
- •Credits
- •About the Author
- •About the Reviewers
- •www.PacktPub.com
- •Table of Contents
- •Preface
- •Introduction
- •Shortest setup possible
- •OpenVPN secret keys
- •Multiple secret keys
- •Plaintext tunnel
- •Routing
- •Configuration files versus the command-line
- •Complete site-to-site setup
- •3-way routing
- •Introduction
- •Setting up the public and private keys
- •Simple configuration
- •Server-side routing
- •Routing: subnets on both sides
- •Redirecting the default gateway
- •Using an 'ifconfig-pool' block
- •Using the status file
- •Management interface
- •Proxy-arp
- •Introduction
- •Simple configuration—non-bridged
- •Enabling client-to-client traffic
- •Bridging—Linux
- •Bridging—Windows
- •Checking broadcast and non-IP traffic
- •External DHCP server
- •Using the status file
- •Management interface
- •Introduction
- •Certificate generation
- •xCA: a GUI for managing a PKI (Part 1)
- •xCA: a GUI for managing a PKI (Part 2)
- •OpenSSL tricks: x509, pkcs12, verify output
- •Revoking certificates
- •The use of CRLs
- •Checking expired/revoked certificates
- •Intermediary CAs
- •Multiple CAs: stacking, using --capath
- •Introduction
- •Initializing a hardware token
- •Getting a hardware token ID
- •Using a hardware token
- •Selecting a PKCS#11 certificate using the management interface
- •Generating a key on the hardware token
- •Private method for getting a PKCS#11 certificate
- •Pin caching example
- •Introduction
- •Using a client-side up/down script
- •Windows login greeter
- •Using client-connect/client-disconnect scripts
- •Using a 'learn-address' script
- •Using a 'tls-verify' script
- •Using an 'auth-user-pass-verify' script
- •Script order
- •Script security and logging
- •Using the 'down-root' plugin
- •Using the PAM authentication plugin
- •Introduction
- •Cipher mismatches
- •TUN versus TAP mismatches
- •Compression mismatches
- •Key mismatches
- •Troubleshooting MTU and tun-mtu issues
- •Troubleshooting network connectivity
- •How to read the OpenVPN log files
- •Introduction
- •The missing return route
- •Missing return routes when 'iroute' is used
- •Source routing
- •Routing and permissions on Windows
- •Troubleshooting client-to-client traffic routing
- •Understanding the 'MULTI: bad source' warnings
- •Failure when redirecting the default gateway
- •Introduction
- •Optimizing performance using 'ping'
- •OpenSSL cipher speed
- •Compression tests
- •Traffic shaping
- •Tuning UDP-based connections
- •Tuning TCP-based connections
- •Analyzing performance using tcpdump
- •Introduction
- •Linux: using NetworkManager
- •MacOS: using Tunnelblick
- •Windows Vista/7: elevated privileges
- •Windows: using the CryptoAPI store
- •Windows: updating the DNS cache
- •Windows: running OpenVPN as a service
- •Windows: public versus private network adapters
- •Windows: routing methods
- •Introduction
- •Including configuration files in config files
- •Details of ifconfig-pool-persist
- •Connecting using a SOCKS proxy
- •Connecting via an HTTP proxy
- •Connecting via an HTTP proxy with authentication
- •Using dyndns
- •IP-less setups (ifconfig-noexec)
- •Introduction
- •Inline certificates
- •Connection blocks
- •Port sharing with an HTTPS server
- •Routing features: redirect-private, allow-pull-fqdn
- •OCSP support
- •New for 2.2: the 'x509_user_name' parameter
- •Index
Point-to-Point Networks
There's more...
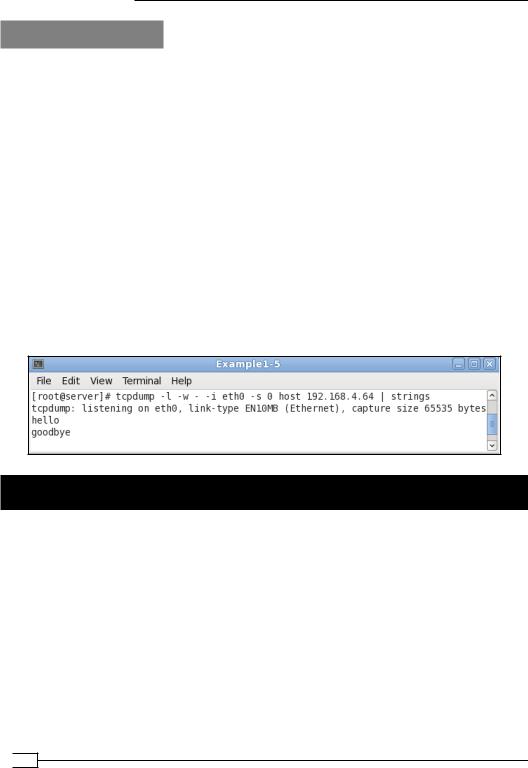
To actually view the traffic, we can use tcpdump:
Set up the connection as outlined.
Start tcpdump and listen on the network interface, not the tunnel interface itself:
[root]@client]# tcpdump -w -I eth0 -s 0 host openvpnserver \ | strings
Now, send some text across the tunnel, using something like nc (Netcat). First, launch nc on the server side:
[server]$ nc -l 31000
On the client side, launch nc in client mode and type the words hello and goodbye.
[client]$ nc 10.200.0.1 3100 hello
goodbye
In the tcpdump window, you should now see:
Routing
Point-to-point style networks are great if you want to connect two networks together over a static, encrypted tunnel. If you only have a small number of endpoints (fewer than four), then it is far easier than using a client/server setup as described in Chapter 2, Client-server IP-only Networks.
 16
16
Chapter 1
Getting ready
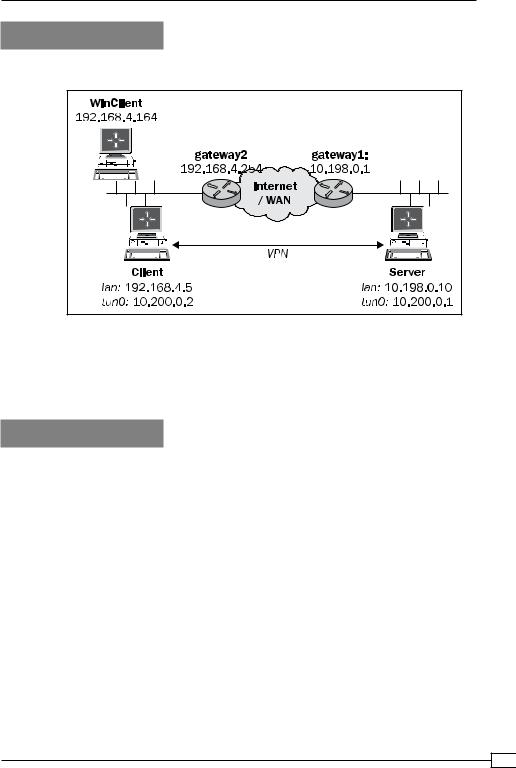
For this recipe, we use the following network layout:
Install OpenVPN 2.0 or higher on two computers. Make sure the computers are connected over a network. For this recipe, the server computer was running CentOS 5 Linux and OpenVPN 2.1.1 and the client was running Fedora 13 Linux and OpenVPN 2.1.1. We'll use the secret.key file from the OpenVPN Secret keys recipe here.
How to do it...
1.First we establish the connection, but we also make sure OpenVPN daemonized itself:
[root@server]# openvpn \
--ifconfig 10.200.0.1 10.200.0.2 \ --dev tun --secret secret.key \ --daemon --log /tmp/openvpnserver.log
2. Then we launch the client-side OpenVPN process:
[client]$ openvpn \
--ifconfig 10.200.0.2 10.200.0.1 \ --dev tun --secret secret.key \ --remote openvpnserver \
--daemon --log /tmp/openvpnclient.log
17 

Point-to-Point Networks
The connection is established:
[server]$ tail -1 /tmp/openvpnserver.log Initialization Sequence Completed
Now we add routing:
1. On the server side, we add a static route:
[root@server]# route add -net 192.168.4.0/24 gw 10.200.0.2
2. On the client side, we need to do two things:
Make sure that you have IP traffic forwarding enabled. On Linux this can be achieved using the following:
[root@client]# sysctl -w net.ipv4.ip_forward=1
Note that this setting does not survive a reboot of the system.
Make sure that on the Windows client on the client-side LAN there is a route back to the OpenVPN server:
C:> route add 10.200.0.0 mask 255.255.255.0 192.168.4.5
Here 192.168.4.5 is the LAN IP address of the OpenVPN client.
3.From the server, we can now ping machines on the client LAN. First we ping the LAN IP of the OpenVPN client:
[root@server]# ping -c 2 192.168.4.5
PING 192.168.4.5 (192.168.4.5) 56(84) bytes of data.
64 bytes from 192.168.4.5: icmp_seq=0 ttl=64 time=31.7 ms 64 bytes from 192.168.4.5: icmp_seq=1 ttl=64 time=31.3 ms
--- 192.168.4.5 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1000ms
rtt min/avg/max/mdev = 31.359/31.537/31.716/0.251 ms, pipe 2
4. And next the LAN IP of a machine on the OpenVPN client LAN:
[root@server]# ping -c 2 192.168.4.164
[server]$ ping -c 2 192.168.4.164
PING 192.168.4.164 (192.168.4.164) 56(84) bytes of data. 64 bytes from 192.168.4.164: icmp_seq=0 ttl=63 time=31.9 ms 64 bytes from 192.168.4.164: icmp_seq=1 ttl=63 time=31.4 ms
--- 192.168.4.164 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 31.486/31.737/31.989/0.308 ms, pipe 2
 18
18
Chapter 1
How it works...
In our network setup, the LAN we want to reach is behind the OpenVPN client, so we have to add a route to the server:
[server]$ route add -net 192.168.4.0/24 gw 10.200.0.2
On the client side, we need to do two things:
Make sure that the routing is enabled. If you want routing to remain enabled after a reboot, edit the file /etc/sysctl.cnf.
net.ipv4.ip_forward = 1
We also need to make sure that on the client LAN there is a route back to the OpenVPN server. This can be done by adding a route to the LAN gateway or by adding a static route to each of the machines on the client LAN. In this recipe, we added a route to a Windows client that is in the same LAN as the OpenVPN client:
C:> route add 10.200.0.0 mask 255.255.255.0 192.168.4.5
where 192.168.4.5 is the LAN IP address of the OpenVPN client.
There's more...
Routing issues
On the openvpn-users mailing list, a large number of the problems reported have to do with routing issues. Most of them have little to do with the OpenVPN itself but more with understanding the routing and the flow of packets over the network. Chapter 8,
Troubleshooting OpenVPN: Routing Issues, provides some recipes to diagnose and fix the most common routing problems.
Automating the setup
It is also possible to add the appropriate routes when the tunnel first comes up. This can be done using the --route statement:
[server]$ openvpn \
--ifconfig 10.200.0.1 10.200.0.2 \ --dev tun --secret secret.key \
--daemon --log /var/log/openvpnserver-1.5.log \ --route 192.168.4.0 255.255.255.0
Note that on the client LAN the route back to the server still has to be set manually.
19 
