
Network Plus 2005 In Depth
.pdf
172 |
Chapter 4 NETWORK PROTOCOLS |
NET+ |
TFTP (Trivial File Transfer Protocol) |
2.10TFTP (Trivial File Transfer Protocol) is another TCP/IP Application layer protocol that enables file transfers between computers, but it is simpler (or more trivial) than FTP. A significant difference between FTP and TFTP is that TFTP relies on UDP at the Transport layer. Its use of UDP means that TFTP is connectionless and does not guarantee reliable delivery of data. Also, TFTP does not require users to log on to the remote host with an ID and password in order to gain access to a directory and transfer files. Instead, when you enter the TFTP command, your computer issues a simple request to access the host’s files. The remote host responds with an acknowledgment, and then the two computers begin transferring data. Each time a packet of data is transmitted to the host, the local workstation waits for an acknowledgment from the host before issuing another packet. In this way, TFTP overcomes some of the limitations of relying on a connectionless Transport layer protocol. A final difference between FTP and TFTP is that the latter does not allow directory browsing. In FTP, you can connect to a host and navigate through all the directories you’ve been granted access to view.
TFTP is useful when you need to load data or programs on a diskless workstation. For example, suppose a TFTP server holds Microsoft Excel. When a client issues a TFTP request for that program, the server would transmit the program files to the workstation’s memory. After the user completes his Excel work, the program files would be released from his workstation’s memory. In this situation, the fact that TFTP does not require a user to log on to a host is an advantage. It makes the transfer of program files quick and easy. As you can imagine, however, not requiring a login also presents a security risk, so TFTP servers must be carefully placed and monitored on a network.
NTP (Network Time Protocol)
NTP (Network Time Protocol) is a simple Application layer protocol used to synchronize the clocks of computers on a network. NTP depends on UDP for Transport layer services. Although it is simple, it is also important. Time is critical in routing to determine the most efficient path for data over a network. Time synchronization across a network is also important for timestamped security methods and maintaining accuracy and consistency between multiple storage systems. NTP is a protocol that benefits from UDP’s quick, connectionless nature at the Transport layer. NTP is time-sensitive and cannot wait for the error checking that TCP would require.
NNTP (Network News Transport Protocol)
Another Application layer protocol in the TCP/IP suite is NNTP (Network News Transport Protocol), which facilitates the exchange of newsgroup messages between multiple servers and users. A newsgroup is similar to e-mail, in that it provides a means of conveying messages; it differs from e-mail in that it distributes messages to a wide group of users at once rather than from one user to another. Newsgroups have been formed to discuss every conceivable topic, such as political issues, professional affiliations, entertainment interests, or sports clubs. To join a newsgroup, a user subscribes to the server that hosts the newsgroup. From that point forward, the user receives all messages that other newsgroup members post to the group. To
TCP/IP |
Chapter 4 173 |
NET+ |
send a message to the group, a user only has to address the message to the newsgroup’s e-mail |
2.10address.
Newsgroups require news servers that act as a central collection and distribution point for newsgroup messages. News servers are organized hierarchically across the Internet, similar to the way DNS servers are organized. Clients can use e-mail, Internet browsers, or special newsgroup reading software to receive newsgroup messages. NNTP supports the process of reading newsgroup messages, posting new messages, and transferring news files between news servers.
NET+ PING (Packet Internet Groper)
4.1PING (Packet Internet Groper) is a utility that can verify that TCP/IP is installed, bound to
4.2the NIC, configured correctly, and communicating with the network. It is often employed simply to determine whether a host is responding (or “up”). PING uses ICMP services to send echo request and echo reply messages that determine the validity of an IP address. These two types of messages work in much the same way that sonar operates. First, a signal, called an echo request, is sent out to another computer. The other computer then rebroadcasts the signal, in the form of an echo reply, to the sender. The process of sending this signal back and forth is known as pinging.
You can ping either an IP address or a host name. For example, to determine whether the www.loc.gov site is responding, you could type: ping www.loc.gov and press Enter. Alternately, you could type: ping 140.147.249.7 (the IP address of this site at the time this book was written) and press Enter. If the site is operating correctly, you would receive a response that includes multiple replies from that host. If the site is not operating correctly, you will receive a response indicating that the request timed out or that the host was not found. You could also get a “request timed out” message if your workstation is not properly connected to the network, or if the network is malfunctioning. Figure 4-16 gives examples of a successful and an unsuccessful ping test.
By pinging the loopback address, 127.0.0.1, you can determine whether your workstation’s TCP/IP services are running. By pinging a host on another subnet, you can determine whether the problem lies with a connectivity device between the two subnets.
For example, suppose that you have recently moved your computer from the Accounting Department to the Advertising Department, and now you cannot access the Web. The first test you should perform is pinging the loopback address. If that test is successful, then you know that your workstation’s TCP/IP services are running correctly. Next, you might try pinging your neighbor’s machine. If you receive a positive response, you know that your network connection is working. You should then try pinging a machine on another subnet that you know is connected to the network—for example, a computer in the IT department. If this test is unsuccessful, you can safely conclude that you do not have the correct settings in your TCP/IP configuration or that something is wrong with your network’s connectivity (for example, a router may be malfunctioning).

174 Chapter 4 NETWORK PROTOCOLS
NET+
4.1
4.2
FIGURE 4-16 Output from successful and unsuccessful PING tests
As with other TCP/IP commands, PING can be used with a number of different options, or switches, and the syntax of the command may vary depending on the operating system. But a ping command always begins with the word “ping” followed by a hyphen (-) and a switch, followed by a variable pertaining to that switch. Below are some useful PING switches:
-?—Displays the help text for the ping command, including its syntax and a full list of switches.
-a—When used with an IP address, resolves the address to a host name.
-n—Allows you to specify a number of echo requests to send. For example, if you
wanted to ping the Library of Congress site with only two echo requests (rather than the standard four that a Windows operating system uses), you could type the following command: ping -n 2 www.loc.gov.
-r—When used with a number from 1 to 9, displays the route taken during ping hops.
To view the proper syntax and a list of switches available for PING, type ping at the command prompt on a Windows-based computer or at the shell prompt on a UNIX-type system.
IPX/SPX |
Chapter 4 175 |
IPX/SPX (Internetwork Packet
Exchange/Sequenced Packet Exchange)
NET+ |
IPX/SPX (Internetwork Packet Exchange/Sequenced Packet Exchange) is a protocol orig- |
2.4inally developed by Xerox, then modified and adopted by Novell in the 1980s for its NetWare network operating system. IPX/SPX is required to ensure the interoperability of LANs running NetWare versions 3.2 and lower and can be used with LANs running higher versions of the NetWare operating system. On versions 5.0 and higher of NetWare, IPX/SPX has been replaced by TCP/IP as the default protocol. You will probably only use IPX/SPX if your clients must connect with older NetWare systems. To ensure interoperability, other operating systems can use IPX/SPX. Microsoft’s implementation of IPX/SPX is called NWLink.
IPX/SPX, like TCP/IP, is a combination of protocols that reside at different layers of the OSI Model. Also like TCP/IP, IPX/SPX carries network addressing information, so it is routable.
The IPX and SPX Protocols
The core protocols of IPX/SPX provide services at the Transport and Network layers of the OSI Model. As you might guess, the most significant core protocols are IPX and SPX.
IPX (Internetwork Packet Exchange) operates at the Network layer of the OSI Model and provides logical addressing and internetworking services, similar to IP in the TCP/IP suite. Like IP, IPX also uses datagrams to transport data and its datagrams also contain source and destination addresses. Furthermore, IPX is a connectionless service because it does not require a session to be established before it transmits, and it does not guarantee that data will be delivered in sequence or without errors. In summary, it is an efficient subprotocol with limited capabilities. All IPX/SPX communication relies upon IPX, however, and upper-layer protocols handle the functions that IPX cannot perform.
SPX (Sequenced Packet Exchange) belongs to the Transport layer of the OSI Model. It works in tandem with IPX to ensure that data are received whole, in sequence, and error free. SPX, like TCP in the TCP/IP suite, is a connection-oriented protocol and therefore must verify that a session has been established with the destination node before it will transmit data. It can detect whether a packet was not received in its entirety. If it discovers a packet has been lost or corrupted, SPX will resend the packet.
The SPX information is encapsulated by IPX. That is, its fields sit inside the data field of the IPX datagram. The SPX packet, like the TCP segment, contains a number of fields to ensure data reliability. An SPX packet consists of a 42-byte header followed by 0 to 534 bytes of data. An SPX packet can be as small as 42 bytes (the size of its header) or as large as 576 bytes.
Addressing in IPX/SPX
Just as with TCP/IP-based networks, IPX/SPX-based networks require that each node on a network be assigned a unique address to avoid communication conflicts. Because IPX is the
176 |
|
|
Chapter 4 NETWORK PROTOCOLS |
|
|
||||
|
|
|
|
|
|
|
component of the protocol that handles addressing, addresses on an IPX/SPX network are |
||
NET+ |
|
|
||
2.4called IPX addresses. IPX addresses contain two parts: the network address (also known as the external network number) and the node address.
Maintaining network addresses for clients running IPX/SPX is somewhat easier than maintaining addresses for TCP/IP-based networks, because IPX/SPX-based networks primarily rely on the MAC address for each workstation. To begin, the network administrator chooses a network address when installing the (older) NetWare operating system on a server. The network address must be an 8-bit hexadecimal address, which means that each of its bits can have a value of either 0–9 or A–F. An example of a valid network address is 000008A2. The network address then becomes the first part of the IPX address on all nodes that use the particular server as their primary server.
NOTE
The address 00000000 is a null value and cannot be used as a network address. The address FFFFFFFF is a broadcast address and also cannot be assigned as a network address.
The second part of an IPX address, the node address, is by default equal to the network device’s MAC address. Because every network interface card should have a unique MAC address, no possibility of duplicating IPX addresses exists under this system (unless MAC addresses have been manually altered). In addition, the use of MAC addresses means that you need not configure addresses for the IPX/SPX protocol on each client workstation. Instead, they are already defined by the NIC. Adding a MAC address to the network address example used previously, a complete IPX address for a workstation on the network might be 000008A2:0060973E97F3.
NetBIOS and NetBEUI
NET+ |
NetBIOS (Network Basic Input Output System) is a protocol originally designed for IBM |
2.4to provide Transport and Session layer services for applications running on small, homogenous networks. Early versions of NetBIOS did not provide a standard Transport layer specification, and networks that used NetBIOS were not necessarily compatible. However, when Microsoft adopted IBM’s NetBIOS as its foundation protocol it added a standard Transport layer component called NetBEUI (the NetBIOS Enhanced User Interface), pronounced, “net-bóo-ee”.
On small networks, NetBEUI is an efficient protocol that consumes few network resources, provides excellent error correction, and requires little configuration. It can support only 254 connections, however, and does not allow for good security. Furthermore, because NetBEUI frames include only Data Link layer (or MAC) addresses and not Network layer addresses, it is not routable. On the other hand, because NetBEUI does not use Network layer headers and
NETBIOS AND NETBEUI |
Chapter 4 177 |
NET+ |
trailers, it can operate more efficiently. If necessary, NetBEUI can be encapsulated by other |
2.4protocols, such as TCP/IP, then routed, but in many cases, the preferred method would be to migrate a NetBEUI network to a network running TCP/IP. Thus, this protocol is not suitable for large networks.
Today, NetBEUI might be used in very small Microsoft-based networks to integrate legacy clients. In newer Microsoft-based networks, TCP/IP is the protocol of choice because it is more flexible and scalable than NetBEUI. In fact, with its release of the Windows XP operating system, Microsoft has discontinued its support of NetBEUI. However, the company will provide the necessary tools to communicate with clients that still use NetBEUI and cannot be easily migrated to TCP/IP.
Addressing in NetBEUI
In case you do need to integrate older NetBEUI clients, you should understand how this protocol addresses clients. You have learned that NetBIOS does not contain a Network layer and therefore cannot be routed. To transmit data between network nodes, however, NetBIOS needs to reach each workstation. For this reason, network administrators must assign a NetBIOS name to each workstation. The NetBIOS name can consist of any combination of 16 or fewer alphanumeric characters (the only exception is that you cannot begin a NetBIOS name with an asterisk). Once NetBIOS has found a workstation’s NetBIOS name, it will discover the workstation’s MAC address and then use this address in further communications with the workstation. For example, a valid NetBIOS name is MY_COMPUTER.
TIP
On networks running both TCP/IP and NetBIOS, it is simplest to make the NetBIOS name identical to the TCP/IP host name.
NET+ WINS (Windows Internet Naming Service)
2.13WINS (Windows Internet Naming Service) provides a means of resolving NetBIOS names to IP addresses. WINS is used exclusively with systems that use NetBIOS—therefore, it only appears on Windows-based systems. With fewer and fewer networks relying on NetBIOS, however, WINS is becoming less common.
A computer’s NetBIOS name and its TCP/IP host name are different entities, though you can choose to use the same name for the NetBIOS name as you use for the TCP/IP name. Earlier, you learned that DNS provides resolutions of TCP/IP host names and IP addresses. WINS, on the other hand, provides resolution of NetBIOS names and IP addresses. Essentially, WINS has the same relationship to NetBIOS as DNS has to TCP/IP. That is, both WINS and DNS associate names with IP addresses.
178 |
|
|
Chapter 4 NETWORK PROTOCOLS |
|
|
||||
|
|
|
|
|
|
|
WINS is an automated service that runs on a server. In this sense, it resembles DHCP. WINS |
||
NET+ |
|
|
||
2.13may be implemented on servers running Windows NT Server, Windows 2000 Server, or Windows Server 2003. It maintains a database on the server that accepts requests from Windows or DOS clients to register with a particular NetBIOS name. Note that WINS does not assign names or IP addresses, but merely keeps track of which NetBIOS names are linked to which IP addresses.
A distinct advantage to using WINS is that it will guarantee that a unique NetBIOS name is used for each computer on a network. It can also be integrated with DHCP to combine IP address assignment and NetBIOS-to-IP address association. Finally, WINS can offer better network performance because as WINS manages the mappings between IP addresses and NetBIOS names, clients do not have to broadcast their NetBIOS names to the rest of the network. The elimination of this broadcast traffic improves network performance.
Every client workstation that needs to register with the WINS server must know how to find the server. Thus the WINS server cannot use a dynamic IP address (such as one assigned by a DHCP server). Instead, a specific IP address must be assigned to the WINS server. A client’s WINS server address is designated in the same way as its other TCP/IP properties.
AppleTalk
NET+ |
Businesses and institutions involved in art or education, such as advertising agencies, elemen- |
2.4tary schools, and graphic designers, often use Apple Macintosh computers. AppleTalk is the protocol suite originally designed to interconnect Macintosh computers. Although AppleTalk was meant to support peer-to-peer networking among Macintoshes, it can be routed between network segments and integrated with NetWare-, UNIX-, Linux-, or Microsoft-based networks. Still, it remains impractical for use on large networks. This is just one reason that AppleTalk, as with IPX/SPX and NetBEUI, has been replaced by TCP/IP. An overview of AppleTalk’s characteristics is presented here, in case you have to integrate older, AppleTalkreliant devices with your network.
An AppleTalk network is separated into logical groups of computers called AppleTalk zones. Each network can contain multiple zones, but each node can belong to only one zone. AppleTalk zones enable users to share file and printer resources on each other’s Macintoshes. Zone names are not subject to the same strict naming conventions that TCP/IPand IPX/SPXbased networks must follow. Instead, zone names typically describe a department or other group of users who share files. For example, a zone could be named “Sales and Marketing.”
In addition to zone names, AppleTalk uses node IDs and network numbers to identify computers on a network. An AppleTalk node ID is a unique 8-bit or 16-bit number that identifies a computer on an AppleTalk network. AppleTalk assigns a node ID to each workstation when the workstation first connects to the network. The ID is randomly chosen from a group of currently available addresses. Once a device has obtained an address, it stores it for later use.
BINDING PROTOCOLS ON A WINDOWS XP WORKSTATION |
Chapter 4 179 |
NET+ |
An AppleTalk network number is a unique 16-bit number that identifies the network to which |
2.4a node is connected. Its use allows nodes from several different networks to communicate. AppleTalk addressing is simple because it allows you to identify a group of shared addresses from the server. When clients attach to that server they pick up an address, thus eliminating the need to configure addresses on each workstation.
Binding Protocols on a
Windows XP Workstation
NET+ |
The protocols you install will depend on which operating system you are running. This section |
3.2describes how to bind a protocol suite on a Windows XP client workstation. No equivalent procedure exists on a UNIXor Linux-based computer, because UNIX and Linux only support the TCP/IP protocol suite, and the TCP/IP protocols are automatically bound to the network interface(or interfaces).
Core Network and Transport layer protocols are normally included with your computer’s operating system. When enabled, these protocols attempt to bind with the network interfaces on your computer. Binding is the process of assigning one network component to work with another. You can manually bind protocols that are not already associated with a network interface. For optimal network performance, you should bind only those protocols that you absolutely need. For example, a Windows Server 2003 server will attempt to use bound protocols in the order in which they appear in the protocol listing until it finds the correct one for the response at hand. If not all bound protocols are necessary, this approach wastes processing time.
Normally, a workstation running the Windows XP operating system would, by default, have the TCP/IP protocol bound to its network interfaces. The following exercise shows you how to install the NWLink IPX/SPX/NetBIOS Compatible Transport protocol (which is not, by default, bound to interfaces) on a Windows XP workstation:
1.Log on to the workstation as an Administrator.
2.Click Start, then click My Network Places. The My Network Places window appears.
3.From the Network Tasks list, click View network connections. The Network Connections window appears.
4.Right-click the icon that represents your network adapter, and click Properties in the shortcut menu. The network adapter’s Properties dialog box appears.
5.Click Install…. The Select Network Component Type dialog box appears.
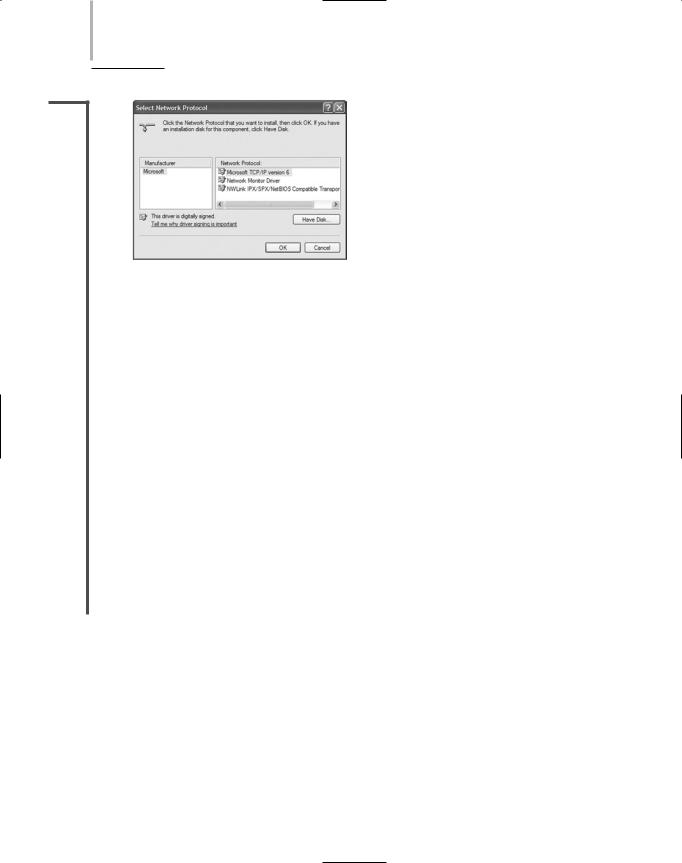
6.From the list of network components, select Protocol, then click Add…. The Select Network Protocol dialog box appears, as shown in Figure 4-17.
180 Chapter 4 NETWORK PROTOCOLS
NET+
3.2
FIGURE 4-17 The Windows XP Select Network Protocol dialog box
7.Select NWLink IPX/SPX/NetBIOS Compatible Transport Protocol, then click OK.
8.Wait a moment while Windows XP adds the protocol to the network components already bound to your NIC. Your network adapter Properties dialog box appears, now with the NWLink NetBIOS and the NWLink IPX/SPX/ NetBIOS Compatible Transport protocols listed under the “This connection uses the following items:” heading.
9.Click Close to save your changes, then close the Network Connections window.
On a Windows XP workstation, you can install any other protocol in the same manner as you installed the NWLink protocol.
It is possible to bind multiple protocols to the same network adapter. In fact, this is necessary on networks that use more than one type of protocol. In addition, a workstation may have multiple NICs, in which case several different protocols might be bound to each NIC. What’s more, the same protocol may be configured differently on different NICs. For example, let’s say you managed a NetWare server that contained two NICs and provided both TCP/IP and IPX/SPX communications to many clients. Using the network operating system’s protocol configuration utility, you would need to configure TCP/IP separately for each NIC. Similarly, you would need to configure IPX/SPX separately for each NIC. If you did not configure the protocols for each NIC separately, clients would not know which NIC to address when sending and receiving information to and from the server.
Chapter Summary
Protocols define the standards for communication between nodes on a network. The term protocol can refer to a group, or suite, of individual protocols that work together to accomplish data translation, data handling, error checking, and addressing.
Protocols vary by transmission efficiency, utilization of resources, ease of setup, compatibility, and ability to travel between one LAN segment and another. Protocols that can span more than one LAN are routable, which means they carry Network layer addressing information that can be interpreted by a router.

CHAPTER SUMMARY |
Chapter 4 181 |
TCP/IP is the most popular protocol suite, because of its low cost, open nature, ability to communicate between dissimilar platforms, and the fact that it is routable. It is a de facto standard on the Internet and is commonly the protocol of choice on LANs.
TCP (Transmission Control Protocol) belongs to the Transport layer of the OSI Model. TCP is a connection-oriented subprotocol; it requires a connection to be established between communicating nodes before it will transmit data. TCP provides reliability through checksum, flow control, and sequencing information.
UDP (User Datagram Protocol), like TCP, is a Transport layer protocol. UDP is a connectionless service and offers no delivery guarantees. But UDP is more efficient than TCP and useful in applications that require fast data transmission, such as videoconferencing.
IP (Internet Protocol) belongs to the Network layer of the OSI Model and provides information about how and where data should be delivered.
ARP (Address Resolution Protocol) belongs to the Network layer of the OSI Model. It obtains the MAC (physical) address of a host, or node, then creates a local database that maps the MAC address to the host’s IP (logical) address. RARP (Reverse Address Resolution Protocol) performs the opposite function; it maps IP addresses to MAC addresses.
In IPv4, each IP address is a unique 32-bit number, divided into four octets (or bytes). Every IP address contains two types of information: network and host.
All nodes on a Class A network share the first octet of their IP numbers, a number between 1 and 126. Nodes on a Class B network share the first two octets, and all their IP addresses begin with a number between 128 and 191. Class C network IP numbers share the first three octets, with their first octet being a number between 192 and 223.
Although computers read IP addresses in binary form, humans usually read them in dotted decimal notation, in which a decimal number represents each octet and every number is separated by a period.
A subnet mask is a 32-bit number that indicates whether and how a network has been subnetted—that is, subdivided into multiple smaller networks—and indicates the difference between network and host information in an IP address. Subnetting is implemented to control network traffic and conserve a limited number of IP addresses.
IP addresses assigned manually are called static IP addresses; however, using static IP addresses allows for the possibility of assigning the same address to more than one device.
Dynamic IP address assignment can be achieved using BOOTP or the more sophisticated DHCP. DHCP, though not foolproof, will essentially eliminate duplicateaddressing problems.
