
- •Table of Contents
- •Cisco Network Security Little Black Book
- •Introduction
- •Is this Book for You?
- •How to Use this Book
- •The Little Black Book Philosophy
- •Chapter 1: Securing the Infrastructure
- •In Brief
- •Enterprise Security Problems
- •Types of Threats
- •Enterprise Security Challenges
- •Enterprise Security Policy
- •Securing the Enterprise
- •Immediate Solutions
- •Configuring Console Security
- •Configuring Telnet Security
- •Configuring Enable Mode Security
- •Disabling Password Recovery
- •Configuring Privilege Levels for Users
- •Configuring Password Encryption
- •Configuring Banner Messages
- •Configuring SNMP Security
- •Configuring RIP Authentication
- •Configuring EIGRP Authentication
- •Configuring OSPF Authentication
- •Configuring Route Filters
- •Suppressing Route Advertisements
- •Chapter 2: AAA Security Technologies
- •In Brief
- •Access Control Security
- •Cisco Secure Access Control Server
- •Immediate Solutions
- •Configuring TACACS+ Globally
- •Configuring TACACS+ Individually
- •Configuring RADIUS Globally
- •Configuring RADIUS Individually
- •Configuring Authentication
- •Configuring Authorization
- •Configuring Accounting
- •Installing and Configuring Cisco Secure NT
- •Chapter 3: Perimeter Router Security
- •In Brief
- •Defining Networks
- •Cisco Express Forwarding
- •Unicast Reverse Path Forwarding
- •TCP Intercept
- •Network Address Translation
- •Committed Access Rate
- •Logging
- •Immediate Solutions
- •Configuring Cisco Express Forwarding
- •Configuring Unicast Reverse Path Forwarding
- •Configuring TCP Intercept
- •Configuring Network Address Translation (NAT)
- •Configuring Committed Access Rate (CAR)
- •Configuring Logging
- •Chapter 4: IOS Firewall Feature Set
- •In Brief
- •Port Application Mapping
- •IOS Firewall Intrusion Detection
- •Immediate Solutions
- •Configuring Port Application Mapping
- •Configuring IOS Firewall Intrusion Detection
- •Chapter 5: Cisco Encryption Technology
- •In Brief
- •Cryptography
- •Benefits of Encryption
- •Symmetric and Asymmetric Key Encryption
- •Digital Signature Standard
- •Cisco Encryption Technology Overview
- •Immediate Solutions
- •Configuring Cisco Encryption Technology
- •Chapter 6: Internet Protocol Security
- •In Brief
- •IPSec Packet Types
- •IPSec Modes of Operation
- •Key Management
- •Encryption
- •IPSec Implementations
- •Immediate Solutions
- •Configuring IPSec Using Manual Keys
- •Configuring Tunnel EndPoint Discovery
- •Chapter 7: Additional Access List Features
- •In Brief
- •Wildcard Masks
- •Standard Access Lists
- •Extended Access Lists
- •Reflexive Access Lists
- •Dynamic Access Lists
- •Additional Access List Features
- •Immediate Solutions
- •Configuring Standard IP Access Lists
- •Configuring Extended IP Access Lists
- •Configuring Extended TCP Access Lists
- •Configuring Named Access Lists
- •Configuring Commented Access Lists
- •Configuring Dynamic Access Lists
- •Configuring Reflexive Access Lists
- •Appendix A: IOS Firewall IDS Signature List
- •Appendix B: Securing Ethernet Switches
- •Configuring Management Access
- •Configuring Port Security
- •Configuring Permit Lists
- •Configuring AAA Support
- •List of Figures
- •List of Tables
- •List of Listings
Immediate Solutions
Configuring Context−Based Access Control
Many steps must be followed to configure CBAC to function properly. The first major step is to decide whether to configure CBAC on the inside or outside interface of your firewall router. The inside interface is the interface that originates the sessions and allows traffic back through the firewall. The outside interface refers to the interface where sessions cannot originate. This step is a mental step and requires no configuration command at this point. To configure CBAC, perform the tasks described in the following steps:
1.Use the following command to define an extended access list and the parameters that CBAC will use to inspect traffic or deny traffic:
access−list <access−list−number> <deny | permit> <protocol> − <source source−wildcard> <destination destination−wildcard>
2. Use the following command to configure CBAC for generic TCP or UDP packet inspection:
ip inspect name <inspection−name> <tcp | udp> <alert on | off> − <audit−trail on | off> <timeout seconds>
3.Use the following command to define an inspection rule on a per−Application−layer−traffic basis:
ip inspect name <inspection−name> <protocol> <alert on | off> − <audit−trail <on | off> <timeout seconds>
This command can be used for all CBAC inspection protocols except for RPC and Java. Per−protocol inspection takes precedence over generic TCP or UDP inspection.
4. Use the following command to enable CBAC for RPC inspection:
ip inspect name <inspection−name> <rpc program−number number> − <wait−time minutes> <alert on | off> <audit−trail on |
off> <timeout seconds>
Use of this command is optional, but it must be used to support blocking of RPC protocols. 5. Use the following command to enable CBAC for Java applet blocking:
ip inspect name <inspection−name> http <java−list access− list> −
<alert on | off> <audit−trail on | off> <timeout seconds>
This command specifies the use of the HTTP protocol and a standard numbered access list to use to determine if a site's Java applets should be allowed. Use of this command is optional; however, it must be used to support blocking of Java applets.
6. Use the following command to configure the router for inspection of fragmented packets:
ip inspect name <inspection−name> <fragment − max number> <timeout seconds>
131
Use of this command is optional, but it is always recommended because it specifies the maximum number of packets that can arrive at the router interface before the initial packet for a session, for which state information is allocated.
7.Use the ip inspect audit−trail command to turn on audit trail logging for CBAC messages. Use of this command is optional.
The next few steps configure the timeouts and thresholds that CBAC uses to determine how long to manage the state information for each session and to determine when to drop a session if the session does not become established. The timeouts and thresholds apply globally to all sessions, and the default timeout and threshold values may be used or you can change them to the values that are determined by the enterprise's security policy. To configure specific CBAC timeout and threshold values, use the commands in the following steps:
8.Use this command to determine the length of time the software waits for a TCP session to reach the established state before dropping the session:
ip inspect tcp synwait−time seconds
The session has reached the established state after the session's first SYN bit is detected.
9.Use this command to determine the length of time a TCP session will still be managed after the firewall detects a FIN−exchange, which determines that a session is about to close:
ip inspect tcp finwait−time seconds
10.Use the following command to determine the length of time a TCP session will still be managed after no activity:
ip inspect tcp idle−time seconds
CBAC will not continue to maintain state information for a session that violates the idle time.
11.Use this command to determine the length of time a UDP session will still be managed after no activity:
ip inspect udp idle−time seconds
Because UDP is a connectionless service, there are no actual sessions, so CBAC will approximate sessions by examining the information in the packet and determining if the packet is similar to other UDP packets and if the packet was detected soon after another similar UDP packet. CBAC will not continue to maintain state information for a session that violates the idle time.
12.Use this command to determine the length of time a DNS name lookup session will still be managed after no activity:
ip inspect dns−timeout seconds
132
CBAC applies the DNS timeout to all DNS name lookup sessions, and the DNS timeout overrides the timeout value specified by the UDP timeout.
13.Because CBAC measures both the total number of existing half−open sessions and the rate of session establishment attempts for both TDP and UDP, use this command to determine the number of existing half−open sessions that will cause the software to start deleting them:
ip inspect max−incomplete high number
A high number of half−open sessions could indicate a denial−of−service attack.
14.If the total max−incomplete high session threshold is reached, CBAC will begin dropping half−open sessions and continue to do so until the total number of half−open sessions falls below the value configured using this command:
ip inspect max−incomplete low number
15.Use this command to set the rate of thresholds that are measured as the number of new session connection attempts are detected in the last one−minute sample period:
ip inspect one−minute high number
When new connection attempts rise above the configured threshold within the sample period, CBAC will begin to drop new connection requests.
16.If the total one−minute high session threshold is reached, CBAC will begin dropping half−open sessions and continue to do so until the total number of half−open sessions fall below the value configured using this command:
ip inspect one−minute low number
17.Use the following command to set the number of existing half−open TCP sessions with the same destination host address that will cause the software to start dropping half−open sessions to the same destination host address:
ip inspect tcp max−incomplete host number block−time minutes
Some very important rules relate to Step 1, configuring the access lists for CBAC operation on the internal and external interfaces. These rules will be referred to over and over again within this section, and it is highly recommended that you refer back to these rules for clarity if you are planning to implement CBAC within your organization, and you are having trouble implementing CBAC within your network. If you are configuring CBAC on the internal interface, follow these rules:
∙If an inbound IP access list is configured on the internal interface, the access list can be either a standard or extended access list. The access lists should permit traffic that should be inspected by CBAC. If traffic is not permitted, it will not be inspected by CBAC and will be dropped.
∙An outbound IP access list at the internal interface must be an extended access list. The outbound access list should deny traffic that you want to be inspected by CBAC. CBAC will create temporary openings in the outbound access list as needed to permit only return traffic that is part of an existing session.
If you are configuring CBAC on the external interface, follow these rules:
133

∙If an outbound IP access list is configured on the external interface, the access list can be a standard or extended access list. The access list should permit traffic that should be inspected by CBAC. If traffic is not permitted, it will not be inspected by CBAC and will be dropped.
∙If an inbound IP access list is configured on the external interface, the access list must be an extended access list. The inbound access list should deny traffic that should be inspected by CBAC. CBAC will create temporary openings in the inbound access list as needed to permit only return traffic that is part of an existing session.
Note If you are planning to implement CBAC within your organization, refer to the access list rules listed above for help in understanding how to configure your access lists to define your rules of inspection.
Well, think about it; are there enough commands for CBAC? At first glance the configuration for CBAC may seem overwhelming, but I shall take a slow approach into explaining the configuration power that CBAC provides. I will start with a simple network that is shown in Figure 4.2. In this network, Router 3 has two interfaces and is the router that provides CBAC functionality for the inside trusted network. Router 3's inside trusted network uses address space within the private 192.168.10.0 address space. Router 3 is also connected to the outside untrusted network using its Serial interface and using the public address space 192.168.20.0.
The 192.168.20.0 network is actually private address space as a l l o c a t e d f r o m R F C 1 9 1 8 , w h i c h c a n b e f o u n d a t http://www.ietf.org/rfc/rfc1918.txt?number=1918. It is only used here for the benefit of protecting the innocent.
In Figure 4.2, you can see that Router 3 is connected to an inside and outside network. The security administrators for Router 3 want to provide CBAC security for the hosts displayed in Figure 4.2. The first host is a mail server, at IP address 192.168.10.10, which needs to have the Simple Mail Transport Protocol opened for its use. The other host is a host on the network, at IP address 192.168.10.20; the security administrators have decided it would also benefit from the security functionality that CBAC provides.
134

CBAC actively inspects the activity behind a firewall. CBAC specifies what traffic should be let in and what traffic should be let out by using access lists. However, CBAC access lists include ip inspect statements that allow the inspection of the protocol to make sure that it has not been tampered with before the protocol goes to the systems behind the firewall. Listing 4.1 displays Router 3's configuration for CBAC, which meets the security requirements of the network displayed in Figure 4.2.
Listing 4.1: Example configuration of Router 3 for CBAC.
access−list 110 |
permit tcp 192.168.10.0 0.0.0.255 any |
access−list 110 |
permit udp 192.168.10.0 0.0.0.255 any |
access−list 110 |
permit icmp 192.168.10.0 0.0.0.255 any |
access−list 110 |
deny ip any any |
access−list 120 |
permit icmp any 192.168.10.0 0.0.0.255 − |
echo−reply |
|
access−list 120 |
permit icmp any 192.168.10.0 0.0.0.255 − |
unreachable |
|
access−list 120 |
permit icmp any 192.168.10.0 0.0.0.255 |
admin−prohibited |
|
access−list 120 |
permit icmp any 192.168.10.0 0.0.0.255 − |
packet−too−big |
|
access−list 120 |
permit icmp any 192.168.10.0 0.0.0.255 − |
echo |
|
access−list 120 |
permit icmp any 192.168.10.0 0.0.0.255 − |
time−exceeded |
|
access−list 120 |
deny ip any any |
! |
|
ip inspect name |
samplecbac ftp |
ip inspect name |
samplecbac smtp |
ip inspect name |
samplecbac tcp |
ip inspect name |
samplecbac fragment max 6000 timeout 8 |
! |
|
interface FastEthernet0/0 |
|
ip address 192.168.10.1 255.255.255.0 |
|
ip access−group |
110 in |
ip inspect samplecbac in |
|
ip inspect samplecbac out |
|
! |
|
interface Serial0/0 |
|
ip address 192.168.20.1 255.255.255.0 |
|
ip access−group |
120 in |
! |
|
ip route 0.0.0.0 0.0.0.0 192.168.20.2
Notice that CBAC is performing a more generic TCP and UDP inspection. The access list that permits ICMP traffic, access list 110, is there to permit outbound ICMP traffic that arrives inbound on interface FastEthernet0/0. CBAC does not inspect ICMP traffic but it has to be listed in order to permit the outbound ICMP traffic because of the deny any any statement at the end of the access list. The ip inspect name command configures Router 3 to perform CBAC inspection. At first glance, the CBAC configuration combined with the access lists that are configured on each interface may not seem correct, but remember that CBAC creates temporary access list openings. Referring back to the rules for creating an inbound access list on an interface, the rule states that the access lists should permit traffic that should be inspected by CBAC. If traffic is not permitted, it will not be inspected by CBAC and will be dropped. The temporary openings will be created in access list 120, which is applied to the outside Serial interface.
135

Looking now at access list 120, you can see that the access list is applied as an inbound access list on interface Serial0/0. Still doesn't look correct though, does it? Look again at the rules for creating an inbound access list on the external interface. The rule states that an inbound access list applied to the external interface should deny traffic that should be inspected by CBAC. CBAC will create temporary openings in the inbound access list as needed to permit only return traffic that is part of an existing session. Notice that access list 120 permits only ICMP traffic inbound on the Serial interface and denies all other traffic; all traffic that is denied by an access list will be inspected by CBAC, and an opening was created within this access list by the originating traffic.
To view the complete CBAC inspection configuration, you must issue the sh ip inspect config command. The output of this command displays the protocols that should be inspected by CBAC and the associated timeout values for each protocol. Issuing the show ip inspect config command on Router 3 lists the output displayed in Listing 4.2.
Listing 4.2: Output of the show ip inspect command.
Router−3#sh ip inspect config
Session audit trail is disabled Session alert is enabled one−minute (sampling period) thresholds are [400:500] − connections
max−incomplete sessions thresholds are [400:500] max−incomplete tcp connections per host is 50. Block−time 0 − minute.
tcp synwait−time is 30 sec — tcp finwait−time is 5 sec tcp idle−time is 3600 sec — udp idle−time is 30 sec dns−timeout is 5 sec
Inspection Rule Configuration Inspection name samplecbac
ftp alert is on audit−trail is off timeout 3600 smtp alert is on audit−trail is off timeout 3600 tcp alert is on audit−trail is off timeout 3600
fragment Max 6000 In Use 0 alert is on audit−trail is off timeout − 8
Router−3#
The output of the show ip inspect config command displays many of the configured timeout and threshold values for the CBAC configuration. The first line of the output tells you that CBAC audit trail messages are disabled. The second line shows that session alerting is enabled; use of the show ip inspect config command displays alert messages to the console port of the router. The next six lines display output that pertain to timeout values for CBAC. The inspection rules section is the major output section within the show ip inspect config command and details the inspection name and the protocols that are configured for CBAC operation, the audit trail information, and the configured timeout values for each inspection rule.
You can use the ip inspect audit−trail global configuration command to configure CBAC audit trail messages and display them on the console after each session closes. Audit trail messages help in analyzing problems that are occurring during CBAC operation. The following shows the command issued on Router 3:
Router−3#config t
Router−3(config)#ip inspect audit−trail
Router−3(config)#end
Router−3#
136

Immediately after the command is issued on Router 3, audit trail information begins to appear on the console. The output of the audit trail messages is shown in Listing 4.3.
Listing 4.3: Audit trail messages on Router 3.
:tcp session initiator (192.168.10.13:38992)sent 22 bytes − responder (192.168.40.11:25) sent 198 bytes
:ftp session initiator 192.168.10.18:32294) sent 336 bytes − responder (192.168.129.11:21) sent 495 bytes
After enabling audit trail output and taking a quick glance back at the inspection configuration, you can see that audit trail messages are now enabled. Listing 4.4 shows the updated listing.
Listing 4.4: Updated output from the show ip inspect command.
Router−3#show ip inspect config Session audit trail is enabled Session alert is enabled
one−minute (sampling period) thresholds are [400:500] − connections
max−incomplete sessions thresholds are [400:500] max−incomplete tcp connections per host is 50. Block−time 0 − minute.
tcp synwait−time is 30 sec – tcp finwait−time is 5 sec tcp idle−time is 3600 sec – udp idle−time is 30 sec dns−timeout is 5 sec
Inspection Rule Configuration Inspection name samplecbac
ftp alert is on audit−trail is on timeout 3600 smtp alert is on audit−trail is on timeout 3600 tcp alert is on audit−trail is on timeout 3600
fragment Maximum 6000 In Use 0 alert is on audit−trail is off − timeout 8
Router−3#
Changes to any of the global timeout and threshold values described earlier can be made to the configuration, and the change will be reflected in the output of the show ip inspect config.
CBAC can also be configured to perform Java blocking, which will allow into the network Java applets from specified sites on the Internet and deny all others. This type of blocking denies access to Java applets that are not embedded in an archived or compressed file. Referring to Figure 4.3, I will continue with the example from above and configure Router 3 for Java blocking. In Figure 4.3, you can see that three different Web servers have been added to the outside network of Router 3. The IP addresses of the Web servers are 192.168.100.100, 192.168.200.200, and 192.168.300.300. The security policy of the company is to configure Router 3 such that any Java applet from the Web servers at IP addresses 192.168.100.100 and 192.168.200.200 are permitted and inspected by CBAC, yet the Java applets from the server at IP address 192.168.300.300 are denied. Listing 4.5 shows the configuration needed to configure Router 3 for Java blocking.
137
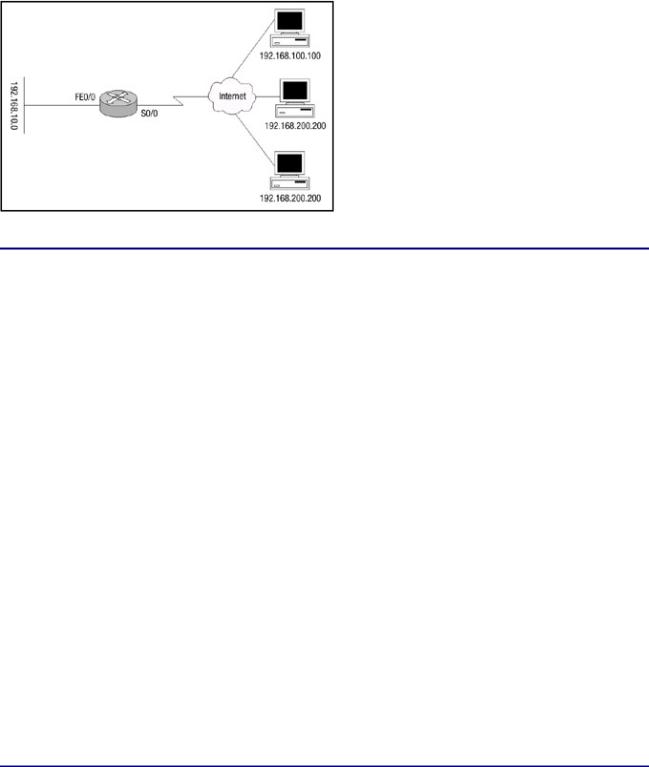
Figure 4.3: Network configured for Java blocking.
Listing 4.5: Configuring Router 3 for Java blocking.
access−list 30 permit 192.168.100.100 access−list 30 permit 192.168.200.200
access−list 110 permit tcp 192.168.10.0 0.0.0.255 any access−list 110 permit udp 192.168.10.0 0.0.0.255 any access−list 110 permit icmp 192.168.10.0 0.0.0.255 any access−list 150 permit icmp any 192.168.10.0 0.0.0.255 − echo−reply
access−list 150 permit icmp any 192.168.10.0 0.0.0.255 − unreachable
access−list 150 permit icmp any 192.168.10.0 0.0.0.255 admin−prohibited
access−list 150 permit icmp any 192.168.10.0 0.0.0.255 − packet−too−big
access−list 150 permit icmp any 192.168.10.0 0.0.0.255 − echo
access−list 150 permit icmp any 192.168.10.0 0.0.0.255 − time−exceeded
access−list 150 deny ip any any
!
ip inspect name mytest tcp ip inspect name mytest udp
ip inspect name mytest http java−list 30
ip inspect name mytest fragment max 6000 timeout 8 ip inspect audit−trial
!
interface FastEthernet0/0
ip address 192.168.10.1 255.255.255.0 ip access−group 110 in
!
interface Serial0/0
ip address 192.168.20.1 255.255.255.0 ip access−group 150 in
ip inspect mytest out ip inspect mytest in
In this example, access−list 30 allows Java from friendly sites at IP addresses 192.168.100.100 and 192.168.200.200 while implicitly denying Java from other sites. The output displayed in Listing 4.6 is sample debug output from the debug ip inspect detail command after attempting to connect to the Web servers on 192.168.100.100, 192.168.200.200, and 192.168.300.300. The debug ip inspect detail displays the output of connection requests from friendly Java Web servers, and it also shows Java being blocked from a nonfriendly Web server. Friendly Web servers are servers that are listed with a permit statement within the access list configuration.
138

Listing 4.6: Debug output of Java blocking.
Router−3#debug ip inspect detail
...
:http session initiator (192.168.10.37:3271) sent 215 bytes − responder (192.168.100.100:80) sent 3162 bytes
:http session initiator (192.168.10.28:4972) sent 143 bytes − responder (192.168.200.200:80) sent 254 bytes
:http session initiator (192.168.10.37:3272) sent 324 bytes − responder (192.168.100.10:80) sent 234 bytes
:http session initiator (192.168.10.28:4973) sent 343 bytes − responder (192.168.200.200:80) sent 314 bytes
:http session initiator (192.168.10.37:3274) sent 344 bytes − responder (192.168.100.100:80) sent 8 bytes
:http session initiator (192.168.10.28:4974) sent 360 bytes − responder (192.168.200.200:80) sent 206 bytes
:http session initiator (192.168.10.37:3275) sent 345 bytes − responder (192.168.100.100:80) sent 12276 bytes
:http session initiator (192.168.10.28:4975) sent 369 bytes − responder (192.168.200.200:80) sent 206 bytes
:http session initiator (192.168.10.37:3276) sent 354 bytes − responder (192.168.100.100:80) sent 278 bytes
:JAVA applet is blocked from (192.168.300.300:80) to (192.168.10.28:8394).
:JAVA applet is blocked from (192.168.300.300:80) to − (192.168.10.28:8395).
:http session initiator (192.168.10.37:1298) sent 215 bytes − responder (192.168.100.100:80) sent 302 bytes
:JAVA applet is blocked from (192.168.300.300:80) to − (192.168.10.37:1422).
:http session initiator (192.168.10.28:1203) sent 362 bytes − responder (192.168.100.100:80) sent 162 bytes
:JAVA applet is blocked from (192.168.300.300:80) to − (192.168.10.37:1723).
The CBAC configurations have been fairly basic so far. In the next example, Router 3 will be configured for CBAC, but this time, another interface has been added to the Router (see Figure 4.4). This interface, interface Ethernet1/0, will be used for providing Web, FTP, and mail services to the outside external Internet. Ethernet1/0 is connected to the "DMZ" network and has a single host within the network used to provide the services mentioned earlier to the outside world. Ethernet0/0 is connected to the internal local network. Router 3's configuration is shown in Listing 4.7.
Figure 4.4: Router 3 configured for CBAC with three interfaces.
Listing 4.7: CBAC configuration of Router 3 with three interfaces.
139

ip inspect audit−trail |
|
ip inspect tcp idle−time |
14400 |
ip inspect udp idle−time |
1800 |
ip inspect dns−timeout 7 |
|
! |
|
ip inspect name cbactest |
cuseeme |
ip inspect name cbactest |
ftp |
ip inspect name cbactest |
h323 |
ip inspect name cbactest |
http |
ip inspect name cbactest |
rcmd |
ip inspect name cbactest |
realaudio |
ip inspect name cbactest |
smtp |
ip inspect name cbactest |
sqlnet |
ip inspect name cbactest |
streamworks |
ip inspect name cbactest |
tcp |
ip inspect name cbactest |
tftp |
ip inspect name cbactest |
udp |
ip inspect name cbactest |
vdolive |
ip inspect name cbactest |
fragment max 6000 timeout 8 |
!
interface ethernet0/0
ip address 192.168.10.1 255.255.255.0 ip access−group 100 in
ip access−group 101 out ip inspect cbactest in
!
interface ethernet1/0
ip address 192.168.20.1 255.255.255.0 ip access−group 102 in
ip access−group 103 out
!
interface serial0/0
ip address 192.168.30.1 255.255.255.0 ip access−group 104 in
ip access−group 105 out ip inspect cbactest in
!
access−list 100 permit ip 192.168.10.0 0.0.0.255 any access−list 100 deny ip any any
!
access−list 101 permit icmp any 192.168.10.0 0.0.0.255 − admin−prohibited
access−list 101 permit icmp any 192.168.10.0 0.0.0.255 − echo
access−list 101 permit icmp any 192.168.10.0 0.0.0.255 − echo−reply
access−list 101 permit icmp any 192.168.10.0 0.0.0.255 − packet−too−big
access−list 101 permit icmp any 192.168.10.0 0.0.0.255 − time−exceeded
access−list 101 permit icmp any 192.168.10.0 0.0.0.255 − traceroute
access−list 101 permit icmp any 192.168.10.0 0.0.0.255 − unreachable
access−list 101 deny ip any any
!
access−list 102 permit ip 192.168.20.0 0.0.0.255 any access−list 102 deny ip any any
!
access−list 103 permit udp any host 192.168.20.20 eq domain access−list 103 permit tcp any host 192.168.20.20 eq domain access−list 103 permit tcp any host 192.168.20.20 eq www
140

access−list 103 |
permit |
tcp any host 192.168.20.20 eq ftp |
||
access−list 103 |
permit |
tcp any host 192.168.20.20 eq smtp |
||
access−list 103 |
permit |
tcp 192.168.10.0 0.0.0.255 host |
− |
|
192.168.20.20 eq pop3 |
|
|
|
|
access−list 103 |
permit |
tcp 192.168.10.0 0.0.0.255 any eq telnet |
||
access−list 103 |
permit |
icmp |
any 192.168.20.0 0.0.0.255 |
− |
admin−prohibited |
|
|
|
|
access−list 103 |
permit |
icmp |
any 192.168.20.0 0.0.0.255 |
echo |
access−list 103 |
permit |
icmp |
any 192.168.20.0 0.0.0.255 |
echo−reply |
access−list 103 |
permit |
icmp |
any 192.168.20.0 0.0.0.255 |
− |
packet−too−big |
|
|
|
|
access−list 103 |
permit |
icmp |
any 192.169.20.0 0.0.0.255 |
− |
time−exceeded |
|
|
|
|
access−list 103 |
permit |
icmp |
any 192.168.20.0 0.0.0.255 |
traceroute |
access−list 103 |
permit |
icmp |
any 192.168.20.0 0.0.0.255 |
unreachable |
access−list 103 |
deny ip any |
any |
|
|
! |
|
|
|
|
access−list 104 |
deny ip 192.168.10.0 0.0.0.255 any |
|
||
access−list 104 |
deny ip 192.168.20.0 0.0.0.255 any |
|
||
access−list 104 |
permit |
ip any any |
|
|
! |
|
|
|
|
access−list 105 |
permit |
icmp |
192.168.10.0 0.0.0.255 any |
echo−reply |
access−list 105 |
permit |
icmp |
192.168.20.0 0.0.0.255 any |
echo−reply |
access−list 105 |
permit |
icmp |
192.168.10.0 0.0.0.255 any |
− |
time−exceeded |
|
|
|
|
access−list 105 |
permit |
icmp |
192.168.20.0 0.0.0.255 any |
− |
time−exceeded |
|
|
|
|
access−list 105 |
deny ip 192.168.20.0 0.0.0.255 any |
|
||
access−list 105 |
permit |
ip 192.168.10.0 0.0.0.255 any |
|
|
|
|
|
|
|
In the configuration in Listing 4.7, the first command line enables audit trail logging of session information, the second and third lines set the length of time a TCP and UDP session is managed after no activity is received, and the fourth line sets the length of time a DNS name lookup session is still managed after no activity is received. The next set of configuration lines sets up an inspection list that is named cbactest; this CBAC inspection list will be used for inspection of inbound traffic on Ethernet0/0 and inbound return traffic on Serial0/0. Under interface Ethernet0/0, access list 100 is applied to allow all legitimate traffic from the inside network. Access list 101 is also applied to allow some ICMP traffic and deny everything else. The inspection list cbactest will add entries to this list to permit return traffic for connections established from the inside. Finally, under interface Ethernet0/0, the inspection list cbactest is applied to inspect inbound traffic on Ethernet0/0.
Under interface Ethernet1/0, access list 102 is applied to permit inbound traffic initiated from hosts within the DMZ. Access list 103 is also applied, which allows only certain services to establish a connection with the hosts within the DMZ network. The inspection rules that are configured on other interfaces will add temporary entries to this list. Under interface Serial0/0, access list 104 is applied; it is configured to prevent any spoofing of packets that are inbound on Serial0/0 and contain a source address in the header of the packet such that the packet appears to have originated from within the "inside" network. Access list 105 is also configured; it allows Ping replies from the inside network or the DMZ network and permits inside traffic back out.
CBAC can also function on a router that also has Network Address Translation (NAT) or Port Address Translation (PAT) configured. The configuration in the next example works well for any office connected directly to the Internet and utilizing the functionality of NAT.
In the sample network shown in Figure 4.5, no services are run on the inside network behind Router 3. Ethernet1/0 is the "inside" network. Serial0/0 is the outside interface. Users on the inside local
141

network of 192.168.10.0 must have their IP addresses translated to public routable addresses within the 192.168.20.0 address space. Also, CBAC services must be provided for users on the inside network. The configuration for Router 3 that is shown in Listing 4.8 meets these requirements.
Figure 4.5: CBAC and NAT network design.
Note The 192.168.20.0 network is actually private address space as allocated from RFC 1918, which can be found at http://www.ietf.org/rfc/rfc1918. It is only used here for the benefit of protecting the innocent.
Listing 4.8: Router 3 configured for CBAC and NAT.
ip inspect name cbacnat cuseeme timeout 3600
ip inspect name cbacnat ftp audit−trail on timeout 3600 ip inspect name cbacnat h323 timeout 3600
ip inspect name cbacnat http timeout 3600
ip inspect name cbacnat realaudio timeout 3600 ip inspect name cbacnat smtp timeout 3600
ip inspect name cbacnat sqlnet timeout 3600
ip inspect name cbacnat streamworks timeout 3600 ip inspect name cbacnat tcp timeout 3600
ip inspect name cbacnat tftp timeout 30 ip inspect name cbacnat udp timeout 15
!
ip inspect tcp synwait−time 15 ip inspect tcp idle−time 1800 ip inspect udp idle−time 60
ip inspect max−incomplete high 250 ip inspect max−incomplete low 150 ip inspect one−minute high 250
ip inspect one−minute low 150
!
interface Ethernet0
ip address 192.168.10.1 255.255.255.0 ip access−group 101 in
no ip directed−broadcast ip nat inside
ip inspect cbacnat in
!
interface Serial0
ip address 192.168.20.1.1 255.255.255.0 ip access−group 112 in
no ip directed−broadcast ip nat outside
!
ip nat pool natpool 192.168.20.3 192.168.20.254 − netmask 255.255.255.0
ip nat inside source list 1 pool natpool ip classless
ip route 0.0.0.0 0.0.0.0 192.168.20.2
ip route 192.168.10.0 255.255.255.0 192.168.10.2
!
access−list 1 permit 192.168.10.0 0.0.0.255 access−list 101 permit tcp 192.168.10.0 0.0.0.255 any access−list 101 permit udp 192.168.10.0 0.0.0.255 any
142
