
Microsoft Windows XP Networking Inside Out
.pdf
5: Advanced Networking
19 Chapter
Part 5: Advanced Networking
Inside Out (continued) headaches and access problems. The point is that wireless networking is rather easy in single subnet networks, especially those that are small and located in one place. In larger networks, access can certainly become a more complex issue, depending on how the user needs to move about and how the user intends on accessing the wireless network.
The good news, however, is that Windows XP is able to detect changes in the access point used and automatically reconfigure itself. Each time that a computer running Windows XP associates with a new wireless access point, it uses DHCP either to renew its current IP configuration (its lease) or to obtain a new lease that is valid for the new subnet. Additionally, Windows XP can even redetect proxy server settings for Microsoft Internet Explorer so that Internet connectivity is not disrupted when a move is made to a different access point. As a general rule, these automatic configuration tactics work well and are invisible to the user. Because an association with an access point has to be formed, that information can be passed from access point to access point as the user moves. This association passing is performed through Inter-Access Point Protocol (IAPP) so that an association only has to be made one time instead of each time the user moves from one access point to another. IAPP is supported by most access point vendors so that different access points from different manufacturers can be used, providing seamless operation.
Ad hoc mode Ad hoc mode allows wireless client computers to connect directly without the use of an access point. For example, a collection of clients in a conference room can use ad hoc mode to create a network, as shown in the following illustration. However, if you want to access a wired LAN, you’ll need some sort of bridge, such as a wireless access point or a Windows XP computer acting as a network bridge. Otherwise, the wireless network clients can only communicate with each other.
Wireless Clients Networking in Ad Hoc Mode
Wireless
clients
538

5: Advanced Networking
Chapter 19: Wireless Networking
Using Both Infrastructure Mode and Ad Hoc Mode
Windows XP can operate in both wireless modes. Perhaps you use a wireless laptop at work in an office that uses infrastructure mode. Your laptop uses the office network during the day through a wireless access point. However, at night, you might bring your laptop home and want to connect your laptop to your home network for Internet access by connecting to a wireless-equipped desktop computer. Windows includes a service called Wireless Zero Configuration, which initiates a sequential process for determining the appropriate wireless network mode to use. Windows XP first searches for a wireless access point. If one is found, Windows XP switches the wireless adapter to infrastructure mode. If no access point is available, Windows XP looks for other computers operating in ad hoc mode. This process lets you move from infrastructure to ad hoc mode as needed without making any changes to the configuration of the wireless adapter. This feature requires that the software drivers for the wireless adapters support the Wireless Zero Configuration service.
Chapter 19
Wireless Networking Hardware
To create a wireless network, you need wireless NICs for the computers that will participate on the wireless network as well as a wireless access point if you plan on configuring your wireless network to use infrastructure mode.
●Wireless NICs. Wireless NICs are readily available as PC Cards for laptop computers. PCI adapters are also available and allow you to plug a PC Card wireless NIC into a desktop computer. Some laptops also include built-in wireless NICs. Each wireless NIC has a miniature antenna for transmitting and receiving wireless data. Major networking companies like NetGear, Linksys, and SMC produce wireless networking devices in addition to their more traditional wired networking devices. Wireless NICs typically range in cost from $60 to $100; thus, they’re a little more expensive than Ethernet NICs, but the price difference should not deter you from building a wireless network. Make sure that any wireless NIC you buy is compatible with the standard you intend to use, either 802.11b or 802.11a.
●Wireless Access Point. Wireless access points can either be stand-alone devices or can be built into other devices such as residential gateways. Some have built-in wireless NICs and antennas, whereas others provide a PCMCIA slot in which to insert a PC Card wireless network adapter. They also often include ports for adding more flexible external antennas.
539

5: Advanced Networking
19 Chapter
Part 5: Advanced Networking
If you want to extend a wired LAN with the wireless network connection, you simply connect the wireless access point to the Ethernet network with an RJ-45 cable. Wireless clients can then communicate with one another through the wireless access point, and if the access point is also connected to a wired network hub, the clients can communicate with the wired network as well. Wireless access points tend to be more expensive than simple wired hubs, and as with hubs, there are many options to choose from.
Selecting a Wireless Network Topology
Topology refers to the physical layout of your network. Before purchasing any wireless networking equipment, you need to take a look at your needs and make a firm decision about how the wireless network will benefit you. How many computers will have wireless network adapters? Do you need an access point? Will you combine an existing network with wireless access, or do you want an entirely wireless network? These are important questions to consider, and the following sections point out some topology options for you. Note that the following sections describe wireless networking in a home or small office setting because that is what you will most likely be configuring. In a large network environment, wireless networking takes more advanced planning and administrative planning, which is beyond the scope of this book.
Completely Wireless Network, Ad Hoc Mode
In a completely wireless network, each computer can be outfitted with a wireless network adapter and configured in ad hoc mode. You do not need a wireless access point unless you are bridging two dissimilar networks, such as a wired Ethernet network and a wireless network.
Ad hoc wireless networks are useful if you want to minimize the initial costs of bringing up a wireless network, if you don’t need to connect to any outside networks, or if one of the ad hoc wireless hosts will also serve as an ICS host. In this latter configuration, the computer connected to the Internet acts as the ICS host, and the wireless clients access the Internet by connecting to the ICS host over the wireless network. With this configuration, ICS works the same way as it does in a wired network, as shown in the following illustration. You can learn more about setting up ICS in “Using Internet Connection Sharing,” page 301.
Although ad hoc networks reduce the initial hardware cost of a wireless network, the limited range of each wireless card means that it’s easy to disrupt network communications by moving computers too far apart from one another. This drastically limits the utility of ad hoc wireless networking in medium-to-large size network installations.
540

Chapter 19: Wireless Networking
Internet |
Ad Hoc Mode Network Accessing the Internet |
|
Through an ICS Host |
||
|
Wireless DSL laptop modem
ICS host
Wireless workstation
Completely Wireless Network with a
Wireless Access Point as a Residential Gateway
5: Advanced Networking
Chapter 19
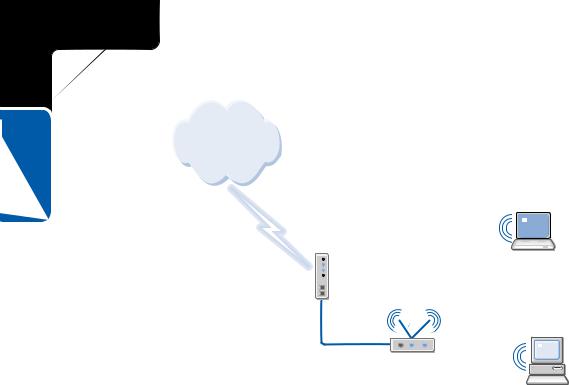
If you are using a wireless access point as a residential gateway to the Internet rather than using ICS, you will use infrastructure mode, and all computers will connect to the network through the wireless access point. The advantage to this configuration over an ad hoc network is that you do not need a computer that acts as an Internet gateway— all of your computers can be mobile. Also, an ICS computer must always be on for any of the other network computers to reach the Internet. With a wireless access point, only the wireless access point must be powered up. Furthermore, the wireless network will not be disrupted if one or more network clients move out of range of one another.
Individual computers will drop off the network as they move out of range of the wireless access point, but the others will continue to function normally. However, you’ll have to buy a somewhat expensive wireless access point ($200 and up) that includes residential gateway or router functions, whereas ICS is included with Windows. If you decide you want an infrastructure mode network, configure each computer with a wireless network adapter and connect your Internet connection’s DSL or cable modem connection to the wireless access point, as shown in the following illustration. Follow the manufacturer’s instructions for configuring the access point for Internet and wireless connectivity.
541
5: Advanced Networking
19 Chapter
Part 5: Advanced Networking
Internet |
Infrastructure Mode Network Accessing the Internet |
|
Through a Wireless Access Point |
||
|
Wireless DSL laptop modem
Wireless access point
Wireless workstation
Wireless Access Point as a Bridge
If you have an existing home or small office network, such as an Ethernet network, you can add wireless clients to the network, but you’ll need to bridge the two networks together. A wireless access point can serve this function. When you use a wireless access point, it connects to the wired network, typically by being plugged into an Ethernet hub. All traffic from the wireless computers flows through the access point so that wireless clients can communicate with the wired clients and reach the Internet as well.
Windows XP as a Bridge
If you want to bridge wireless and wired networks without purchasing additional hardware, you can do so using the Network Bridge feature built into Windows XP. To use this feature, you’ll need to install both a wireless and wired NIC in one of your Windows XP systems. That computer then serves as the network bridge device. You will have to leave this computer running for the two networks to have connectivity. To set up Network Bridge, follow the instructions listed in “Bridging Network Connections,” page 75.
Understanding Wireless Security
Network security is always a concern regardless of the kind of network that you choose to implement. However, with a wireless network, where data flows freely in the air as radio waves instead of being confined to a cable, security becomes more of a challenge.
542
5: Advanced Networking
Chapter 19: Wireless Networking
For example, how can you stop a corporate spy from accessing your wireless network from outside your building? In a home network, what’s to keep a neighbor from using your wireless network to gain access to your network resources and your personal data or to tap into your Internet connection? In the past, these problems had few solutions. Fortunately, new security standards for wireless communications can set your mind at ease.
Wired Equivalent Privacy (WEP) is an encryption algorithm system that’s included as part of the IEEE 802.11 standard. It’s commonly used and supported by wireless networking hardware devices. The WEP encryption algorithm sends data through the air in encrypted form. WEP can utilize either 40or 104-bit shared encryption keys, along with a standard 24-bit initialization vector, which augments the shared keys to produce a different encryption key for each data packet. The combination of the encryption key and the initialization vector produces WEP keys with a total length of 64 or 128 bits.
The WEP encryption standard prevents unauthorized access to the network as well as to the data that’s being transmitted over the wireless network. WEP, however, does not define a key management protocol. A single WEP key can be configured on all the wireless clients and the wireless access point of a home network, but there is no way to manage or distribute WEP keys on a large organization’s network; instead, they must be manually distributed and configured on each system. To provide a stronger authentication mechanism and a method to automatically distribute WEP encryption keys, the IEEE 802.1x standard was developed, and 802.11b uses this standard.
caution Unfortunately, WEP encryption suffers from a number of well-understood flaws that make it far less secure than the length of its encryption keys would imply. These flaws, along with best practices for securing your wireless network, are covered in “Securing Network Protocols” on page 588.
IEEE 802.1x is a standard for port-based network access control. This control method is used to provide authentication for access to Ethernet networks. The standard, which enforces authentication before LAN ports can be used, is an Ethernet standard that has been adapted to 802.11b. When 802.1x is used on networks, the wireless access point authenticates wireless clients in conjunction with a Remote Authentication Dial-in User Service (RADIUS) server. The RADIUS server provides authentication and authorization of wireless connections for the wireless access point. In large wireless networks, the use of 802.1x, RADIUS, and digital certificates provides a high level of authentication security and a method to determine strong per-session WEP encryption keys. Windows XP supports 802.1x authentication for all types of LAN adapters including wireless. For a large network, ensure that your wireless access points support WEP and IEEE 802.1x.
Chapter 19
543
5: Advanced Networking
Part 5: Advanced Networking
Setting Up Your Wireless Network
19 Chapter
After you’ve carefully thought through the design possibilities of your wireless network and have decided how the network can best suit your needs, you’re ready to purchase the wireless networking equipment that you need to begin setting up your wireless network. The following sections explore the setup and configuration of infrared and Wi-Fi networks.
Setting Up an Infrared Wireless Network
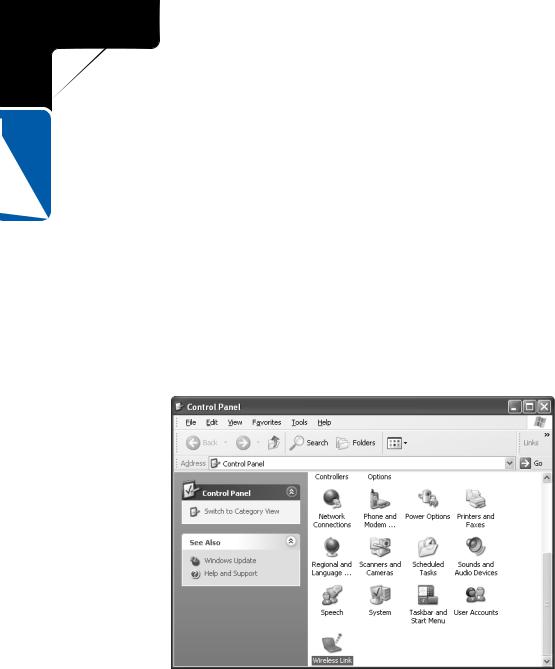
Most laptop computers ship with an infrared port. If your desktop system does not have an infrared port (many do not), you can purchase an external infrared device that connects to either a serial or USB port on your PC. In addition, some desktop motherboards have a built-in specialized connector to which you can connect an infrared device. If you need to buy an infrared port, check the Windows Hardware Compatibility List at www.microsoft.com/hcl to make sure the device is compatible with Windows XP. After the port is installed, it appears in Control Panel as Wireless Link, as shown in Figure 19-1.
Figure 19-1. The infrared wireless link is found in Control Panel.
To make the best use of your infrared port, Windows XP uses several protocols under the IrDA specification that give you the infrared flexibility you need:
●Wireless Link File Transfer. This protocol gives you the ability to transfer files over the wireless port.
●Infrared Printing (IrLPT). This protocol gives you the ability to print to wireless printers using infrared.
544

5: Advanced Networking
Chapter 19: Wireless Networking
●Infrared Image Transfer Protocol (IrTran-P). This protocol is used to transfer photos from a digital camera to your computer.
●Infrared Networking (IrNET and IrComm). These protocols give your computer the capability of communicating with other computers using infrared. IrNET is a point-to-point protocol between two computers, whereas IrComm uses a central infrared hub when several computers need to connect.
How Fast Is Infrared Networking?
Infrared networking, despite its distance limitations, remains a viable networking alternative because of its speed and ease of use. Infrared provides a quick and easy way to transfer information from one computer to another or synchronize with a PDA. There are two flavors of infrared devices, and the speed depends on which you use. Serial IrDA uses existing serial port hardware without the additional expense of other hardware. Serial IrDA is the most common type of infrared networking, and you can expect transfer speeds of up to 115 Kbps. Serial IrDA obviously is not as fast as an Ethernet or HomePNA connection, but it is much faster than using a null modem cable. On the other hand, Fast IrDA (FIR) can transfer data up to 4 Mbps and Very Fast IrDA (VFIR) can provide speeds of up to 16 Mbps. These solutions require additional hardware, however.
Configuring the Infrared Connection
Chapter 19
After the infrared device is installed on your computer, you can double-click the Wireless Link icon in Control Panel and configure a few important options concerning the infrared port.
On the Infrared tab of the Wireless Link dialog box, shown in Figure 19-2 on the next page, you can set the following options:
●Display An Icon On The Taskbar Indicating Infrared Activity. This option allows you to see when you are connected to an infrared link and when another computer or device is within your infrared range.
●Play Sound When Infrared Device Is Near By. This option sounds a tone when an infrared device first comes within range of your infrared port.
●Allow Others To Send Files To Your Computer Using Infrared Communications. If you want to let other devices send files to your computer over the infrared link, make sure this item is selected. Otherwise, users will receive an error message stating “Access is denied.”
545

5: Advanced Networking
19 Chapter
Part 5: Advanced Networking
●Notify Me When Receiving Files. If this item is selected, a transfer status dialog box appears when files are being received.
●Default Location For Received Files. If you choose to receive files, you can specify a default location where those files are stored. Click the Browse button to help select the location.
Figure 19-2. Configure basic infrared operations on the Infrared tab of the Wireless Link dialog box.
On the Image Transfer tab of the Wireless Link dialog box, shown in Figure 19-3, you can choose to use the wireless link to transfer images from a digital camera to your computer. Simply enable the first option, and then choose a default storage location for the picture files. Also notice the option Explore Location After Receiving Pictures. If you select this option, the folder in which the pictures are stored will automatically open after you have received the files.
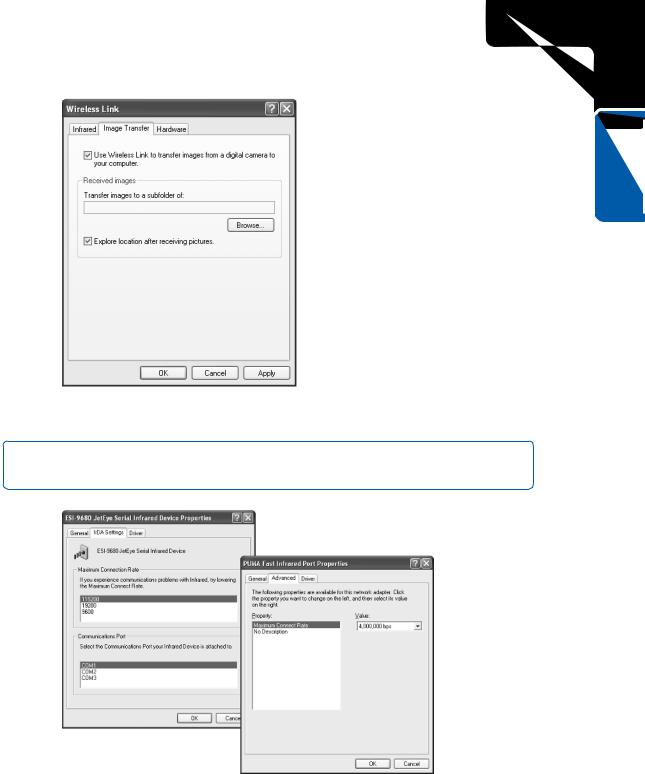
The Hardware tab of the Wireless Link dialog box lists the infrared device that is installed. It displays basic information about the device, such as the manufacturer, COM port location, and the current device status. If you select the device and click the Properties button, a properties dialog box opens—the same dialog box you see from within Device Manager. You’ll see the standard General and Driver tabs, but depending on your hardware, there might also be an IrDA Settings or Advanced tab that will let you further configure your port. Figure 19-4 shows the IrDA Settings tab for a serial infrared device and the Advanced tab for a FIR device. On these tabs, you can set the maximum connection rate and, for the serial device, select the COM port. The highest possible speeds are selected by default for both devices. Notice that the serial device tops out at 115.2 Kbps, whereas the FIR device can reach 4,000 Kbps (4 Mbps).
546
5: Advanced Networking
Chapter 19: Wireless Networking
Chapter 19
Figure 19-3. You can choose to receive digital photos on the Image Transfer tab and specify where to store them.
tip If you find you’re having problems communicating with a certain IrDA device, try lowering the maximum values.
Figure 19-4. Use the IrDA Settings or Advanced tab to set properties such as the port’s connection speed.
547
