
Microsoft Windows XP Networking Inside Out
.pdf
5: Advanced Networking
20 Chapter
Part 5: Advanced Networking
The Data Encryption box lets you select from four options: to not allow encryption, to attempt to use it, to require it, or require maximum strength encryption. This dialog box also lets you select Use Extensible Authentication Protocol (EAP) to use a smart card or other authentication mechanism, or to use an Internetor Microsoft-standard remote access authentication protocol (selected from the Allow These Protocols section). The protocols are listed in order of security, from lowest to highest. Password Authentication Protocol (PAP) passes authentication information in clear text, Shiva Password Authentication Protocol (SPAP) is designed for use with Shiva remote access servers, Challenge Handshake Authentication Protocol (CHAP) encrypts passwords, and the Microsoft CHAP (MS-CHAP) protocols include Microsoft-specific logon information including domain-related data.
When configuring connections, use the settings recommended by your network administrator for outbound remote access or VPN connections. If you are configuring a remote access or VPN connection server, select the most secure options that will allow your entire range of clients to connect. For instance, if you intend to only allow hosts running releases of Microsoft Windows 95 or later to connect to your Windows XP computer, you should use MS-CHAP v2.
Securing Network Protocols
One of the most common techniques for violating security and privacy on networks involves intercepting transmissions sent via unencrypted protocols. It’s critical to avoid sending personal information, such as credit card numbers, across the network in the clear. It’s also important to avoid sending user names and passwords across the network in clear text because a hacker that intercepts them can use the user names and passwords to log on to systems and initiate local attacks or even take complete control. The following practices will help to minimize this threat.
Encrypt wireless network traffic whenever possible When using wireless communications, use Wireless Encryption Protocol (WEP) with as large a key length as possible. WEP is hardly perfect because fundamental flaws in WEP’s key design allow it to be penetrated by a dedicated hacker with sufficient computing resources. Additionally, it only encrypts communication between wireless network adapters and wireless access points (or between adapters when configured in ad hoc mode). As soon as traffic is bridged to a wired medium, it travels without encryption. However, using WEP definitely reduces the chances that your wireless communications will be easily intercepted and deciphered. See Chapter 19, “Wireless Networking,” for more information about WEP and wireless network configurations.
Encrypt all TCP/IP traffic whenever possible The Internet Protocol Security (IPSec) standard provides a uniform process for securely encrypting TCP/IP traffic, including authentication, key negotiation, and packet encryption. Windows XP supports IPSec for both VPN tunneling (via the IPSec/L2TP standard discussed in
588
5: Advanced Networking
Chapter 20: Maintaining Network Security
Chapter 17, “Remote Access and Virtual Private Networking”) and for normal TCP/IP communications. IPSec configuration for standard TCP/IP traffic is done by setting a system policy, which allows IPSec to be configured for all computers within a domain or organizational unit as well as on a per-computer basis.
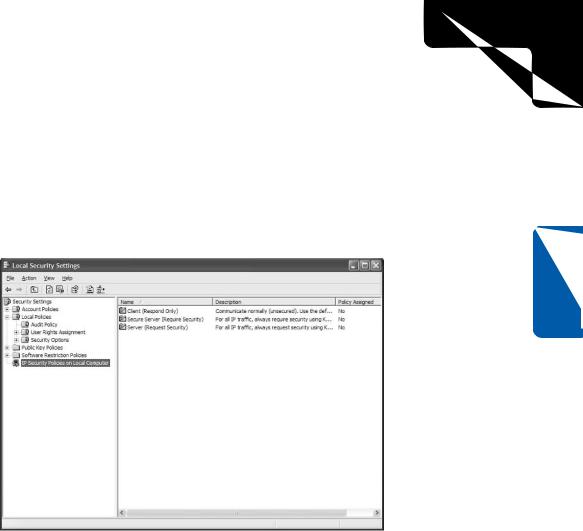
To configure IPSec policies on a Windows XP computer, open Local Security Policy from the Administrative Tools folder. Select IP Security Policies On Local Computer in the left pane to view the default IPSec policies that come with Windows XP, as shown in Figure 20-5.
Chapter 20
Figure 20-5. IPSec policies are defined in Local Security Policy.
The simplest way to activate IPSec is to use one of the predefined policies. The first policy, Client (Respond Only), communicates normally with remote TCP/IP hosts using unsecured traffic unless a particular server requests IPSec encryption. At that point, communication with that specific server over the specific requested port will be encrypted; all other traffic will remain unencrypted. The second policy, Secure Server (Require Security), requires all inbound and outbound TCP/IP traffic to be secured using Kerberos authentication (against an Active Directory domain or other authentication system that uses Kerberos). Kerberos is an authentication mechanism originally developed at MIT. All unencrypted traffic, or traffic to or from hosts that cannot be authenticated using Kerberos, will be dropped. The third policy, Server (Request Security), is a compromise between the others. If this policy is in place, Windows XP will always ask remote communication partners to use encryption via Kerberos trust, but will communicate without encryption if it is not available.
589

5: Advanced Networking
Part 5: Advanced Networking
tip Accelerate Your IPSec Traffic
20 Chapter
Because IPSec traffic is encrypted, it requires significant CPU resources to process each IP packet. If you intend to use IPSec, it is wise to invest in a high-end network adapter that includes an onboard processor that automatically handles IPSec encryption and decryption tasks at the hardware level, leaving the system’s CPU free to perform other tasks.
To activate one of these policies, simply right-click it and choose Assign.
If you want to have finer control over IPSec policies, including selecting specific encryption algorithms, using a different authentication technique (such as a shared key or assigned certificates), or defining specific ports and servers that require IPSec communications, you can develop a custom IPSec policy. For more information on the details of IPSec communication, consult the Windows XP Help and Support Center (choose Start, Help And Support).
note You might find many references, even in the Windows XP Help and Support Center, that claim that IPSec cannot be used with NAT. This is no longer strictly the case. Most modern residential gateways and NAT devices support IPSec communications, either out of the box or via a firmware upgrade. Some devices, however, will only support traffic with one IPSec-enabled computer behind the NAT gateway at one time.
Avoid applications that use clear text when transmitting sensitive data. If at all possible, avoid using the Telnet protocol to communicate with your Windows XP host or to a UNIX-based server because it passes user names and passwords in clear text. Never e-mail credit card numbers, passwords, or any other sensitive data. If you intend to use your credit card online, make certain that you only submit such sensitive data over an SSL-encrypted HTTP connection to a Web host that has a valid security certificate.
Protecting Windows XP from Viruses
Viruses are one of the most common, and insidious, threats to system security. They can be transmitted via e-mail, via removable media, or can even be deposited on unsecured network shares by Internet worms.
Using quality antivirus software with Windows XP is critical to maintaining the security and integrity of your system. The most effective antivirus programs are designed to automatically scan all files as they are created, read, or otherwise accessed, allowing them to be quarantined before any harmful acts can take place. Quality antivirus software should be able to handle macro viruses as well as executable viruses and should also include the ability to integrate with your e-mail application to scan attachments and e-mail messages before they are opened.
590

5: Advanced Networking
Chapter 20: Maintaining Network Security
When using antivirus software, you must keep the antivirus pattern files updated! Pattern files tell the antivirus scanning engines how to detect the latest viruses, and out-of-date pattern files leave Windows XP nearly as vulnerable as if you were using no antivirus software at all. Many antivirus applications include the ability to automatically download pattern updates from the manufacturer on a regular basis.
When choosing an antivirus package, be sure to select a recent version that is certified to work with Windows XP. There are a number of vendors of quality antivirus tools on the market.
Coping with E-mail Security Threats
Many of the most publicized security attacks of recent memory have come from selfpropagating worms that use e-mail as their delivery mechanism. More traditional viruses can also use e-mail to deliver their payloads by exploiting the scripting functionality built into recent e-mail applications such as Outlook and Outlook Express. Follow these practices to protect yourself from these threats:
●Use the most recent version of your e-mail application. Microsoft has updated Outlook and Outlook Express to reduce their vulnerability to virus and worm attacks via e-mail, and patches continue to be released as new vulnerabilities are detected.
●Never open an attachment from an address you don’t recognize. Never open an attachment without first scanning it with up-to-date antivirus software.
●Always configure Outlook Express to use the Restricted Sites zone for incoming e-mail. For more information on how to do this, see “Security Tab,” page 199.
●Always configure Outlook Express to warn you when other applications attempt to send e-mail using your identity. See “Security Tab,” page 199, for more information.
Detecting Trojan Horse Applications
Trojan horse programs can be extremely difficult to ferret out, particularly because they are not commonly detected by antivirus applications and are normally concealed within innocuous applications. To avoid these programs, never download and install applications unless you are extremely confident that they were developed by a reputable vendor. However, even some reputable vendors install spyware.
How can you detect these applications? An application such as ZoneAlarm will warn you of suspicious outbound Internet connections and notify you of which application is making them. See “Inbound vs. Outbound Firewalls,” page 568, for more information on ZoneAlarm.
Chapter 20
591

5: Advanced Networking
Part 5: Advanced Networking
You can also use Netstat to view all current TCP/IP connections and track down suspicious process IDs. See “Using Netstat to Observe IP Connections,” page 584, to learn more about Netstat.
Additionally, you can use a Trojan-detection tool to scan your computer for Trojan horses, much like antivirus software scans for viruses. One of the most popular tools for detecting and removing Trojan horses and spyware is Ad-aware by Lavasoft. You can learn more about Ad-aware and download the tool from the company’s Web site at www.lavasoft.de. Figure 20-6 shows Lavasoft’s Ad-aware in action.
20 Chapter
Figure 20-6. Ad-aware by Lavasoft is a popular tool for detecting Trojan horses and spyware.
Using Internet Explorer Safely
Browsing Web sites poses another potential avenue for violating the security of your computer and the data stored on it. Internet Explorer includes a number of features designed to improve the look and feel of the Internet; however, these features also increase the risk of surfing the Web.
Proper use of the Internet Zones feature, as described in “Security Zones,” page 144, can help protect Windows XP from exploits that can be delivered via client-side scripting technologies such as JavaScript as well as illicit Web-hosted applications using Java or ActiveX controls. It is also crucial to remain up-to-date on the latest patches for Internet Explorer to eliminate any newly detected security threats.
Cookies are used by many Web sites to track user preferences, but they can also be used to spy on your viewing habits. Trojan horse and spyware detection utilities can often detect and remove such cookies, and Internet Explorer 6.0 includes advanced cookie management features that allow you to select which types of cookies, if any, that you want to have automatically downloaded to your computer. You can learn more about these settings in “Understanding Privacy and Content Settings,” page 148. If you are
592

5: Advanced Networking
Chapter 20: Maintaining Network Security
concerned about cookies but want to retain the ability to use them for convenience on some Web sites, consider using the High privacy setting. This setting will prevent sites that do not provide privacy statements from generating cookies and will require your explicit consent before generating any personally identifiable cookies.
Using Administrative Privileges
It is common practice for Windows XP users to log on using an account that has administrative privileges. This practice eases the process of performing system configuration and software installation. However, being logged on as an administrator leaves the system vulnerable to attack because any Trojan horse or virus that is accidentally launched using the logged on user’s credentials will have full control over the computer.
For maximum safety, it’s best to log on as a Power User (or other type of User) for performing most day-to-day functions and only switch to an administrative account when you need to perform system maintenance or configuration. Once those tasks are done, you should log back out and rely on one of the user level accounts. Being logged on as a Power User or User allows Windows XP to protect itself from malicious applications (or accidental damage) using NTFS permissions and system policy.
note Many Windows applications have traditionally required administrative privileges in order to properly install; however, this is changing because the Windows logo requirements now specify that normal user applications must not require administrative rights in order to be installed successfully.
Chapter 20
Protecting Files Using NTFS
Chapter 13, “Selecting a File System,” discusses the differences between FAT32 and NTFS, and discusses the strengths and weaknesses of each. To maximize system security, however, it is best to only use NTFS on any partition that will be made accessible via the network. In fact, due to its ability to audit file access (useful when performing forensic analysis of a security violation) and its ability to protect files from unauthorized local access, NTFS should be used on all system and boot partitions as well to prevent damage to the operating system or important personal data.
Auditing Logon Events
Tracking user logons is crucial for being able to detect undesired logon attempts to your Windows XP computer as well as for diagnosing problems with desired account accesses.
593
5: Advanced Networking
20 Chapter
Part 5: Advanced Networking
Auditing must first be enabled at the system level before it becomes effective. To enable system auditing, launch Local Security Settings by opening Local Security Policy from the Administrative Tools folder. Double-click Local Policies, and then select Audit Policy. From here, you can audit either successful or failed (or both) account logon events, account management events (such as password changes), directory service access, logon events, object access, policy changes, privilege uses, process tracking, and system events. For basic security purposes, enable auditing for Audit Account Logon Events and Audit Logon Events. Right-click the first of these audit policies, choose Properties, and select both the Success and Failure options. Then repeat the steps for the other policy.
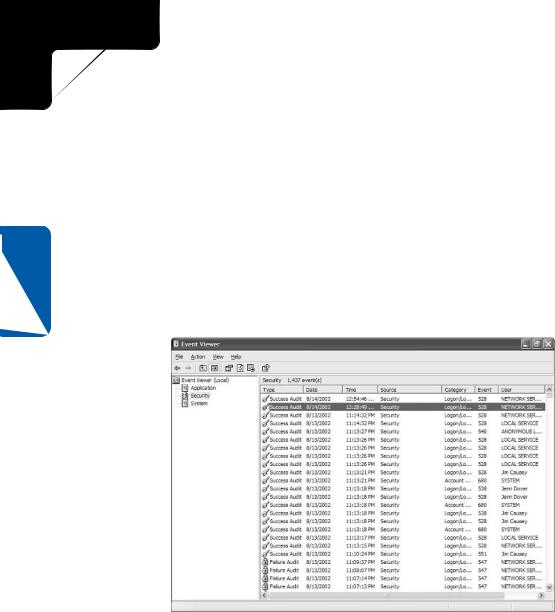
Once auditing is enabled, you can review the logon successes and failures in the Security Event Log by opening Event Viewer in the Administrative Tools folder and clicking Security in the left pane, as shown in Figure 20-7.
Figure 20-7. The Security Event Log shows system, file, and directory auditing messages.
Auditing File System Access
NTFS volumes enable the tracking of all access to particular files using the auditing features built into NTFS. Auditing can be useful when trying to diagnose security problems as well as for detecting and tracking undesired access to files on the computer.
594
5: Advanced Networking
Chapter 20: Maintaining Network Security
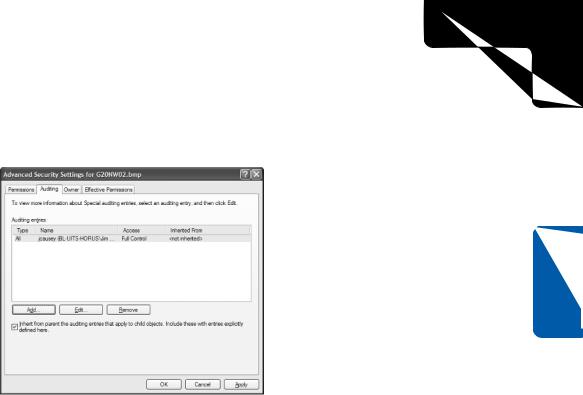
To enable auditing on a file or directory, right-click the file or directory and choose Properties. On the Security tab, click the Advanced button, and then select the Auditing tab, which is shown in Figure 20-8.
Chapter 20
Figure 20-8. NTFS allows file and directory accesses to be audited.
Click the Add button to add an auditing entry. Auditing entries work much like advanced NTFS permissions. You can select the users whose attempted access will be audited, the types of access that will be audited, and whether success, failure, or both success and failure of those attempted accesses will be audited. As with NTFS permissions, auditing entries can be inherited from parent directories.
Once auditing is enabled, auditing messages will appear in the Event Log’s Security node when the specified files or directories are accessed in the fashion specified by the auditing entries.
Managing EFS
Encrypting File System (EFS) is a powerful tool for preventing files from being read by others, even those with administrative access or those who are able to physically access your Windows XP computer. However, its use can be potentially disastrous without the creation and management of security keys.
EFS allows Windows XP users with administrative privileges to designate users as file recovery agents, or users that can provide keys that can be used to decrypt a file should the user account that originally encrypted the file be damaged or lost. The administrator
595

5: Advanced Networking
Part 5: Advanced Networking
20 Chapter
must create a self-signed security certificate (or use a third-party certificate) to generate recovery keys that can then be stored in case files need to be recovered.
caution It is essential to designate file recovery agents before EFS is used to encrypt files; otherwise, the file recovery agents will be unable to decrypt any file that was encrypted before they were designated.
For more information on managing file recovery certificates and keys for EFS, search for these topics in the Windows XP Help and Support Center: Best Practices: File encryption, Managing Certificates, and Recovering Data.
596

Chapter 21
Monitoring
Network
Performance 598
5: Advanced Networking
Monitoring
Windows XP
Network
Performance
Microsoft Windows XP was designed from the ground up to provide high levels of network performance. Many factors, however, can contribute to the speed and reliability of a network, and detecting and resolving network performance issues can be difficult. The good news is that Windows XP provides a wide range of tools that can be used to troubleshoot network performance.
The process of monitoring network performance involves examining different parts of the network, including various operating system and network hardware components, to look for patterns that could contribute to network difficulties. Once you isolate those potential problems, you can then take steps to resolve them. Finding those patterns can be difficult in some cases, and in order to solve networking performance problems, you’ll need to become a detective of sorts.
597
