
- •Credits
- •About the Author
- •About the Reviewers
- •www.PacktPub.com
- •Table of Contents
- •Preface
- •Introduction
- •Shortest setup possible
- •OpenVPN secret keys
- •Multiple secret keys
- •Plaintext tunnel
- •Routing
- •Configuration files versus the command-line
- •Complete site-to-site setup
- •3-way routing
- •Introduction
- •Setting up the public and private keys
- •Simple configuration
- •Server-side routing
- •Routing: subnets on both sides
- •Redirecting the default gateway
- •Using an 'ifconfig-pool' block
- •Using the status file
- •Management interface
- •Proxy-arp
- •Introduction
- •Simple configuration—non-bridged
- •Enabling client-to-client traffic
- •Bridging—Linux
- •Bridging—Windows
- •Checking broadcast and non-IP traffic
- •External DHCP server
- •Using the status file
- •Management interface
- •Introduction
- •Certificate generation
- •xCA: a GUI for managing a PKI (Part 1)
- •xCA: a GUI for managing a PKI (Part 2)
- •OpenSSL tricks: x509, pkcs12, verify output
- •Revoking certificates
- •The use of CRLs
- •Checking expired/revoked certificates
- •Intermediary CAs
- •Multiple CAs: stacking, using --capath
- •Introduction
- •Initializing a hardware token
- •Getting a hardware token ID
- •Using a hardware token
- •Selecting a PKCS#11 certificate using the management interface
- •Generating a key on the hardware token
- •Private method for getting a PKCS#11 certificate
- •Pin caching example
- •Introduction
- •Using a client-side up/down script
- •Windows login greeter
- •Using client-connect/client-disconnect scripts
- •Using a 'learn-address' script
- •Using a 'tls-verify' script
- •Using an 'auth-user-pass-verify' script
- •Script order
- •Script security and logging
- •Using the 'down-root' plugin
- •Using the PAM authentication plugin
- •Introduction
- •Cipher mismatches
- •TUN versus TAP mismatches
- •Compression mismatches
- •Key mismatches
- •Troubleshooting MTU and tun-mtu issues
- •Troubleshooting network connectivity
- •How to read the OpenVPN log files
- •Introduction
- •The missing return route
- •Missing return routes when 'iroute' is used
- •Source routing
- •Routing and permissions on Windows
- •Troubleshooting client-to-client traffic routing
- •Understanding the 'MULTI: bad source' warnings
- •Failure when redirecting the default gateway
- •Introduction
- •Optimizing performance using 'ping'
- •OpenSSL cipher speed
- •Compression tests
- •Traffic shaping
- •Tuning UDP-based connections
- •Tuning TCP-based connections
- •Analyzing performance using tcpdump
- •Introduction
- •Linux: using NetworkManager
- •MacOS: using Tunnelblick
- •Windows Vista/7: elevated privileges
- •Windows: using the CryptoAPI store
- •Windows: updating the DNS cache
- •Windows: running OpenVPN as a service
- •Windows: public versus private network adapters
- •Windows: routing methods
- •Introduction
- •Including configuration files in config files
- •Details of ifconfig-pool-persist
- •Connecting using a SOCKS proxy
- •Connecting via an HTTP proxy
- •Connecting via an HTTP proxy with authentication
- •Using dyndns
- •IP-less setups (ifconfig-noexec)
- •Introduction
- •Inline certificates
- •Connection blocks
- •Port sharing with an HTTPS server
- •Routing features: redirect-private, allow-pull-fqdn
- •OCSP support
- •New for 2.2: the 'x509_user_name' parameter
- •Index
Chapter 3
Using the status file
OpenVPN offers several options to monitor the clients connected to a server. The most commonly-used method is using a status file. This recipe will show how to use and read the OpenVPN status file. We will also focus on some subtleties of the status file in a
TAP-style setup.
Getting ready
Set up the client and server certificates using the first recipe from Chapter 2, Client-server IP-only Networks. For this recipe the server computer was running CentOS 5 Linux and
OpenVPN 2.1.1. The first client was running Fedora 12 Linux and OpenVPN 2.1.1 . The second client was running Windows XP and OpenVPN 2.1.1. For the Linux client, keep the client configuration file example3-1-client.conf at hand. For the Windows client, keep the client configuration file example3-2-client2.ovpn at hand.
How to do it...
1.Create the server configuration file by adding a line to the example3-1-server. conf. file:
status /var/log/openvpn.status
Save it as example3-7-server.conf. 2. Start the server:
[root@server]# openvpn --config example3-7-server.conf
3.First, start the Linux client using the configuration file from the earlier recipe and ping a host on the remote network:
[root@client1]# openvpn --config example3-1-client.conf [root@client1]# ping 10.198.0.1
4.After the VPN is established, list the contents of the openvpn.status file (as user root):
[root@server]# cat /var/log/openvpn.status
OpenVPN CLIENT LIST
Updated,Fri Jun 4 13:34:39 2010
Common Name,Real Address,Bytes Received,Bytes Sent,Connected Since
openvpnclient1,192.168.4.65:50183,10024,10159,Fri Jun 4 13:26:48 2010
ROUTING TABLE
95 
Client-server Ethernet-style Networks
Virtual Address,Common Name,Real Address,Last Ref 5e:52:73:5c:6a:ce,openvpnclient1,192.168.4.65:50183,Fri Jun 4 13:27:06 2010
GLOBAL STATS
Max bcast/mcast queue length,1 END
5. Start the Windows client:
6.Ping a host on the remote network:
[WinClient2]C:> ping 10.198.0.1
7.List the contents of the status file again on the server:
[root@server]# cat /var/log/openvpn.status
OpenVPN CLIENT LIST
Updated,Fri Jun 4 13:34:39 2010
Common Name,Real Address,Bytes Received,Bytes Sent,Connected Since
openvpnclient1,192.168.4.65:50183,10024,10159,Fri Jun 4 13:27:08 2010
openvpnclient2,192.168.4.64:50186,18055,9726,Fri Jun 4 13:26:48 2010
ROUTING TABLE
Virtual Address,Common Name,Real Address,Last Ref 5e:52:73:5c:6a:ce,openvpnclient1,192.168.4.65:50183,Fri Jun 4 13:27:06 2010 00:ff:17:82:55:db,openvpnclient2,192.168.4.64:50186,Fri Jun 4 13:27:16 2010
GLOBAL STATS
Max bcast/mcast queue length,1 END
 96
96
Chapter 3
How it works...
Each time a client connects to the OpenVPN server, the status file is updated with the connection information. The OPENVPN CLIENT LIST and ROUTING TABLE are the most interesting tables, as they show:
Which clients are connected
From which IP address the clients are connecting
The number of bytes each client has received and transferred
The time at which the client connected
The routing table also shows which networks are routed to each client. This routing table is filled when clients start sending traffic that needs to be routed. The ping commands in the recipe were used to trigger the routing table entries.
There's more...
Difference with TUN-style networks
The major difference in the status file when using a 'tap'-style network compared to a
'tun'-style network (see the Chapter 2 recipe, Using the status file) is in the ROUTING TABLE. The recipe from the previous chapter shows:
192.168.200.2,openvpnclient1,192.168.4.65:56764,<Date>
Whereas in this recipe, we see:
5e:52:73:5c:6a:ce,openvpnclient1,192.168.4.65:50183,<Date>
The address 5e:52:73:5c:6a:ce is the randomly-chosen MAC address of the 'tap' adapter on the openvpnclient1 machine.
Disconnecting clients
Note that when a client disconnects, the status file is not updated immediately. OpenVPN first tries to reconnect to the client based on the keepalive parameters in the server configuration file. The server configuration file in this recipe uses:
keepalive 10 60
This tells the server that it will ping the client every 10th second. The OpenVPN server will double the second argument: if it does not get response after 2 * 60 seconds, the connection is restarted. The server will also tell the client to ping the server every 10 seconds and to restart the connection after 60 seconds if it does not get any response.
If the client explicitly closes the connection using the directive explicit-exit-notify or when a TCP-based setup is used, the server does not wait for ping responses from the client.
97 
Client-server Ethernet-style Networks
See also
Chapter 2's recipe, Using the status file, which explains how the status file can be configured and used for IP-only style networks.
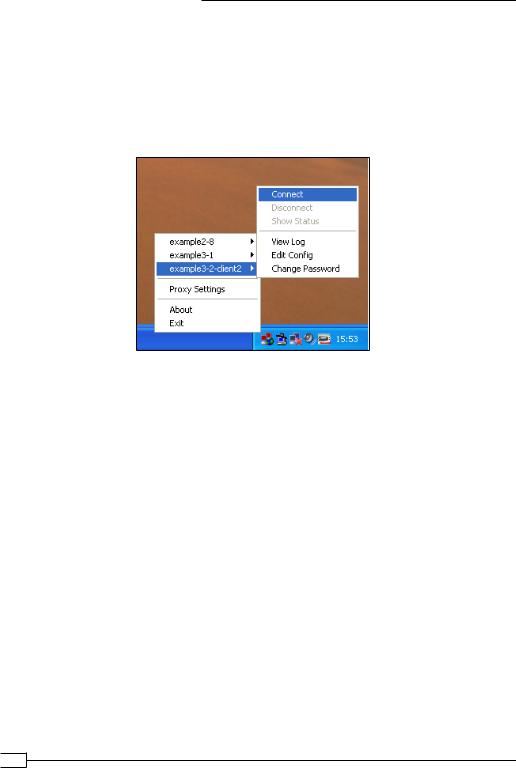
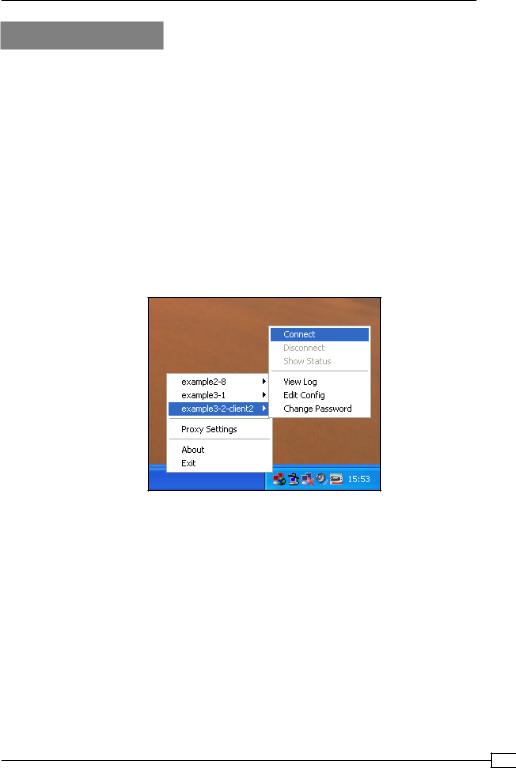
Management interface
This recipe shows how OpenVPN can be managed using the management interface on the server.
Getting ready
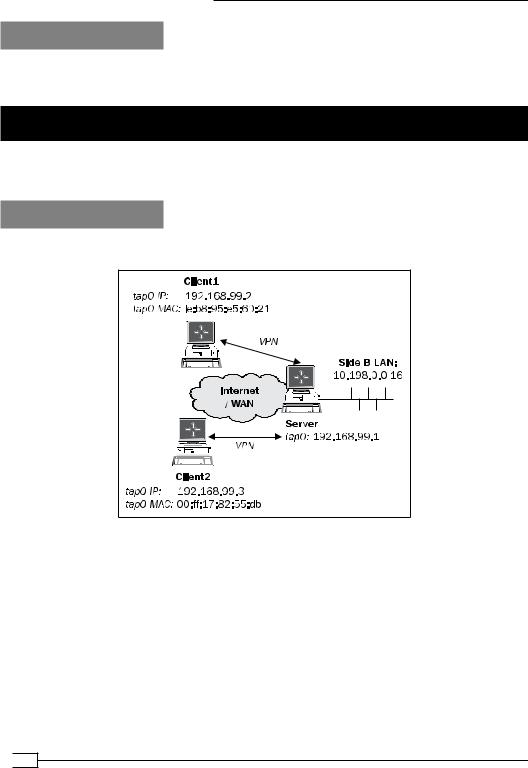
We use the following network layout:
Set up the client and server certificates using the first recipe from Chapter 2, Client-server IP-only Networks. For this recipe, the server computer was running CentOS 5 Linux and
OpenVPN 2.1.1. For the server, keep the configuration file example3-1-server.conf from the first recipe of this chapter at hand. The first client was running Fedora 12 Linux and
OpenVPN 2.1.1. The second client was running Windows XP and OpenVPN 2.1.1. For the
Linux client, keep the client configuration file example3-1-client.conf from the first recipe of this chapter at hand. For the Windows client, keep the client configuration file example3-2-client2.ovpn from the recipe Enabling client-to-client traffic at hand.
 98
98
Chapter 3
How to do it...
1.Create the server configuration file by adding a line to the example3-1-server. conf file:
management tunnel 23000 stdin
And save it as example3-8-server.conf.
2.Start the server:
[root@server]# openvpn --config example3-8-server.conf
The OpenVPN server will now first ask for a password for the management interface.
3.Start the clients using the configuration files from the earlier recipe:
[root@client1]# openvpn --config example3-1-client.conf
And the Windows client:
4.After the VPN is established, we can connect from the server to the management interface of the OpenVPN client using the telnet program:
[server]$ telnet 127.0.0.1 23000
Trying 127.0.0.1...
Connected to localhost.localdomain (127.0.0.1). Escape character is '^]'.
ENTER PASSWORD:cookbook SUCCESS: password is correct
>INFO:OpenVPN Management Interface Version 1 -- type 'help' for more info
status
OpenVPN CLIENT LIST
99 
Client-server Ethernet-style Networks
Updated,Fri Jun 4 13:57:07 2010
Common Name,Real Address,Bytes Received,Bytes Sent,Connected Since openvpnclient1,192.168.4.64:50209,7851,8095,Fri Jun 4 13:56:08 2010
openvpnclient2,192.168.4.5:50212,11696,7447,Fri Jun 4 13:56:45 2010
ROUTING TABLE
Virtual Address,Common Name,Real Address,Last Ref 00:ff:17:82:55:db,openvpnclient2,192.168.4.5:50212,Fri Jun 4 13:56:49 2010 1e:b8:95:e5:60:21,openvpnclient1,192.168.4.64:50209,Fri Jun 4 13:56:53 2010
GLOBAL STATS
Max bcast/mcast queue length,1 END
Note that it looks exactly like the status file from the previous recipe.
5.It is also possible to disconnect a client:
kill openvpnclient2
SUCCESS: common name 'openvpnclient2' found, 1 client(s) killed
status
OpenVPN CLIENT LIST
Updated,Fri Jun 4 13:58:51 2010
Common Name,Real Address,Bytes Received,Bytes Sent,Connected Since openvpnclient1,192.168.4.64:50209,8381,8625,Fri Jun 4 13:56:08 2010
ROUTING TABLE
Virtual Address,Common Name,Real Address,Last Ref 1e:b8:95:e5:60:21,openvpnclient1,192.168.4.64:50209,Fri Jun 4 13:56:53 2010
GLOBAL STATS
Max bcast/mcast queue length,1 END
6.Use Ctrl+] or "exit" to exit the 'telnet' program.
How it works...
When the OpenVPN server starts a special management interface is set up using the directive:
management 127.0.0.1 23000 stdin
 100
100
Chapter 3
And with these parameters:
127.0.0.1 to bind the management interface to localhost only.
The port 23000 on which the management interface will be listening.
The last parameter is the password file or the special keyword stdin to indicate that the management interface password will be specified when OpenVPN starts up. Note that this password is completely unrelated to the private key passphrases or any other user management passwords that OpenVPN uses.
After the management interface comes up, the server operator can connect to it using telnet and can query the server. By typing the following the operator can disconnect a client:
kill <clientcommonname>
Note that if the OpenVPN client is configured to automatically reconnect, it will do so after a few minutes.
When comparing the output of the management interface status command to the status file output shown in the Chapter 2 recipe, Using the status file, the major difference is the fact that here the clients MAC addresses are listed instead of the VPN IP addresses. The OpenVPN does not even need to know the clients' IP addresses, as they can be assigned by an external DHCP server.
There's more...
Client side management interface
The management interface can also be run on the OpenVPN clients. See Management interface in Chapter 2, Client-server IP-only Networks.
It is expected that the management interface will become more important in future versions of OpenVPN both on the client and the server side as the preferred method for programmatically interacting with the OpenVPN software.
See also
Chapter 2's recipe, Management interface, in which the client-side management interface is explained
Chapter 2's recipe, Using the status file, where the details of the status file for a TUN-style network are explained.
101
