
- •Icons Used in This Book
- •Network Security
- •Vulnerabilities
- •Threats
- •Types of Attacks
- •Network Security Policy
- •AVVID and SAFE
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Firewall Technologies
- •Cisco PIX Firewall
- •Foundation Summary
- •The Cisco Secure PIX Firewall
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Overview of the Cisco PIX Firewall
- •Cisco PIX Firewall Models and Features
- •Foundation Summary
- •System Maintenance
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Accessing the Cisco PIX Firewall
- •Installing a New Operating System
- •Upgrading the Cisco PIX OS
- •Creating a Boothelper Diskette Using a Windows PC
- •Auto Update Support
- •Password Recovery
- •Foundation Summary
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •How the PIX Firewall Handles Traffic
- •Address Translation
- •Translation Versus Connection
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Access Modes
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •TurboACL
- •Object Grouping
- •Advanced Protocol Handling
- •Foundation Summary
- •Syslog
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •How Syslog Works
- •How Log Messages Are Organized
- •How to Read System Log Messages
- •Disabling Syslog Messages
- •Foundation Summary
- •Cisco PIX Firewall Failover
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •What Causes a Failover Event
- •What Is Required for a Failover Configuration
- •Failover Monitoring
- •Stateful Failover
- •LAN-Based Failover
- •Foundation Summary
- •Virtual Private Networks
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Overview of VPN Technologies
- •Cisco VPN Client
- •PPPoE Support
- •Foundation Summary
- •Scenario
- •Completed PIX Configurations
- •PIX Device Manager
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •PDM Overview
- •PIX Firewall Requirements to Run PDM
- •Foundation Summary
- •Content Filtering with the Cisco PIX Firewall
- •“Do I Know This Already?” Quiz
- •Filtering Java Applets
- •Filtering ActiveX Objects
- •Filtering URLs
- •Foundation Summary
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Overview of AAA and the Cisco PIX Firewall
- •Cisco Secure Access Control Server (CSACS)
- •Foundation Summary
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Specifying Your AAA Servers
- •Troubleshooting Your AAA Setup
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Multimedia Support on the Cisco PIX Firewall
- •Attack Guards
- •PIX Firewall’s Intrusion Detection Feature
- •ip verify reverse-path Command
- •Foundation Summary
- •Answers to the “Do I Know This Already?” Quizzes and Q&A Questions
- •Chapter 1
- •Chapter 2
- •Chapter 3
- •Chapter 4
- •Chapter 5
- •Chapter 6
- •Chapter 7
- •Chapter 8
- •Chapter 9
- •Chapter 10
- •Chapter 11
- •Chapter 12
- •Chapter 13
- •Chapter 14
- •Chapter 15
- •Appendix B
- •What’s Wrong with This Picture?

C H A P T E R 3
The Cisco Secure PIX Firewall
This chapter discusses the Cisco PIX Firewall in greater detail. It covers the many different models available, including their design and specifications.
How to Best Use This Chapter
Chapter 2, “Firewall Technologies and the Cisco PIX Firewall,” gave you insight into the different firewall technologies and the functionality designed into the Cisco PIX Firewall. This chapter gives you more-specific information about this functionality and how this makes the PIX a truly high-performance solution. This chapter also covers all the PIX models available today and the possible configurations of each model. It is very important for you to understand the technology that powers the Cisco PIX Firewall in great detail. Test yourself with the “Do I Know This Already?” quiz and see how familiar you are with the PIX in general and with the specifics of each available model.
“Do I Know This Already?” Quiz
The purpose of this quiz is to help you determine your current understanding of the topics covered in this chapter. Write down your answers and compare them to the answers in Appendix A. If you have to look at any references to correctly answer the questions about the PIX functionality, you should read that portion and double-check your thinking by reviewing the Foundation Summary. It is a good idea to be familiar with the different PIX models, their purpose, and their available options. The concepts in this chapter are the foundation of much of what you need to understand to pass the CSPFA Certification Exam. Unless you do exceptionally well on the “Do I Know This Already?” pretest and are 100% confident in your knowledge of this area, you should read through the entire chapter.
1What is the ASA, and how does the Cisco PIX Firewall use it?
2What three authentication methods can the PIX Firewall use when performing cutthrough proxy?
3Why does the ASA generate random TCP sequence numbers?

24 Chapter 3: The Cisco Secure PIX Firewall
4If a user has successfully authenticated but cannot establish a connection to the server, what is most likely the problem?
5What is the best way to remove the ASA from a PIX Firewall?
6What components of a TCP session does the ASA write to the state table?
7What can cause a session object to be deleted from the state table?
8What are the three ways to initiate a cut-through proxy session?
9What happens to a reply that does not have the correct TCP sequence number?
10How many interfaces does a PIX 501 have, and how many network segments does it support?
11What X509 certificates do all PIX firewalls support?
12What is the maximum throughput of the PIX 535?
13How many interfaces can you install in a PIX 515?
14What is the lowest model number of the PIX Firewall family to support failover?
15What are three methods of managing a Cisco PIX Firewall?

Overview of the Cisco PIX Firewall 25
Foundation Topics
Overview of the Cisco PIX Firewall
As discussed in Chapter 2, the design of the Cisco PIX Firewall provides some significant advantages over application-based firewalls. Having a single operating environment allows the device to operate more efficiently, and because it was designed with security in mind, it is not vulnerable to any known exploits.
Adaptive Security Algorithm (ASA)
A key part of the operating environment is the Adaptive Security Algorithm (ASA). The ASA is more secure and efficient than packet filtering and provides better performance than application-type proxy firewalls. The ASA segregates the network segments connected to the firewall, maintains secure perimeters, and can control traffic between those segments. The firewall’s interfaces are assigned security levels. The PIX can allow outbound traffic to pass from an interface with a higher security level (inside) to an interface with a lower security level (outside) without an explicit rule for each resource on the higher-level segment. Traffic that is coming from an interface with a lower security level destined for an interface with a higher security level must meet the following two requirements: A static translation must exist for the destination, and an access list or conduit must be in place to allow the traffic.
The ASA is designed to function as a stateful, connection-oriented process that maintains session information in a state table. Applying the security policy to the state table controls all traffic passing through the firewall. The ASA writes the connection information to the state table as an outbound connection is initiated. If the connection is allowed by the security policy, the request goes out. Return traffic is compared to the existing state information. If the information does not match, the firewall drops the connection. The security emphasis on the connection rather than on the packets makes it nearly impossible to gain access by hijacking a TCP session.
Figure 3-1 and the following list explain the mechanics of how ASA and stateful filtering work on the PIX:
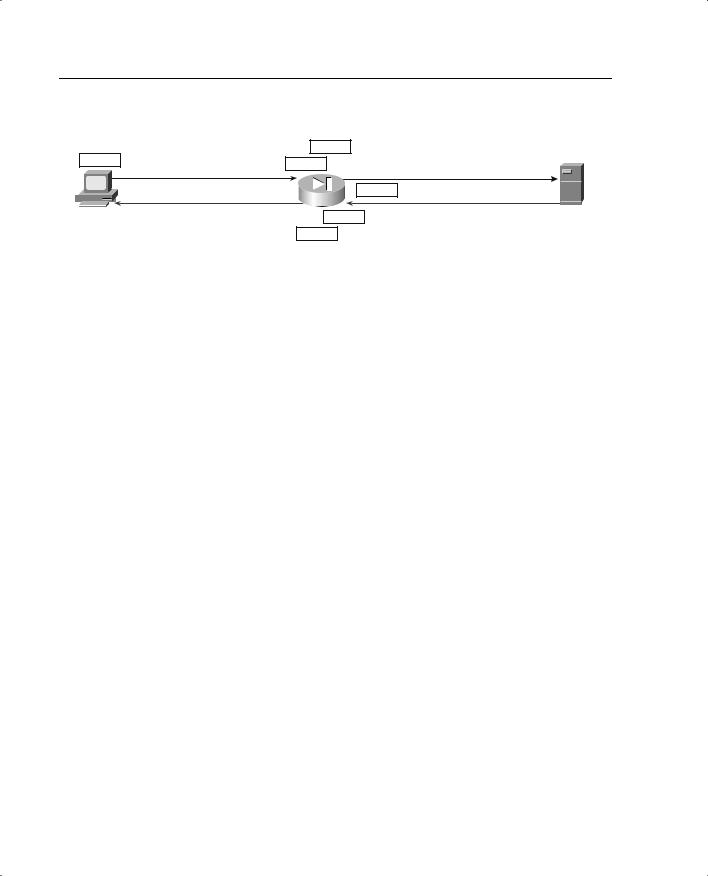
26 Chapter 3: The Cisco Secure PIX Firewall
Figure 3-1 How the Adaptive Security Algorithm Works
1
Internal
Host
3
2
4
5
External
Resource
6
The following list explains the mechanics of how ASA and stateful filtering work on the PIX:
1The internal host initiates a connection to an external resource.
2The PIX writes the following information about this connection into the state table:
—Source IP
—Source port
—Destination IP
—Destination port
—TCP sequencing information
—Additional TCP/UDP flags
—A randomly generated TCP sequence number is applied
This entry in the state table is called the session object.
3The connection object is compared to the security policy. If the connection is not allowed, the session object is deleted, and the connection is dropped.
4If the connection is approved by the security policy, the request continues to the external resource.
5The external resource replies to the request.
6The response arrives at the firewall and is compared to the session object. If the response matches the session object, the traffic passes to the internal host. If it does not match, the connection is dropped.
Cut-Through Proxy
The cut-through proxy feature on the Cisco PIX Firewall provides significantly better performance than application proxy firewalls, because it completes user authentication at the application layer, verifies authorization against the security policy, and then opens the connection as authorized by the security policy. Subsequent traffic for this connection is no longer handled at the application layer but is statefully inspected, providing significant performance benefits over proxy-based firewalls.
