
- •Using Your Sybex Electronic Book
- •Acknowledgments
- •Introduction
- •Assessment Test
- •Answers to Assessment Test
- •Types of Network Security Threats
- •Types of Security Weaknesses
- •Technology Weaknesses
- •Configuration Weaknesses
- •Policy Weaknesses
- •Types of Network Attacks
- •Eavesdropping
- •Denial-of-Service Attacks
- •Unauthorized Access
- •WareZ
- •Masquerade Attack (IP Spoofing)
- •Session Hijacking or Replaying
- •Rerouting
- •Repudiation
- •Smurfing
- •Password Attacks
- •Man-in-the-Middle Attacks
- •Application-Layer Attacks
- •Trojan Horse Programs, Viruses, and Worms
- •HTML Attacks
- •The Corporate Security Policy
- •Summary
- •Exam Essentials
- •Key Terms
- •Written Lab
- •Review Questions
- •Answers to Written Lab
- •Answers to Review Questions
- •Authentication Methods
- •Windows Authentication
- •Security Server Authentication
- •PAP and CHAP Authentication
- •PPP Callback
- •Configuring the NAS for AAA
- •Securing Access to the Exec Mode
- •Enable AAA Locally on the NAS
- •Authentication Configuration on the NAS
- •Authorization Configuration on the NAS
- •Accounting Configuration on the NAS
- •Verifying the NAS Configuration
- •Troubleshooting AAA on the Cisco NAS
- •Summary
- •Exam Essentials
- •Key Terms
- •Commands Used in This Chapter
- •Written Lab
- •Review Questions
- •Hands-On Labs
- •Lab 2.1: Setting the Line Passwords
- •Lab 2.2: Setting the Enable Passwords
- •Lab 2.3: Encrypting your Passwords
- •Lab 2.4: Creating Usernames and Logging In
- •Lab 2.5: Configuring AAA Authentication on the NAS
- •Answers to Written Lab
- •Answers to Review Questions
- •Introduction to the CiscoSecure ACS
- •Using User Databases for Authentication
- •Populating the User Database Population
- •New ACS Features
- •Installing CiscoSecure ACS 3.0
- •Administering CiscoSecure ACS
- •TACACS+ Overview
- •Configuring TACACS+
- •Using RADIUS
- •CiscoSecure User Database NAS Configuration for RADIUS
- •Verifying TACACS+
- •Summary
- •Exam Essentials
- •Key Terms
- •Commands Used in This Chapter
- •Written Lab
- •Review Questions
- •Answers to Written Lab
- •Answers to Review Questions
- •Solving Eavesdropping and Session Replay Problems
- •Fighting Rerouting Attacks
- •Fighting Denial-of-Service Attacks
- •Turning Off and Configuring Network Services
- •Blocking SNMP Packets
- •Disabling Echo
- •Turning Off BOOTP and Auto-Config
- •Disabling the HTTP Interface
- •Disabling IP Source Routing
- •Disabling Proxy ARP
- •Disabling Redirect Messages
- •Disabling the Generation of ICMP Unreachable Messages
- •Disabling Multicast Route Caching
- •Disabling the Maintenance Operation Protocol (MOP)
- •Turning Off the X.25 PAD Service
- •Enabling the Nagle TCP Congestion Algorithm
- •Logging Every Event
- •Disabling Cisco Discovery Protocol
- •Disabling the Default Forwarded UDP Protocols
- •Summary
- •Exam Essentials
- •Key Terms
- •Commands Used in This Chapter
- •Written Lab
- •Review Questions
- •Hands-On Lab
- •Lab 4.1: Controlling TCP/IP Services
- •Answers to Written Lab
- •Answers to Review Questions
- •Understanding the Cisco IOS Firewall
- •Authentication Proxy and IDS
- •Context-Based Access Control
- •CBAC Compared to ACLs
- •CBAC-Supported Protocols
- •Introduction to CBAC Configuration
- •Using Audit Trails and Alerts
- •Configuring Global Timeouts and Thresholds
- •Configuring PAM
- •Defining Inspection Rules
- •Applying Inspection Rules and ACLs to Router Interfaces
- •Configuring IP ACLs at the Interface
- •Testing and Verifying CBAC
- •Summary
- •Exam Essentials
- •Key Terms
- •Commands Used in This Chapter
- •Written Lab
- •Review Questions
- •Hands-On Labs
- •Lab 5.1: Configure Logging and Audit Trails
- •Lab 5.2: Define and Apply Inspection Rules and ACLs
- •Lab 5.3: Test and Verify CBAC
- •Answers to Written Lab
- •Answers to Review Questions
- •Introduction to the Cisco IOS Firewall Authentication Proxy
- •Configuring the AAA Server
- •Configuring AAA
- •Configuring the Authentication Proxy
- •Testing and Verifying Your Configuration
- •show Commands
- •Clearing the Cache
- •Introduction to the Cisco IOS Firewall IDS
- •Initializing Cisco IOS Firewall IDS
- •Configuring, Disabling, and Excluding Signatures
- •Creating and Applying Audit Rules
- •Setting Default Actions
- •Creating an Audit Rule
- •Applying the Audit Rule
- •Verifying the Configuration
- •Stopping the IOS Firewall IDS
- •Summary
- •Exam Essentials
- •Key Terms
- •Commands Used in This Chapter
- •Written Lab
- •Review Questions
- •Hands-On Labs
- •Lab 6.1: Enabling the IOS Firewall Authentication Proxy
- •Lab 6.2: Enabling the IOS Firewall IDS
- •Answers to Written Lab
- •Answers to Review Questions
- •What is a Virtual Private Network?
- •Introduction to Cisco IOS IPSec
- •IPSec Transforms
- •IPSec Operation
- •The Components of IPSec
- •IPSec Encapsulation
- •Internet Key Exchange (IKE)
- •Summary
- •Exam Essentials
- •Key Terms
- •Written Lab
- •Review Questions
- •Answers to Written Lab
- •Answers to Review Questions
- •Configuring Cisco IOS IPSec for Pre-Shared Keys Site-to-Site
- •Preparing for IKE and IPSec
- •Configuring IKE
- •Configuring IPSec
- •Testing and Verifying IPSec
- •Configuring IPSec Manually
- •Configuring IPSec for RSA-Encrypted Nonces
- •Configuring Cisco IOS IPSec Certificate Authority Support Site-to-Site
- •Configuring CA Support Tasks
- •Preparing for IKE and IPSec
- •Configuring CA Support
- •Configuring IKE Using CA
- •Configuring IPSec for CA
- •Testing and Verifying IPSec for CA
- •Summary
- •Exam Essentials
- •Key Terms
- •Commands Used in This Chapter
- •Written Lab
- •Review Questions
- •Hands-On Labs
- •Lab 8.1: Configure IKE on Lab_A and Lab_B
- •Lab 8.2: Configure IPSec on Lab_A and Lab_B
- •Answers to Written Lab
- •Answers to Review Questions
- •Answers to Hands-On Labs
- •Answer to Lab 8.1
- •Answer to Lab 8.2
- •Introduction to Cisco Easy VPN
- •The Easy VPN Server
- •Introduction to the Cisco VPN 3.5 Client
- •Easy VPN Server Configuration Tasks
- •Pre-Configuring the Cisco VPN 3.5 Client
- •Summary
- •Exam Essentials
- •Key Terms
- •Written Lab
- •Review Questions
- •Hands-On Lab
- •Lab 9.1: Installing the Cisco VPN 3.5 Client Software on Windows
- •Answers to Written Lab
- •Answers to Review Questions
- •Network Separation
- •Three Ways through a PIX Firewall
- •PIX Firewall Configuration Basics
- •Configuring Interfaces
- •Saving Your Configuration
- •Configuring Access through the PIX Firewall
- •Configuring Outbound Access
- •Configuring Inbound Access
- •Configuring Multiple Interfaces and AAA on the PIX Firewall
- •Configuring Multiple Interfaces
- •Implementing AAA on the PIX Firewall
- •Configuring Advanced PIX Firewall Features
- •Failover
- •Outbound Access Control
- •Logging
- •SNMP Support
- •Java Applet Blocking
- •URL Filtering
- •Password Recovery
- •Glossary
The Cisco Packet Internet eXchange (PIX) Firewall |
325 |
PIX Firewall interfaces must be purchased from Cisco or Cisco resellers. No other interfaces are supported, because vendors would not be able to provide drivers to work with the closed operating system used by the PIX Firewall. Currently, the following interface types are available:
Single-port 10/100BaseT Ethernet
Four-port 10/100BaseT Ethernet
Token Ring
FDDI
Network Separation
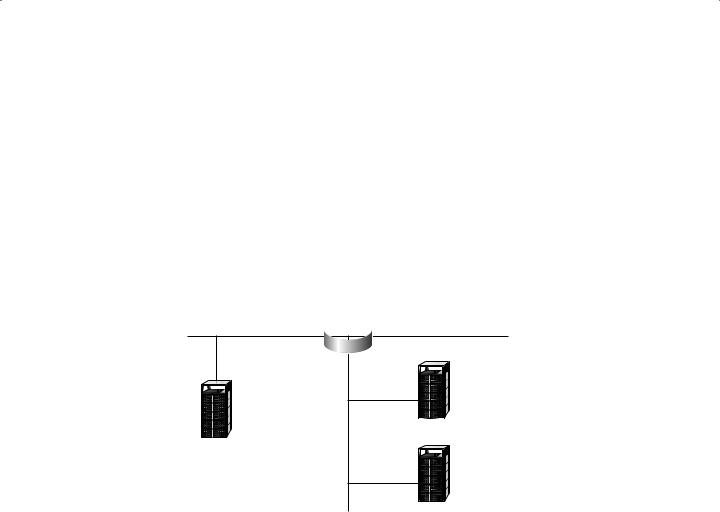
Consider the following PIX Firewall separating three distinct networks:
PIX Firewall
Inside  Outside
Outside
Perimeter
DNS server
Enterprise server
E-mail server
Because all traffic between these three networks must physically pass through the PIX Firewall, it is in the ultimate position to control and potentially limit all access between these networks. These networks are labeled inside, perimeter, and outside. They each have a separate function:
Inside network The inside network is your internal network where you keep your protected resources such as enterprise servers or other internal-access devices, along with your internal users.
Outside network The outside network is the open, untrusted Internet.
Perimeter network Also called a DMZ (for de-militarized zone), the perimeter network is where you host services such as DNS (Domain Name System) servers, e-mail servers, web and FTP servers, and so on. These services are generally made available to users from the outside network.
Some of you may recognize this terminology from the classic three-part firewall.
The administrator has the ability to control what the PIX Firewall lets through. There are many functions that the PIX Firewall can accomplish, but once it is installed, there are only three ways to get traffic through a PIX Firewall. You will learn about these next.
Copyright ©2003 SYBEX Inc., 1151 Marina Village Parkway, Alameda, CA 94501. |
www.sybex.com |

326 Appendix A Introduction to the PIX Firewall
Three Ways through a PIX Firewall
The PIX Firewall has ultimate control over what traffic goes between the networks it separates, and it gives a great deal of control to the administrator in configuring which traffic is to be permitted and which traffic is not allowed. The PIX Firewall can permit traffic between networks using three methods:
Cut-through proxy user authentication
Static route
Adaptive Security Algorithm (ASA)
Cut-Through Proxy User Authentication
The cut-through proxy user authentication method performs user authentication at the Application layer. When a user requests a resource through the PIX Firewall, the firewall intercepts that request and forces the user to provide a username and password. The firewall then authenticates this user against a security server using either the TACACS+ or the RADIUS security protocol (as discussed in Chapter 3, “Configuring CiscoSecure ACS and TACACS+”). Assuming that the security policy allows this particular user to access this resource, the user’s request is forwarded through the firewall. This method can be used for either inbound or outbound requests.
One common problem with proxy servers is that they must evaluate the contents of each and every packet passing through them. This is a processor-expensive operation and can introduce a potential bottleneck into the network. The PIX Firewall gets around this requirement by using a cut-through proxy technique. Once the user’s request has been approved, the PIX Firewall establishes a data flow between the two communicating partners. All traffic between that user and the resource then flows directly through the PIX Firewall, without needing to have each individual packet “proxied.”
Static Route
You can enter static routes on a PIX Firewall. The syntax is similar to that used on a Cisco router, but it is not the same. You must specify an interface name in the command, as in the following examples:
route outside 0.0.0.0 0.0.0.0 172.19.20.1 1
route inside 10.0.0.0 255.0.0.0 10.1.1.1
This syntax should look familiar to those of you with router experience. The only difference is the addition of the inside and outside parameters, which are the interface names. The “Configuring Interfaces” section later in this appendix discusses the naming of interfaces.
The routing protocol that the PIX Firewall supports is RIP (Routing Information Protocol). Earlier PIX Firewall versions support only RIP version 1 (RIPv1). RIP version 2 (RIPv2) is supported as of PIX Firewall version 5.1(1).
Copyright ©2003 SYBEX Inc., 1151 Marina Village Parkway, Alameda, CA 94501. |
www.sybex.com |
