
- •Table of Contents
- •Cisco Network Security Little Black Book
- •Introduction
- •Is this Book for You?
- •How to Use this Book
- •The Little Black Book Philosophy
- •Chapter 1: Securing the Infrastructure
- •In Brief
- •Enterprise Security Problems
- •Types of Threats
- •Enterprise Security Challenges
- •Enterprise Security Policy
- •Securing the Enterprise
- •Immediate Solutions
- •Configuring Console Security
- •Configuring Telnet Security
- •Configuring Enable Mode Security
- •Disabling Password Recovery
- •Configuring Privilege Levels for Users
- •Configuring Password Encryption
- •Configuring Banner Messages
- •Configuring SNMP Security
- •Configuring RIP Authentication
- •Configuring EIGRP Authentication
- •Configuring OSPF Authentication
- •Configuring Route Filters
- •Suppressing Route Advertisements
- •Chapter 2: AAA Security Technologies
- •In Brief
- •Access Control Security
- •Cisco Secure Access Control Server
- •Immediate Solutions
- •Configuring TACACS+ Globally
- •Configuring TACACS+ Individually
- •Configuring RADIUS Globally
- •Configuring RADIUS Individually
- •Configuring Authentication
- •Configuring Authorization
- •Configuring Accounting
- •Installing and Configuring Cisco Secure NT
- •Chapter 3: Perimeter Router Security
- •In Brief
- •Defining Networks
- •Cisco Express Forwarding
- •Unicast Reverse Path Forwarding
- •TCP Intercept
- •Network Address Translation
- •Committed Access Rate
- •Logging
- •Immediate Solutions
- •Configuring Cisco Express Forwarding
- •Configuring Unicast Reverse Path Forwarding
- •Configuring TCP Intercept
- •Configuring Network Address Translation (NAT)
- •Configuring Committed Access Rate (CAR)
- •Configuring Logging
- •Chapter 4: IOS Firewall Feature Set
- •In Brief
- •Port Application Mapping
- •IOS Firewall Intrusion Detection
- •Immediate Solutions
- •Configuring Port Application Mapping
- •Configuring IOS Firewall Intrusion Detection
- •Chapter 5: Cisco Encryption Technology
- •In Brief
- •Cryptography
- •Benefits of Encryption
- •Symmetric and Asymmetric Key Encryption
- •Digital Signature Standard
- •Cisco Encryption Technology Overview
- •Immediate Solutions
- •Configuring Cisco Encryption Technology
- •Chapter 6: Internet Protocol Security
- •In Brief
- •IPSec Packet Types
- •IPSec Modes of Operation
- •Key Management
- •Encryption
- •IPSec Implementations
- •Immediate Solutions
- •Configuring IPSec Using Manual Keys
- •Configuring Tunnel EndPoint Discovery
- •Chapter 7: Additional Access List Features
- •In Brief
- •Wildcard Masks
- •Standard Access Lists
- •Extended Access Lists
- •Reflexive Access Lists
- •Dynamic Access Lists
- •Additional Access List Features
- •Immediate Solutions
- •Configuring Standard IP Access Lists
- •Configuring Extended IP Access Lists
- •Configuring Extended TCP Access Lists
- •Configuring Named Access Lists
- •Configuring Commented Access Lists
- •Configuring Dynamic Access Lists
- •Configuring Reflexive Access Lists
- •Appendix A: IOS Firewall IDS Signature List
- •Appendix B: Securing Ethernet Switches
- •Configuring Management Access
- •Configuring Port Security
- •Configuring Permit Lists
- •Configuring AAA Support
- •List of Figures
- •List of Tables
- •List of Listings
Chapter 4: IOS Firewall Feature Set
In Brief
The IOS Firewall feature set available for Cisco routers is an add−on component to the Cisco IOS that provides routers with many of the features available to the PIX firewall, thus extending to routers functionality similar to the functionality a separate firewall device provides. When a Cisco router is configured with the Cisco IOS Firewall feature set, it is transformed into an effective, robust featured firewall. The IOS Firewall feature set software has been designed with security services that include access controls, strong authentication, and encryption services, and it maintains all fundamental routing features. It is a value−added option for Cisco IOS software that enforces security policies while maintaining vital traffic flow requirements within the enterprise. The Firewall feature set is currently available for the Cisco 1600, 1720, 2500, 2600, 3600, and 7200 series router platforms.
Some of the key features of the IOS Firewall feature set are listed here:
∙Context−Based Access Control (CBAC) provides secure IP traffic filtering for each unique session for many applications.
∙Java blocking protects against malicious Java applets, allowing only applets from identified and trusted sources.
∙Denial−of−service (DoS) detection and prevention protects resources against common attacks.
∙Realtime alerts notify administrators during DoS attacks and certain other conditions.
∙Audit trail mechanisms track sessions by time, source and destination address, ports, and total number of bytes transmitted.
∙Intrusion detection provides realtime monitoring, interception, and response to network misuse with a set of common attack and probing intrusion detection signatures.
∙Provides multiservice integration, advanced security for dialup connections, and integrated routing and security at the Internet gateway.
As you can see, the IOS Firewall feature set has an extensive set of features that are designed to help secure an enterprise's network with robust firewall functionality. This chapter aims to discuss many of the enhanced features the IOS Firewall feature set encompasses. I'll discuss Context−Based Access Control (CBAC), which examines not only Network layer and Transport layer information, but also the Application layer protocol information to learn about the state of TCP and UDP connections. CBAC maintains connection state information for individual connections. This state information is used to make intelligent decisions about whether packets should be permitted or denied and dynamically creates and deletes temporary openings in the firewall. I'll discuss Port Application Mapping (PAM), which allows enterprises to customize TCP or UDP port numbers to support network environments that run services using ports that are different from the registered or well−known ports associated with an application. The information in the PAM table enables CBAC−supported services to run on nonstandard ports. I'll also discuss the IOS Firewall Intrusion Detection System (IDS), which acts as an inline intrusion detection sensor, watching packets and sessions as they flow through the router and scanning each to match any of the IDS signatures.
Context−Based Access Control
Context−Based Access Control was designed for use with multiple protocols that are unable to be processed with access lists. During many types of network attacks, packets that are not part of an
123
existing session are sent to a target machine, or there may be an attempt to inject packets within an existing session. Additionally, devices that are not properly configured can cause interruptions in service by sending inappropriate packets. The CBAC process will stop these types of attacks and problems by inspecting the TCP and UDP sessions. Only packets within sessions that meet certain criteria will be allowed to pass. Packets that are not within recognized sessions or that do not meet the security policy will be dropped.
More often than not, a router will make every attempt to forward a packet toward its destination in the most efficient manner. CBAC changes the forwarding nature by investigating aspects of each packet within the context of its session to determine if the packet or session meets the policy. If the packet or session meets the policy, it will be forwarded. If it does not, it will be discarded, and in some cases, the session will be terminated. To determine this, CBAC adds processes to a router so it will be able to perform the following:
∙Watch for the start of new sessions and ensure they meet the policy.
∙Maintain the state information of each session flowing through it by watching flags, sequence numbers, and acknowledgment numbers.
∙Set up and install dynamic access control lists for permitted sessions.
∙Close out sessions and remove temporary access control lists that have been terminated.
∙Closely examine SMTP sessions to allow only a minimum set of permitted commands.
∙Watch the permitted control sessions (such as FTPcontrol) and allow associated data sessions (such as FTPdata) to pass.
∙Watch for Java applets within HTTP sessions and block them if the router is configured to do so.
∙Examine each packet within each session to ensure that it conforms to the current session state.
∙Maintain a timer after each session's packet is forwarded and terminate any sessions that have exceeded the session timeout policy.
∙Watch for signs that a SYN attack is in progress, and if so, reset excessive session requests.
∙Send out alerts of unexpected events and packets that have been dropped because they don't meet the policy.
∙Optionally record time, source, and destination addresses; ports; and the total number of bytes transmitted by each participant at the end of the session.
Each of these security elements uses memory and processing cycles that will decrease normal packet forwarding efficiency of the Cisco IOS software on the router. CBAC uses 600 bytes of memory per connection and CPU resources during the access list inspection process.
Context−Based Access Control Protocol Support
CBAC can be configured to inspect the following protocols:
∙TCP sessions
∙UDP sessions
CBAC can also be configured to specifically inspect certain Application layer protocols. The following Application layer protocols can all be configured for CBAC:
∙CU−SeeMe
∙FTP
∙H.323
124
∙HTTP
∙Java
∙Microsoft NetShow
∙Unix R−commands
∙RealAudio
∙RPC, specifically Sun RPC and Microsoft RPC
∙SMTP
∙SQLNet
∙StreamWorks
∙TFTP
∙VDOLive
When a protocol is configured for CBAC that protocol's traffic is inspected and all state information is updated and maintained in the state table. Return traffic will be permitted back only through the firewall if the state table contains information indicating that the packet belongs to a permissible session. CBAC controls the traffic that belongs to a valid session. When return traffic is inspected, the state table information is updated as necessary.
Note UDP is a connectionless protocol; therefore, there are no actual "sessions," so the CBAC process examines particular information within the UDP packet and keeps track of that information. To determine if the packet is part of UDP "session," the CBAC process compares the information gathered against similar packets received within the idle timeout.
Operation of Context−Based Access Control
CBAC inspects traffic traveling through a router to discover and manage information about the state of the TCP or UDP sessions. This state information is used to create a temporary opening in access lists, which allows the returning traffic from the same session to enter the internal network through the firewall. To illustrate the operation of CBAC, Figure 4.1 shows an example CBAC network. When the router in Figure 4.1 initializes after a power−up or reload, it begins with an empty table to maintain state information for every session. When the host on the inside network of the router initiates a connection to a host on the outside network of the router, the router receives the first packet and will match the packet against any inbound access lists on the interface. If the packet is permitted by the inbound access list, CBAC will set up a table entry to record information about thesession. CBAC will also set up temporary access lists to permit returning packets that are part of the same session. This setup is handled through process−switching the first packet, and the information gathered is used as a reference so that all subsequent packets in the session may be fast−switched. The TCP and UDP sessions are identified through the IP addresses and the port numbers. To protect the session, the firewall feature set will inspect the TCP sequence and acknowledgment values as well as the flags, which must correspond to the transmitted data. For UDP and TCP, the subsequent packets must arrive within a timeout period. After the session has completed, the opened session entry is torn down and the connection is closed.
125
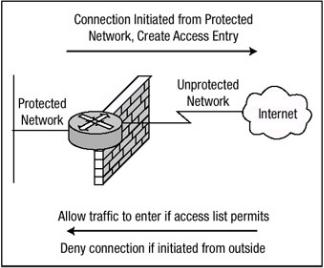
Figure 4.1: Basic operation of CBAC.
When using CBAC, the protocols that are to be inspected must be specified, and the interface and interface direction where inspection originates should be configured. Only protocols that have been specified will be inspected by CBAC. Packets that enter the IOS firewall are inspected by CBAC only if they first pass the inbound access list at the input interface, and the outbound access list at the output interface will be serviced by the router. If a packet is denied by the access list, the packet is simply dropped and not inspected by CBAC. CBAC inspection tracks sequence numbers in all TCP packets and drops those packets with sequence numbers that are not within expected ranges.
There are some protocols, such as Telnet or SMTP, that will have only one connection between client and server. These are called singlechannel sessions. All packets are identified as conforming to the session by acknowledging the receipt of bytes from the other device. After the session ends, one side or the other can start the termination process by setting the FIN flag. CBAC monitors this, and when the returning ACK is seen, CBAC will remove the temporary access control list. Removing the temporary access list will deny packets from the outside network from entering the inside network after the two devices in the session have agreed to terminate. During a session, CBAC will drop packets that violate its policy, such as packets with sequence/acknowledgment values outside of the acceptable window or with incorrectly set flags.
In addition to the single−channel sessions, several applications also use a control channel and create one or more additional data channels to carry information. These are called multichannel sessions, such as FTP and H.323. When the control channel forms, CBAC watches for an indication that a subsequent data channel will be needed. When this occurs, CBAC will add the access control list elements to accommodate the data channels. When the data channels are terminated, CBAC will remove the temporary access control list elements.
Two special cases also need to be mentioned: SMTP and Java processing. If SMTP inspection is enabled, only a set of the SMTP commands will be permitted through the firewall feature set. If some other command is seen coming from the untrusted network, CBAC will send a TCP/IP packet within the session to each participant with the RST flag set. This will terminate the session.
A Web browser request may return an HTML document that will initiate more than one TCP session from the client to the server to retrieve additional parts of the page. These can include text and graphics and may also include Java applets. If HTTP inspection is enabled and Java applets are being filtered, CBAC will inspect the leading parts of each HTTP session to match the Java applet signature. If CBAC finds this signature, it will terminate the session with a TCP packet, with the RST flag set sent to both client and server. When CBAC terminates a session like this, the temporary
126
