
- •CCIE Security Written Exam Blueprint
- •General Networking Topics
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Networking Basics—The OSI Reference Model
- •Ethernet Overview
- •Internet Protocol
- •Variable-Length Subnet Masks
- •Classless Interdomain Routing
- •Transmission Control Protocol
- •TCP Services
- •Routing Protocols
- •ISDN
- •IP Multicast
- •Asynchronous Communications and Access Devices
- •Foundation Summary
- •Requirements for FastEther Channel
- •Scenario
- •Scenario 2-1: Routing IP on Cisco Routers
- •Scenario Answers
- •Scenario 2-1 Answers: Routing IP on Cisco Routers
- •Application Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Domain Name System
- •Trivial File Transfer Protocol
- •File Transfer Protocol
- •Hypertext Transfer Protocol
- •Secure Socket Layer
- •Simple Network Management Protocol
- •Simple Mail Transfer Protocol
- •Network Time Protocol
- •Secure Shell
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Scenario 3-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Cisco Hardware
- •show and debug Commands
- •Password Recovery
- •Basic Security on Cisco Routers
- •IP Access Lists
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Security Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Authentication, Authorization, and Accounting (AAA)
- •Remote Authentication Dial-In User Service (RADIUS)
- •Kerberos
- •Virtual Private Dial-Up Networks (VPDN)
- •Encryption Technology Overview
- •Internet Key Exchange (IKE)
- •Foundation Summary
- •Scenario
- •Scenario 5-1: Configuring Cisco Routers for IPSec
- •Scenario Answers
- •Scenario 5-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •UNIX
- •Microsoft NT Systems
- •Common Windows DOS Commands
- •Cisco Secure for Windows and UNIX
- •Cisco Secure Policy Manager
- •Cisco Secure Intrusion Detection System and Cisco Secure Scanner
- •Cisco Security Wheel
- •Foundation Summary
- •Scenarios
- •Scenario 6-1: NT File Permissions
- •Scenario 6-2: UNIX File Permissions
- •Scenario Answers
- •Scenario 6-1 Solution
- •Scenario 6-2 Solution
- •Security Technologies
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Advanced Security Concepts
- •Cisco Private Internet Exchange (PIX)
- •Cisco IOS Firewall Security Feature Set
- •Public Key Infrastructure
- •Virtual Private Networks
- •Foundation Summary
- •Scenario
- •Scenario Answer
- •Scenario 7-1 Solution
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Network Security Policies
- •Standards Bodies and Incident Response Teams
- •Vulnerabilities, Attacks, and Common Exploits
- •Intrusion Detection System
- •Protecting Cisco IOS from Intrusion
- •Foundation Summary
- •Scenario
- •Scenario 8-1: Defining IOS Commands to View DoS Attacks in Real Time
- •Scenario Answer
- •Scenario 8-1 Solution
Scenario 5-1: Configuring Cisco Routers for IPSec 271
Scenario
Scenario 5-1: Configuring Cisco Routers for IPSec
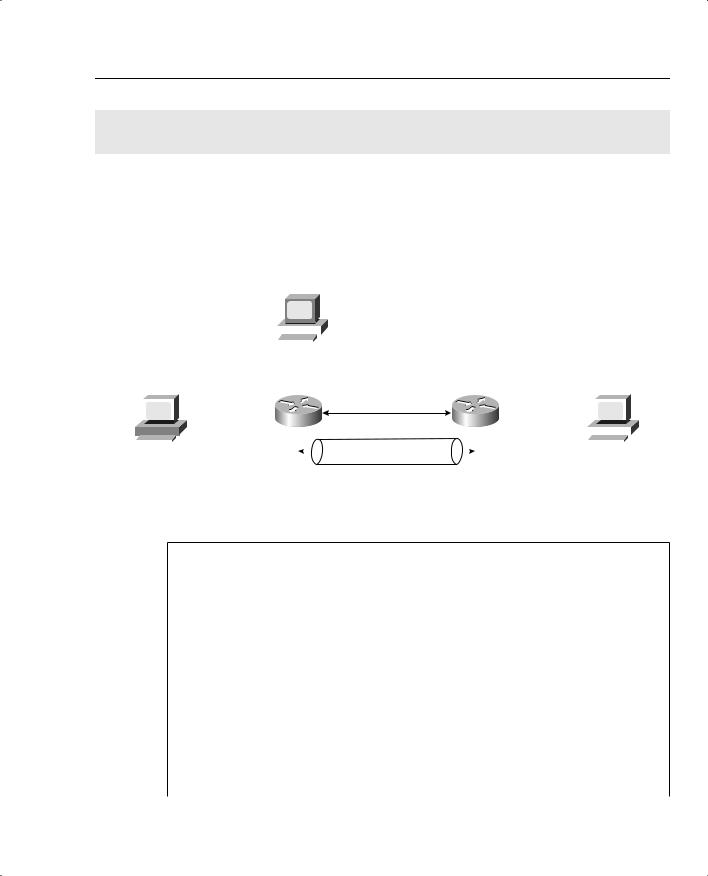
Figure 5-21 displays a simple two-router topology where traffic from network 131.108.100.0/24 is encrypted when it is sent to the remote network 131.108.200.0/24.
Figure 5-21 Scenario Topology
Host C
131.108.101.5/24
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Ethernet 0/1 |
|
|
|
|
|
|
|
||||||
|
|
Host A |
131.108.101.0/24 |
|
|
|
|
|
|
Host B |
||||||||||||||
|
|
|
|
|
|
|
|
|
131.108.255.0/24 |
|
|
|
|
|
|
|
|
|
|
|||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Ethernet 0/0 |
|
|
|
|
|
|
|
|
|
Ethernet 0/0 |
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||
|
|
|
|
|
|
131.108.100.1/24 |
|
|
|
|
|
|
IPSec Tunnel |
|
|
|
131.108.200.1/24 |
|
|
|
|
|
|
|
131.108.100.5/24 |
|
|
|
|
|
|
|
|
|
|
131.108.200.5/24 |
|||||||||||||
|
|
|
|
|
|
|
|
|||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Example 5-21 displays the working configuration of R1 numbered from 1 to 31.
Example 5-21 R1’s Full Configuration
1. version 12.2 2.hostname R1
3.enable password cisco 4.crypto isakmp policy 1
5.hash md5
6.authentication pre-share
7.crypto isakmp key CCIE address 131.108.255.2
8.crypto ipsec transform-set anyname esp-des esp-sha-hmac
9.mode transport
10.crypto map anyname1 1 ipsec-isakmp
11.set peer 131.108.255.2
12.set security-association lifetime seconds 180
13.set transform-set anyname
14.match address 100
15.interface Ethernet0/0
16.ip address 131.108.100.1 255.255.255.0
17.interface Serial0/0
18.ip address 131.108.255.1 255.255.255.252
19.encapsulation frame-relay
continues
272 Chapter 5: Security Protocols
Example 5-21 R1’s Full Configuration (Continued)
20.ip split-horizon
21.ip ospf network point-to-point
22.frame-relay map ip 131.108.255.2 102 broadcast
23.frame-relay interface-dlci 102
24.frame-relay lmi-type ansi
25.crypto map anyname1
26.interface Ethernet0/1
27.ip address 131.108.101.1 255.255.255.0
28.router ospf 1
29.network 131.108.0.0 0.0.255.255 area 0
30.access-list 100 permit ip 131.108.100.0 0.0.0.255 131.108.200.0 0.0.0.255
31.end
Example 5-22 displays the working configuration of R2 numbered from 1 through 29.
Example 5-22 R2’s Full Configuration
1.Version 12.2
2.hostname R2
3.enable password cisco
4.crypto isakmp policy 1
5.hash md5
6.authentication pre-share
7.crypto isakmp key CCIe address 131.108.255.1
8.crypto ipsec transform-set anyname esp-des esp-sha-hmac
9.mode transport
10.crypto map anyname1 1 ipsec-isakmp
11.set peer 131.108.255.1
12.set security-association lifetime seconds 180
13.set transform-set anyname
14.match address 100
15.interface Ethernet0/0
16.ip address 131.108.200.1 255.255.255.0
17.interface Serial0/0
18.ip address 131.108.255.2 255.255.255.252
19.encapsulation frame-relay
20.ip split-horizon
21.ip ospf network point-to-point
22.frame-relay map ip 131.108.255.1 201 broadcast
23.frame-relay interface-dlci 201
24.frame-relay lmi-type ansi
25.crypto map anyname1
26.router ospf 1
27.network 131.108.0.0 0.0.255.255 area 0
28.access-list 100 permit ip 131.108.200.0 0.0.0.255 131.108.100.0 0.0.0.255
29.end

Scenario 5-1: Configuring Cisco Routers for IPSec 273
1The following debug output is seen on R1 after the network administrator pings remote network 131.108.100.1 from Router R2’s console port.
Why will the IPSec tunnel not negotiate properly?
R2#debug crypto engine
Crypto Engine debugging is on R2#ping
Protocol [ip]:
Target IP address: 131.108.100.1 Repeat count [5]:
Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y
Source address or interface: 131.108.200.1 Type of service [0]:
Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 131.108.100.1, timeout is 2 seconds: 22:58:55: CryptoEngine0: generate alg parameter
22:58:55: CRYPTO_ENGINE: Dh phase 1 status: 0 22:58:55: CRYPTO_ENGINE: Dh phase 1 status: 0 22:58:55: CryptoEngine0: generate alg parameter
22:58:55: CryptoEngine0: create ISAKMP SKEYID for conn id 1 22:58:55: CryptoEngine0: generate hmac context for conn id 1.
22:58:55: %CRYPTO-4-IKMP_BAD_MESSAGE: IKE message from 131.108.255.1 failed it s sanity check or is malformed....
Success rate is 0 percent (0/5) R2#
2What subnets will be encrypted between Routers R1 and R2?
3What IOS command produced the following display and from which router?
Crypto Map "anyname1" 1 ipsec-isakmp Peer = 131.108.255.2 Extended IP access list 100
access-list 100 permit ip 131.108.100.0 0.0.0.255 131.108.200.0 0.0.0.255 Current peer: 131.108.255.2
Security association lifetime: 4608000 kilobytes/180 seconds PFS (Y/N): N
Transform sets={ anyname, } Interfaces using crypto map anyname1:
Serial0/0
4Will Host A be able to communicate with Host B or Host C? The following displays are the IP routing tables on R1 and R2. (Assume the gateway configurations on the PCs are correct.)
R1’s IP routing table:
R1>show ip route
Codes: C - connected, , O - OSPF,
131.108.0.0/16 is variably subnetted, 4 subnets, 2 masks
C131.108.255.0/30 is directly connected, Serial0/0
O 131.108.200.0/24 [110/400] via 131.108.255.2, 00:52:00, Serial0/0
C131.108.101.0/24 is directly connected, Ethernet0/1
C131.108.100.0/24 is directly connected, Ethernet0/0

274 Chapter 5: Security Protocols
R2’s IP routing table:
R2>show ip route
Codes: C - connected, , O - OSPF
131.108.0.0/16 is variably subnetted, 4 subnets, 2 masks
C131.108.255.0/30 is directly connected, Serial0/0
C131.108.200.0/24 is directly connected, Ethernet0/0
O 131.108.101.0/24 [110/58] via 131.108.255.1, 00:52:09, Serial0/0 131.108.100.0/24 [110/58] via 131.108.255.1, 00:52:09, Serial0/0
5To allow the IP subnet 131.108.101.0/24 attached to R1 Ethernet 0/1 interface to be encrypted over the IPSec tunnel and to communicate with the remote PC IP address 131.108.200.5, what configuration changes are required on which router?
