
- •Table of Contents
- •Cisco Network Security Little Black Book
- •Introduction
- •Is this Book for You?
- •How to Use this Book
- •The Little Black Book Philosophy
- •Chapter 1: Securing the Infrastructure
- •In Brief
- •Enterprise Security Problems
- •Types of Threats
- •Enterprise Security Challenges
- •Enterprise Security Policy
- •Securing the Enterprise
- •Immediate Solutions
- •Configuring Console Security
- •Configuring Telnet Security
- •Configuring Enable Mode Security
- •Disabling Password Recovery
- •Configuring Privilege Levels for Users
- •Configuring Password Encryption
- •Configuring Banner Messages
- •Configuring SNMP Security
- •Configuring RIP Authentication
- •Configuring EIGRP Authentication
- •Configuring OSPF Authentication
- •Configuring Route Filters
- •Suppressing Route Advertisements
- •Chapter 2: AAA Security Technologies
- •In Brief
- •Access Control Security
- •Cisco Secure Access Control Server
- •Immediate Solutions
- •Configuring TACACS+ Globally
- •Configuring TACACS+ Individually
- •Configuring RADIUS Globally
- •Configuring RADIUS Individually
- •Configuring Authentication
- •Configuring Authorization
- •Configuring Accounting
- •Installing and Configuring Cisco Secure NT
- •Chapter 3: Perimeter Router Security
- •In Brief
- •Defining Networks
- •Cisco Express Forwarding
- •Unicast Reverse Path Forwarding
- •TCP Intercept
- •Network Address Translation
- •Committed Access Rate
- •Logging
- •Immediate Solutions
- •Configuring Cisco Express Forwarding
- •Configuring Unicast Reverse Path Forwarding
- •Configuring TCP Intercept
- •Configuring Network Address Translation (NAT)
- •Configuring Committed Access Rate (CAR)
- •Configuring Logging
- •Chapter 4: IOS Firewall Feature Set
- •In Brief
- •Port Application Mapping
- •IOS Firewall Intrusion Detection
- •Immediate Solutions
- •Configuring Port Application Mapping
- •Configuring IOS Firewall Intrusion Detection
- •Chapter 5: Cisco Encryption Technology
- •In Brief
- •Cryptography
- •Benefits of Encryption
- •Symmetric and Asymmetric Key Encryption
- •Digital Signature Standard
- •Cisco Encryption Technology Overview
- •Immediate Solutions
- •Configuring Cisco Encryption Technology
- •Chapter 6: Internet Protocol Security
- •In Brief
- •IPSec Packet Types
- •IPSec Modes of Operation
- •Key Management
- •Encryption
- •IPSec Implementations
- •Immediate Solutions
- •Configuring IPSec Using Manual Keys
- •Configuring Tunnel EndPoint Discovery
- •Chapter 7: Additional Access List Features
- •In Brief
- •Wildcard Masks
- •Standard Access Lists
- •Extended Access Lists
- •Reflexive Access Lists
- •Dynamic Access Lists
- •Additional Access List Features
- •Immediate Solutions
- •Configuring Standard IP Access Lists
- •Configuring Extended IP Access Lists
- •Configuring Extended TCP Access Lists
- •Configuring Named Access Lists
- •Configuring Commented Access Lists
- •Configuring Dynamic Access Lists
- •Configuring Reflexive Access Lists
- •Appendix A: IOS Firewall IDS Signature List
- •Appendix B: Securing Ethernet Switches
- •Configuring Management Access
- •Configuring Port Security
- •Configuring Permit Lists
- •Configuring AAA Support
- •List of Figures
- •List of Tables
- •List of Listings
62 unknown protocol, 0 not a gateway
0 security failures, 0 bad options, 1147 with options
.....
Drop: 1468583 encap failed, 325 unresolved, 0 no adjacency 7805049 no route, 41 unicast RPF, 1428682 forced drop
Router−1#
Interface statistics help to provide information about which interface is the source of the attack. Statistics for each interface can be viewed using the show ip interface command. Interface statistics display two separate types of RPF drops: Unicast RPF drops and Unicast RPF suppressed drops. The display for Unicast RPF drops shows the number of drops at the interface, and the display for Unicast suppressed drops shows the number of packets that failed the Unicast RPF reverse lookup check but were forwarded because of a permit statement configured within the access list that is applied to Unicast RPF. The following output is from the show ip interface command:
Router−1#show ip interface serial1/0
...
Unicast RPF ACL 114 37 unicast RPF drops
12 unicast RPF suppressed drops Router−1#
Configuring TCP Intercept
The configuration of TCP Intercept is based on access lists, which are bound within TCP Intercept commands. Thus, access lists bound within TCP Intercept are not bound to an interface, as in most access list configurations.
Use the following steps to configure TCP Intercept (Steps 4, 5 and 6 are optional):
1. Use the following global configuration command to define an extended IP access list:
access−list access−list number [deny|permit] tcp any = <destination> <destination−wildcard mask>
The access list can be configured to intercept either all TCP requests or only those coming from specific networks or destined for specific servers. The access list should define the source as any and define specific destination networks or servers; do not attempt to filter on the source addresses because you may not know which source address to intercept packets from. Identify the destination to protect destination servers.
2. Use the following command to enable TCP Intercept:
ip tcp intercept list access−list number
3. Use this command to configure the mode in which TCP Intercept should operate:
ip tcp intercept mode <watch|intercept>
4.If Intercept is configured to run in watch mode, configure the amount of time it will wait for a watched connection to an established state before terminating the connection. Use this command to do so:
98
ip tcp intercept watch−timeout <seconds>
5.Configure the mode that Intercept should use to drop connections when under attack and running in aggressive mode by using this command:
ip tcp intercept drop−mode <random\oldest>
6.Configure the amount of time that a connection will be managed by Intercept by using the following command:
ip tcp intercept connection−timeout <seconds>
TCP Intercept has a number of other command arguments, which will be discussed in detail throughout this section. It should be noted that only the first three steps in the preceding list are required to take advantage of the features that TCP Intercept provides. The other steps, as well as the commands that will be discussed later, are considered commands that are used to fine−tune the operation of TCP Intercept.
Note Do not configure TCP Intercept on the perimeter router if the router is configured for Context−Based Access Control (CBAC).
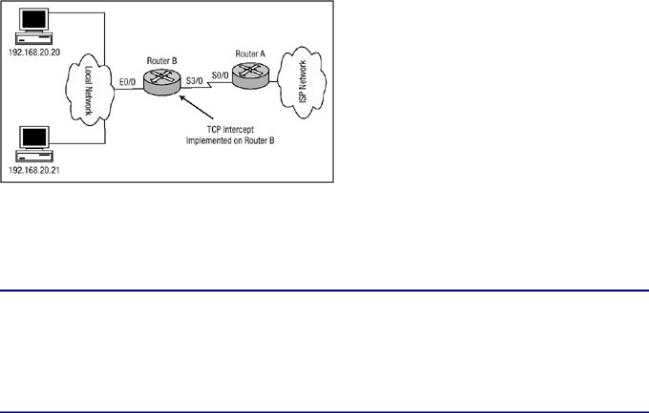
In Figure 3.4, Router B is the perimeter router for the enterprise and is configured for TCP Intercept. Router B has been configured to intercept requests to a Web server that has an IP address of 192.168.20.20 and to intercept requests to an FTP server with an IP address of 192.168.20.21.
Figure 3.4: An example TCP Intercept network.
Listing 3.5 details the configuration commands needed to configure Router B to intercept requests to the Web server and FTP server. Router B is configured for TCP Intercept in watch mode.
Listing 3.5: TCP Intercept configuration of Router B.
#config t
#access−list 100 permit tcp any host 192.168.20.20 #access−list 100 permit tcp any host 192.168.20.21 #ip tcp intercept list 100
#ip tcp intercept mode intercept #end
#
The configuration in Listing 3.5 defines access list 100 and permits any TCP traffic with a destination of 192.168.20.20 and 192.168.20.21 to be intercepted by Router B. TCP Intercept is configured on Router B and access list 100 is bound to the TCP Intercept configuration and the mode is configured for watch mode. TCP Intercept has a limited number of verification and debugging tools. One of the most useful verification commands is the show tcp intercept statistics command. Listing 3.6 lists the output of this command.
99

Listing 3.6: The output of show tcp intercept statistics.
Router−B#show tcp intercept statistics Intercepting new connections using access−list 100
148 incomplete, 851 established connections (total 999)
1 minute connection request rate 49 requests/sec Router−B#
The output of the show tcp intercept statistics command demonstrates that TCP Intercept is using access list 100 to compare against all new connections. The output of the command displays the number of incomplete connections and established connections.
The connection requests for each server can be monitored in realtime using the sh tcp intercept connections command. Issuing the command on Router B displays the output shown in Listing 3.7.
Listing 3.7: Example of show TCP intercept connections output.
Router−B# show tcp intercept connections |
|
|
|
||
Incomplete: |
|
|
|
|
|
Client |
Server |
State |
Create |
Timeout M |
|
208.19.121.12:58190 |
192.168.20.20:80 SYNRCVD |
00:00:06 |
00:00:02 I |
||
208.19.121.12:57934 |
192.168.20.20:80 SYNRCVD |
00:00:06 |
00:00:02 I |
||
168.41.18.4:59274 |
192.168.20.21:23 SYNRCVD |
00:00:06 |
00:00:02 I |
||
168.41.18.4:56196 |
192.168.20.21:23 SYNRCVD 00:00:06 00:00:02 |
I |
|||
... |
|
|
|
|
|
Established: |
|
|
|
|
|
Client |
Server |
State |
Create |
Timeout |
M |
17.96.23.23:1045 |
192.168.20.20:80 |
ESTAB |
00:01:10 23:58:52 I |
||
... |
|
|
|
|
|
|
|
|
|
|
|
Note The "M" in the 3rd and 10th lines in Listing 3.7 represents the word "Mode."
In Listing 3.7, the Incomplete section displays information related to connections that are not yet established. The Client field displays the source IP address of the client requesting service from the server and also lists the randomly generated source port number the source is using to communicate on. The Server field displays the destination server IP address and port number that is being protected by TCP Intercept. As discussed earlier, TCP Intercept will intercept each incoming connection request from the source and respond to the source on behalf of the server. After the source responds back to the router, the router will send the original SYN request packet to the server and merge the connections. The state of each of the connection requests is listed in the State field. The State field can contain one of three values:
∙SYNRCVD—When the connection is in this state, the router is attempting to establish a connection with the source of the connection request. It is during this phase that the router sends a SYN−ACK to the source and is awaiting an ACK from the source.
∙SYNSENT—When the connection is in this state, the router is attempting to establish a connection with the destination of the connection request. It is during this phase that the router has received an ACK from the source and is sending the original SYN request to the server in an attempt to perform the three−way handshake.
∙ESTAB—In order for the connection to reach this state, the two separate connections have been joined and communication between the source and destination is established.
The Create field details the amount of time since the connection was created. The Timeout field lists the amount of time remaining until the retransmission timeout is reached. The Mode field displays
100

the mode under which TCP Intercept is running; the values can be either I (for intercept mode) or W (for watch mode). The Established section displays information related to connections that have become established. All fields in the Established section maintain the same values they have in the Incomplete section with the exception of the Timeout field, which displays the time remaining until the connection timeout is reached and the connection is dropped.
In Listing 3.5, Router B was configured to operate in intercept mode in the earlier configuration; however, this can be changed using the ip tcp intercept mode command. Below, Router B is configured to operate in watch mode, and the ip tcp intercept watch−timeout command is used to lower the watch timeout from the default 30 seconds to a value of 16 seconds. Changing the watch timeout will define how long Intercept will wait for a watched TCP connection to reach an established state before it sends a reset to the server. The following configuration reflects the changes:
#config t
#ip tcp intercept mode watch
#ip tcp intercept watch−timeout 16\ #end
The default timeout value for an established session with no activity is 24 hours, or one day. Notice in Listing 3.7 that there is one established session between the client and server. The timeout value for the connection still has 23 hours, 58 minutes, and 52 seconds left before it times out. This means the connection will still be managed by the router for that amount of time, even if there is no activity between the client and server. In some environments, such as those with a large amount of connection requests, the default connection timeout value should be lowered so that the router does not have to use resources managing connections that are not being used. The connection timeout value can be changed using the ip tcp intercept connection−timeout command. Router B will now be configured to lower the default connection timeout value to 6 hours:
#config t
#ip tcp intercept connection−timeout 21600 #end
The connection−timeout command accepts the timeout value in seconds. The timeout value can be configured as low as 1 second and as high as 2147483 seconds.
Another method of viewing TCP Intercept statistics is to use the debug ip tcp intercept command. Using the debug command allows administrators to view a connections request in realtime. Using Listing 3.7 as a reference, the debug ip tcp intercept command was issued to monitor each connection request. Listing 3.8 details the output of the debug command; only the first and second connection requests are recorded in the output.
Listing 3.8: Example output from debug ip tcp intercept.
!1st connection attempt\
:new connection (208.19.121.12:58190) => (192.168.20.20:80)
:(208.19.121.12:58190) <− ACK+SYN (192.168.20.20:58190)
!2nd connection attempt
:new connection (168.41.18.4:59274) => (192.168.20.21:23)
:(168.41.18.4:59274) <− ACK+SYN (192.168.20.21:59274)
101

!Router B retransmits to the 1st client
:retransmit 4 (208.19.121.12:58190) <− (192.168.20.20:80)
:SYNRCVD
!Router B establishes a connection to the second client
:1st half of conn is established
:(168.41.18.4:59274)=>(192.168.20.21:23)
:(168.41.18.4:59274) SYN −> (192.168.20.21:23) SYNSENT
!Server responds and the connection is established
:2nd half of conn established
:(168.41.18.4:59274)=>(192.168.20.21:23)
:(168.41.18.4:59274) ACK −> (192.168.20.21:23)
!The router tries to establish a connection to the 1st client, !then times the connection out and sends a reset to the server.
:retransmit 16 (208.19.121.12:58190)>−(192.168.20.20:80)
:SYNRCVD
:retransmit expire
:(208.19.121.12:58190)=>(192.168.20.20:80) SYNRCVD
:(208.19.121.12:58190) <− RST (192.168.20.20:80)
The debug output in Listing 3.8 details the steps that TCP Intercept takes after it's configured, and a new connection request to a device that is matched by the configured access list is initiated.
After a device comes under attack from SYN floods, TCP Intercept will transition to a mode known as aggressive mode. Whether or not Intercept transitions to aggressive mode is determined by two values: the total number of incomplete connections and the total number of connection requests during Intercept's last 60−second sampling period. If either of these values is exceeded, TCP Intercept assumes that the device is under attack and transitions to aggressive mode. After both of the values fall below the configured minimum, the aggressive behavior ends.
When TCP Intercept is in aggressive mode, it will begin to drop the oldest partial connection request for each new connection that is requested when under attack; however, this action can be changed using the ip tcp intercept drop−mode global configuration command. The drop mode can be changed, so that TCP Intercept will drop any connection request regardless of age, instead of dropping the oldest partial connection request. TCP Intercept will also change the watch timeout if it is configured to run in watch mode. If Intercept is running in watch mode, the watch mode timeout value is reduced by half when TCP Intercept transitions to aggressive mode. The threshold for triggering aggressive mode is based on the total number of incomplete connections and can be configured using the following commands:
ip tcp intercept max−incomplete low number ip tcp intercept max−incomplete high number
The default for the low value is 900 incomplete connections, and the default for the high value is 1100 incomplete connections. The threshold for triggering aggressive mode based on the number of connection requests received in the last 60−second sample period can be configured using the following commands:
ip tcp intercept one−minute low number ip tcp intercept one−minute high number
102
