
- •Using Your Sybex Electronic Book
- •Acknowledgments
- •Introduction
- •Assessment Test
- •Answers to Assessment Test
- •Types of Network Security Threats
- •Types of Security Weaknesses
- •Technology Weaknesses
- •Configuration Weaknesses
- •Policy Weaknesses
- •Types of Network Attacks
- •Eavesdropping
- •Denial-of-Service Attacks
- •Unauthorized Access
- •WareZ
- •Masquerade Attack (IP Spoofing)
- •Session Hijacking or Replaying
- •Rerouting
- •Repudiation
- •Smurfing
- •Password Attacks
- •Man-in-the-Middle Attacks
- •Application-Layer Attacks
- •Trojan Horse Programs, Viruses, and Worms
- •HTML Attacks
- •The Corporate Security Policy
- •Summary
- •Exam Essentials
- •Key Terms
- •Written Lab
- •Review Questions
- •Answers to Written Lab
- •Answers to Review Questions
- •Authentication Methods
- •Windows Authentication
- •Security Server Authentication
- •PAP and CHAP Authentication
- •PPP Callback
- •Configuring the NAS for AAA
- •Securing Access to the Exec Mode
- •Enable AAA Locally on the NAS
- •Authentication Configuration on the NAS
- •Authorization Configuration on the NAS
- •Accounting Configuration on the NAS
- •Verifying the NAS Configuration
- •Troubleshooting AAA on the Cisco NAS
- •Summary
- •Exam Essentials
- •Key Terms
- •Commands Used in This Chapter
- •Written Lab
- •Review Questions
- •Hands-On Labs
- •Lab 2.1: Setting the Line Passwords
- •Lab 2.2: Setting the Enable Passwords
- •Lab 2.3: Encrypting your Passwords
- •Lab 2.4: Creating Usernames and Logging In
- •Lab 2.5: Configuring AAA Authentication on the NAS
- •Answers to Written Lab
- •Answers to Review Questions
- •Introduction to the CiscoSecure ACS
- •Using User Databases for Authentication
- •Populating the User Database Population
- •New ACS Features
- •Installing CiscoSecure ACS 3.0
- •Administering CiscoSecure ACS
- •TACACS+ Overview
- •Configuring TACACS+
- •Using RADIUS
- •CiscoSecure User Database NAS Configuration for RADIUS
- •Verifying TACACS+
- •Summary
- •Exam Essentials
- •Key Terms
- •Commands Used in This Chapter
- •Written Lab
- •Review Questions
- •Answers to Written Lab
- •Answers to Review Questions
- •Solving Eavesdropping and Session Replay Problems
- •Fighting Rerouting Attacks
- •Fighting Denial-of-Service Attacks
- •Turning Off and Configuring Network Services
- •Blocking SNMP Packets
- •Disabling Echo
- •Turning Off BOOTP and Auto-Config
- •Disabling the HTTP Interface
- •Disabling IP Source Routing
- •Disabling Proxy ARP
- •Disabling Redirect Messages
- •Disabling the Generation of ICMP Unreachable Messages
- •Disabling Multicast Route Caching
- •Disabling the Maintenance Operation Protocol (MOP)
- •Turning Off the X.25 PAD Service
- •Enabling the Nagle TCP Congestion Algorithm
- •Logging Every Event
- •Disabling Cisco Discovery Protocol
- •Disabling the Default Forwarded UDP Protocols
- •Summary
- •Exam Essentials
- •Key Terms
- •Commands Used in This Chapter
- •Written Lab
- •Review Questions
- •Hands-On Lab
- •Lab 4.1: Controlling TCP/IP Services
- •Answers to Written Lab
- •Answers to Review Questions
- •Understanding the Cisco IOS Firewall
- •Authentication Proxy and IDS
- •Context-Based Access Control
- •CBAC Compared to ACLs
- •CBAC-Supported Protocols
- •Introduction to CBAC Configuration
- •Using Audit Trails and Alerts
- •Configuring Global Timeouts and Thresholds
- •Configuring PAM
- •Defining Inspection Rules
- •Applying Inspection Rules and ACLs to Router Interfaces
- •Configuring IP ACLs at the Interface
- •Testing and Verifying CBAC
- •Summary
- •Exam Essentials
- •Key Terms
- •Commands Used in This Chapter
- •Written Lab
- •Review Questions
- •Hands-On Labs
- •Lab 5.1: Configure Logging and Audit Trails
- •Lab 5.2: Define and Apply Inspection Rules and ACLs
- •Lab 5.3: Test and Verify CBAC
- •Answers to Written Lab
- •Answers to Review Questions
- •Introduction to the Cisco IOS Firewall Authentication Proxy
- •Configuring the AAA Server
- •Configuring AAA
- •Configuring the Authentication Proxy
- •Testing and Verifying Your Configuration
- •show Commands
- •Clearing the Cache
- •Introduction to the Cisco IOS Firewall IDS
- •Initializing Cisco IOS Firewall IDS
- •Configuring, Disabling, and Excluding Signatures
- •Creating and Applying Audit Rules
- •Setting Default Actions
- •Creating an Audit Rule
- •Applying the Audit Rule
- •Verifying the Configuration
- •Stopping the IOS Firewall IDS
- •Summary
- •Exam Essentials
- •Key Terms
- •Commands Used in This Chapter
- •Written Lab
- •Review Questions
- •Hands-On Labs
- •Lab 6.1: Enabling the IOS Firewall Authentication Proxy
- •Lab 6.2: Enabling the IOS Firewall IDS
- •Answers to Written Lab
- •Answers to Review Questions
- •What is a Virtual Private Network?
- •Introduction to Cisco IOS IPSec
- •IPSec Transforms
- •IPSec Operation
- •The Components of IPSec
- •IPSec Encapsulation
- •Internet Key Exchange (IKE)
- •Summary
- •Exam Essentials
- •Key Terms
- •Written Lab
- •Review Questions
- •Answers to Written Lab
- •Answers to Review Questions
- •Configuring Cisco IOS IPSec for Pre-Shared Keys Site-to-Site
- •Preparing for IKE and IPSec
- •Configuring IKE
- •Configuring IPSec
- •Testing and Verifying IPSec
- •Configuring IPSec Manually
- •Configuring IPSec for RSA-Encrypted Nonces
- •Configuring Cisco IOS IPSec Certificate Authority Support Site-to-Site
- •Configuring CA Support Tasks
- •Preparing for IKE and IPSec
- •Configuring CA Support
- •Configuring IKE Using CA
- •Configuring IPSec for CA
- •Testing and Verifying IPSec for CA
- •Summary
- •Exam Essentials
- •Key Terms
- •Commands Used in This Chapter
- •Written Lab
- •Review Questions
- •Hands-On Labs
- •Lab 8.1: Configure IKE on Lab_A and Lab_B
- •Lab 8.2: Configure IPSec on Lab_A and Lab_B
- •Answers to Written Lab
- •Answers to Review Questions
- •Answers to Hands-On Labs
- •Answer to Lab 8.1
- •Answer to Lab 8.2
- •Introduction to Cisco Easy VPN
- •The Easy VPN Server
- •Introduction to the Cisco VPN 3.5 Client
- •Easy VPN Server Configuration Tasks
- •Pre-Configuring the Cisco VPN 3.5 Client
- •Summary
- •Exam Essentials
- •Key Terms
- •Written Lab
- •Review Questions
- •Hands-On Lab
- •Lab 9.1: Installing the Cisco VPN 3.5 Client Software on Windows
- •Answers to Written Lab
- •Answers to Review Questions
- •Network Separation
- •Three Ways through a PIX Firewall
- •PIX Firewall Configuration Basics
- •Configuring Interfaces
- •Saving Your Configuration
- •Configuring Access through the PIX Firewall
- •Configuring Outbound Access
- •Configuring Inbound Access
- •Configuring Multiple Interfaces and AAA on the PIX Firewall
- •Configuring Multiple Interfaces
- •Implementing AAA on the PIX Firewall
- •Configuring Advanced PIX Firewall Features
- •Failover
- •Outbound Access Control
- •Logging
- •SNMP Support
- •Java Applet Blocking
- •URL Filtering
- •Password Recovery
- •Glossary

|
|
Introduction to the Cisco VPN 3.5 Client |
305 |
T A B L E 9 . 1 Easy VPN Supported and Unsupported Options (continued) |
|
||
|
|
|
|
Options |
Supported |
Unsupported |
|
|
|
|
|
Diffie-Hellman (DH) groups |
2 |
1 |
|
|
5 |
|
|
IKE encryption algorithms |
DES |
|
|
|
3DES |
|
|
IPSec encryption algorithms |
DES |
|
|
|
3DES |
|
|
|
NULL |
|
|
IPSec protocol identifiers |
ESP |
Authentication Header (AH) |
|
|
IPCOMP-LZS |
|
|
IPSEC protocol mode |
Tunnel |
Transport |
|
|
|
|
|
And I have to note a couple more options that aren’t supported: manual keys and perfect forward security (PFS).
Let’s move on to the Cisco VPN 3.5 Client and how it is installed and configured.
Introduction to the Cisco VPN 3.5 Client
The Cisco VPN 3.5 Client can be used to establish VPN connections to any of the Easy VPN Server devices listed earlier in this chapter, including an IOS router. Cisco VPN 3.5 Client is also available via Cisco Connection Online (CCO) to customers with SMARTnet support.
The Cisco VPN 3.5 Client is available for the following operating systems:
Windows 95, 98, Me, NT 4.0, 2000, and XP
Linux (Intel)
Solaris (Ultra-Sparc 32-bit)
Mac OS X 10.1
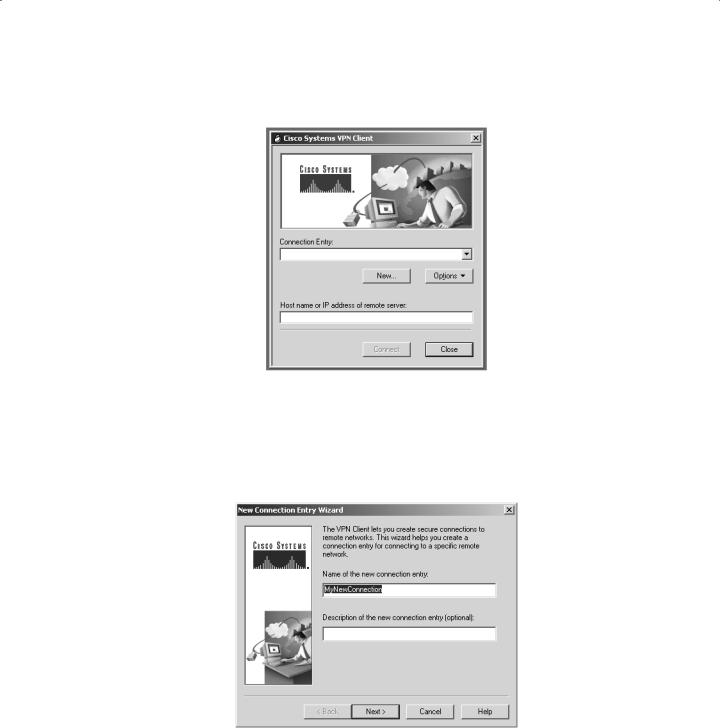
Once installed, the VPN Client allows you to configure and select a number of possible VPN servers. When you launch the VPN Client, the window shown in Figure 9.1 appears.
Copyright ©2003 SYBEX Inc., 1151 Marina Village Parkway, Alameda, CA 94501. |
www.sybex.com |
306 Chapter 9 Cisco IOS Remote Access Using Cisco Easy VPN
F I G U R E 9 . 1 Launching VPN Client
Since no connections are configured, you need to add one by clicking the New button. When you do this, the New Connection Entry Wizard appears, illustrated in Figure 9.2. This window prompts you to give the connection a name and gives you the option of adding a description for the new connection entry.
F I G U R E 9 . 2 Creating a new connection entry
After naming the connection, you click the Next button and enter the IP address of the VPN server you’re connecting to in the window illustrated in Figure 9.3.
Copyright ©2003 SYBEX Inc., 1151 Marina Village Parkway, Alameda, CA 94501. |
www.sybex.com |
Introduction to the Cisco VPN 3.5 Client |
307 |
F I G U R E 9 . 3 Identifying the VPN server to be connected to
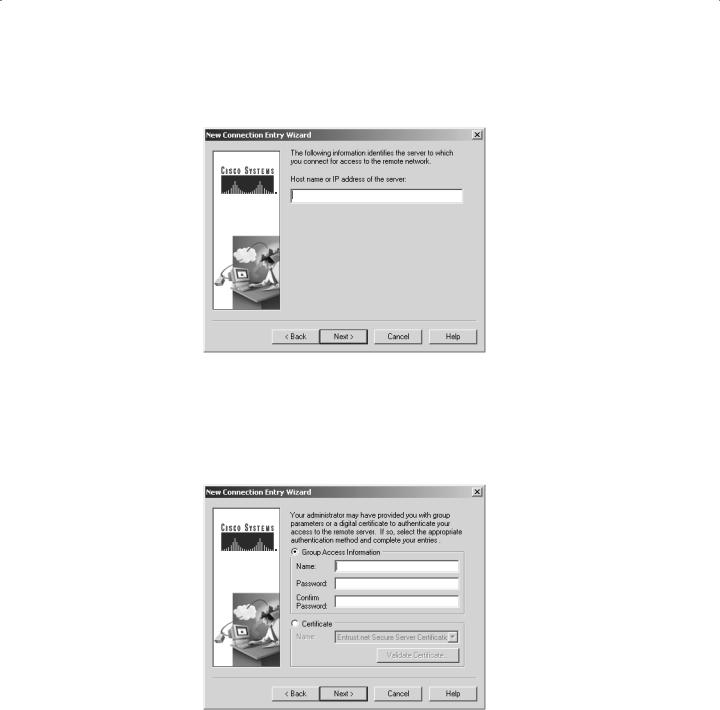
Next, you’re queried for group access or certificate information. This is the only remotely challenging part of the Easy VPN concept, and it isn’t even that bad. But if you’re not doing this yourself, you’ll need to provide users with the correct information so they can fill out the screen shown in Figure 9.4.
F I G U R E 9 . 4 Entering group access information
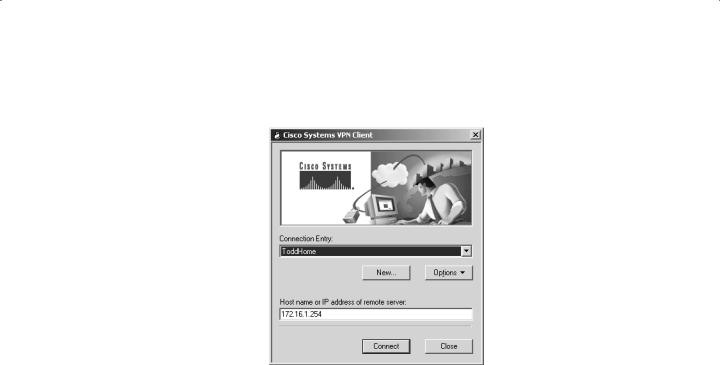
You’ll get one last chance to make any changes when you’re asked if you want to save the connection information. Once this is done, click Connect from the initial screen, as you can see in Figure 9.5.
Copyright ©2003 SYBEX Inc., 1151 Marina Village Parkway, Alameda, CA 94501. |
www.sybex.com |
308 Chapter 9 Cisco IOS Remote Access Using Cisco Easy VPN
F I G U R E 9 . 5 Connecting your VPN server
You can add as many connections as you want and then select one to use from the pull-down menu before connecting.
The VPN 3.5 Client supports many VPN features. In fact, it’s so supportive, it doesn’t have some of the limitations that the IOS Easy VPN Server does. This requires a little thought when configuring connections to avoid incompatibilities. Here’s an example—VPN Client supports Diffie-Hellman groups 1, 2, and 5, but as you know, the Easy VPN Server doesn’t support DH1.
Easy VPN Server Configuration Tasks
Easy VPN Server configuration uses skills and commands I’ve already covered in previous chapters. Basically, you need to configure AAA and then configure IPSec. There are some optional features you can configure such as DPD, but they’re not required.
Cisco has defined the following seven steps to configuring the Easy VPN Server:
1.Enable policy lookup via AAA.
2.Define group policy for mode configuration push.
3.Apply mode configuration and Xauth to crypto maps.
4.Enable Reverse Route Injection (RRI) for the VPN Client (optional).
5.Enable IKE Dead Peer Detection (optional).
6.Configure RADIUS server support (optional).
7.Verify the Easy VPN Server.
Each step itself consists of multiple steps. Step 1 involves enabling AAA. Steps 2 and 3 involve configuring IPSec. Steps 4 through 6 are specific to Easy VPN Server configuration,
Copyright ©2003 SYBEX Inc., 1151 Marina Village Parkway, Alameda, CA 94501. |
www.sybex.com |
