
- •CCIE Security Written Exam Blueprint
- •General Networking Topics
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Networking Basics—The OSI Reference Model
- •Ethernet Overview
- •Internet Protocol
- •Variable-Length Subnet Masks
- •Classless Interdomain Routing
- •Transmission Control Protocol
- •TCP Services
- •Routing Protocols
- •ISDN
- •IP Multicast
- •Asynchronous Communications and Access Devices
- •Foundation Summary
- •Requirements for FastEther Channel
- •Scenario
- •Scenario 2-1: Routing IP on Cisco Routers
- •Scenario Answers
- •Scenario 2-1 Answers: Routing IP on Cisco Routers
- •Application Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Domain Name System
- •Trivial File Transfer Protocol
- •File Transfer Protocol
- •Hypertext Transfer Protocol
- •Secure Socket Layer
- •Simple Network Management Protocol
- •Simple Mail Transfer Protocol
- •Network Time Protocol
- •Secure Shell
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Scenario 3-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Cisco Hardware
- •show and debug Commands
- •Password Recovery
- •Basic Security on Cisco Routers
- •IP Access Lists
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Security Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Authentication, Authorization, and Accounting (AAA)
- •Remote Authentication Dial-In User Service (RADIUS)
- •Kerberos
- •Virtual Private Dial-Up Networks (VPDN)
- •Encryption Technology Overview
- •Internet Key Exchange (IKE)
- •Foundation Summary
- •Scenario
- •Scenario 5-1: Configuring Cisco Routers for IPSec
- •Scenario Answers
- •Scenario 5-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •UNIX
- •Microsoft NT Systems
- •Common Windows DOS Commands
- •Cisco Secure for Windows and UNIX
- •Cisco Secure Policy Manager
- •Cisco Secure Intrusion Detection System and Cisco Secure Scanner
- •Cisco Security Wheel
- •Foundation Summary
- •Scenarios
- •Scenario 6-1: NT File Permissions
- •Scenario 6-2: UNIX File Permissions
- •Scenario Answers
- •Scenario 6-1 Solution
- •Scenario 6-2 Solution
- •Security Technologies
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Advanced Security Concepts
- •Cisco Private Internet Exchange (PIX)
- •Cisco IOS Firewall Security Feature Set
- •Public Key Infrastructure
- •Virtual Private Networks
- •Foundation Summary
- •Scenario
- •Scenario Answer
- •Scenario 7-1 Solution
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Network Security Policies
- •Standards Bodies and Incident Response Teams
- •Vulnerabilities, Attacks, and Common Exploits
- •Intrusion Detection System
- •Protecting Cisco IOS from Intrusion
- •Foundation Summary
- •Scenario
- •Scenario 8-1: Defining IOS Commands to View DoS Attacks in Real Time
- •Scenario Answer
- •Scenario 8-1 Solution
File Transfer Protocol 115
Example 3-6 TFTP File Transfer (Continued)
[OK - 11432808/22864896 bytes] Verifying checksum... OK (0xBC59)
11432808 bytes copied in 106.126 secs (107856 bytes/sec) R1#
The file (c2600-js-mz.121-5.T10.bin) is successfully copied and placed on the flash system on Router R1. The only two mechanisms for security permitted with TFTP are the filename and directory. TFTP has no mechanism for checking username and password. On a UNIX server where the TFTP server daemon is installed, the file to be copied must have the appropriate access rights. In UNIX, the Touch command is used to allow a TFTP request. For a Windowsbased platform, the software must be configured to permit file creation on the Windows-based file system.
FTP, on the other hand, is a connection-based protocol, where username and password combinations are used to authorize file transfers.
File Transfer Protocol
File Transfer Protocol (FTP), an application layer protocol of the TCP/IP protocol suite of applications, allows users to transfer files from one host to another. Two ports are required for FTP—one port is used to open the connection (port 21), and the other port is used to transfer data (20). FTP runs over TCP and is a connection-oriented protocol. To provide security, FTP allows usernames and passwords to be exchanged before any data can be transferred, adding some form of security authentication mechanism to ensure that only valid users access FTP servers.
The advantages of FTP are the ability to list a remote FTP server’s full list of directories and ensure that only valid users are connected. The file transfer progress can be displayed to the FTP client, as well. Many FTP applications are available, and the range of options is endless. For example, on the CCIE Security lab exam, the application Reflection 2000 can be used for Telnet and FTP. For more details on this application, visit www.wrq.com/products/reflection/.
NOTE FTP connection issues are typically communicated by end users (FTP clients) as poor network performance when the problem might actually be a result of filtering the FTP data on port 20. For example, when a client successfully logs into an FTP server remotely but fails to list the remote FTP server’s directory or to transfer files, this can indicate a problem with the FTP data port (via TCP port 20) or an access list problem on the remote network.
116 Chapter 3: Application Protocols
FTP clients can be configured for two modes of operation:
•
•
Active mode
Passive mode
Active FTP
Active FTP is defined as one connection initiated by the client to the server for FTP control connection. Remember that FTP requires two port connections through TCP ports 20 (data) and 21 (control). The second connection is made for the FTP data connection (where data is transferred), which is initiated from the server back to the client.
Active FTP is less secure than passive mode because the FTP server, which, in theory, could be any host, initiates the data channel.
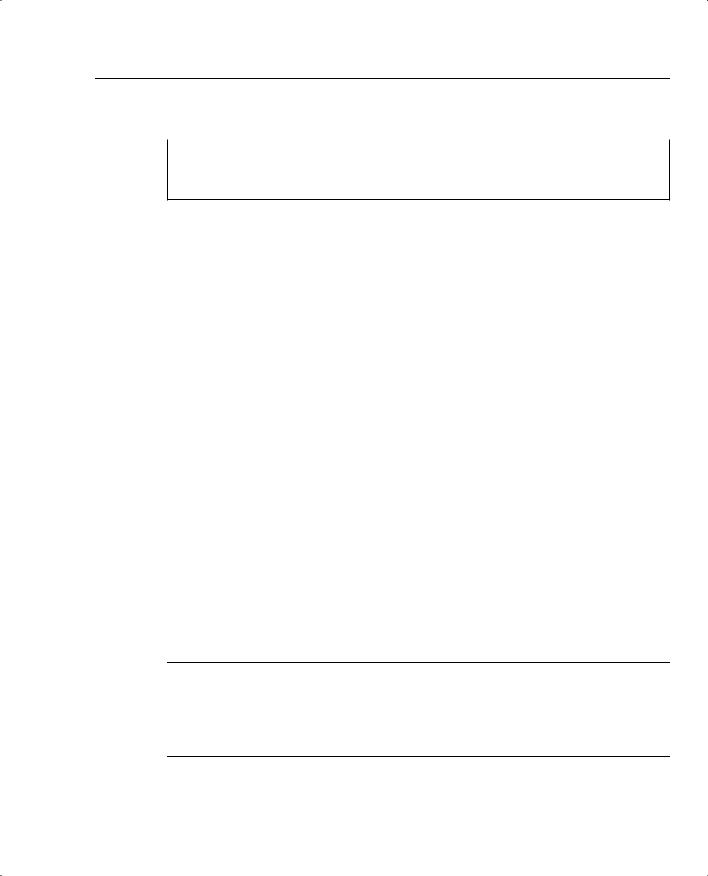
Figure 3-2 displays the active FTP mode of operation between an FTP client and FTP server.
Figure 3-2 FTP Active Mode
|
|
|
|
FTP |
|
|
FTP |
|
|
||||
|
|
|
Server |
|
|
Client |
|
|
|||||
|
|
|
|
|
Active FTP |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
FTP Port |
|
20 Data |
|
|
21 Command |
> 1023 |
> 1023 |
|
FTP Port |
||||
|
|
|
|
||||||||||
Number |
|
|
|
|
Local TCP |
1 |
|
|
|
|
|
|
Number |
|
|
|
|
|
Number |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
2
ok
3
Data Channel
4
ok
File Transfer Protocol 117
Figure 3-2 displays a typical FTP mode of operation between a client PC and FTP server in active mode. The following steps are completed before FTP data can be transferred:
1The FTP client opens a control channel on TCP port number 21 to the FTP server. The source TCP port number on the FTP client is any number randomly generated above 1023.
2The FTP server receives the request and sends an acknowledgment. FTP commands are exchanged between client and server.
3When the FTP client requests a directory list or initiates a file transfer, the client sends a command (FTP port command). The FTP server then opens (initiates) a data connection on the FTP data port, TCP port 20.
4The FTP client responds and data can be transferred.
Passive FTP
Passive FTP still requires a connection for the initial FTP control connection, which is initiated by the FTP client to the server. However, the second connection for the FTP data connection is also initiated from the client to the server (the reverse of active FTP).
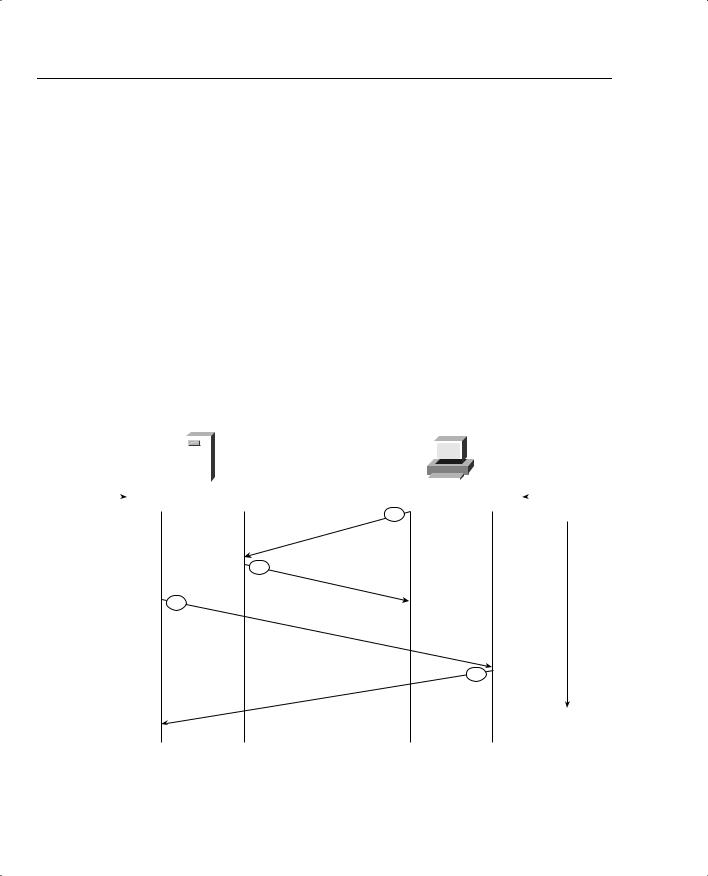
Figure 3-3 displays a typical FTP mode of operation between a client PC and FTP server in passive mode.
Figure 3-3 FTP Passive Mode
|
|
|
|
|
FTP |
|
|
FTP |
|
|
||||
|
|
|
|
Server |
|
|
Client |
|
|
|||||
|
|
|
|
|
|
|
Passive FTP |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
FTP Port |
20 Data |
|
|
21 Command |
> 1023 |
> 1023 |
|
FTP Port |
||||||
|
|
|
||||||||||||
Number |
|
|
|
|
|
|
1 |
|
|
|
|
|
|
Number |
|
|
|
|
|
|
|
PASV |
|
|
|
|
|
|
|
|
FTP Port |
|
|
> 1023 |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|||||
|
number |
2 |
ok |
|
|
|
|
|
|
|
||||
|
|
|
|
|
|
|
|
|
|
|
||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Data Channel |
|
|
|
|
|
|
|
3
ok
4

118 Chapter 3: Application Protocols
The following steps are completed before data can be transferred:
1The FTP client opens a control channel on TCP port 21 to the FTP server and requests passive mode with the FTP command pasv, or passive. The source TCP port number is any number randomly generated above 1023.
2The FTP server receives the request and agrees to the connections using a randomly generated, local TCP port number greater than 1023.
3The FTP client receives the information, selects a local TCP number randomly generated and greater than 1023, and opens a data channel to the FTP server (on TCP greater than 1023).
4The FTP server receives the FTP client’s request and agrees to the connection.
In passive FTP, the client initiates both the control connection and the data connection. In active mode, the FTP server initiates the FTP data channel. When using passive FTP, the probability of compromising data is less because the FTP client initiates both connections.
Hypertext Transfer Protocol
Hypertext Transfer Protocol (HTTP), used by web browsers and web servers, transfers files, such as text and graphic files. HTTP can also authenticate users with username and password verification between client and web servers.
Cisco IOS routers can be configured from a browser client. By default, Cisco routers are disabled for HTTP server (HTTP is enabled by default on a few Cisco 1000 models, namely the Cisco 1003,1004, and 1005 model routers), and there have been issues with users entering certain hash pairs to gain access to configuration commands when HTTP has been enabled. Fortunately, the latest versions of Cisco IOS code have been strengthened, and users must now enter valid username and password pairings to gain access to the configuration options. HTTP authentication is not very secure, so Secure Socket Layer (SSL) was developed to allow a stronger method to authenticate HTTP users.
NOTE For more details on the HTTP security vulnerability with Cisco IOS, please visit www.cisco.com/warp/public/707/ioshttpserver-pub.shtml
To view the router’s home page, use a web browser pointed to http://a.b.c.d, where a.b.c.d is the IP address of your router or access server. If a name has been set via a DNS server, use http://router-name.
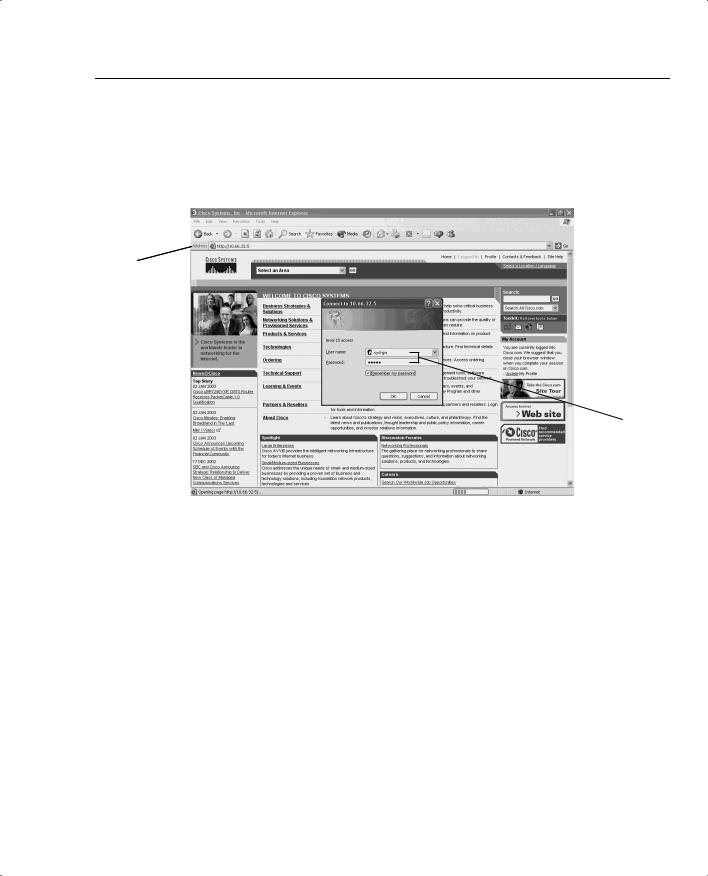
Hypertext Transfer Protocol 119
Figure 3-4 displays a sample HTTP request to a remote router with the IP address 10.66.32.5 displaying the request for a valid username and password. The default username is the Cisco router’s local host name, and the password is set to the enable or secret password.
Figure 3-4 HTTP Authentication on a Cisco Router
IP Address of
Remote Router
Username and password are entered here.
After the user is authenticated, the user enters the remote IP address or DNS name.
Varying forms of authentication for login can be set using the ip http authentication command. However, the default login method is entering the host name as the username and the enable or secret password as the password, as displayed in Figure 3-4.
After the user is authenticated with the correct username and password pairing, the user is permitted HTTP access. Figure 3-5 displays the options available after authentication.
After HTTP is authenticated, the available options are identical to the command-line interface (CLI) prompt. Depending on the configurable username and password pairing on the router, you will have certain privileged levels. For example, if you type the username as the local host name of the IOS router and the enable or secret password as completed in Figure 3-5, you will have privilege level 15, which is the same as the PRIV level on the CLI permitting all IOS commands. If the username/password pairing has a lower privileged level (via the ip http authentication command), the corresponding IOS command set will be available via HTTP. For example, a user with privilege level 5 will not have the option to reload the router.
