
- •CCIE Security Written Exam Blueprint
- •General Networking Topics
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Networking Basics—The OSI Reference Model
- •Ethernet Overview
- •Internet Protocol
- •Variable-Length Subnet Masks
- •Classless Interdomain Routing
- •Transmission Control Protocol
- •TCP Services
- •Routing Protocols
- •ISDN
- •IP Multicast
- •Asynchronous Communications and Access Devices
- •Foundation Summary
- •Requirements for FastEther Channel
- •Scenario
- •Scenario 2-1: Routing IP on Cisco Routers
- •Scenario Answers
- •Scenario 2-1 Answers: Routing IP on Cisco Routers
- •Application Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Domain Name System
- •Trivial File Transfer Protocol
- •File Transfer Protocol
- •Hypertext Transfer Protocol
- •Secure Socket Layer
- •Simple Network Management Protocol
- •Simple Mail Transfer Protocol
- •Network Time Protocol
- •Secure Shell
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Scenario 3-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Cisco Hardware
- •show and debug Commands
- •Password Recovery
- •Basic Security on Cisco Routers
- •IP Access Lists
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Security Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Authentication, Authorization, and Accounting (AAA)
- •Remote Authentication Dial-In User Service (RADIUS)
- •Kerberos
- •Virtual Private Dial-Up Networks (VPDN)
- •Encryption Technology Overview
- •Internet Key Exchange (IKE)
- •Foundation Summary
- •Scenario
- •Scenario 5-1: Configuring Cisco Routers for IPSec
- •Scenario Answers
- •Scenario 5-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •UNIX
- •Microsoft NT Systems
- •Common Windows DOS Commands
- •Cisco Secure for Windows and UNIX
- •Cisco Secure Policy Manager
- •Cisco Secure Intrusion Detection System and Cisco Secure Scanner
- •Cisco Security Wheel
- •Foundation Summary
- •Scenarios
- •Scenario 6-1: NT File Permissions
- •Scenario 6-2: UNIX File Permissions
- •Scenario Answers
- •Scenario 6-1 Solution
- •Scenario 6-2 Solution
- •Security Technologies
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Advanced Security Concepts
- •Cisco Private Internet Exchange (PIX)
- •Cisco IOS Firewall Security Feature Set
- •Public Key Infrastructure
- •Virtual Private Networks
- •Foundation Summary
- •Scenario
- •Scenario Answer
- •Scenario 7-1 Solution
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Network Security Policies
- •Standards Bodies and Incident Response Teams
- •Vulnerabilities, Attacks, and Common Exploits
- •Intrusion Detection System
- •Protecting Cisco IOS from Intrusion
- •Foundation Summary
- •Scenario
- •Scenario 8-1: Defining IOS Commands to View DoS Attacks in Real Time
- •Scenario Answer
- •Scenario 8-1 Solution
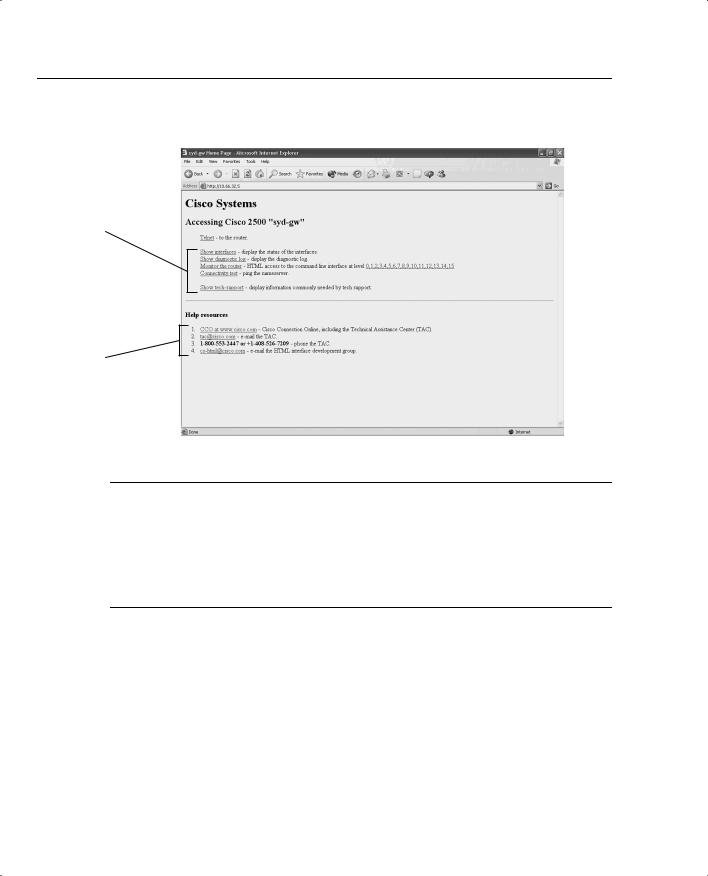
120 Chapter 3: Application Protocols
Figure 3-5 HTTP Web Page on a Cisco Router
HTTP options; simply click to expand IOS command set.
Help Options
NOTE The command to disable HTTP server on a Cisco router is no ip http server. To set username/password pairs, use the following IOS command:
username username privilege [0-15] password password
You can also define the HTTP port number with the following command:
ip http [0-65535]
The default is 80.
Secure Socket Layer
Secure Socket Layer (SSL) is an encryption technology for web host devices used to provide secure transactions. For example, a secure transaction is required when clients enter their credit card numbers for e-commerce via their browser. When the end user enters a web address via an Internet browser, such as Internet Explorer, instead of entering HTTP: //web address in the address window, the end user enters HTTPS://web address.

Simple Network Management Protocol 121
Secure Hypertext Transfer Protocol secure site, or HTTPS, transports HTTP-based traffic over an SSL connection and provides a stronger authentication mechanism than HTTP.
HTTPS runs over TCP port 443. SSL is defined in RFC 2246.
The SSL Handshake Protocol was first developed by Netscape Communications Corporation to provide security and privacy over the World Wide Web. The SSL protocol supports server and client authentication. The SSL protocol is application-independent, allowing protocols like HTTP, FTP, and Telnet to be layered on top of it transparently. In other words, it is a session layer-based protocol. Cisco has developed a number of content-based switches to accelerate this communication, such as the Cisco SCA 11000 Series Secure Content Accelerator. The Cisco SCA 11000 Series Secure Content Accelerator is an appliance-based solution that increases the number of secure connections supported by a website by offloading the processorintensive tasks related to securing traffic with SSL. After an SSL session is established, no further authentication is required. Chapter 5, “Security Protocols,” broadens this discussion on public security by discussing topics such as private and public keys, and how keys are exchanged through the Certificate Authority (CA) to ensure that SSL is secure.
Simple Network Management Protocol
Application layer protocol, Simple Network Management Protocol (SNMP), is used to manage IP devices. SNMP is part of the TCP/IP application layer suite. SNMP allows network administrators the ability to view and change network parameters and monitor connections locally and remotely. Managing network performance over a period of time is one of the major functions that SNMP provides.
There are three version of SNMP:
•
•
•
SNMP Version 1 (SNMPv1)
SNMP Version 2 (SNMPv2)
SNMP Version 3 (SNMPv3)
Both SNMPv1 and SNMPv2 use a community-based form of security. The community string allows access to the SNMP agent and can also be defined by an IP address access control list and password.
To set up the community access strings to permit access to the Simple Network Management Protocol (SNMP) on a Cisco IOS router, use the snmp-server community global configuration command:
snmp-server community string [view view-name] [ro | rw] [number]

122 Chapter 3: Application Protocols
Table 3-1 describes this syntax.
Table 3-1 |
snmp-server community Command Syntax Description |
|
|
|
|
|
Syntax |
Description |
|
|
|
|
string |
Case-sensitive community string that acts like a password and permits access to the |
|
|
SNMP protocol. |
|
|
|
|
view view-name |
(Optional) Name of a previously defined view. The view defines the objects |
|
|
available to the community. |
|
|
|
|
ro |
(Optional) Specifies read-only access. Authorized management stations are able to |
|
|
retrieve only MIB objects. |
|
|
|
|
rw |
(Optional) Specifies read-write access. Authorized management stations are able to |
|
|
retrieve and modify MIB objects. |
|
|
|
|
number |
(Optional) Integer from 1 to 99 that specifies an access list of IP addresses that are |
|
|
allowed to use the community string to gain access to the SNMP agent. |
|
|
|
SNMP servers collect information from remote devices known as SNMP agents. SNMP packets are sent and received by devices on UDP ports 161 (SNMP servers) and 162 (SNMP agents).
The Management Information Base (MIB) is a virtual information storage area for network management information consisting of collections of managed objects. Within the MIB are collections of related objects, defined in MIB modules. MIB modules are written in the SNMP MIB module language, as defined in STD 58, RFC 2578, RFC 2579, and RFC 2580. SNMP port 161 is used to query SNMP devices, and SNMP port 162 is used to send SNMP traps. SNMP runs over UDP and is secured by a well-known, case-sensitive community string.
SNMP Notifications
SNMP’s key feature is the ability to generate notifications from SNMP agents.
Cisco routers can be configured to send SNMP traps or informed requests to a Network Management System (NMS) where a network administrator can view the data.
Figure 3-6 displays the typical communication between an SNMP manager and the SNMP agent (for example, a Cisco-enabled SNMP router).
Unsolicited notifications can be generated as traps or inform requests. Traps are messages alerting the SNMP manager to a condition on the network (sent by the SNMP agent). Inform requests (informs) are traps that include a request for confirmation of receipt from the SNMP manager. SNMP notifications can indicate improper user authentication, restarts, the closing of a connection, loss of connection to a neighbor router, or other significant events.

|
|
|
|
|
|
|
|
Simple Network Management Protocol 123 |
||||
|
|
|
|
|
|
|
|
|
|
|
|
|
Figure 3-6 Communication Between SNMP Manager and SNMP Agent |
||||||||||||
|
|
|
Trap (no acknowledge) or Inform |
|||||||||
|
|
|
Requests (acknowledgment sent) |
|||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
UDP 162 |
||||
|
SNMP |
|
|
|
|
|
|
|
|
|
SNMP |
|
|
|
|
|
|
|
|
|
|
|
|||
|
Manager |
|
|
|
|
|
|
|
|
|
Agent |
|
|
|
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
UDP 161 |
||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
Inform acknowledgment sent |
|||||||
|
The major difference between a trap and an inform packet is that an SNMP agent has no way |
|||||||||||
|
of knowing if an SNMP trap was received by the SNMP manager. An inform request will be |
|||||||||||
|
sent continually until an acknowledgment is received by the sending SNMP agent. |
|||||||||||
|
Table 3-2 defines some of the common terminology used in SNMP. |
|||||||||||
Table 3-2 |
SNMP Terminology |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Term |
Description |
||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Managed device |
A network node that contains an SNMP agent and resides on a managed |
||||||||||
|
|
|
network. Managed devices collect and store management information and |
|||||||||
|
|
|
make this information available to Network Management Systems using |
|||||||||
|
|
|
SNMP. |
|||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Agent |
A network management software module that resides in a managed device. |
||||||||||
|
|
|
An agent has local knowledge of management information and translates that |
|||||||||
|
|
|
information into a form compatible with SNMP. |
|||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Network Management |
Executes applications that monitor and control managed devices. |
||||||||||
|
System (NMS) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
NOTE Managed devices are monitored and controlled using three common SNMP commands: read, write, and trap.
The read command is used by an NMS to monitor managed devices. The NMS examines different variables that are maintained by managed devices.
The write command is used by an NMS to control managed devices. The NMS changes the values of variables stored within managed devices.
The trap command is used by managed devices to asynchronously report events to the NMS. For example, Cisco IOS routers can be configured to report errors, such as emergencies alerts, to the NMS for urgent action, such as low memory resources or unauthorized access. When certain types of events occur, a managed device sends a trap to the NMS.

124 Chapter 3: Application Protocols
Management Information Base (MIB), a database of network management information, is used and maintained by a management protocol such as SNMP. The value of an MIB object can be changed or retrieved using SNMP commands, usually through a GUI network management system. Cisco supports a number of defined and proprietary MIB commands.
If the snmp-server community command is not used during the SNMP configuration session, it will automatically be added to the configuration after the snmp-server host command is used. In this case, the default password (string) for the snmp-server community is taken from the snmp-server host command. You must always set the community string manually; otherwise, your router could be left vulnerable to SNMP get commands.
Example 3-7 configures a Cisco IOS router for SNMP support.
Example 3-7 Sample SNMP Configuration
snmp-server community public RO snmp-server enable traps config snmp-server host 131.108.255.254 isdn
The IOS command snmp-server community public RO enables SNMP on a Cisco router. This command is also used to restrict access via SNMP. The community string is defined as public and acts as a password protection mechanism against unauthorized users. The community string is sent in every SNMP packet, so an incorrect community string results in no authorized access to the SNMP agent. The read-only attribute means that no configuration changes will be permitted via an SNMP.
The IOS command snmp-server enable traps config advises the NMS of any configuration changes. The IOS command snmp-server host 131.108.255.254 isdn alerts the host 131.108.254.254 of any ISDN traps. ISDN traps can include link flapping or high link usage, for example. (See Table 3-2 for a comprehensive list of traps.)
To specify the recipient of an SNMP notification operation, use the snmp-server host global configuration command. To remove the specified host, use the no form of this command.
snmp-server host host-addr [traps | informs] [version {1 | 2c | 3
[auth | noauth | priv]}] community-string [udp-port port] [notification-type]
Table 3-3 expands the snmp-server host IOS command and presents the full range of options, including MD5 authentication.

|
|
Simple Network Management Protocol 125 |
|
|
|
Table 3-3 |
snmp-server host Command |
|
|
|
|
|
Syntax Description |
Meaning |
|
|
|
|
host-addr |
Name or Internet address of the host (the targeted recipient). |
|
|
|
|
traps |
(Optional) Sends trap messages to this host. This is the default. |
|
|
|
|
informs |
(Optional) Sends Inform messages to this host. |
|
|
|
|
version |
(Optional) Version of the SNMP used to send the traps. Version 3 is the most |
|
|
secure model because it allows packet encryption with the priv keyword. If |
|
|
you use the version keyword, one of the following must be specified: |
|
|
1—SNMPv1. This option is not available with informs. |
|
|
2c—SNMPv2C. |
|
|
3—SNMPv3. |
|
|
The following three optional keywords can follow the 3 keyword: |
|
|
auth—(Optional) Enables Message Digest 5 (MD5) and Secure Hash |
|
|
Algorithm (SHA) packet authentication. |
|
|
noauth—(Default) The noAuthNoPriv security level. This is the default if the |
|
|
[auth | noauth | priv] keyword choice is not specified. |
|
|
priv—(Optional) Enables Data Encryption Standard (DES) packet |
|
|
encryption (also called privacy). |
|
|
|
|
community-string |
Password-like community string sent with the notification operation. |
|
|
Although you can set this string using the snmp-server host command by |
|
|
itself, it is recommended that you define this string using the snmp-server |
|
|
community command prior to using the snmp-server host command. |
|
|
|
|
udp-port port |
(Optional) UDP port of the host to use. The default is 162. |
|
|
|
|
notification-type |
(Optional) Type of notification to be sent to the host. If no type is specified, |
|
|
all notifications are sent. The notification type can be one or more of the |
|
|
following keywords: |
|
|
bgp—Sends Border Gateway Protocol (BGP) state change notifications. |
|
|
calltracker—Sends Call Tracker call-start/call-end notifications. |
|
|
config—Sends configuration notifications. |
|
|
dspu—Sends downstream physical unit (DSPU) notifications. |
|
|
entity—Sends Entity MIB modification notifications. |
|
|
envmon—Sends Cisco enterprise-specific environmental monitor |
|
|
notifications when an environmental threshold is exceeded. |
|
|
frame-relay—Sends Frame Relay notifications. |
|
|
hsrp—Sends Hot Standby Routing Protocol (HSRP) notifications. |
|
|
|
continues

126 Chapter 3: Application Protocols
Table 3-3 snmp-server host Command (Continued)
Syntax Description |
Meaning |
|
|
notification-type |
isdn—Sends Integrated Services Digital Network (ISDN) notifications. |
(Continued) |
llc2—Sends Logical Link Control, type 2 (LLC2) notifications. |
|
|
|
repeater—Sends standard repeater (hub) notifications. |
|
rsrb—Sends remote source-route bridging (RSRB) notifications. |
|
rsvp—Sends Resource Reservation Protocol (RSVP) notifications. |
|
rtr—Sends SA Agent (RTR) notifications. |
|
sdlc—Sends Synchronous Data Link Control (SDLC) notifications. |
|
sdllc—Sends SDLLC notifications. |
|
snmp—Sends any enabled RFC 1157 SNMP linkUp, linkDown, |
|
authenticationFailure, warmStart, and coldStart notifications. |
|
stun—Sends serial tunnel (STUN) notifications. |
|
syslog—Sends error message notifications (Cisco Syslog MIB). Specify the |
|
level of messages to be sent with the logging history level command. |
|
tty—Sends Cisco enterprise-specific notifications when a Transmission |
|
Control Protocol (TCP) connection closes. |
|
voice—Sends SNMP poor quality of voice traps when used with the snmp |
|
enable peer-trap poor qov command. |
|
x25—Sends X.25 event notifications. |
|
|
*Table 3-3 is sourced from the Cisco Documentation website, www.cisco.com/univercd/cc/td/doc/product/ software/ios121/121cgcr/fun_r/frprt3/frd3001.htm#xtocid655917.
SNMP is disabled by default on Cisco IOS routers.
SNMP Examples
The following example assigns the SimonisCool string to SNMP, allowing read-only access, and specifies that IP access list 4 can use the community string:
R1(config)# snmp-server community SimonisCool ro 4
R1(confiog)# access-list 4 permit 131.108.1.0 0.0.0.255
The hosts on network 131.108.1.0/24 are permitted SNMP access if the read-only string is set to SimonisCool. This enables an added feature to ensure that devices that source SNMP information are from a trusted or internal network.
The following example assigns the string SnR to SNMP, allowing read-write access to the objects in the restricted view (read only):
R1(config)# snmp-server community SnR view restricted ro
