
- •Table of Contents
- •Cisco Network Security Little Black Book
- •Introduction
- •Is this Book for You?
- •How to Use this Book
- •The Little Black Book Philosophy
- •Chapter 1: Securing the Infrastructure
- •In Brief
- •Enterprise Security Problems
- •Types of Threats
- •Enterprise Security Challenges
- •Enterprise Security Policy
- •Securing the Enterprise
- •Immediate Solutions
- •Configuring Console Security
- •Configuring Telnet Security
- •Configuring Enable Mode Security
- •Disabling Password Recovery
- •Configuring Privilege Levels for Users
- •Configuring Password Encryption
- •Configuring Banner Messages
- •Configuring SNMP Security
- •Configuring RIP Authentication
- •Configuring EIGRP Authentication
- •Configuring OSPF Authentication
- •Configuring Route Filters
- •Suppressing Route Advertisements
- •Chapter 2: AAA Security Technologies
- •In Brief
- •Access Control Security
- •Cisco Secure Access Control Server
- •Immediate Solutions
- •Configuring TACACS+ Globally
- •Configuring TACACS+ Individually
- •Configuring RADIUS Globally
- •Configuring RADIUS Individually
- •Configuring Authentication
- •Configuring Authorization
- •Configuring Accounting
- •Installing and Configuring Cisco Secure NT
- •Chapter 3: Perimeter Router Security
- •In Brief
- •Defining Networks
- •Cisco Express Forwarding
- •Unicast Reverse Path Forwarding
- •TCP Intercept
- •Network Address Translation
- •Committed Access Rate
- •Logging
- •Immediate Solutions
- •Configuring Cisco Express Forwarding
- •Configuring Unicast Reverse Path Forwarding
- •Configuring TCP Intercept
- •Configuring Network Address Translation (NAT)
- •Configuring Committed Access Rate (CAR)
- •Configuring Logging
- •Chapter 4: IOS Firewall Feature Set
- •In Brief
- •Port Application Mapping
- •IOS Firewall Intrusion Detection
- •Immediate Solutions
- •Configuring Port Application Mapping
- •Configuring IOS Firewall Intrusion Detection
- •Chapter 5: Cisco Encryption Technology
- •In Brief
- •Cryptography
- •Benefits of Encryption
- •Symmetric and Asymmetric Key Encryption
- •Digital Signature Standard
- •Cisco Encryption Technology Overview
- •Immediate Solutions
- •Configuring Cisco Encryption Technology
- •Chapter 6: Internet Protocol Security
- •In Brief
- •IPSec Packet Types
- •IPSec Modes of Operation
- •Key Management
- •Encryption
- •IPSec Implementations
- •Immediate Solutions
- •Configuring IPSec Using Manual Keys
- •Configuring Tunnel EndPoint Discovery
- •Chapter 7: Additional Access List Features
- •In Brief
- •Wildcard Masks
- •Standard Access Lists
- •Extended Access Lists
- •Reflexive Access Lists
- •Dynamic Access Lists
- •Additional Access List Features
- •Immediate Solutions
- •Configuring Standard IP Access Lists
- •Configuring Extended IP Access Lists
- •Configuring Extended TCP Access Lists
- •Configuring Named Access Lists
- •Configuring Commented Access Lists
- •Configuring Dynamic Access Lists
- •Configuring Reflexive Access Lists
- •Appendix A: IOS Firewall IDS Signature List
- •Appendix B: Securing Ethernet Switches
- •Configuring Management Access
- •Configuring Port Security
- •Configuring Permit Lists
- •Configuring AAA Support
- •List of Figures
- •List of Tables
- •List of Listings

The default for the 60−second low value is the same as the max−in− complete low value, 900. The default value for the 60−second high value is the same as the max−incomplete high value, 1100.
Router B should be configured to trigger TCP Intercept aggressive mode sooner than normal, and the drop mode should be configured such that it will randomly drop partial connections regardless of the age time for each connection request. This can be accomplished using the configuration in Listing 3.9.
Listing 3.9: Example Intercept aggressive mode configuration.
#config |
t |
|
#ip tcp |
intercept drop−mode random |
|
#ip tcp |
intercept max−incomplete |
low 400 |
#ip tcp |
intercept max−incomplete |
high 600 |
#ip tcp |
intercept one−minute low |
400 |
#ip tcp |
intercept one−minute high 600 |
|
#end |
|
|
|
|
|
The drop mode for router B has been changed from the default of dropping the oldest partial connection to dropping any connection regardless of the age value. The configuration also lowered the values that TCP Intercept uses to trigger aggressive mode behavior. The final TCP configuration of Router B can be seen in Listing 3.10.
Listing 3.10: Final TCP Intercept configuration.
#ip tcp intercept list 100 #ip tcp intercept mode watch
#ip tcp intercept watch−timeout 16
#ip tcp intercept connection−timeout 21600 #ip tcp intercept drop−mode random
#ip tcp intercept max−incomplete low 400 #ip tcp intercept max−incomplete high 600 #ip tcp intercept one−minute low 400
#ip tcp intercept one−minute high 600
#access−list 100 permit tcp any host 192.168.20.20 #access−list 100 permit tcp any host 192.168.20.21
Configuring Network Address Translation (NAT)
Perimeter routers help enterprises to solve IP address space depletion problems; they can also hide internal IP addresses from outside networks. To provide these functions as well as many others, perimeter routers use Network Address Translation (NAT) and Port Address Translation (PAT). The following sections provide guidelines for configuring the various types of NAT and PAT on Cisco routers.
Configuring Static NAT Translations
Static Network Address Translation (NAT) allows security administrators to configure their routers such that individual inside local IP addresses can be translated to individual global inside IP addresses.
103
Static NAT is particularly useful when hosts on the outside network need the capability to access a host or hosts on the inside network. NAT compares the packets that are destined to a global outside address against the inside local address that is configured on the NAT translation entries. If the source of the packet has a valid entry in the translation table, the packet source address is rewritten with the matching inside global IP address.
NAT maintains a table of translated IP addresses. To the outside network, the inside network appears to have a certain range of IP addresses. These addresses are mapped to the actual IP addresses that are used inside the enterprise. Static NAT is referred to as a simple translation entry.
Use the following steps to configure static NAT translation for inside IP addresses:
1.Use the following command to establish a static translation between an inside local address and an inside global address:
ip nat inside source static <inside local address> <inside global address>
The inside local address is the address that is to be translated, and the inside global address is the address that the inside local address is to be translated to.
2. Use this command to move into interface configuration mode:
interface <interface type> <interface number>
3.Use the ip nat inside interface configuration command to apply NAT to the interface that is connected to the networks with the local addresses.
4.Use this command to move into interface configuration mode:
interface <interface type> <interface number>
5.Use the ip nat outside interface configuration command to apply NAT to the interface that is connected to the networks with the inside global addresses.
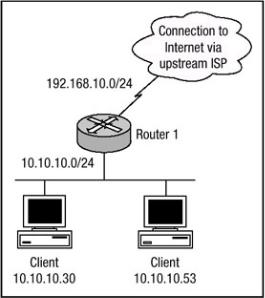
The preceding steps included the minimum commands needed to configure static NAT translation. Figure 3.5 displays a network that must use NAT to communicate with outside networks.
104

Figure 3.5: Static NAT.
The networks that are behind Router 1 are all allocated from RFC 1918 nonroutable address space. The Web server has an inside local address of 10.10.10.30 and must be accessible to outside networks via the address 192.168.10.30. The other server is an email server that has an IP address of 10.10.10.53 and must be accessible to outside networks via the address 192.168.10.53. The commands used to configure static NAT translations on Router 1 are shown in Listing 3.11.
Listing 3.11: Static NAT configuration.
#config t
#ip nat inside source static 10.10.10.30 192.168.10.30 #ip nat inside source static 10.10.10.53 192.168.10.53
!
#interface FastEthernet0/0
#ip address 10.10.10.2 255.255.255.0 #ip nat inside
!
#interface Serial1/0
#ip address 192.168.10.2 255.255.255.0 #ip nat outside
In Listing 3.11, Router 1 has been configured with two static translation entries.
Note Although the 192.168.0.0 range is allocated from RFC 1918 private address space, it is being used in these examples as a registered IP address block.
The Fast Ethernet interface is designated as the inside interface with the ip nat inside command, and interface Serial1/0 is designated as the outside interface with the ip nat outside command. To verify that the configuration is correct, issue the sh ip nat translation command. The following output lists the information related to the simple translation entry:
Router−1#sh ip nat trans
Pro Inside global Inside local Outside local Outside global
− |
192.168.10.30 |
10.10.10.30 |
− |
− |
− |
192.168.10.53 |
10.10.10.53 |
− |
− |
The show ip nat translations command lists the protocol field, the inside global address, the inside local address, the outside local address, and the outside global address. The outside local and outside global fields will be discussed later in this chapter when you learn more about extended entries. Another command that can be used to monitor and verify the operation of NAT is the show ip nat translations verbose command. Issuing this command on Router 1 displays the following output:
Router−1#sh ip nat |
trans ver |
|
|
Pro Inside global |
Inside local |
Outside local |
Outside global |
− 192.168.10.30 10.10.10.30 |
− |
− |
|
create 00:49:01, use 00:00:01, |
|
||
flags: static, |
use_count: 74 |
|
|
− 192.168.10.53 |
10.10.10.53 |
− |
− |
create 00:49:12, use 00:00:7, flags: static, use_count: 50
Router−1#
105
The verbose argument of the show ip nat translations command produces more detailed information regarding the status of the NAT translations. As you can see in the preceding output, the fields that are listed with the verbose argument are the same as the fields that were listed without it. The output when the verbose argument is used includes a create field that lists how long ago the entry was created. The use field lists how long ago the translation entry was last used. The times in the create and use fields are listed in the hours:minutes:seconds format. The flag field indicates the type of translation entry, and there are a total of five possible flags:
∙static—States that the entry was created by a static translation entry
∙extended—States that the entry was created by an extended translation entry
∙outside—States that the entry was created by an outside translation entry
∙destination—States that the entry was created by an outside translation entry
∙time out—States that the entry will no longer be used and is being torn down
The use count field lists the total number of times the entry has been used. One last command used to monitor and verify the operation of NAT is the show ip nat statistics command. The following output is displayed when the show ip nat statistics command is issued on Router 1:
Router−1#sh ip nat stat
Total active translations: 2 (2 static, 0 dynamic; 0 extended)
Outside interfaces:
Serial1/0
Inside interfaces:
FastEthernet0/0
Hits: 124 Misses: 0
Expired translations: 0
Dynamic mappings:
Router−1#
The total active translations field lists the total number of active NAT translations on the router. This field is populated in realtime; each time a translation entry is created, the field is incremented accordingly, and each time a translation entry is dropped or times out, the field is decremented accordingly. The outside interface is then listed and is determined based on the ip nat outside command. The inside interface is listed next and is determined based on the ip nat inside command. The hits field lists the total number of times NAT does a translation table lookup and finds a match. The misses field list the total number of times NAT does a translation table lookup, fails to find an entry, and attempts to create one. The expired translations field lists the total number of entries that have expired. The dynamic mapping field lists information that pertains to a NAT entry that was created by a dynamic translation entry. This field will be discussed later in this chapter.
Configuring Static NAT Translations Using Route Maps
Static NAT supports the use of route maps, which give enterprises the opportunity to take advantage of multihoming without having to lose the features that static NAT provides. To configure static NAT with route maps, use the following steps:
1. Use this command to enable static NAT with route maps configured on the inside interface:
ip nat inside source list {acl−number|acl−name} pool pool−name
[overload]|static local−ip global−ip route−map map−name}
106

2.Use the following command to define an extended access list and the parameters of the access list:
access−list <acl−number> {deny|permit} <protocol> − <source> <source−wildcard> <destination> <destination− wildcard>
The access list should specify which traffic arriving at the inside interface and destined to the outside interface is eligible to create a translation entry.
3. Use this command to move into interface configuration mode:
interface <interface type> <interface number>
4.Use the ip nat inside interface configuration command to apply NAT to the interface that is connected to the networks with the local addresses.
5.Use the following command to move into interface configuration mode:
interface <interface type> <interface number>
6.Use the ip nat outside interface configuration command to apply NAT to the interface that is connected to the networks with the inside global addresses.
7.Use this command to enter route map configuration mode and define the parameters of the route map:
route−map <name> {permit|deny} <sequence number>}
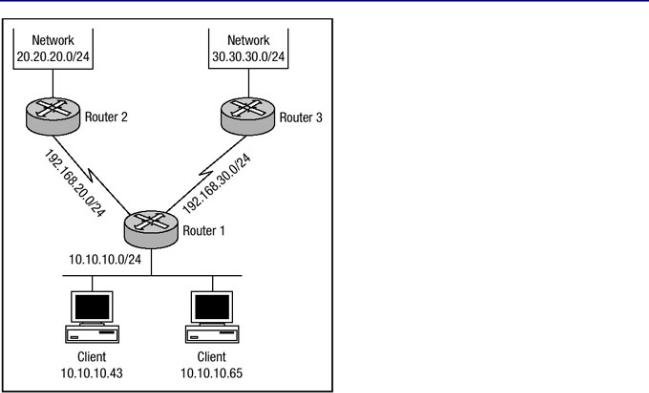
Figure 3.6 shows a network in which the use of static NAT and route maps would be beneficial. Router 1 has a connection to Router 2 and another connection to Router 3. The hosts behind Router 1 have varying requirements: When a connection is established to hosts within Network 2 behind Router 2, their IP address should appear to be sourced from one subnet. Yet, when connections are established to hosts within Network 3 behind Router 3, their IP address should appear to be sourced from a different subnet. To meet the requirements, the configuration in Listing 3.12 can be used.
Listing 3.12: Router 1 static NAT with route map configuration.
hostname Router−1
!
interface Serial2/0
ip address 192.168.20.1 255.255.255.0 ip nat outside
!
interface Serial3/0
ip address 192.168.30.1 255.255.255.0 ip nat outside
!
interface Ethernet1/0
ip address 10.10.10.1 255.255.255.0 ip nat inside
duplex full speed 100
!
ip route 20.20.20.0 255.255.255.0 192.168.20.2 ip route 30.30.30.0 255.255.255.0 192.168.30.2
!
ip nat inside source static 10.10.10.43 192.168.20.2 − route−map network2
107
!
ip nat inside source static 10.10.10.43 192.168.30.2 − route−map network3
!
ip nat inside source static 10.10.10.65 192.168.20.3 − route−map network2
!
ip nat inside source static 10.10.10.65 192.168.30.3 − route−map network3
!
access−list 101 permit ip 10.10.10.0 0.0.0.255 − 20.20.20.0 0.0.0.255
!
access−list 102 permit ip 10.10.10.0 0.0.0.255 − 30.30.30.0 0.0.0.255
!
route−map network2 permit 10 match ip address 101
set ip next−hop 192.168.20.2
!
route−map network3 permit 10 match ip address 102
set ip next−hop 192.168.30.2
Figure 3.6: Example static NAT and route map network.
Note Because of the format limitations of this book, some lines of code listed above have been broken with a hyphen.
The configurations in Listing 3.11 and Listing 3.12 are very similar; in Listing 3.12 the route−map option is at the end of the ip nat inside source command. The inside and outside NAT interfaces are defined for Router 1. Each of the ip nat inside source static commands creates a static NAT translation entry and defines a route map that should be applied for each of the entries. The route map is configured to match addresses sourced from an inside subnet and destined for an outside subnet. The next hop to send the packet to is then defined.
108
Configuring Dynamic NAT Translations
Dynamic NAT translation of addresses is one of many types of NAT configurations. The difference in the configuration of dynamic NAT translations and static NAT translations is minimal. However, the manner in which the translation table is populated is vastly different. With static NAT, you need to manually enter the pairs of translation addresses. Using dynamic NAT, the table is populated dynamically after a packet is received on the inside interface and the packet matches parameters defined within an access list. Packets that are to be translated by NAT should match a permit statement within the access list. A deny statement in the access list tells NAT not to perform translation on the packet.
To perform translation on packets moving between interfaces labeled as "inside" and interfaces labeled as "outside," NAT must be told what address to change the packet to. With static NAT, the address is manually entered so NAT doesn't have to decide which address to allocate to a certain flow. With dynamic NAT, a pool of inside global addresses is configured, and NAT chooses the next available address to allocate to every new flow. NAT chooses addresses from the configured pool, starting with the lowest IP address first and then continuing to translate each new flow with the next available address. After all of the addresses in the pool are in use and allocated, NAT translates a new flow until a translation times out or is cleared and released back into the pool. To configure basic dynamic NAT, use the following steps:
1.Use the following global configuration command to define a pool of inside global addresses to be allocated as needed:
ip nat pool <name> <start−ip address> <end−ip address> − {netmask netmask|prefix−length prefix−length}
The start IP address is the address that NAT will begin with when creating a dynamic translation entry. The end IP address is the last IP address that NAT will be able to use when creating a dynamic translation entry.
2. Use this command to define an extended access list and its parameters:
access−list <access−list−number> {deny|permit} <protocol> − <source> <source−wildcard> <destination> <destination− wildcard>
The access list should specify which traffic arriving at the inside interface and destined to the outside interface is eligible to create a translation entry.
3.Use the following command to establish an association between the local inside addresses and the pool of global addresses:
ip nat inside source list <access−list−number> pool <name>
4. Use the following command to move into interface configuration mode:
interface <interface type> <interface number>
5.Use the ip nat inside interface configuration command to apply NAT to the interface that is connected to the networks with the local addresses.
6.Use this command to move into interface configuration mode:
interface <interface type> <interface number>
109
7.Use the ip nat outside interface configuration command to apply NAT to the interface that is connected to the networks with the inside global addresses.
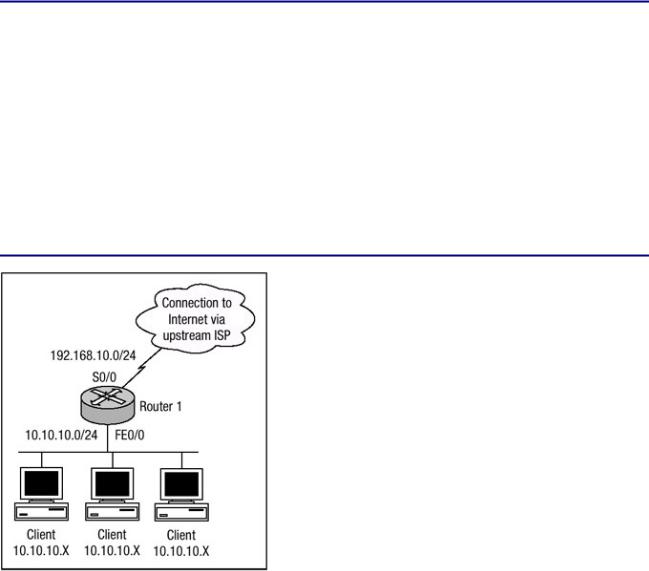
The preceding steps contain all the commands needed to configure dynamic NAT translation. Figure 3.7 displays a network that must use NAT to communicate with outside networks. The networks that are behind Router 1 are all allocated from RFC 1918 nonroutable address space. The clients located behind Router 1 have inside local addresses allocated from the 10.10.10.0 subnet. The configuration of Router 1 is shown in Listing 3.13.
Listing 3.13: Dynamic NAT configuration.
ip subnet−zero
!
ip nat pool INTERNET 192.168.10.129 192.168.10.254 − netmask 255.255.255.128
!
ip nat inside source list 1 pool INTERNET
!
interface Serial0/0
ip address 192.168.10.1 255.255.255.128 ip nat outside
!
int FastEthernet0/0
ip address 10.10.10.1 255.255.255.0 ip nat inside
!
access−list 1 permit 10.10.10.0 0.0.0.255
Figure 3.7: Dynamic NAT network example.
The configuration in Listing 3.13 defines an inside global pool of addresses named INTERNET with 126 inside global addresses. The access list command is used to tell NAT which inside local addresses are eligible for translation. The ip nat inside source command is used to bound the access list and the pool of addresses together. Interface serial0/0 is defined as the outside interface, and interface fastethernet0/0 is defined as the inside interface.
When hosts on the 10.10.10.0 network need to connect to networks outside of their local network, NAT will perform a translation table lookup and determine if a translation entry already exists. If a
110

translation is present in the translation table, the router performs no other function. If no translation exists in the translation table, NAT performs a translation and allocates the next lowest available IP address for the packet. To view the translation table of Router 1, use the sh ip nat translations command. Listing 3.14 displays the output when the command is issued on Router 1.
Listing 3.14: Display of NAT translations.
Router−1#show ip nat translations |
|
|
||
Pro |
Inside global |
Inside local |
|
Outside local Outside global |
− |
192.168.10.129 |
10.10.10.1 |
− |
− |
− |
192.168.10.130 |
10.10.10.35 |
− |
− |
− |
192.168.10.131 |
10.10.10.47 |
− |
− |
− |
192.168.10.132 |
10.10.10.68 |
− |
− |
... |
|
|
|
|
Router−1#
The output from Listing 3.14 confirms that NAT is allocating IP addresses from the inside global pool of addresses and translating the inside local address to an inside global address. After an entry is created, all connections from hosts on the inside network to hosts on the outside network should be successful.
Another command used to monitor and verify the operation of NAT is the show ip nat statistics command. This command was used earlier to monitor and verify the operation of static NAT; however, when it was used with static NAT, no information regarding the dynamic mappings was listed. When the command is issued on Router 1, information specific to the dynamic mappings is included. Listing 3.15 displays the output of issuing the command on Router 1 with dynamic mapping.
Listing 3.15: Display of NAT statistics.
Router−1#sh ip nat stat
Total active translations: 11 (0 static, 11 dynamic; 0 extended) Outside interfaces:
Serial0/0 Inside interfaces:
FastEthernet0/0
Hits: 63 Misses: 5 Expired translations: 0 Dynamic mappings:
−− Inside Source
access−list 1 pool INTERNET refcount 11 pool INTERNET: netmask 255.255.255.128 start 192.168.10.129 end 192.168.10.254
type generic, total addresses 126, allocated 11 (8%), misses 0 Router−1#
Configuring Dynamic NAT Translations Using Route Maps
As discussed earlier, NAT supports the use of static translations using route maps; it also supports the use of dynamic translation using route maps. To configure dynamic NAT translations using route maps, use the following steps:
1.Use the following command to establish an association between the configured route map and the pool of global addresses:
111

ip nat inside source route−map <route map name> pool <pool − name>
2. Use this command to define a pool of addresses to be allocated for translation as needed:
ip nat pool <pool name> <start−ip address> <end−ip address> − {netmask netmask | prefix−length prefix−length}
The start IP address is the address that NAT will begin with when creating a dynamic translation entry. The end IP address is the last IP address that NAT will be able to use when creating a dynamic translation entry.
3. Use the following command to define an extended access list and its parameters:
access−list <access−list−number> {deny|permit} <protocol> − <source> <source−wildcard> <destination> <destination − wildcard>
The access list should specify which traffic arriving at the inside interface and destined to the outside interface is eligible to create a translation entry.
4.Use this command to enter route map configuration mode and define the parameters of the route map:
route−map <name> {permit|deny} <sequence number>}
5. Use the following command to move into interface configuration mode:
interface <interface type> <interface number>
6.Use the ip nat inside interface configuration command to apply NAT to the interface that is connected to the networks with the local addresses.
7.Use the following command to move into interface configuration mode:
interface <interface type> <interface number>
8.Use the ip nat outside interface configuration command to apply NAT to the interface that is connected to the networks with the inside global addresses.
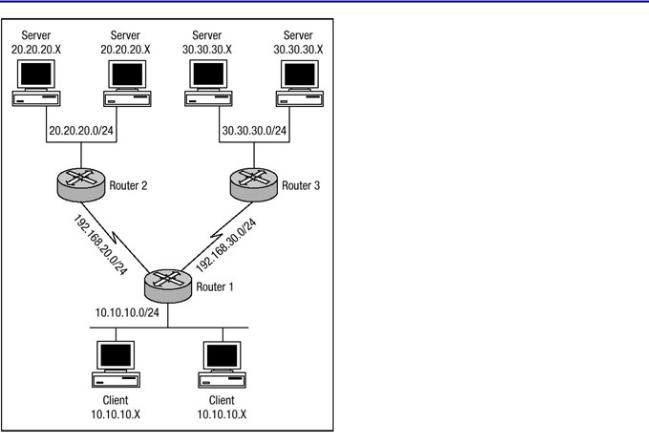
Referring to Figure 3.8, you can see that Router 1 is multihomed to two different routers. It has a connection to Router 2 and another to Router 3. When the hosts behind Router 1 in network 10.10.10.0 establish a connection to hosts within Network 2 behind Router 2 with IP addresses of 20.20.20.0, their IP addresses should appear to be sourced from one subnet; yet, when establishing connections to hosts within Network 3 behind Router 3 with a network of 30.30.30.0, their IP addresses should appear to be sourced from a different subnet. To meet the requirements using dynamic NAT and route maps, the configuration in Listing 3.16 can be used.
Listing 3.16: Router 1 Dynamic NAT with route map configuration.
hostname Router−1
!
interface Serial2/0
ip addres 192.168.20.1.255.255.255.0 ip nat outside
!
interface Serial3/0
ip addres 192.168.30.1.255.255.255.0 ip nat outside
112
!
interface Serial1/0
ip addres 10.10.10.1.255.255.255.0 ip nat inside
duplex full speed 100
!
ip route 20.20.20.0.255.255.255.0 192.168.20.2 ip route 30.30.30.0 255.255.255.0 192.168.30.2
!
ip nat pool network−20 192.168.20.20 192.168.20.254 − prefix−length 24
!
ip nat pool network−30 192.168.30.20 192.168.30.254 − prefix−length 24
!
ip nat inside source route−map network2 pool network−20 ip nat inside source route−map network3 pool network−30
!
access−list 101 permit ip 10.10.10.0 0.0.0.255 − 20.20.20.0 0.0.0.255
!
access−list 102 permit ip 10.10.10.0 0.0.0.255 − 30.30.30.0 0.0.0.255
!
route−map network2 permit 10 match ip address 101
set ip next−hop 192.168.20.2
!
route−map network3 permit 10 match ip address 102
set ip next−hop 192.168.30.2
113
Figure 3.8: Router 1 Dynamic NAT with route map.
Note Because of the format limitations of this book, some lines of code in Listing 3.16 have been broken with a hyphen.
If you compare the configurations in Listing 3.12 and Listing 3.16, you'll notice that there are slight differences between the two. The configuration in Listing 3.16 does not include any static mappings and the ip nat pool command has been added. When a route map is used by NAT to match the inside traffic to be translated, NAT will create a fully extended translation entry that can be viewed using the show ip nat translations command. The translation entry created by NAT will contain both the inside and outside local and global address entries and also contain any TCP or UDP port information. Issuing the show ip nat translations command on Router 1 displays the following output:
Router−1#show ip nat translations
...
Pro |
Inside global |
Inside local |
... |
TCP |
192.168.20.20:1134 |
10.10.10.43:1134 ... |
|
TCP |
192.168.30.20:1135 |
10.10.10.43:1135 ... |
|
TCP |
192.168.20.21:1026 |
10.10.10.65:1026 ... |
|
TCP |
192.168.30.21:1027 |
10.10.10.65:1027 ... |
|
|
|
... Outside local Outside global |
|
|
|
... 20.20.20.20:21 20.20.20.20:21 |
|
|
|
... 30.30.30.30:23 30.30.30.30:23 |
|
|
|
... 20.20.20.21:23 20.20.20.21:23 |
|
|
|
... 30.30.30.31:21 30.30.30.31:21 |
|
Note Because of the format limitations of this book, lines of code have been broken with ellipsis points.
Configuring Port Address Translation (PAT)
Because of the rapid depletion of public IP version 4 address space and the limited number of public IP addresses that can be used on the Internet, enterprises may not be able to purchase blocks of public addresses that contain the number of private addresses being used on the inside network to perform Network Address Translation. A solution to working with the limited number of addresses being allocated to enterprises is the use Port Address Translation (PAT). PAT allows multiple hosts on the inside local network to access hosts located on outside networks using a single inside global address. PAT utilizes a NAT feature known as overloading. When overloading is configured on the router, the router maintains enough information from the higher−layer protocols like TCP or UDP port numbers, which allows the router to translate the global address back to the originating local address. More than one inside local address can be mapped to an inside global address, and when multiple inside local addresses map to one global address, the TCP or UDP port numbers of each inside host distinguish between the local addresses.
To configure PAT, perform the following steps (these steps are similar to the steps for configuring dynamic NAT translations):
1.Use the following global configuration command to define a pool of inside global addresses to be allocated as needed:
ip nat pool <name> <start−ip address> <end−ip address> − {netmask netmask|prefix−length prefix−length}
114

The start IP address is the address that NAT will begin with when creating a dynamic translation entry. The end IP address is the same IP address used for the start IP address.
2. Use this command to define an extended access list and its parameters:
access−list <access−list−number> {deny|permit}<protocol> − <source> <source−wildcard> <destination> <destination− wildcard>
The access list should specify which traffic arriving at the inside interface and destined to the outside interface is eligible to create a translation entry.
3.Use this command to establish an association between the local inside addresses and the pool of global addresses (notice the use of the overload keyword):
ip nat inside source list <access−list−number> pool <name> − overload
4. Use the following command to move into interface configuration mode:
interface <interface type> <interface number>
5.Use the ip nat inside interface configuration command to apply NAT to the interface that is connected to the networks with the local addresses.
6.Use this command to move into interface configuration mode:
interface <interface type> <interface number>
7.Use the ip nat outside interface configuration command to apply NAT to the interface that is connected to the networks with the inside global addresses.
Using Figure 3.7 as a reference, you can see that Router 1 must now be configured to support PAT. The figure displays a network that must use PAT to communicate with outside networks. The networks that are behind Router 1 are all allocated from RFC 1918 nonroutable address space. The clients located behind Router 1 have inside local addresses allocated from the 10.10.10.0 subnet; however, the enterprise has been allocated only one public IP address. Listing 3.17 shows the configuration needed to configure Router 1 for PAT.
Listing 3.17: PAT configuration example.
ip subnet−zero
!
ip nat pool INTERNET 192.168.10.254 192.168.10.254 − netmask 255.255.255.128
!
ip nat inside source list 1 pool INTERNET overload
!
interface Serial0/0
ip address 192.168.10.1 255.255.255.128 ip nat outside
!
int FastEthernet0/0
ip address 10.10.10.1 255.255.255.0 ip nat inside
!
access−list 1 permit 10.10.10.0 0.0.0.255
115
