
- •CCIE Security Written Exam Blueprint
- •General Networking Topics
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Networking Basics—The OSI Reference Model
- •Ethernet Overview
- •Internet Protocol
- •Variable-Length Subnet Masks
- •Classless Interdomain Routing
- •Transmission Control Protocol
- •TCP Services
- •Routing Protocols
- •ISDN
- •IP Multicast
- •Asynchronous Communications and Access Devices
- •Foundation Summary
- •Requirements for FastEther Channel
- •Scenario
- •Scenario 2-1: Routing IP on Cisco Routers
- •Scenario Answers
- •Scenario 2-1 Answers: Routing IP on Cisco Routers
- •Application Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Domain Name System
- •Trivial File Transfer Protocol
- •File Transfer Protocol
- •Hypertext Transfer Protocol
- •Secure Socket Layer
- •Simple Network Management Protocol
- •Simple Mail Transfer Protocol
- •Network Time Protocol
- •Secure Shell
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Scenario 3-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Cisco Hardware
- •show and debug Commands
- •Password Recovery
- •Basic Security on Cisco Routers
- •IP Access Lists
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Security Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Authentication, Authorization, and Accounting (AAA)
- •Remote Authentication Dial-In User Service (RADIUS)
- •Kerberos
- •Virtual Private Dial-Up Networks (VPDN)
- •Encryption Technology Overview
- •Internet Key Exchange (IKE)
- •Foundation Summary
- •Scenario
- •Scenario 5-1: Configuring Cisco Routers for IPSec
- •Scenario Answers
- •Scenario 5-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •UNIX
- •Microsoft NT Systems
- •Common Windows DOS Commands
- •Cisco Secure for Windows and UNIX
- •Cisco Secure Policy Manager
- •Cisco Secure Intrusion Detection System and Cisco Secure Scanner
- •Cisco Security Wheel
- •Foundation Summary
- •Scenarios
- •Scenario 6-1: NT File Permissions
- •Scenario 6-2: UNIX File Permissions
- •Scenario Answers
- •Scenario 6-1 Solution
- •Scenario 6-2 Solution
- •Security Technologies
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Advanced Security Concepts
- •Cisco Private Internet Exchange (PIX)
- •Cisco IOS Firewall Security Feature Set
- •Public Key Infrastructure
- •Virtual Private Networks
- •Foundation Summary
- •Scenario
- •Scenario Answer
- •Scenario 7-1 Solution
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Network Security Policies
- •Standards Bodies and Incident Response Teams
- •Vulnerabilities, Attacks, and Common Exploits
- •Intrusion Detection System
- •Protecting Cisco IOS from Intrusion
- •Foundation Summary
- •Scenario
- •Scenario 8-1: Defining IOS Commands to View DoS Attacks in Real Time
- •Scenario Answer
- •Scenario 8-1 Solution
132 Chapter 3: Application Protocols
Example 3-11 displays that R2 is dynamically peered to R1 and is authenticated.
Secure Shell
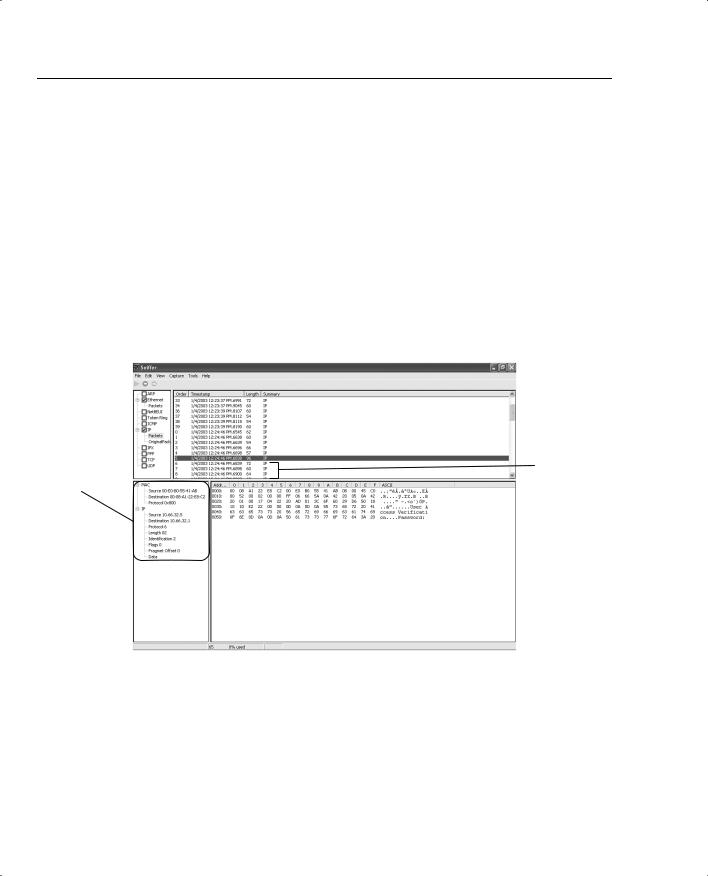
Secure Shell (SSH) is a protocol that provides a secure connection to a router. Cisco IOS supports version 1 of SSH, which enables clients to make a secure and encrypted connection to a Cisco router. Before SSH was implemented, the only form of security available when accessing devices such as routers was Telnet username/password authentication, which is clearly visible with a network sniffer. Telnet is insecure because a protocol analyzer can view the information in clear text form. Figure 3-8 displays a simple protocol analyzer viewing information between a source address, 10.66.32.5, and the destination address 192.168.1.13 after a Telnet session is initiated by the address (PC) 192.168.1.13/24.
Figure 3-8 Sniffer Capture of a Telnet Connection
Password will be
Detailed IP
viewable in
Information
these frames.
Figure 3-8 displays a simple Telnet connection between a PC and a remote router. Figure 3-8 is a packet trace from a client PC Telnet connection to a Cisco IOS router with the IP address 10.32.66.5. The packet trace clearly captures the password prompt sent by the router. Therefore, the prompt is viewable in clear text. If you scrolled down the next few frames (frames numbered 98-103 in Figure 3-8), the password would be clearly visible. An intruder or hacker can piece together the password and gain unauthorized access. For security reasons, these frames are not shown, but it is clear that the Telnet application protocol is not a secure protocol; all data is sent as clear text (including the password exchanged).
Secure Shell 133
SSH is implemented with TCP port 22 and UDP port 22, and ensures that data is encrypted and untraceable by a network sniffer. SSH can be configured on both Cisco IOS routers and Catalysts switches.
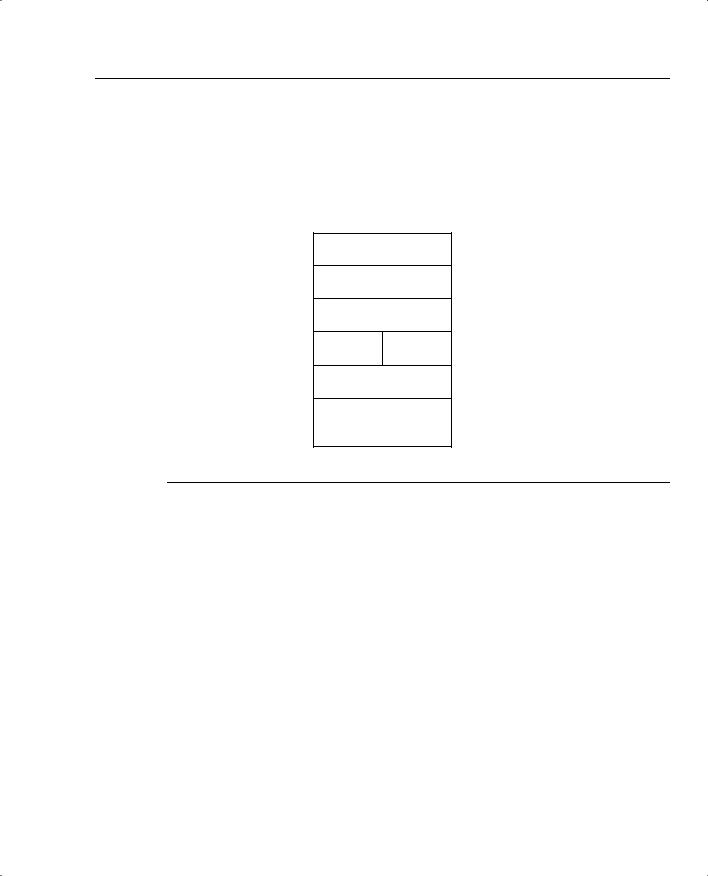
Figure 3-9 displays the SSH protocol layers.
Figure 3-9 SSH Protocol Layers
SSH Connection Layer
SSH Authentication Layer
SSH Transport Layer
TCP UDP
IP
Network Interface
NOTE |
Lightweight Directory Access Protocol (LDAP) is an Internet protocol that e-mail programs |
|
use to look up contact information from a server. For more details on LDAP, visit |
|
www.gracion.com/server/whatldap.html. |
|
Active Directory is a Windows-defined application that stores and manages network services, |
|
resources, and information about where computers and printers are located. Active Directory |
|
allows network administrators of 2000 servers the ability to allocate and control how network |
|
resources are accessed by clients’ PCs. For more information on Active Directory, visit |
|
www.microsoft.com. |
|
|
|
SSH sits on top of the TCP/IP layers, protecting the hosts from unknown devices. The SSH |
|
transport layer is responsible for securing the data using strong encryption authentication. |
|
There are currently two versions of SSH: SSHv1 and SSHv2. Cisco IOS only supports SSHv1. |
|
UNIX devices support SSH clients and Cisco routers can be configured to allow SSH between |
|
the UNIX device and Cisco router to ensure a secure Telnet connection. Currently, Cisco IOS |
|
12.2 supports SSH and a number of hardware platforms, including the 2600 and 3600 series |
|
routers. |
|
For more detailed information on SSH and the Cisco IOS functional matrix, visit |
|
www.ssh.com/products/ssh/ and www.cisco.com/warp/public/707/ssh.shtml, respectively. |

134 Chapter 3: Application Protocols
Foundation Summary
The “Foundation Summary” is a condensed collection of material for a convenient review of this chapter’s key concepts. If you are already comfortable with the topics in this chapter and decided to skip most of the “Foundation Topics” material, the “Foundation Summary” will help you recall a few details. If you just read the “Foundation Topics” section, this review should help further solidify some key facts. If you are doing your final preparation before the exam, the “Foundation Summary” offers a convenient and quick final review.
Table 3-5 |
DNS Concepts |
|
|
|
|
|
|
|
Concept |
|
Description |
|
|
|
|
|
Well-known port numbers |
|
UDP Port 53, TCP Port 53 |
|
|
|
|
|
ip host name [tcp-port-number] |
Configured locally to assign a host name with up to 8 IP |
|
|
ip address1 [ip address2...ip address8] |
addresses |
|
|
|
|
|
|
no ip domain-lookup |
|
Disables the IP DNS-based host name-to-address translation |
|
|
|
|
|
ip domain-name name |
|
Defines a default domain name that the Cisco IOS Software |
|
|
|
uses to complete unqualified host names |
|
|
|
|
|
ip domain-list name |
|
Defines a list of default domain names to complete |
|
|
|
unqualified host names |
|
|
|
|
|
ip name-server ip address |
|
Specifies the address of one or more name servers to use for |
|
|
|
name and address resolution; up to six name servers |
|
|
|
permitted |
Table 3-6 |
|
|
|
TFTP Concepts |
|
|
|
|
|
|
|
|
Concept |
Description |
|
|
|
|
|
|
Well-known port numbers |
UDP Port 69 (UDP is typically the only supported protocol for TFTP |
|
|
|
produced by vendors) and TCP Port 69 |
|
|
|
|
|
|
copy tftp flash |
Cisco IOS command to copy images from a TFTP server |
|
|
|
|
|
|
Security |
Only filename and directory name are methods used to secure transfers |
|
Table 3-7 |
|
|
|
Secure Shell (SSH) Concepts |
|
|
|
|
|
|
|
|
Concept |
Description |
|
|
|
|
|
|
Well-known port number |
TCP port 443. |
|
|
|
|
|
|
HTTPS |
HTTP traffic runs over a secure connection. |
|
|
|
|
|
|
Service/client |
SSH uses a client server model where clients request secure connections |
|
|
authentication |
to a host device, such as with a credit card transaction over the World |
|
|
|
Wide Web. |
|
|
|
|
|

|
|
|
|
Foundation Summary 135 |
|
|
|
|
|
Table 3-8 |
SNMP Concepts |
|
|
|
|
|
|
|
|
|
Concept |
|
Description |
|
|
|
|
|
|
|
Well-known port numbers |
|
UDP 161 (SNMP servers) and UDP 162 (SNMP clients). |
|
|
|
|
|
|
|
SNMP managed devices |
|
An SNMP managed device is a network node that contains an SNMP |
|
|
|
|
agent and resides on a managed network. Managed devices collect and |
|
|
|
|
store management information and make this information available to |
|
|
|
|
Network Management System using SNMP. |
|
|
|
|
|
|
|
SNMP agent |
|
SNMP Agent is a network management software module that resides in a |
|
|
|
|
managed device. An agent has local knowledge of management |
|
|
|
|
information and translates that information into a form compatible with |
|
|
|
|
SNMP. |
|
Table 3-9 |
|
|
|
|
SMTP Concepts |
|
|
||
|
|
|
|
|
|
Concept |
|
Description |
|
|
|
|
|
|
|
Well-known port numbers |
|
TCP 25 and UDP 25 |
|
|
|
|
|
|
|
HELO command |
|
Used in communications between host and client |
|
Table 3-10 |
|
|
|
|
NTP Concepts |
|
|
||
|
|
|
|
|
|
Concept |
|
Description |
|
|
|
|
|
|
|
Well-known port numbers |
|
TCP 123 and UDP 123. |
|
|
|
|
|
|
|
ntp master 1-15 |
|
Defines stratum value between 1 and 15. |
|
|
|
|
||
|
clock set hh:mm:ss day month year |
Manually sets clock on a Cisco router. |
||
|
|
|
||
|
ntp peer ip-address [version number] [key |
Defines NTP peers. |
||
|
keyid] [source interface] [prefer] |
|
||
|
|
|
|
|
|
ntp authenticate |
|
Enables authentication. |
|
|
|
|
||
|
ntp authentication-key number md5 value |
Defines NTP authentication key and password. |
||
|
|
|
|
|
|
ntp trusted-key key-number |
|
Defines NTP to authenticate NTP session; key-number |
|
|
|
|
|
is the authentication key to be trusted. |
|
|
|
|
|

136 Chapter 3: Application Protocols
Q & A
The Q & A questions are designed to help you assess your readiness for the topics covered on the CCIE Security written exam and those topics presented in this chapter. This format should help you assess your retention of the material. A strong understanding of the answers to these questions will help you on the CCIE Security written exam. You can also look over the questions at the beginning of the chapter again for review. As an additional study aid, use the CD-ROM provided with this book to take simulated exams, which draw from a database of over 300 multiple-choice questions—all different from those presented in the book. Select the best answer. Answers to these questions can be found in Appendix A, “Answers to Quiz Questions.”
1According to RFC 1700, what is the well-known TCP/UDP port used by DNS?
2What does the IOS command no ip domain-lookup accomplish?
3What is the correct IOS syntax to specify local host mapping on a Cisco router?
4TFTP uses what well-known, defined TCP/UDP port?
5What is the correct IOS command to copy a file from a TFTP server to the system flash?

Q & A 137
6Define the two modes of FTP.
7FTP uses what TCP port numbers?
8What well-known port do Secure Socket Layer (SSL) and Secure Shell (SSH) use?
9Define SNMP and give an example.
10What well-known UDP ports are used by SNMP?
11What IOS command enables SNMP on a Cisco IOS router?
12Which TCP/UDP port numbers are defined for use by Network Time Protocol or NTP?

138 Chapter 3: Application Protocols
13When defining a stratum value on a Cisco router, what is the range and what value is closest to an atomic clock?
14Secure Shell (SSH) allows what to be accomplished when in use?
15What is the difference between an SNMP inform request and an SNMP trap?
16What does the SNMP MIB refer to?
17What is the SNMP read-write community string for the following router configuration?
snmp-server community simon ro snmp-server community Simon rw
18Before you can TFTP a file from a Cisco router to a UNIXor Windows-based system, what is the first step you must take after enabling the TFTP server daemon on both platforms?

Q & A 139
19What IOS command can be implemented to restrict SNMP access to certain networks by applying access lists? Can you apply standard, extended, or both?
20Does TFTP have a mechanism for username and password authentication?
21Can you use your Internet browser to configure a Cisco router? If so, how?
22A network administrator defines a Cisco router to allow HTTP requests but forgets to add the authentication commands. What is the default username and password pairing that allows HTTP requests on the default TCP port 80? Can you predefine another TCP port for HTTP access other than port 80?
