remember, No is good.) The preceding configuration is valid.
T A B L E 5 . 6 Addresses with Route Distinguisher
Atlanta |
Customer A |
1:1:10.1.0.0 /16 |
Atlanta |
Customer B |
1:2:10.1.0.0 /16 |
Raleigh |
Customer A |
1:3:10.2.0.0 /16 |
Raleigh |
Customer B |
1:4:10.2.0.0 /16 |
|
|
|
For simple VPNs such as this example, each customer requires a unique route distinguisher. To support complex topologies, each VRF may require a unique route distinguisher. Only one route distinguisher can be configured per VRF; you can’t have two VRFs on the same router using the same route distinguisher. For this reason, a route distinguisher is generally regarded as a locally significant VPN identifier.
After all of this configuration, the VPN is still not yet completely configured. In the next chapter, we’ll complete this configuration and discuss routing protocols in MPLS. Make sure that you’re familiar with the configuration and concepts presented in this chapter. Once you get to Chapter 6, you’ll be hammered on routing protocols and MPLS VPNs. Be sure you’re ready.
Copyright ©2002 SYBEX, Inc., Alameda, CA |
www.sybex.com |
