
- •Table of Contents
- •Cisco Network Security Little Black Book
- •Introduction
- •Is this Book for You?
- •How to Use this Book
- •The Little Black Book Philosophy
- •Chapter 1: Securing the Infrastructure
- •In Brief
- •Enterprise Security Problems
- •Types of Threats
- •Enterprise Security Challenges
- •Enterprise Security Policy
- •Securing the Enterprise
- •Immediate Solutions
- •Configuring Console Security
- •Configuring Telnet Security
- •Configuring Enable Mode Security
- •Disabling Password Recovery
- •Configuring Privilege Levels for Users
- •Configuring Password Encryption
- •Configuring Banner Messages
- •Configuring SNMP Security
- •Configuring RIP Authentication
- •Configuring EIGRP Authentication
- •Configuring OSPF Authentication
- •Configuring Route Filters
- •Suppressing Route Advertisements
- •Chapter 2: AAA Security Technologies
- •In Brief
- •Access Control Security
- •Cisco Secure Access Control Server
- •Immediate Solutions
- •Configuring TACACS+ Globally
- •Configuring TACACS+ Individually
- •Configuring RADIUS Globally
- •Configuring RADIUS Individually
- •Configuring Authentication
- •Configuring Authorization
- •Configuring Accounting
- •Installing and Configuring Cisco Secure NT
- •Chapter 3: Perimeter Router Security
- •In Brief
- •Defining Networks
- •Cisco Express Forwarding
- •Unicast Reverse Path Forwarding
- •TCP Intercept
- •Network Address Translation
- •Committed Access Rate
- •Logging
- •Immediate Solutions
- •Configuring Cisco Express Forwarding
- •Configuring Unicast Reverse Path Forwarding
- •Configuring TCP Intercept
- •Configuring Network Address Translation (NAT)
- •Configuring Committed Access Rate (CAR)
- •Configuring Logging
- •Chapter 4: IOS Firewall Feature Set
- •In Brief
- •Port Application Mapping
- •IOS Firewall Intrusion Detection
- •Immediate Solutions
- •Configuring Port Application Mapping
- •Configuring IOS Firewall Intrusion Detection
- •Chapter 5: Cisco Encryption Technology
- •In Brief
- •Cryptography
- •Benefits of Encryption
- •Symmetric and Asymmetric Key Encryption
- •Digital Signature Standard
- •Cisco Encryption Technology Overview
- •Immediate Solutions
- •Configuring Cisco Encryption Technology
- •Chapter 6: Internet Protocol Security
- •In Brief
- •IPSec Packet Types
- •IPSec Modes of Operation
- •Key Management
- •Encryption
- •IPSec Implementations
- •Immediate Solutions
- •Configuring IPSec Using Manual Keys
- •Configuring Tunnel EndPoint Discovery
- •Chapter 7: Additional Access List Features
- •In Brief
- •Wildcard Masks
- •Standard Access Lists
- •Extended Access Lists
- •Reflexive Access Lists
- •Dynamic Access Lists
- •Additional Access List Features
- •Immediate Solutions
- •Configuring Standard IP Access Lists
- •Configuring Extended IP Access Lists
- •Configuring Extended TCP Access Lists
- •Configuring Named Access Lists
- •Configuring Commented Access Lists
- •Configuring Dynamic Access Lists
- •Configuring Reflexive Access Lists
- •Appendix A: IOS Firewall IDS Signature List
- •Appendix B: Securing Ethernet Switches
- •Configuring Management Access
- •Configuring Port Security
- •Configuring Permit Lists
- •Configuring AAA Support
- •List of Figures
- •List of Tables
- •List of Listings
Immediate Solutions
Configuring TACACS+ Globally
The process for configuring a Cisco router to support the TACACS+ protocol is fairly uniform. The basic configuration to enable the TACACS+ protocol always includes the following steps; however, the steps can be accomplished using two different methods. The first method configures TACACS+ globally on the network access server. This method is generally used in environments that use only one TACACS+ server or in environments in which all TACACS+ servers within the network are configured to use the same security values. This configuration method is outlined in the following steps:
1.Use the aaa new−model global configuration command to enable AAA. This command establishes a new AAA configuration. The command must be configured if you plan to support the TACACS+ protocol.
2.Use the tacacs−server host <ip address> command to specify the IP address of one or more TACACS+ servers.
3.Set the global TACACS+ authentication key and encryption key using the tacacs−server key <key> command. The key string configured on the network access server must match the key string configured on the TACACS+ server or all communication between the devices will fail.
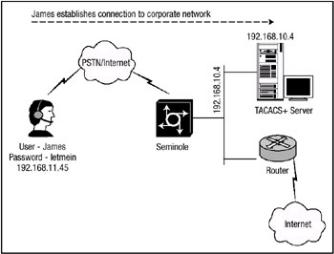
The preceding steps include the basic configuration commands needed to enable TACACS+ globally on the network access server. Figure 2.8 illustrates how to configure the network access server named Seminole to provide TACACS+ services for user James. James is an administrator who must access the network access server Seminole remotely and perform administrative functions. The access server Seminole is configured to communicate with the Cisco Secure ACS server at IP address 192.168.10.4.
Figure 2.8: Single TACACS+ server.
The following configuration commands are needed to configure the router based on the requirements:
Seminole#config t
Enter configuration commands, one per line. End with CNTL/Z.
Seminole(config)#aaa new−model
Seminole(config)#tacacs−server host 192.168.10.4
Seminole(config)#tacacs−server key 1Cisco9
56

In this configuration, the key 1Cisco9 is the encryption key that is shared between router Seminole and the Cisco Secure server at IP address 192.168.10.4. The encryption key should be kept secret for privacy reasons because it is encrypted only after it is sent across the network to the Cisco Secure server but it's not stored in encrypted format on the local device. Issuing the show running−config command allows you see the results of the preceding configuration:
Seminole#show running−config
!
hostname Seminole
!
aaa new−model
tacacs−server host 192.168.10.4 tacacs−server key 1Cisco9
!
Issuing the show running−config command allows you to review the configuration changes that were made to the local device; however, a few more commands are needed to verify that the network access server and TACACS+ server are communicating properly. After you verify that the configuration changes are correct, the next command you should issue is the show tacacs command. The output of this command verifies that the network access server and the TACACS+ server are communicating properly. Issuing the show tacacs command will verify that network access server Seminole in Figure 2.8 is communicating with the TACACS+ server.
Seminole#sh tacacs
Server: 192.168.10.4/49: opens=215 closes=214 aborts=79 errors=4 packets in=1637 packets out=1930 expected replies=0 connection 62524500 state=ESTAB
The output of the show tacacs command first lists the TACACS+ server's IP address and the port number that the router and the TACACS+ server are communicating on; port 49 is the default port number. The port number may be changed in instances in which the TACACS+ server has been configured to communicate on a different port number. The values for opens and closes are the number of times the router opened or closed a session with the TACACS+ server. The most important output that is displayed by the show tacacs command is the state of the connection. In the preceding example, the state equals Established. If, for instance, the router and TACACS+ server could not communicate, the following output listed would be seen:
Server: 192.168.10.4/49: opens=0 closes=0 aborts=0 errors=227 packets in=0 packets out=0 expected replies=0
no connection
Notice the high number of errors. The number is high because there is no connection between the router and the TACACS+ server after a determination has been made that the router and the TACACS+ server are communicating. The command debug tacacs events is needed to make sure the session communication is functioning properly. The debug tacacs events command displays the opening and closing of TCP connections to the TACACS+ server and also displays the bytes written and read during the connection. This output can be seen in Listing 2.1.
Listing 2.1: Debugging TACACS+ events output.
Seminole#debug tacacs events
TACACS+ events debugging is on
Seminole#
57

:TAC+: Opening TCP/IP to 192.168.10.4/49 timeout=5
:TAC+: Opened TCP/IP handle 0x47B76A to 192.168.10.4/49
:TAC+: req=6257CD64 Qd id=3392702625 ver=192 handle=0x0 – : TAC+: (NONE) expire=4
AUTHEN/START/LOGIN/ASCII processed
:TAC+: periodic timer stopped (queue empty)
:TAC+: periodic timer started
:TAC+: 192.168.10.4 req=6257CD64 Qd id=3392702625 ver=192 –
:TAC+: handle=0x0 (NONE) expire=5 AUTHEN/START/LOGIN/ASCII queued
:TAC+: 192.168.10.4 ESTAB id=3392702625 wrote 37 of 37 bytes
:TAC+: 192.168.10.4 req=6257CD64 Qd id=3392702625 ver=192 –
:TAC+: handle=0x0 (NONE)expire=4
AUTHEN/START/LOGIN/ASCII sent
:TAC+: 192.168.10.4 ESTAB read=12 wanted=12 alloc=55 got=12
:TAC+: 192.168.10.4 ESTAB read=28 wanted=28 alloc=55 got=16
:TAC+: 192.168.10.4 received 28 byte reply for 6257CD64 –
:TAC+: id=3392702625
:TAC+: req=6257CD64 Tx id=3392702625 ver=192 handle=0x0 –
:TAC+: (NONE) expire=4
AUTHEN/START/LOGIN/ASCII processed
:TAC+: periodic timer stopped (queue empty)
:TAC+: periodic timer started
:TAC+: 192.168.10.4 req=6252CD78 Qd id=3392702625 ver=192 –
:TAC+: handle=0x0 (NONE)expire=5AUTHEN/CONT queued
:TAC+: 192.168.10.4 ESTAB id=3392702625 wrote 24 of 24 bytes
:TAC+: 192.168.10.4 req=6252CD78 Qd id=3392702625 ver=192 –
:TAC+: handle=0x0 (NONE)expire=4
AUTHEN/CONT sent
:TAC+: 192.168.10.4 ESTAB read=12 wanted=12 alloc=55 got=12
:TAC+: 192.168.10.4 ESTAB read=28 wanted=28 alloc=55 got=16
:TAC+: 192.168.10.4 received 28 byte reply for 6252CD78 –
:TAC+: id=3392702625
:TAC+: req=6252CD78 Tx id=3392702625 ver=192 handle=0x0 –
:TAC+: (NONE) expire=4
AUTHEN/CONT processed
:TAC+: periodic timer stopped (queue empty)
:TAC+: periodic timer started
:TAC+: 192.168.10.4 req=6257CD64 Qd id=3392702625 ver=192 – : TAC+: handle=0x0 (NONE)expire=5
AUTHEN/CONT queued
:TAC+: 192.168.10.4 ESTAB id=3392702625 wrote 27 of 27 bytes
:TAC+: 192.168.10.4 req=6257CD64 Qd id=3392702625 ver=192 – : TAC+: handle=0x0 (NONE)expire=4
AUTHEN/CONT sent
:TAC+: 192.168.10.4 ESTAB read=12 wanted=12 alloc=55 got=12
:TAC+: 192.168.10.4 ESTAB read=18 wanted=18 alloc=55 got=6
:TAC+: 192.168.10.4 received 18 byte reply for 6257CD64 –
:TAC+: id=3392702625
:TAC+: req=6257CD64 Tx id=3392702625 ver=192 –
:TAC+: handle=0x0 (NONE) expire=3
AUTHEN/CONT processed
: TAC+: periodic timer stopped (queue empty)
Configuring TACACS+ Individually
The second method used to enable TACACS+ allows a finer granularity of control in specifying features on a per−security−server basis. This method is generally used in environments that use multiple TACACS+ servers, and each server is configured to use separate values. Use the following steps to enable this method of TACACS+ configuration:
58
1.Use the aaa new−model global configuration command to enable AAA. This command establishes a new AAA configuration. The command must be configured if you plan to support the TACACS+ protocol.
2.Use the following command to specify the IP address of one or more TACACS+ servers:
tacacs−server host hostname <single−connection> <port integer> <timeout <integer> <key string>
The network access server searches for the hosts in the order specified; this feature allows you to set up a list of preferred servers.
The optional single−connection argument specifies that the network access server should maintain a single connection to the TACACS+ server as opposed to having the network access server open and close a TCP connection to the daemon process on the TACACS+ server each time it needs to communicate with the server. This allows the daemon process on the TACACS+ server to handle a higher number of TACACS+ operations. The default TCP port the network access server uses to communicate with the TACACS+ server may be changed using the portinteger argument. If this argument is not specified, the default TCP port 49 is used. The timeout integer argument allows the network access server to specify the period of time it will wait for a response from the TACACS+ server daemon before it times out and declares an error; the default is set to 5 seconds. The key string argument allows for specification of an encryption key for encrypting and decrypting all traffic between the network access server and the TACACS+ daemon. The key string configured on the network access server must match the key string configured on the TACACS+ server or all communication between the devices will fail.
As mentioned, there are two different methods used to enable the TACACS+ process on a Cisco router. The Cisco IOS allows you to configure many values at a global level, which affects all other related values configured on the router. The method detailed in this section allows you to enhance security on your network by uniquely configuring individual TACACS+ connections for multiple servers and applying separate values for each server. Use the preceding configuration in instances in which your network has many independent TACACS+ servers and each server has different values configured.
Note Some of the parameters of the tacacs−server host command override other globally configured TACACS+ commands.
Figure 2.9 shows another TACACS+ server added to the local network. The new TACACS+ server has an IP address of 192.168.10.5. This server is configured to use a different key value and timeout value than the server located at IP address 192.168.10.4:
config t
aaa new−model
tacacs−server host 192.168.10.4 single−connection key 1Cisco9 tacacs−server host 192.168.10.5 single−connection timeout 15 –
key 2Systems8
59
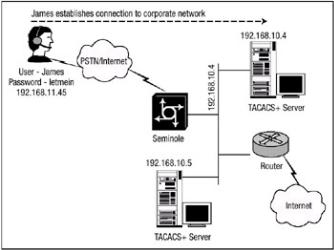
Figure 2.9: Multiple TACACS+ servers.
This configuration names two TACACS+ servers: 192.168.10.4 and 192.168.10.5. TACACS+ server 192.168.10.4 is configured as it was in the global configuration; only the single−connection option has been added to the configuration. However, the 192.168.10.5 server has been added to the network and the values that the network access server needs to have configured are different for this server. Notice the timeout value—the network access waits for a response from the security server according to the timeout value, which has been changed from the default value of 5 seconds to a value of 15 seconds. The encryption key and authentication that is used to communicate with this server has been changed as well. Issuing the show running−config command allows you to view the results of the configuration:
Seminole#show running−config
!
hostname Seminole
!
aaa new−model
tacacs−server host 192.168.10.4 single−connection key 1Cisco9 tacacs−server host 192.168.10.5 single−connection timeout –
15 key 2Systems8
!
After you verify that the configuration changes are correct, the next command you should issue is the show tacacs command. The output of this command verifies that the network access server and the TACACS+ server are communicating properly. Here is the output of the sh tacacs command:
Seminole#sh tacacs
Server: 192.168.10.4/49: opens=127 closes=126 aborts=24 errors=1 packets in=1083 packets out=1233 expected replies=0 connection 623F8098 state=ESTAB
Server: 192.168.10.5/49: opens=1 closes=0 aborts=0 errors=0 packets in=14 packets out=14 expected replies=0 connection 623FFC28 state=CLOSEWAIT
60
