
- •Table of Contents
- •Cisco Network Security Little Black Book
- •Introduction
- •Is this Book for You?
- •How to Use this Book
- •The Little Black Book Philosophy
- •Chapter 1: Securing the Infrastructure
- •In Brief
- •Enterprise Security Problems
- •Types of Threats
- •Enterprise Security Challenges
- •Enterprise Security Policy
- •Securing the Enterprise
- •Immediate Solutions
- •Configuring Console Security
- •Configuring Telnet Security
- •Configuring Enable Mode Security
- •Disabling Password Recovery
- •Configuring Privilege Levels for Users
- •Configuring Password Encryption
- •Configuring Banner Messages
- •Configuring SNMP Security
- •Configuring RIP Authentication
- •Configuring EIGRP Authentication
- •Configuring OSPF Authentication
- •Configuring Route Filters
- •Suppressing Route Advertisements
- •Chapter 2: AAA Security Technologies
- •In Brief
- •Access Control Security
- •Cisco Secure Access Control Server
- •Immediate Solutions
- •Configuring TACACS+ Globally
- •Configuring TACACS+ Individually
- •Configuring RADIUS Globally
- •Configuring RADIUS Individually
- •Configuring Authentication
- •Configuring Authorization
- •Configuring Accounting
- •Installing and Configuring Cisco Secure NT
- •Chapter 3: Perimeter Router Security
- •In Brief
- •Defining Networks
- •Cisco Express Forwarding
- •Unicast Reverse Path Forwarding
- •TCP Intercept
- •Network Address Translation
- •Committed Access Rate
- •Logging
- •Immediate Solutions
- •Configuring Cisco Express Forwarding
- •Configuring Unicast Reverse Path Forwarding
- •Configuring TCP Intercept
- •Configuring Network Address Translation (NAT)
- •Configuring Committed Access Rate (CAR)
- •Configuring Logging
- •Chapter 4: IOS Firewall Feature Set
- •In Brief
- •Port Application Mapping
- •IOS Firewall Intrusion Detection
- •Immediate Solutions
- •Configuring Port Application Mapping
- •Configuring IOS Firewall Intrusion Detection
- •Chapter 5: Cisco Encryption Technology
- •In Brief
- •Cryptography
- •Benefits of Encryption
- •Symmetric and Asymmetric Key Encryption
- •Digital Signature Standard
- •Cisco Encryption Technology Overview
- •Immediate Solutions
- •Configuring Cisco Encryption Technology
- •Chapter 6: Internet Protocol Security
- •In Brief
- •IPSec Packet Types
- •IPSec Modes of Operation
- •Key Management
- •Encryption
- •IPSec Implementations
- •Immediate Solutions
- •Configuring IPSec Using Manual Keys
- •Configuring Tunnel EndPoint Discovery
- •Chapter 7: Additional Access List Features
- •In Brief
- •Wildcard Masks
- •Standard Access Lists
- •Extended Access Lists
- •Reflexive Access Lists
- •Dynamic Access Lists
- •Additional Access List Features
- •Immediate Solutions
- •Configuring Standard IP Access Lists
- •Configuring Extended IP Access Lists
- •Configuring Extended TCP Access Lists
- •Configuring Named Access Lists
- •Configuring Commented Access Lists
- •Configuring Dynamic Access Lists
- •Configuring Reflexive Access Lists
- •Appendix A: IOS Firewall IDS Signature List
- •Appendix B: Securing Ethernet Switches
- •Configuring Management Access
- •Configuring Port Security
- •Configuring Permit Lists
- •Configuring AAA Support
- •List of Figures
- •List of Tables
- •List of Listings
Chapter 3: Perimeter Router Security
In Brief
To say that the Internet is the single−most amazing technological achievement of the "Information Age" is a gross understatement. This massive network has changed the way the world conducts business and approaches education, and it has even changed the way in which people spend their leisure time. At the same time, the Internet has presented a new, complex set of challenges that not even the most sophisticated technical experts have been able to adequately solve. The Internet is only in its infancy, and its growth is measured exponentially on a yearly basis.
With the rapid growth of the Internet, network security has become a major concern for companies throughout the world, and although protecting an enterprise's informational assets may be the security administrator's highest priority, protecting the integrity of the enterprise's network is critical to protecting the information it contains. A breach in the integrity of an enterprise's network can be extremely costly in time and effort, and it can open multiple avenues for continued attacks.
When you connect your enterprise network to the Internet, you are connecting your network to thousands of unknown networks, thus giving millions of people the opportunity to access your enterprise's assets. Although such connections open the door to many useful applications and provide great opportunities for information sharing, most enterprises contain some information that should not be shared with outside users on the Internet.
This chapter describes many of the security issues that arise when connecting an enterprise network to the Internet and details the technologies that can be used to minimize the threat of potential intruders to the enterprise and its assets. In this chapter, I'll discuss the Unicast Reverse Path Forwarding (Unicast RPF) feature, which helps to mitigate problems that are caused by forged IP source addresses that the perimeter router receives. I'll also discuss Committed Access Rate (CAR) and the features it provides to rate−limit traffic, thus providing mitigation services for DoS attacks. In addition, I'll discuss TCP SYN− flooding attacks and the features of TCP Intercept, which protect your network from this method of attack. This chapter covers Network Address Translation (NAT) and Port Address Translation (PAT), which were developed to address the depletion of global IP addresses and the security features that each provide. Finally, there is a discussion on logging of events that take place on the perimeter routers.
Defining Networks
This chapter classifies three different types of networks:
∙Trusted
∙Untrusted
∙Unknown
Trusted Networks
Trusted networks are the networks inside your network's security perimeter. These are the networks you are trying to protect. Often, someone in your organization's IT department administers the computers that these networks comprise, and your enterprise's security policy determines their security controls. Usually, trusted networks are within the security perimeter.
85
Untrusted Networks
Untrusted networks are the networks that are known to be outside your security perimeter. They are untrusted because they are outside of your control. You have no control over the administration or security policies for these networks. They are the private, shared networks from which you are trying to protect your network. However, you still need and want to communicate with these networks even though they are untrusted. Untrusted networks are outside the security perimeter and external to the security perimeter.
Unknown Networks
Unknown networks are networks that are neither trusted nor untrusted. They are unknown to the security router because you cannot explicitly tell the router that the network is a trusted or an untrusted network. Unknown networks exist outside your security perimeter.
Cisco Express Forwarding
Cisco Express Forwarding (CEF) is an advanced layer 3 topology− based forwarding mechanism that optimizes network performance and accommodates the traffic characteristics of the Internet for the IP protocol. The topology−based forwarding method builds a forwarding table that exactly matches the topology of the routing table; thus, there is a one−to−one correlation between the entries in the CEF table and the prefixes in the route table. CEF offers improved performance over other router switching mechanisms by avoiding the overhead associated with other cache−driven switching mechanisms. CEF uses a Forwarding Information Base (FIB) to make destination prefix− based switching decisions. The FIB is very similar to the routing table. It maintains an identical copy of the forwarding information contained in the routing table. When topology changes occur in the network, the IP routing table will be updated, and the updated changes are reflected in the FIB. The FIB maintains next−hop address information based on the information in the routing table. Because there is a correlation between FIB entries and the routing table entries, the FIB contains all known routes.
CEF also builds an adjacency table, which maintains layer 2 next−hop addresses for all Forwarding Information Base entries, is kept separate from the CEF table, and can be populated by any protocol that can discover an adjacency. The adjacency table is built by first discovering the adjacency. Each time an adjacency entry is created through a dynamic process, the adjacent node's link−layer header is precomputed and stored in the adjacency table. After a route is resolved, its CEF entry points to a next−hop and corresponding adjacency entry. The entry is subsequently used for encapsulation during CEF switching of packets.
CEF can operate in two different modes: central and distributed. In central mode, the FIB and adjacency tables reside on the route processor and the route processor performs the forwarding.
CEF can act in a distributed mode on routers that support interface line cards, which have their own built−in processors, allowing CEF to take advantage of distributed architecture routers. When CEF is operating in distributed mode, the CEF table is copied down to the router line cards so that switching decisions can be made on the line cards instead of being made by the router processor. Distributed CEF uses a reliable Inter Process Communication mechanism that guarantees a synchronized FIB.
86
Unicast Reverse Path Forwarding
Unicast Reverse Path Forwarding (Unicast RPF) is a feature used to prevent problems caused by packets with forged IP sources addresses passing through a router. Unicast RPF helps to prevent denial−of−ser− vice (DoS) attacks based on source IP address spoofing. Unicast RPF requires the CEF switching mechanism to be enabled globally on the router. The router does not have to have each input interface configured for CEF switching because Unicast RPF searches through the FIB using the packet's source IP address. As long as CEF is running globally on the router, each individual interface can be configured to use other switching modes. The effect of Unicast RPF is that packets with forged source IP addresses will be dropped by the router and will not be forwarded beyond the router's ingress interface.
Note Cisco Express Forwarding must be enabled for Unicast Reverse Path Forwarding to operate.
When Unicast RPF is enabled on an interface, the router will verify that all packets received from that interface have a verifiable source address, which is reachable via that same interface or the best return path to the source of the packet via the ingress interface. The backward lookup ability used by Unicast RPF is available only when CEF is enabled on the router because the lookup relies on the presence of the FIB. If there is a reverse path route in the FIB, the packet is forwarded as normal. If there is no reverse path route via the interface from which the packet was received, the router may interpret that packet as being forged, meaning that the source address was modified. If Unicast RPF does not find a reverse path for the packet, the packet is dropped or forwarded, depending on whether an access control list is specified in the configuration. If an access list is specified in the command, then when a packet fails the Unicast RPF check, the access list is checked to see if the packet should be dropped or forwarded. The decision is made based on the presence of a permit or deny statement within the access list. Unicast RPF events can also be logged by specifying the logging option within the ACL entries used by the Unicast RPF command. The log information can be used to gather information about an attack.
Unicast RPF can be used in any enterprise environment that is single− homed to the Internet service provider (ISP), where there is only one access point out of the network; that is, one upstream connection. This would provide ingress filtering to protect the enterprise from receiving forged packets from the Internet. Networks having one entrance and exit point provide symmetric routing, which means that the interface where a packet enters the network is also the interface the return packet takes to the source of the packet. Unicast RPF is best used at the network perimeter for Internet connections. It will also work in environments in which customers are multihomed to separate ISPs, where the enterprise has multiple access points out of the network. With Unicast RPF configured on the enterprise's perimeter router, all equal−cost return paths are considered valid.
Unicast RPF's advantage, when used for IP address spoof prevention, is that it dynamically adapts to changes in the routing tables, including static routes. Unicast RPF has minimal CPU overhead and has a far lower performance impact as an antispoofing tool compared to the traditional access list configuration approach. Unicast RPF should not be used on interfaces that are internal to the network because these interfaces are likely to have routing asymmetry.
TCP Intercept
Management's major misconception is that the firewall is the first, and in many cases the last, line of defense for security−related issues. In fact the external perimeter router should provide the first line of defense for external security−related issues from the enterprises perspective.
87
Note The enterprise should develop a positive working relationship with its ISP. If this relationship is established, the enterprise can request that the ISP provide many of the first−line defense mechanisms.
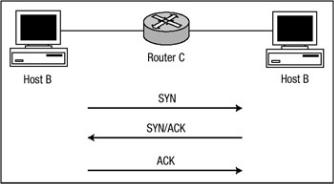
TCP Intercept is a software feature designed to combat the denial−of− service (DoS) attack known as SYN flooding. The TCP protocol uses a three−way handshake to set up an end−to−end connection before data is allowed to flow. This handshake is detailed in Figure 3.1.
Figure 3.1: ICP three−way handshake.
Referring to Figure 3.1, assume that Host B would like to open a connection to Host A. The connection must take place via Router C. Host B sends a SYN packet (a TCP packet with the SYN bit set) to Host A, requesting a connection. Host A then replies with a SYN/ACK packet with both the SYN and ACK bits set, allowing Host B to complete the three−way handshake with a TCP ACK packet. At this point, a connection is established and data is permitted to flow.
A TCP SYN attack occurs when an attacker exploits the buffer space a networked device uses during a TCP session initialization handshake. The attacker sends a large amount of packets with the SYN bit set to the target host, and the target host's in−process queue buffers the request and responds to it with a packet that has the SYN and ACK bits set within it. However, because these packets have an invalid return address, the connections can never be established and remain in a state known as half−open. As these half−open requests begin to build, buffer space is exhausted, which causes the machine to deny service for valid requests because all resources are exhausted waiting for a response. The target host eventually times out while waiting for the proper response.
Many TCP implementations are able to handle only a small number of outstanding connections per port; therefore, the ports become unavailable until the half−open connections time out. Additionally, this attack may also cause the server to exhaust its memory or waste processor cycles in maintaining state information for these connections.
TCP Intercept is designed to prevent a SYN flooding DoS attack by tracking, intercepting, and validating TCP connection requests. Intercept can run in one of two configurable modes: intercept mode and watch mode. In intercept mode, the software actively intercepts each incoming (SYN) request, responds on behalf of the server with a SYN/ ACK, and then waits for an ACK from the client. When that ACK is received, the original SYN is sent to the server and the software performs a three−way handshake with the server. When this is complete, the two connections are joined by the router in a source−destination session.
In watch mode, connection requests are allowed to pass through the router to the server but are watched passively until they become established. If they fail to become established within 30 seconds or a software configurable timeout, the software sends a reset packet to the server to clear the in−process buffer, allowing the server to reallocate the buffer to legitimate requests.
88
