
- •CCIE Security Written Exam Blueprint
- •General Networking Topics
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Networking Basics—The OSI Reference Model
- •Ethernet Overview
- •Internet Protocol
- •Variable-Length Subnet Masks
- •Classless Interdomain Routing
- •Transmission Control Protocol
- •TCP Services
- •Routing Protocols
- •ISDN
- •IP Multicast
- •Asynchronous Communications and Access Devices
- •Foundation Summary
- •Requirements for FastEther Channel
- •Scenario
- •Scenario 2-1: Routing IP on Cisco Routers
- •Scenario Answers
- •Scenario 2-1 Answers: Routing IP on Cisco Routers
- •Application Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Domain Name System
- •Trivial File Transfer Protocol
- •File Transfer Protocol
- •Hypertext Transfer Protocol
- •Secure Socket Layer
- •Simple Network Management Protocol
- •Simple Mail Transfer Protocol
- •Network Time Protocol
- •Secure Shell
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Scenario 3-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Cisco Hardware
- •show and debug Commands
- •Password Recovery
- •Basic Security on Cisco Routers
- •IP Access Lists
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Security Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Authentication, Authorization, and Accounting (AAA)
- •Remote Authentication Dial-In User Service (RADIUS)
- •Kerberos
- •Virtual Private Dial-Up Networks (VPDN)
- •Encryption Technology Overview
- •Internet Key Exchange (IKE)
- •Foundation Summary
- •Scenario
- •Scenario 5-1: Configuring Cisco Routers for IPSec
- •Scenario Answers
- •Scenario 5-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •UNIX
- •Microsoft NT Systems
- •Common Windows DOS Commands
- •Cisco Secure for Windows and UNIX
- •Cisco Secure Policy Manager
- •Cisco Secure Intrusion Detection System and Cisco Secure Scanner
- •Cisco Security Wheel
- •Foundation Summary
- •Scenarios
- •Scenario 6-1: NT File Permissions
- •Scenario 6-2: UNIX File Permissions
- •Scenario Answers
- •Scenario 6-1 Solution
- •Scenario 6-2 Solution
- •Security Technologies
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Advanced Security Concepts
- •Cisco Private Internet Exchange (PIX)
- •Cisco IOS Firewall Security Feature Set
- •Public Key Infrastructure
- •Virtual Private Networks
- •Foundation Summary
- •Scenario
- •Scenario Answer
- •Scenario 7-1 Solution
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Network Security Policies
- •Standards Bodies and Incident Response Teams
- •Vulnerabilities, Attacks, and Common Exploits
- •Intrusion Detection System
- •Protecting Cisco IOS from Intrusion
- •Foundation Summary
- •Scenario
- •Scenario 8-1: Defining IOS Commands to View DoS Attacks in Real Time
- •Scenario Answer
- •Scenario 8-1 Solution

Vulnerabilities, Attacks, and Common Exploits 369
Vulnerabilities, Attacks, and Common Exploits
This section covers some of the vulnerabilities in TCP/IP and the tools used to exploit IP networks.
TCP/IP is an open standard protocol, which means that both network administrators and intruders are aware of the TCP/IP architecture and vulnerabilities.
NOTE There are a number of network vulnerabilities, such as password protection, lack of authentication mechanism, use of unprotected routing protocols, and firewall holes. This section concentrates on TCP/IP vulnerabilities.
Network intruders can capture, manipulate, and replay data. Intruders typically try to cause as much damage to a network as possible by using the following methods:
•Vandalizing—Accessing the web server and altering web pages.
•Manipulating data—Altering the files on a network device.
•Masquerading—Manipulating TCP/IP segments to pretend to be at a valid IP address.
•Session replay—Capturing, altering, and replaying a sequence of packets to causes unauthorized access. This method identifies weaknesses in authentication.
•Session hijacking—Defining himself with a valid IP address after a session has been established to the real IP address by spoofing IP packets and manipulating the sequence number in IP packets.
•Rerouting—Routing packets from one source to an intruder source; altering routing updates to send IP packets to an incorrect destination, allowing the intruder to read and use the IP data inappropriately.
The following are some of the attacking methods intruders use:
•
•
•
•
Probes and scans
Denial-of-Service (DoS) attacks (covered in more detail later)
Compromises
Malicious code (such as viruses)
As described in Chapter 6, “Operating Systems and Cisco Security Applications,” network scanners and tools are available to both network administrators and intruders. These tools can be used and placed at strategic points in the network to gain access to sensitive data. NetSonar, for example, can be used to find network vulnerabilities and can, therefore, be used by intruders to do as much harm as it does network administrators good if you aren’t aware of these vulnerabilities.
370 Chapter 8: Network Security Policies, Vulnerabilities, and Protection
DoS attacks are the most common form of attack used by intruders and can take many forms. The intruder’s goal is to ultimately deny access to authorized users and tie up valuable system resources.
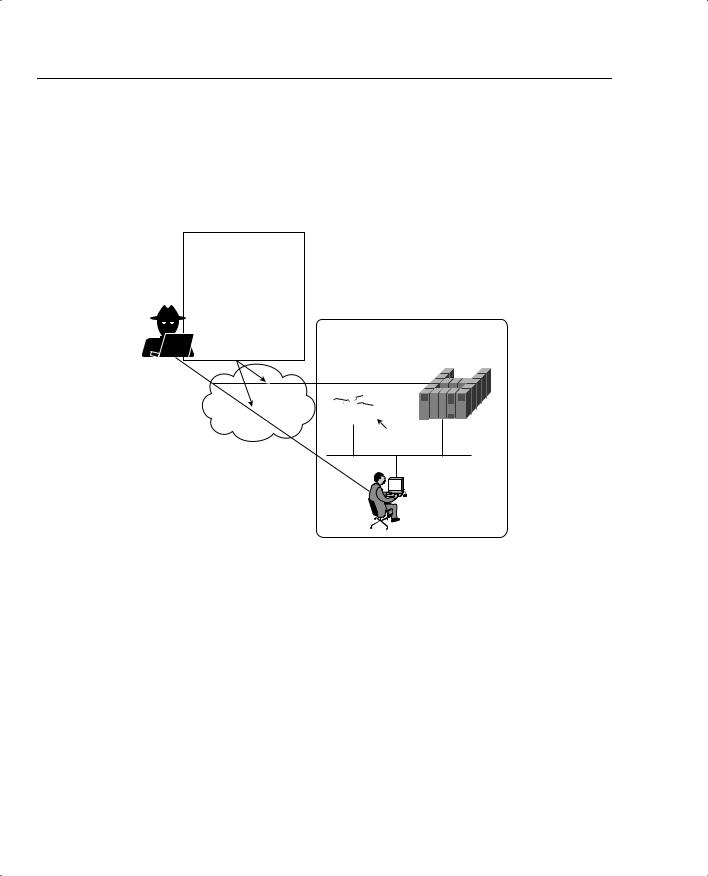
Figure 8-1 displays several techniques deployed in DoS attacks.
Figure 8-1 Forms of Denial of Service Attack
Denial of Service (DoS)
attacks include
-TCP SYN flood attacks -WinNuke -Land.C
-Ping of Death
-Chargen Attacks
-DNS Poisoning
Private Network
Host or
Bastion Hosts


 R1
R1
Vulnerable Cisco
IOS Router
Authorized
Users
Figure 8-1 displays a typical network scenario with a router connected to the Internet and all users have access to hosts in a public domain. A bastion host is a computer or host, such as a UNIX host, that plays a critical role in enforcing any organization’s network security policy.
Bastion hosts are typically highly secured (including physically in secure computer rooms), as these hosts are vulnerable to attacks because they are exposed to untrusted or unknown networks and are the first line of defense. Bastion hosts often provide services to Internet users, such as Web services (WWW), and public access systems, such as FTP or SMTP mail. Because these computers are likely to be attacked, they are often referred to as sacrificial hosts.

Vulnerabilities, Attacks, and Common Exploits 371
The intruder in Figure 8-1 attacks the authorized users and hosts (or bastion host) behind a router by a number of methods, including the following:
•Ping of death—Attack that sends an improperly large ICMP echo request packet with the intent of overflowing the input buffers of the destination machine and causing it to crash. The IP protocol header field is set to 1, the last fragment bit is set, and the data length is greater than 65,535, which is greater than the maximum allowable IP packet size.
•TCP SYN Flood attacks—This form of DoS attack randomly opens up a number of TCP ports ensuring that network devices are using CPU cycles for bogus requests. By tying up valuable resources on the remote host, the CPU is tied up with bogus requests, and legitimate users experience poor network response or are denied access. This type of attack can make the host unusable.
•E-mail attacks—This form of DoS attack sends a random number of e-mails to a host. E-mail attacks try to fill an inbox with bogus e-mails, ensuring that the end user cannot send mail while thousands (or an e-mail bomb) of e-mails are received.
•CPU-intensive attacks—This DoS attack ties up systems’ resources by using programs such as TROJAN (a program designed to capture username/passwords from a network), or enabling viruses to disable remote systems.
•Teardrop—Exploits an overlapping IP fragment implementation bug in various operating systems. The bug causes the TCP/IP fragmentation reassembly code to improperly handle overlapping IP fragments causing the host to hang or crash.
•DNS poisoning—The attacker exploits the DNS server, causing the server to return a false IP address to a domain name query.
•UDP Bomb—Sends illegal length field in the packet header, causing Kernel panic and crash.
•Distributed Denial Of Service (DDoS)—These DoS attacks are run by multiple hosts. The attacker first compromises vulnerable hosts using various tools and techniques. Then, the actual DOS attack on a target is run from the pool of all the compromised hosts.
•Chargen attacks—Establish a User Datagram Protocol (UDP) service by producing a high-character input. This can cause congestion on a network.
•Attacks via dialup (out of band)—Applications such as Windows 95 have built-in vulnerabilities on data port 139 (known as WinNuke) if the intruders can ascertain the IP address.
•Land.C attacks—A program designed to send TCP SYN packets (TCP SYN is used in the TCP connection phase) that specifies the target’s host address as both source and destination. This program can use TCP port 113 or 139 (source/destination), which can also cause a system to stop functioning.

372 Chapter 8: Network Security Policies, Vulnerabilities, and Protection
DoS attacks are designed to send traffic to host systems so that they cannot respond to legitimate traffic by overwhelming the end device through a number of incomplete and illegal connections or requests. DoS attacks send more traffic than is possible to process and can send excessive mail requests, excessive UDP packets, and excessive Internet Control Message Protocol (ICMP) pings with very large data packet sizes to render a remote host unusable.
Many other known and unknown attacking methods and terms exist. Here are a few more you should be aware of for the written exam:
•Spoof attack—The attacker creates IP packets with an address found (or spoofed) from a legitimate source. This attack is powerful in situations where a router is connects to the Internet with one or more internal addresses. The real solution to this form of attack is to track down the source device and stop the attack.
•Smurf attack—Named after its exploit program and one of the most recent in the category of network-level attacks against hosts. In this attack, an intruder sends a large amount of ICMP echo (ping) traffic to IP broadcast addresses, which all have a victim’s spoofed source address. For more details, go to www.cert.org/advisories/CA-1998-01.html.
Smurf attacks include a primary and secondary victim and are extremely potent damaging to any IP network. Smurf attacks result in a large number of broadcast ICMP networks, and if routers are configured to forward, broadcasts can result in a degraded network and poor performance between the primary and secondary device. A quick solution is to disable IP-directed broadcasts.
•Man in the middle attack—Just as with packet sniffers and IP spoofing attacks, a bruteforce password attack can provide access to accounts that can be used to modify critical network files and services. An example that compromises your network’s integrity is an attacker modifying your network’s routing tables. By doing so, the attacker ensures that all network packets are routed to him before they are transmitted to their final destination. In such a case, an attacker can monitor all network traffic, effectively becoming a man in the middle.
•Birthday attack—Refers to a class of brute-force attacks. It gets its name from the surprising fact that the probability that two or more people in a group of 23 share the same birthday is greater than 50 percent; such a result is called a birthday paradox.
Intrusion Detection System
Intrusion detection systems (IDS) are designed to detect and thwart network attacks. Based on their location, they can be either of the following:
•Network IDS—Examines or sniffs every packet flowing across the network and generates an alarm upon detection of a network attack signature.
•Host IDS—Examines operating system information such as logs or system process, against a base line. When the system deviates from the normal values because of an attack, alarms are generated.

Intrusion Detection System 373
Chapter 6 defines some of the intrusion detection mechanisms you can use in an IP network, namely NetRanger.
Cisco IDS delivers a comprehensive, pervasive security solution for combating unauthorized intrusions, malicious Internet worms, and bandwidth and e-Business application attacks.
Recently, Cisco announced a number of new products to support IDS:
•Cisco IDS Host Sensor 2.5—Bolsters enterprise security by delivering unparalleled levels of protection and customization to customers
•Cisco IDS 4250 Appliance Sensor—Raises the performance bar for high-throughput gigabit protection in a performance-upgradable IDS chassis
•Cisco IDS 4235 Appliance Sensor—Provides enterprise-class intrusion protection at new price/performance levels
•Cisco IDS 3.1 Sensor Software—Delivers powerful web-based, embedded device management, graphical security analysis, and data mining capabilities
NOTE In addition to the Cisco IDS 4200 series of IDS appliances, Cisco also has the following IDS sensors:
•IOS with IDS feature set for routers
•Catalyst 6500 IDS module for switch-based sensor
•PIX Firewall with version 6.x with built-in IDS sensor
•Cisco IDS Host sensor for Windows, Solaris OS, and web servers, such as IIS and Apache
You are not expected to know these details for the written exam; they are presented here for completeness only.
Each Cisco IDS sensor can be configured to support a number of different signatures. A Signature Engine is a component of the Cisco IDS sensor designed to support many signatures in a certain category. An engine is composed of a parser and an inspector. Each engine has a set of legal parameters that have allowable ranges or sets of values. Exploit signatures are an identifiable pattern of attack detected by your network device, such as a Cisco IDS Host sensor.
Table 8-1 displays the signature lists and descriptions available with Cisco IDS version 3.1.
IDS can be used, for example, to detect spam e-mail and still allow regular e-mail. Most ISPs do not detect or remove spam e-mail, so it is up to the security administrator to ensure that spam e-mail is not permitted or used as a DoS attack.

374 Chapter 8: Network Security Policies, Vulnerabilities, and Protection
Table 8-1 Cisco IDS Signature Engines*
Signature Engine |
Description |
|
|
ATOMIC.ICMP |
Simple ICMP alarms based on the following parameters: type, code, |
|
sequence, and ID |
|
|
ATOMIC.IPOPTIONS |
Simple alarms based on the decoding of Layer 3 options |
|
|
ATOMIC.L3.IP |
Simple Layer 3 IP alarms |
|
|
ATOMIC.TCP |
Simple TCP packet alarms based on the following parameters: port, |
|
destination, and flags |
|
|
ATOMIC.UDP |
Simple UDP packet alarms based on the following parameters: port, |
|
direction, and data length |
|
|
FLOOD.HOST.ICMP |
ICMP floods directed at a single host |
|
|
FLOOD.HOST.UDP |
UDP floods directed at a single host |
|
|
FLOOD.NET |
Multiprotocol floods directed at a network segment |
|
|
FLOOD.TCPSYN |
Connections to multiple ports using TCP SYN |
|
|
SERVICE.DNS.TCP |
Domain Name Service (DNS) packet analyzer on TCP port 53 (includes |
|
compression handler) |
|
|
SERVICE.DNS.UDP |
UDP-based DNS signatures |
|
|
SERVICE.PORTMAP |
Remote Procedure Call (RPC) program number sent to port mapper |
|
|
SERVICE.RPC |
Simple RPC alarms based on the following parameters: program, |
|
procedure, and length |
|
|
STATE.HTTP |
Stateful HTTP protocol decode-based string search (includes anti-evasive |
|
URL deobfuscation) |
|
|
STRING.HTTP |
Specialized STRING.TCP alarms for Web traffic (includes anti-evasive |
|
URL deobfuscation) |
|
|
STRING.ICMP |
Generic ICMP-based string search engine |
|
|
STRING.TCP |
Generic TCP-based string search engine |
|
|
STRING.UDP |
Generic UDP-based string search engine |
|
|
SWEEP.HOST.ICMP |
A single host sweeping a range of nodes using ICMP |
|
|
SWEEP.HOST.TCP |
A single host sweeping a range of nodes using TCP |
|
|
SWEEP.PORT.TCP |
TCP connections to multiple destination ports between two nodes |
|
|
SWEEP.PORT.UDP |
UDP connections to multiple destination ports between two nodes |
|
|
SWEEP.RPC |
Connections to multiple ports with RPC requests between two nodes |
|
|
*The information in Table 8-1 is from Table 1 at the Cisco web page, www.cisco.com/en/US/partner/products/sw/ secursw/ps2113/prod_technical_reference09186a00800d9dd5.html#56785.
