Kluwer - Handbook of Biomedical Image Analysis Vol
.2.pdfSimultaneous Fuzzy Segmentation of Medical Images |
673 |
It is obvious from these definitions that iσ is an M-semisegmentation, for 1 ≤
i ≤ |R|. |
|
|
|
|
|
|
|
We now demonstrate the definitions on the seeded two-fuzzy graph |
V |
, , V |
|||||
discussed above. In this case R = {1, 0.5, 0.25}. It immediately |
follows from |
||||||
|
|
||||||
Eq. (12.6) that 1σ (−1) = (1, 0, 1), 1σ (0) = (1, 1, 0), and 1σ (1) = (0, 0, 0). It turns out that 2σ = 1σ . This is because 1U = {(−1), (0)}, and there are no chains starting at either of these spels which satisfy, for i = 2, all the conditions listed in the second line of Eq. (12.8). On the other hand, the chain (0), (1) can be used to generate 3σ , which is in fact the 2-segmentation specified by the condition of Theorem 1.1. This is not an accident, we are now going to prove that in general the |R|σ defined by Eq. (12.6)–(12.8) satisfies the property stated in Theorem 1.1(i).
It clearly follows from the definitions (12.6) and (12.8) that, for c V and 1 ≤ m ≤ M, |R|σmc R {0}. Furthermore, it is also not difficult to see, for 1 <
i |
≤ | |
R , that if c |
|
iU , then iσ c |
= |
|R|σ c , and that |
|
|
| |
m |
m |
|
|||
|
|
|
|
iU = |
#c | |R|σ0c ≥ ir$ . |
(12.9) |
|
These imply the following two properties of the M-semisegmentation |R|σ .
(A) For c V and 1 ≤ m ≤ M, |R|σmc = 1 if, and only if, there is a chain of ψm-strength 1 from a seed in Vm to c.
(B)For c V , 1 ≤ m ≤ M, and 2 ≤ i ≤ |R|, |R|σmc = ir if, and only if, there is a chain 7c(0), · · · , c(K )8 of ψm-strength ir such that c(0) (i−1)U, |R|σmc(0) > 0, c(K ) = c and, for 1 ≤ k ≤ K, c(k) / (i−1)U .
Let c, d |
|
V . We say that (c, d) is consistent if, for 1 |
≤ |
m |
≤ |
M, |R|σ c |
= |
|R|σ c |
||||||||
|
|
|
|
|
|
|
|
|
|
|
m |
0 |
||||
implies that one of the following is true: |
|
|
|
|
|
|
|
|
|
|||||||
|
|
|
|
|
c = d; |
|
|
|
|
|
|
(12.10) |
||||
|
|
|
|
|R|σ0d > min |
|
|R| |
σ0c, ψm(c, d) ; |
|
|
|
|
(12.11) |
||||
|R|σ d |
min |
|R|σ c, ψ |
(c, d) |
|
and |
|R|σ d |
|
|R|σ d. |
|
|
(12.12) |
|||||
|
|
0 = |
|
0 |
m |
|
|
m |
= |
|
0 |
|
|
|
|
|
We now show that, for all c, d V , (c, d) is consistent.
To do this, we assume that there is a (c, d) and an m such that
and yet none of Eqs. (12.10)–(12.12) holds and show that this leads to a contradiction. A consequence of our assumption is that c = d and at least one of the
Simultaneous Fuzzy Segmentation of Medical Images |
|
|
|
|
|
|
|
|
|
|
|
|
675 |
|||||||||||||||||||||||||
By B there is a chain c(0), . . . , c(K ) |
of ψm-strength s such that c(0) |
|
(i−1)U, |
|||||||||||||||||||||||||||||||||||
|
(0) |
> 0, |
c(K ) |
|
|
c, and,7 |
for 1 |
|
|
k |
|
8K, c(k) / |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||||
|R|σmc |
= |
≤ |
≤ |
|
(i−1)U . We are now going to |
|||||||||||||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||
show that |
c(0), . . . , c(K ) |
is an |R|σ m-chain by showing that, for 1 |
≤ |
k |
≤ |
K, |
||||||||||||||||||||||||||||||||
|
(k) |
= s. |
7Otherwise, consider8 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||||||||
|R|σmc |
the smallest k ≥ 1 that violates this equation. |
|||||||||||||||||||||||||||||||||||||
Then we have that |R|σ c(k−1) |
≥ |
s and |R|σ c(k) < s (recall that c(k) |
/ (i−1)U and so |
|||||||||||||||||||||||||||||||||||
|R|σ c |
(k) |
|
|
|
|
|
|
|
m |
|
|
|
|
|
|
|
m |
|
|
|
|
|
c(k−1), c(k) |
|
|
s violates the |
||||||||||||
|
≤ |
s). This combined with the fact that ψm |
|
≥ |
||||||||||||||||||||||||||||||||||
0 |
|
|
|
|
(k |
|
1) |
|
(k) |
. Since |
|
(0) |
|
(i |
|
1) |
|
and |
R c |
(0) |
0, |
|
c |
(0) |
|
|
j |
|
|
for |
||||||||
consistency of |
c |
− |
, c |
c |
|
− |
U |
|
R |
|
= |
r |
|
|||||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |σm |
> |
|
| | |
σm |
|
|
|
|||||||||||||
some 1 ≤ j < i and, by the induction hypothesis, there is an |R|σ m-chain from a |
||||||||||||||||||||||||||||||||||||||
seed in Vm to c(0) |
of ψm-strength jr > s. Appending |
c(0), . . . , c(K ) |
|
to this chain |
||||||||||||||||||||||||||||||||||
we obtain |R|σ m-chain from a seed in Vm to c of ψm7-strength s. |
8(Just append- |
|||||||||||||||||||||||||||||||||||||
ing may not result in a chain, since a chain is defined as a sequence of distinct spels. However, this is easily remedied by removing, for a repeated spel in the sequence, all the spels between the repetitions and one of the repetitions.)
Now we show that there is no |R|σ m-chain from a seed in Vm to c of ψm- strength greater than s. This is clearly so if s = 1. Suppose now that s < 1 and
that |
c(0), . . . , c(K ) is an |R|σ m-chain from a seed in Vm of ψm-strength t > s. We |
|||||||||||||||||
now |
7show that, for8 0 |
≤ |
k |
≤ |
K, |R|σmc(k) |
≥ |
t. From this it follows that c(K ) cannot |
|||||||||||
|
|
|
|
|
|
|
|R|σ c |
(0) |
|
1 |
|
t. For k > 0, |
||||||
be c and we are done. Since c(0) is a seed in Vm, |
|
|
= |
≥ |
||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
m |
|
|
|
|||
induction that makes use of the consistency of |
(k |
|
1) |
|
(k) |
leads to the desired |
||||||||||||
result. |
|
|
|
|
|
c |
|
− |
|
, c |
|
|
|
|
|
|
||
To show that σ = |R|σ satisfies the property stated in Theorem 1.1(i), we first make two preliminary observations:
(A)For any c V and 1 ≤ m ≤ M, if σnc > 0, then snc = σnc = σ0c. (The first equality follows from Eqs. (12.14) and (12.15), and the second from the
definition of M-semisegmentation.)
(B)For any c V and 1 ≤ n ≤ M, if σnc = 0 and σ0c > 0, then snc < σ0c. (Assume the contrary. It cannot be that snc is defined by the first line of Eq. (12.4), for then c Vn and by A we would have that σnc = 1.
Hence snc is defined by the second line of Eq. (12.4) using some d
such that min µσ,n,Vn (d), ψ (d, c) = snc ≥ σ0c > 0. Hence, by Eq. (12.15) σnd ≥ σ0c > 0 and so σ0d = σnd ≥ σ0c. Interchanging c and d in the definition of consistency, we see that Eq. (12.10) cannot hold since σnd > 0 and σnc = 0, (12.11) cannot hold since σ0c ≤ σ0d, and (12.12) cannot hold since σnc = 0 and σ0c > 0. This contradiction with the consistency of (d, c) proves B.)
676 Herman and Carvalho
To complete the proof, let c V . We first assume that σ0c = 0. Let 1 ≤ n ≤ M. By the definition of M-semisegmentation, σnc = 0. It follows from A that c Vn and so snc is defined by the second line of Eq. (12.4). If snc were greater than 0, then there would have to be a d V and a chain of positive ψn-strength from
Vn to d, such that ψn(d, c) > 0. But then, that chain to d either contains c or could be extended to a chain of positive ψn-strength from Vn to c; either case would imply by Eq. (12.15) that σnc > 0. Hence snc = 0, and since this is true for 1 ≤ n ≤ M, Eq. (12.5) holds for 1 ≤ m ≤ M.
We now assume that σ0c > 0. By the definition of an M-semisegmentation, for 1 ≤ m ≤ M, either σnc = σ0c (and there is at least one such n) or σnc = 0. In the first case we have, by A, that snc = σnc = σ0c, and in the second case we have, by B, that snc < σ0c. From this it again follows that Eq. (12.5) holds for 1 ≤ m ≤ M.
Next we show that such M-semisegmentation is unique. The following proof was first published in [29].
Proof of Theorem 1.1(ii). Suppose that there are two different M- semisegmentations σ and τ of V having the stated property. We choose a spel c, such that σ c = τ c, but for all d V such that max(σ0d, τ0d) > max(σ0c, τ0c), σ d = τ d. Without loss of generality, we assume that σ0c ≥ τ0c, from which it follows that,
for some m {1, . . . , M}, σmc > τmc (≥ 0) and so, by Eq. (12.5), σmc = smc and c Vm. This implies that there exists a σ m-chain d(0), . . . , d(L) in V of ψm-strength not
less than σmc (> 0) such that d(0) Vm and ψm(d(L), c) ≥ σmc . Next we show thatd(0), . . . , d(L) is a τ m-chain.
We need to show that for 0 ≤ l ≤ L, τmd(l) > 0. This is true for 0, since d(0) Vm. Now assume that it is true for l − 1 (1 ≤ l ≤ L). Since d(0), . . . , d(l−1) is a τ m-
chain in V of ψm-strength at least σmc (> 0) from an element of Vm, we have that µτ,m,Vm(d(l−1)) ≥ σmc . Since we also know that ψm(d(l−1), d(l)) ≥ σmc , we get that ≥ σmc (where t is defined for τ as s is defined for σ in Eq. (12.4)). The only could be 0, if there were an n {1, . . . , M} such that max(σ0d(l) , τ0d(l) ) ≥ = τnd(l) = tnd(l) > tmd(l) ≥ σmc = σ0c = max(σ0c, τ0c). By the choice of c, this would
imply that σ d(l) = τ d(l) , which cannot be since σmd(l) = 0.
From the facts that 7d(0), . . . , d(L)8 is a τ m-chain of ψm-strength not less than σmc and that ψm(d(L), c) ≥ σmc , it follows that τ0c ≥ tmc ≥ σmc = σ0c ≥ τ0c, implying that all the inequalities are in fact equalities. But then σmc = tmc = τmc , contradicting
σmc > τmc and thereby validating uniqueness.
Simultaneous Fuzzy Segmentation of Medical Images |
677 |
Finally we show that provided that (V , , V) is connectable, any M- semisegmentation having the stated property is in fact an M-segmentation. The following proof was also first published in [29].
Proof of Theorem 1.1(iii). We observe that it is a consequence of Eq. (12.5) that, for any spel c, σ0c = max1≤m≤M smc . Since we assume that the seeded M-fuzzy graph (V , , V) is connectable, there exists a chain c(0), . . . , c(K ) of positive (min1≤m≤M ψm)-strength from a seed spel to an arbitrary spel c. We now show
inductively that, for 0 ≤ k ≤ K , σ0c(k) > 0. This is clearly so for k = 0. Suppose now that it is so for k − 1. Choose an m (1 ≤ m ≤ M) such that σ0c(k−1) = σmc(k−1) =
sc(k−1) |
. Then there is a σ m-chain of positive ψm-strength from a spel in Vm to c(k−1). |
||||
m |
|
|
|
|
|
Since ψm(c(k−1), c(k)) > 0, σ c(k) |
≥ |
sc(k) |
> 0. |
|
|
|
0 |
m |
|
||
12.3.2 Algorithm
In this subsection, we present an algorithm that produces the M- semisegmentations whose existence and uniqueness are guaranteed by Theorem 1.1. In designing the algorithm we aimed at making it efficient: as is illustrated in the next subsection, our implementation of it allowed us to find 3-segmentations of images with over 10,000 spels in approximately a tenth of a second.
As the algorithm proceeds, it maintains (and repeatedly changes) an M- semisegmentation σ . The claim is that at the time when the algorithm terminates,
σ satisfies the property of Theorem 1.1(i).
The algorithm makes use of a priority queue H of spels c, with associated keys σ0c [26]. Such a priority queue has the property that the key of the spel at its head is maximal (its value is denoted by Maximum-Key(H), which is defined to be 0 if H is empty). As the algorithm proceeds, each spel is inserted into H exactly once (using the operation H ← H {c}) and is eventually removed from
H using the operation Remove-Max(H), which removes the spel c from the head of the priority queue. At the time when a spel c is removed from H, the vector σ c has its final value. Spels are removed from H in a nonincreasing order of the final value of σ0c. We use the variable l to store the current value of Maximum-Key(H). Algorithm 1 shows a detailed specification using the conventions adopted in [26].
The process is initialized (Steps 1–10) by first setting σmc to 0, for each spel c and 0 ≤ m ≤ M. Then, for every seed spel c Vm, c is put into Um and H and

678 |
Herman and Carvalho |
Algorithm 1 Multiobject fuzzy segmentation.
1.for c V
2.do for m ← 0 to M
3.do σmc ← 0
4.H ←
5.for m ← 1 to M
6.do Um ← Vm
7.for c Um
8.do if σ0c = 0 then H ← H { c}
9. |
σ0c ← σmc ← 1 |
10.l ← 1
11.while l > 0
12.for m ← 1 to M
13.do while Um =
14.do remove a spel d from Um
15. |
σ c |
< min(l, ψ (d, c)) and |
|
C ← { c V | cm |
m |
|
σ0 ≤ min(l, ψm(d, c))} |
|
16. |
while C = |
|
17. |
do remove a spel c from C |
|
18. |
t ← min(l, ψm(d, c)) |
|
19. |
if l = t and σmc < l then Um ← Um { c} |
|
20. |
if σ c < t then |
|
|
0 |
|
21. |
if σ0c = 0 |
then H ← H { c} |
22. |
for n ← 1 to M |
|
23. |
do σnc ← 0 |
|
24. |
σ0c ← σmc ← t |
|
25.while Maximum-Key(H) = l
26.Remove-Max(H)
27.l ← Maximum-Key(H)
28.for m ← 1 to M
29.Um ← { c H | σmc = l}
Simultaneous Fuzzy Segmentation of Medical Images |
679 |
both σ0c and σmc are set to 1. Following this, l is also set to 1. At the end of the initialization, the following conditions are satisfied.
(i)σ is an M-semisegmentation of V .
(ii)A spel c is in H if, and only if, 0 < σ0c ≤ l.
(iii)l = Maximum-Key(H).
(iv)For 1 ≤ m ≤ M, Um = {c H | σmc = l}.
The initialization is followed by the main loop of the algorithm. At the beginning of each execution of this loop, conditions (i) to (iv) above are satisfied. The main loop is repeatedly performed for decreasing values of l until l becomes 0, at which time the algorithm terminates (Step 11). There are two parts to the main loop, each of which has a very different function.
The first part of the main loop (Steps 12–24) is the essential part of the algorithm. It is in here where we update our best guess so far of the final values of the σmc . A current value is replaced by a larger one if it is found that there is a
σ m-chain from a seed spel in Vm to c of ψm-strength greater than the old value (the previously maximal ψm-strength of the known σ m-chains of this kind) and it is replaced by 0 if it is found that (for an n = m) there is a σ n-chain from a seed spel in Vn to c of ψn-strength greater than the old value of σmc .
The purpose of the second part of the main loop (Steps 25–29) is to restore the satisfaction of conditions (iii) and (iv) above for a new (smaller) value of l.
To help with the understanding of why this algorithm performs as desired, we comment that just prior to entering its main loop (Steps 11–29), there are four kinds of spels. There are those spels d that have previously been put into and have subsequently been removed from H; for these spels not only does the vector σ d has its final value, but also we have already put into H (and possibly even have already removed from H) every spel c such that ψm(d, c) > 0, for at least one m. (For spels of this first kind, σ0d > l.) Secondly, there are the spels d that are in at least one of the Um; for these spels the vector σ d has its final value, but we may not have yet put into H every spel c such that ψm(d, c) > 0 for at least one m. (For spels of this second kind, σ0d = σmd = l.) This will get done in the next execution of Steps 13–21, while Steps 22–24 will insure that the σ c get updated appropriately. Consequently, the spels c which are in H but not in any of the Um are those for which there is, for some 1 ≤ m ≤ M, a σ m-chain (for the
680 |
Herman and Carvalho |
current σ ) from a seed spel in Vm to c; for the rest of the spels (those which have not as yet been put into H) there is no m for which there is a σ m-chain (for the current σ ) from a seed spel in Vm to c. (For spels c of these third and fourth kinds, 0 < σ0c < l and σ0c = 0, respectively.)
One tricky aspect of the algorithm is that a spel of the third kind may become a spel of the second kind and a spel of the fourth kind may become a spel of the third (or even of the second) kind during the execution of the main loop. That the description of the four kinds of spels remains as given in the previous paragraph is insured by Steps 19 and 21. (Step 21 also insures that condition (ii) stated above remains satisfied. To see this, observe that Step 15 guarantees that if c is put into C, then 0 < min(l, ψm(d, c)) and consequently the t defined in Step 18 and used in Step 24 is also positive. That condition (i) stated above remains satisfied is obvious from Steps 20–24.)
We complete this subsection with a brief discussion of our implementation of Algorithm 1. As suggested in [26], we use a heap to implement the priority queue H. This provides us with efficient implementations of the operations of insertion into (H ← H c) and removal from (Remove-Max(H)) the priority queue, as well as of Step 29. In applications it is typically the case that, for every
spel d, there is a fixed number of spels c such that mM=1ψm(d, c) > 0 and a list of all such c is inexpensive to produce. In such a case the cost of executing Step 15 becomes proportional to a constant (four, six, or twelve in the examples shown below and in Section 12.4) independent of the size of V . Using L to denote this constant, the computational complexity of the Algorithm 1 is the following: since each spel can belong to multiple objects there can be at most M|V | executions of the loop 13–24, while the loop 16–24 can be executed at most L times. Steps 19 and 24 have O (log |V |) operations while Steps 22–23 have O (M) operations, so the loop 16–24 has O (M log |V |) operations. Since this loop can be executed at most ML|V | times, the time complexity of Algorithm 1 is O (M2L|V | log |V |).
12.3.3 Experiments
Now we demonstrate the usage of Algorithm 1 on mathematically-defined as well as on real images. Similarly to the example shown in section 12.2, the appropriate fuzzy spel affinities were automatically defined by a computer program, based on some minimal information supplied by a user. However, this is not the only option: for example, if sufficient prior knowledge about the class of

Simultaneous Fuzzy Segmentation of Medical Images |
681 |
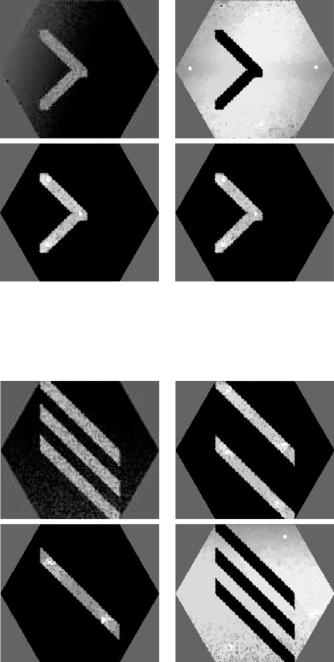
Figure 12.3: A mathematically defined image (top left) including both background variation and noise, and the corresponding 3-segmentation (top right and bottom row).
segmentation problems to which the application at hand belongs is available, then the whole segmentation process can be automated by designing a program that automatically selects the seeds for the objects to be segmented, as it was done in [30] to segment macromolecules in electron microscopy volumes.
On the top-left of Figs. 12.3–12.7 and in the left column of Fig. 12.8 are images defined on a V consisting of regular hexagons that are inside a large hexagon (with 60 spels on each side, a total of 10,621 spels). In all these examples, M = 3. For these experiments we defined Vm (1 ≤ m ≤ 3) to be the set of spels indicated by the user plus their six neighbors. The fuzzy affinity functions ψm (1 ≤ m ≤ 3) were computed according to Eqs. (12.2) and (12.3), with adjacency π between hexagons meaning that they share an edge.
The other three images of Figs. 12.3–12.7 represent the resulting σm (obtained by Algorithm 1) with the brightness of each spel encoding its grade of membership in an object. (For Fig. 12.3 we selected the seed spels so that V1 = V2, for Fig. 12.4 we selected the seed spels so that V2 = V3, and for Figs. 12.5–12.7 the three sets of seed spels are pairwise disjoint, which happens to result, because of the large number of gray levels used in the images