
- •Icons Used in This Book
- •Network Security
- •Vulnerabilities
- •Threats
- •Types of Attacks
- •Network Security Policy
- •AVVID and SAFE
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Firewall Technologies
- •Cisco PIX Firewall
- •Foundation Summary
- •The Cisco Secure PIX Firewall
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Overview of the Cisco PIX Firewall
- •Cisco PIX Firewall Models and Features
- •Foundation Summary
- •System Maintenance
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Accessing the Cisco PIX Firewall
- •Installing a New Operating System
- •Upgrading the Cisco PIX OS
- •Creating a Boothelper Diskette Using a Windows PC
- •Auto Update Support
- •Password Recovery
- •Foundation Summary
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •How the PIX Firewall Handles Traffic
- •Address Translation
- •Translation Versus Connection
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Access Modes
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •TurboACL
- •Object Grouping
- •Advanced Protocol Handling
- •Foundation Summary
- •Syslog
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •How Syslog Works
- •How Log Messages Are Organized
- •How to Read System Log Messages
- •Disabling Syslog Messages
- •Foundation Summary
- •Cisco PIX Firewall Failover
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •What Causes a Failover Event
- •What Is Required for a Failover Configuration
- •Failover Monitoring
- •Stateful Failover
- •LAN-Based Failover
- •Foundation Summary
- •Virtual Private Networks
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Overview of VPN Technologies
- •Cisco VPN Client
- •PPPoE Support
- •Foundation Summary
- •Scenario
- •Completed PIX Configurations
- •PIX Device Manager
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •PDM Overview
- •PIX Firewall Requirements to Run PDM
- •Foundation Summary
- •Content Filtering with the Cisco PIX Firewall
- •“Do I Know This Already?” Quiz
- •Filtering Java Applets
- •Filtering ActiveX Objects
- •Filtering URLs
- •Foundation Summary
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Overview of AAA and the Cisco PIX Firewall
- •Cisco Secure Access Control Server (CSACS)
- •Foundation Summary
- •How to Best Use This Chapter
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Specifying Your AAA Servers
- •Troubleshooting Your AAA Setup
- •Foundation Summary
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Multimedia Support on the Cisco PIX Firewall
- •Attack Guards
- •PIX Firewall’s Intrusion Detection Feature
- •ip verify reverse-path Command
- •Foundation Summary
- •Answers to the “Do I Know This Already?” Quizzes and Q&A Questions
- •Chapter 1
- •Chapter 2
- •Chapter 3
- •Chapter 4
- •Chapter 5
- •Chapter 6
- •Chapter 7
- •Chapter 8
- •Chapter 9
- •Chapter 10
- •Chapter 11
- •Chapter 12
- •Chapter 13
- •Chapter 14
- •Chapter 15
- •Appendix B
- •What’s Wrong with This Picture?

262 Chapter 13: Overview of AAA and the Cisco PIX Firewall
Supported AAA Server Technologies
The Cisco PIX Firewall supports two AAA server authentication protocols:
•Remote Authentication Dial-In User Service (RADIUS)—RADIUS was developed by Livingston Enterprises as a AAA server. It uses a UDP connection between the client (NAS) and the server (AAA). RADIUS combines the authentication and authorization into a single response to a query from the NAS.
•Terminal Access Controller Access Control System (TACACS+)—TACACS+ was developed by Cisco Systems as an alternative to RADIUS. TACACS+ uses a TCP connection between the client and server and divides the authentication and authorization into separate transmissions.
Cisco Secure Access Control Server (CSACS)
CSACS is a AAA server product developed by Cisco that can run on Windows NT/2000 Server. It supports a number of NASs, including the Cisco PIX Firewall. CSACS supports both RADIUS and TACACS+.
Minimum Hardware and Operating System Requirements for CSACS
Table 13-1 documents the minimum requirements needed by a system to run CSACS.
Table 13-1 CSACS System Requirements
System Requirement Type |
Requirements |
Hardware |
Pentium III Processor, 550 MHz or greater |
|
256 MB of RAM |
|
250 MB of available drive space. Additional space is required |
|
if you intend to run the CSACS database on this system. |
|
Screen resolution of 800× 600 256-color display |
|
|
Operating system |
Microsoft Windows NT Server with Service Pack 6a |
|
Microsoft Windows 2000 Server with Service Pack 1 or 2 |
|
Microsoft Windows 2000 Advanced Server with Service Pack |
|
1 or 2, without Microsoft Clustering Services installed |
|
Microsoft Windows 2000 Datacenter Server with Service |
|
Pack 1 or 2, without Microsoft Clustering Services installed |
|
|
Browser |
Microsoft Internet Explorer 5.0 or 5.5 with Java and |
|
JavaScript enabled |
|
Netscape Communicator 4.76 with Java and JavaScript |
|
enabled |
|
|

Cisco Secure Access Control Server (CSACS) 263
Installing CSACS on Windows 2000/NT Server
You can download a 90-day trial version of CSACS from the Cisco Software Center at www.cisco.com. You must register as a user to receive your CCO login. You must have the CCO login to download software from the software center. The installation of CSACS is an easy step-by-step process. It is a good idea to verify that your Windows NT or Windows 2000 Server is up to the current patch level. When you are ready to begin the installation, just run setup.exe. Figure 13-3 shows the initial CSACS installation screen.
Figure 13-3 CSACS Splash Screen
The second screen, shown in Figure 13-4, prompts you to verify that your system is ready for this installation. Before this installation, you should verify that your NT/2000 server is up to date, including Internet Explorer, and that you have connectivity with the NAS. In this case, the PIX functions as the NAS.
Figure 13-4 Before Installation Screen

264 Chapter 13: Overview of AAA and the Cisco PIX Firewall
You are prompted to specify the installation directory, as shown in Figure 13-5. You can use the default directory, C:\Program Files\Cisco Secure ACS V3.0, or you can select another directory for the installation.
Figure 13-5 Installation Directory (Default)
You also select either the CSACS user database or the CSACS database and the Windows NT/2000 user database combined. The latter selection lets you use Windows username/ password management and integrate Windows performance monitoring, which provides you with real-time login statistics.
For the purpose of this installation, the CSACS database only is used. Figure 13-6 shows this installation screen.
Figure 13-6 User Database Screen
Cisco Secure Access Control Server (CSACS) 265
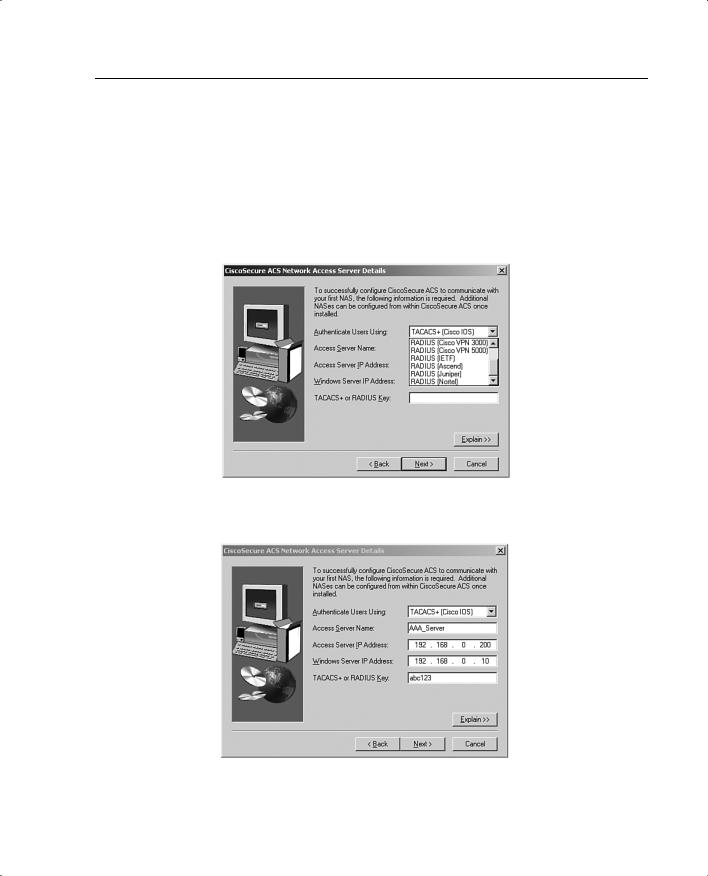
You are prompted to select any of ten possible choices for the connection type to the NAS, as shown in Figure 13-7. Remember that the Cisco PIX Firewall is acting as the NAS. For this configuration, TACACS+ (Cisco IOS) is selected. Having selected the Authenticate Users Using selection, you need to finish the NAS information to complete the connection between the AAA server and the NAS. Figure 13-8 shows the NAS information box. Note the Explain button in the lower-right corner. Click this button to get an explanation of each of the settings, as shown in Figure 13-9.
Figure 13-7 NAS Technology
Figure 13-8 NAS Information

266 Chapter 13: Overview of AAA and the Cisco PIX Firewall
Figure 13-9 Explanation of Settings
You are prompted to select the advanced features you want to appear on the user interface. This allows you to determine how much (or how little) detail you want to see when working in the user interface. Figure 13-10 shows the available selections, and Figure 13-11 shows the explanation screen that describes each of the available options.
Figure 13-10 Available Options in the User Interface
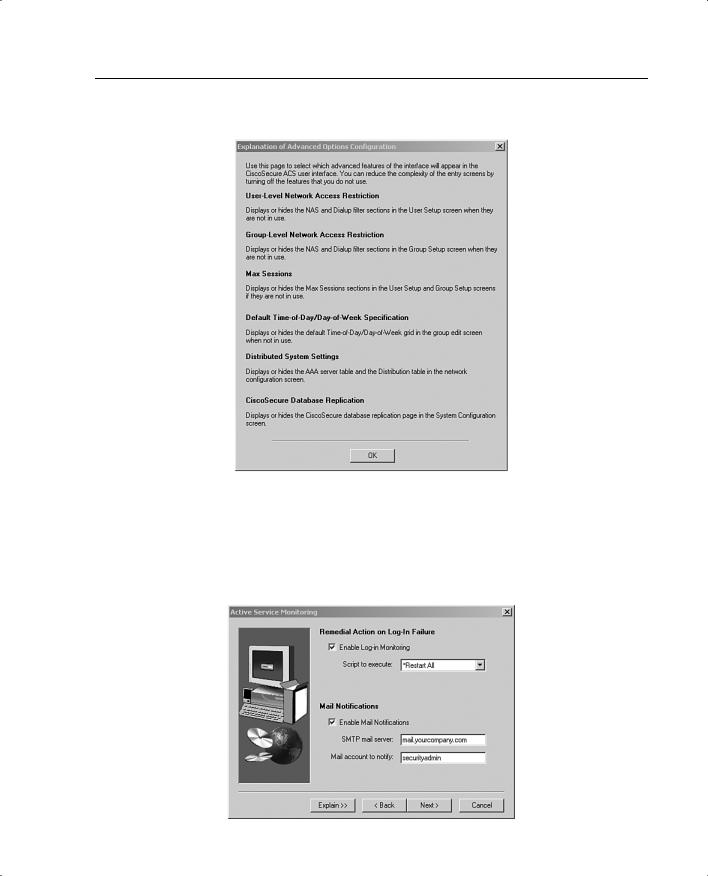
Cisco Secure Access Control Server (CSACS) 267
Figure 13-11 Explanation of Options
Next you select from three actions for the AAA server to initiate in the event of a communications failure between the CSACS and the NAS. These settings also include SMTP settings and the user account for the CSACS to send an alert to if a failure occurs. Figures 13-12 and 13-13 show the settings screen and the settings explanation screen.
Figure 13-12 Alert Action and Notification Settings

268 Chapter 13: Overview of AAA and the Cisco PIX Firewall
Figure 13-13 Explanations for Alert Action and Notification Settings
Congratulations! You have completed the installation of CSACS on a Windows 2000 Server. After completing the review questions, feel free to proceed to Chapter 14, “Configuration of AAA on the PIX Firewall,” to configure CSACS.
