
Microsoft Windows XP Networking Inside Out
.pdf
5: Advanced Networking
Part 5: Advanced Networking
20 Chapter
some combination of these actions. In practice, because attempted attacks are so common and the range of appropriate responses so limited, intrusion-detection systems are of little use; in fact, they are often extremely difficult to configure, and they issue many false alarms.
Authentication
Firewall software can also require authentication from both internal and external requests. Although authentication schemes are very secure, they can interfere with the operation of the network and restrict the data that can be accessed from the Internet. However, for networks requiring a high level of security, authentication requirements can provide it.
Given the benefits provided by these firewall features, it’s clear that installing and configuring a firewall on any network that is connected to another network (especially the Internet) is an essential security step. Obviously, if a remote attacker cannot detect or reach target computers over the network, that attacker cannot launch attacks directly against them, even if the computers are otherwise vulnerable to those attacks.
tip Securing Your Firewall from Attack
Many firewalls, including residential gateways, have features that allow them to be administered and/or updated remotely via the external IP address. It’s almost never a good idea to enable these features. If some unknown security vulnerability exists in your firewall device, enabling these features can leave your network open to attack. In fact, even if vulnerabilities do not exist, enabling these features can cause your firewall to respond to a port scan, giving remote attackers validation that your network exists, which is all the encouragement they need to begin probing your defenses further.
Inbound vs. Outbound Firewalls
Most firewall software and devices act as inbound firewalls; that is, they protect a network or a computer from inbound traffic initiated outside the protected computer or network. However, for the highest level of protection, it’s wise to stop undesired outbound traffic initiated from computers behind the firewall as well. This will prevent Trojan horse applications, spyware, and other unwanted and undetected applications present on your computer from being able to send data out across the Internet.
Most large, dedicated firewall devices for medium-to-large sized networks can be configured to provide both inbound and outbound protection. However, residential gateways, smaller dedicated firewalls, and software solutions such as Windows XP’s Internet Connection Firewall (ICF) are not designed to prevent unwanted outbound traffic.
568

5: Advanced Networking
Chapter 20: Maintaining Network Security
For a strictly locked-down corporate environment, using a firewall device with a strict policy of blocking all Internet traffic might suffice; however, if you want to maintain Internet functionality and still protect against inbound threats and unwanted outbound transmissions, a more flexible solution is needed.
One popular solution is ZoneAlarm, a software product from Zone Labs. ZoneAlarm automatically detects inbound and outbound connection attempts, allowing the user to quickly and easily build rules to define which applications should be allowed to establish outbound connections or provide Internet services from your computer. You can learn more about ZoneAlarm at the company’s Web site, www.zonealarm.com.
TCP/IP Filtering
In addition to using a firewall, you might want to simply use TCP/IP filtering to protect your Windows XP computer. TCP/IP filtering gives you the ability to allow specific TCP and UDP ports or IP protocol numbers to connect to your computer.
To configure TCP/IP filtering for a network connection, follow these steps:
1Right-click the network connection’s icon in the system tray, and choose Open Network Connections. You can also open Network Connections from Control Panel or the Start menu.
2Right-click your network icon in Network Connections, and choose Properties from the shortcut menu to open the dialog box shown here.
Chapter 20
569

5: Advanced Networking
Part 5: Advanced Networking
3On the General tab, select Internet Protocol (TCP/IP), and click Properties to open the Internet Protocol (TCP/IP) Properties dialog box shown in the following illustration.
20 Chapter
4Click the Advanced button and then select the Options tab, shown next, in the Advanced TCP/IP Settings dialog box.
5Select TCP/IP Filtering in the Optional Settings box, and then click Properties to open the TCP/IP Filtering dialog box shown in the following illustration.
570

5: Advanced Networking
Chapter 20: Maintaining Network Security
Chapter 20
6Select Enable TCP/IP Filtering (All Adapters).
7For each of the sections, TCP Ports, UDP Ports, and IP Protocols, select either Permit All or Permit Only. If you select Permit Only, click the Add button to add only the ports or protocols that will be accepted. If you change your mind at any time, select the port or protocol and click Remove.
For more information on deciding which ports and protocols to specify, see “Enabling
Services,” page 130.
TCP/IP Filtering or Internet Connection Firewall?
Because ICF and TCP/IP filtering provide similar services, how can you tell which to use?
ICF is somewhat simpler to configure, and its configuration (and activation) options are easier to find in Windows XP’s configuration options than are the settings for TCP/ IP filtering.
TCP/IP filtering runs in kernel mode on Windows XP, whereas ICF is a user-mode application. Running in kernel mode enhances system performance because inbound filtered packets are examined and dropped immediately within the context of Windows XP’s kernel-mode TCP/IP drivers without forwarding the packets all the way up the protocol stack to be examined in user mode.
(continued)
571
5: Advanced Networking
Part 5: Advanced Networking
20 Chapter
Inside Out (continued) Additionally, by default, ICF blocks all inbound traffic unless configured otherwise; on the contrary, TCP/IP filtering can allow all inbound traffic for particular protocols with minimum configuration while excluding ports for other protocols.
Also, TCP/IP filtering acts on all network adapters on the computer, whereas ICF must be enabled on each adapter you want to protect.
Both TCP/IP filtering and ICF work only on inbound network connections. To filter outbound traffic, another solution, such as ZoneAlarm, is needed.
Detecting Windows XP Security Issues
Microsoft has developed a powerful tool for scanning Windows computers to detect potential security risks. This tool, the Microsoft Baseline Security Analyzer (MBSA), is available from Microsoft at www.microsoft.com/security.
MBSA scans your computer and compares its configuration to security standards maintained by Microsoft. These standards are downloaded in an XML file each time a scan is run to ensure that the latest patches and security issues are included. MBSA
can scan for missing service packs and hotfixes for the operating system, IIS, Microsoft SQL Server, Internet Explorer, and the Office applications, as well as scan to check that the local computer is configured to meet recommended security standards.
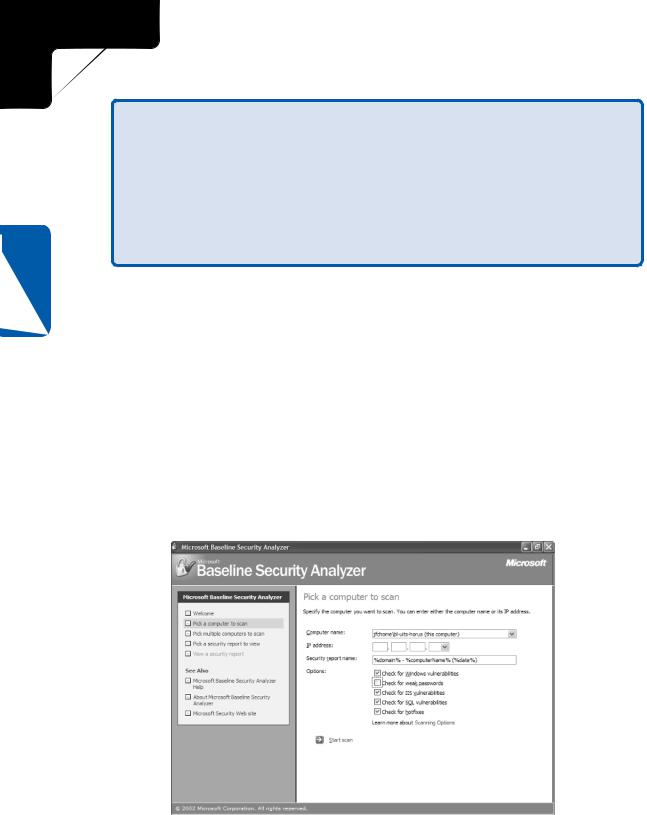
To scan a computer using MBSA, download the tool, and then launch it by doubleclicking its icon. Click the Scan A Computer button to display the following screen.
572
5: Advanced Networking
Chapter 20: Maintaining Network Security
On the Pick A Computer To Scan screen, you can scan either the local computer or a remote computer, which can be specified by computer name or IP address in the Computer Name or IP Address box. You can also select which types of vulnerabilities to scan for in the Options section. Click Start Scan to begin scanning the specified computer.
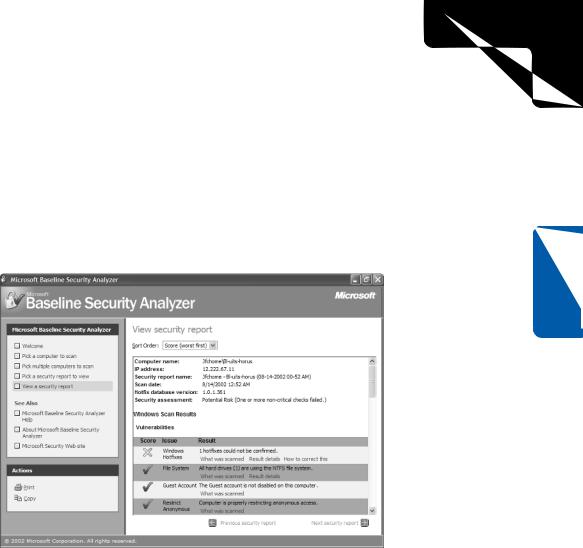
Once the scan is complete, a report is displayed, similar to the one below, showing a summary along with detailed results for each portion of the scan. Each result contains links showing exactly what was scanned, what was detected, and instructions on correcting the vulnerability. This is an extremely powerful tool for securing Windows XP from the most up-to-date list of threats.
Chapter 20
Keeping Software Up to Date
Part of Microsoft’s Trustworthy Computing Initiative involves the aggressive development of patches whenever security vulnerabilities are discovered in Windows XP or in other Microsoft applications, such as Internet Explorer, Outlook Express, or Office.
Taking advantage of these patches is critical to maintaining system security.
Windows Update is a service that can download and install the latest critical updates (as well as feature enhancements) to Microsoft products. It can be launched manually by choosing Start, Windows Update. It can also be automatically run by the Automatic Updates service.
To configure Automatic Updates, follow these steps:
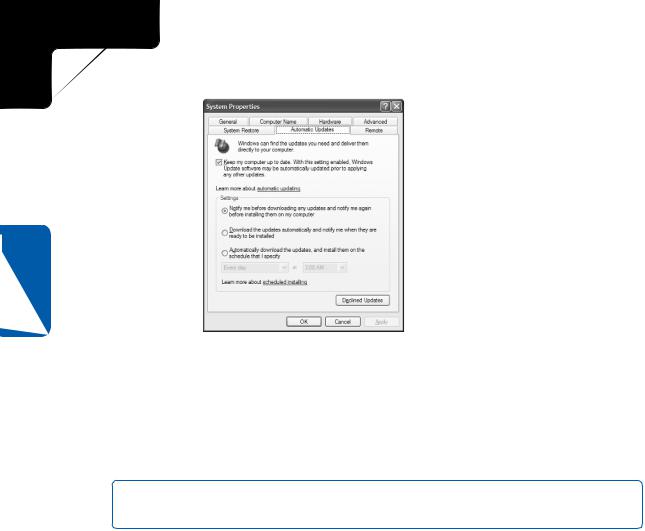
1Open Control Panel and then open System. Select the Automatic Updates tab, as shown on the next page.
573
5: Advanced Networking
Part 5: Advanced Networking
20 Chapter
2Select the check box labeled Keep My Computer Up To Date to enable Automatic Updates.
3In the Settings section, you can choose to be notified before anything is downloaded and installed, choose to have updates automatically downloaded but to be notified before they’re installed, or choose to have updates downloaded and installed automatically. If you select the last option, you can even schedule the updates by specifying a day (or Every Day) and the time of day.
note The Declined Updates button enables Windows to renotify you about any updates that you previously chose not to install.
Automatic Updates displays an icon in the taskbar’s notification area to notify you when updates are ready to be downloaded or installed if it is not configured to install them automatically. You can click this icon and select whether or not to download and install the update. Once installation begins, you will be notified if a system restart is required.
Removing Unneeded Services
Another effective method for preventing attacks on network services is to disable those services entirely. It’s normally wise to disable all network services that aren’t specifically needed. Before doing so, however, it’s important to understand what those services provide and what functionality will be lost if they are disabled.
To view the services currently installed on your computer, follow these steps:
1Launch the Services MMC snap-in by choosing Start, Administrative Tools, Services, as shown next.
574

5: Advanced Networking
Chapter 20: Maintaining Network Security
Chapter 20
2Select the Extended tab to see all currently installed services with a short description to the left of each service you click.
3To disable a service, double-click the service, and select Disabled in the Startup Type box, shown here.
Although many services in Windows XP rely upon, or take advantage of, network connections, there are several that are commonly disabled in order to lock down (protect) a Windows XP installation.
●FTP Publishing. This service, which can be installed as part of IIS, allows for the uploading and downloading of files via the File Transfer Protocol (FTP). If the computer does not need to act as an FTP server, this service should be disabled (or uninstalled completely).
575

5: Advanced Networking
Part 5: Advanced Networking
20 Chapter
●Infrared Monitor. This service supports IrDA infrared communications devices and detects other IrDA devices within range. Unless you specifically intend to perform infrared communications between devices, this service should be disabled.
●Remote Registry. This service allows remote users who have the appropriate rights to connect to a Windows XP computer over the network and view and modify the system registry. Intuitively, it would make sense to disable this service unless remote registry access is absolutely necessary. However, because remote registry access is key to being able to remotely scan a computer for proper security configuration and updates, disabling it causes those scans to fail. In fact, the scans return (strangely enough) error messages claiming the target of the scan is insecure! Therefore, if you intend to scan
a computer remotely for security purposes, leave this service enabled; in addition, if you wish to centrally manage your computers (a process that normally requires at least some registry access), and they are placed behind a firewall, this service can also be left enabled. Otherwise, it should be disabled.
●Server. The Server service allows Windows XP to serve file and printer shares across the network via Server Message Block (SMB). If this functionality is not needed (for instance, you do not intend to share files or printers with others on any network), this service should be disabled. Keep in mind, however, that if you disable the Workstation and Server services, you will not be able to share files or printers with other Windows users.
●Simple Mail Transfer Protocol (SMTP). The SMTP service, which is installed as part of IIS, serves as a delivery and routing agent for electronic mail. SMTP is notorious for its security flaws and should be disabled unless absolutely needed.
note Keep in mind that you do not need to run an SMTP service in order to send and receive personal e-mail messages; using an SMTP service is only required in order to use your computer as an e-mail server or relay.
●SNMP Service. The Simple Network Management Protocol (SNMP) allows for the examination and administration of remote computers and network devices; however, its security mechanisms are limited, and by default, SNMP is totally insecure. Unless needed for network administration, SNMP should be disabled.
●SNMP Trap Service. The SNMP Trap Service allows the computer to receive trap messages, or alerts, sent by local or remote SNMP agents. Unless needed for network administration, the SNMP Trap Service should be disabled.
●TCP/IP NetBIOS Helper. This service allows the use of the NetBIOS Over TCP/IP (NetBT) protocol. The service provides compatibility with Microsoft Windows NT 4.0–style networks. If the computer does not need
576

5: Advanced Networking
Chapter 20: Maintaining Network Security
to perform file and printer sharing with those networks, this service should be disabled.
●Telnet. This service allows remote users running the Internet-standard Telnet client to connect to your Windows XP computer and administer it as though they were connected locally, if they have an account with sufficient privileges on your computer. Telnet passes all data in clear text, including logon user names and passwords; for this reason, this service should be disabled.
●Workstation. The Workstation service allows Windows XP to access file and printer shares across the network via SMB. If this functionality is not needed (for instance, you have no intention of connecting to another computer to access its file and printer shares), this service can be disabled. Keep in mind, however, that if you disable the Workstation and Server services, you will not be able to share files or printers with other Windows users.
●World Wide Web Publishing. This service, which is installed as part of IIS, acts as its HTTP server. Unless you specifically need to serve (host) Web content to others, this service should be disabled.
Securing IIS
Microsoft has included IIS in one version or another of every Windows release since Windows NT 4.0. Its relative ease of configuration and use has made it a popular option for serving Internet and intranet content.
However, IIS also has a reputation for being insecure due to a rash of security vulnerabilities discovered over time in various releases of the product. Some of these vulnerabilities led to the propagation of major Internet worms such as the infamous Code Red. Although these worms did not bring the Internet to its knees, as many doomsayers predicted, they proved to be a major source of frustration and expense for Internet users and system administrators everywhere. These same vulnerabilities can be used to take control of the attacked computer, allowing a hacker to deface Web site content, download or destroy valuable data, or use the computer as part of a DDoS attack (see “Denial of Service Attacks,” page 560).
These security issues were not, however, due to fundamental, irreparable security flaws in IIS. In fact, the vast majority of famous IIS security exploits had been publicized, along with patches to correct them, by Microsoft for weeks, months, or even years before widespread attacks were launched to take advantage of them. However, due to its default installation in previous versions of Windows, many Windows users had no idea IIS was even installed on their computers (or they had forgotten), leaving them wide open to attack. Additionally, in the past, it was difficult for Windows users to learn of new security updates to Microsoft products.
Microsoft has addressed these issues in a number of ways, including increasing the visibility of security updates and releasing tools for securing IIS installations. Perhaps the
Chapter 20
577
