
- •Credits
- •About the Author
- •About the Reviewers
- •www.PacktPub.com
- •Table of Contents
- •Preface
- •Introduction
- •Shortest setup possible
- •OpenVPN secret keys
- •Multiple secret keys
- •Plaintext tunnel
- •Routing
- •Configuration files versus the command-line
- •Complete site-to-site setup
- •3-way routing
- •Introduction
- •Setting up the public and private keys
- •Simple configuration
- •Server-side routing
- •Routing: subnets on both sides
- •Redirecting the default gateway
- •Using an 'ifconfig-pool' block
- •Using the status file
- •Management interface
- •Proxy-arp
- •Introduction
- •Simple configuration—non-bridged
- •Enabling client-to-client traffic
- •Bridging—Linux
- •Bridging—Windows
- •Checking broadcast and non-IP traffic
- •External DHCP server
- •Using the status file
- •Management interface
- •Introduction
- •Certificate generation
- •xCA: a GUI for managing a PKI (Part 1)
- •xCA: a GUI for managing a PKI (Part 2)
- •OpenSSL tricks: x509, pkcs12, verify output
- •Revoking certificates
- •The use of CRLs
- •Checking expired/revoked certificates
- •Intermediary CAs
- •Multiple CAs: stacking, using --capath
- •Introduction
- •Initializing a hardware token
- •Getting a hardware token ID
- •Using a hardware token
- •Selecting a PKCS#11 certificate using the management interface
- •Generating a key on the hardware token
- •Private method for getting a PKCS#11 certificate
- •Pin caching example
- •Introduction
- •Using a client-side up/down script
- •Windows login greeter
- •Using client-connect/client-disconnect scripts
- •Using a 'learn-address' script
- •Using a 'tls-verify' script
- •Using an 'auth-user-pass-verify' script
- •Script order
- •Script security and logging
- •Using the 'down-root' plugin
- •Using the PAM authentication plugin
- •Introduction
- •Cipher mismatches
- •TUN versus TAP mismatches
- •Compression mismatches
- •Key mismatches
- •Troubleshooting MTU and tun-mtu issues
- •Troubleshooting network connectivity
- •How to read the OpenVPN log files
- •Introduction
- •The missing return route
- •Missing return routes when 'iroute' is used
- •Source routing
- •Routing and permissions on Windows
- •Troubleshooting client-to-client traffic routing
- •Understanding the 'MULTI: bad source' warnings
- •Failure when redirecting the default gateway
- •Introduction
- •Optimizing performance using 'ping'
- •OpenSSL cipher speed
- •Compression tests
- •Traffic shaping
- •Tuning UDP-based connections
- •Tuning TCP-based connections
- •Analyzing performance using tcpdump
- •Introduction
- •Linux: using NetworkManager
- •MacOS: using Tunnelblick
- •Windows Vista/7: elevated privileges
- •Windows: using the CryptoAPI store
- •Windows: updating the DNS cache
- •Windows: running OpenVPN as a service
- •Windows: public versus private network adapters
- •Windows: routing methods
- •Introduction
- •Including configuration files in config files
- •Details of ifconfig-pool-persist
- •Connecting using a SOCKS proxy
- •Connecting via an HTTP proxy
- •Connecting via an HTTP proxy with authentication
- •Using dyndns
- •IP-less setups (ifconfig-noexec)
- •Introduction
- •Inline certificates
- •Connection blocks
- •Port sharing with an HTTPS server
- •Routing features: redirect-private, allow-pull-fqdn
- •OCSP support
- •New for 2.2: the 'x509_user_name' parameter
- •Index

Chapter 5
The pkcs11-tool utility can only copy private keys and certificates to a hardware token if they are in so-called DER format. Hence, we first convert the client.key and client.crt files to this format using the openssl command.
There's more...
Public and private objects
The certificate stored on the hardware token is considered as a public object. Even if we did not log in to the token we can still view it:
$ pkcs11-tool --module /usr/lib64/libeTPkcs11.so -O
Certificate Object, type = X.509 cert label: Client1
ID: 20100703
In a later recipe, we will see how we can disable this functionality.
OpenSC versus Aladdin PKI Client driver
In this recipe, we used the proprietary Aladdin PKI Client driver software to initialize the token. This also means that all access to the token has to be done using this driver.
The open source package OpenSC, from which the pkcs11-tool command is used, also supplies a PKCS#11 driver, opensc-pkcs11.so. However, it is not possible to initialize a token using the Aladdin driver software and then access it using the PKCS11 module that comes with the OpenSC package.
The main reason why the Aladdin PKI Client driver was chosen is that this driver works better on the computer used for this recipe. However, this is highly dependent on the operating system installation.
Getting a hardware token ID
Before we can configure OpenVPN to make use of the hardware token, we must first determine what the hardware token ID is. This hardware token ID looks quite complicated at first, hence a separate recipe is included for this purpose.
Getting ready
Keep the hardware token from the previous recipe at hand. Install OpenVPN 2.1. In this recipe, the computer used was running Fedora 12 Linux, pcsc-lite 1.5.2, opensc-0.11.12, PKI Client 5.00, and OpenVPN 2.1.1.
131

Two-factor Authentication with PKCS#11
How to do it...
Use the following command to list the PKCS#11 IDs that are available to OpenVPN:
$ openvpn --show-pkcs11-ids /usr/lib64/libeTPkcs11.so
The following objects are available for use.
Each object shown below may be used as parameter to --pkcs11-id option please remember to use single quote mark.
Certificate
DN: /C=NL/O=Cookbook/CN=openvpnclient1/… Serial: 02
Serialized id: Aladdin\x20Ltd\x2E/eToken/001a01a9/ Cookbook/20100703
How it works...
OpenVPN loads the PKCS#11 library /usr/lib64/libETPkcs11.so and queries it for the certificates in a very similar fashion to the pkcs11-tool command from the previous recipe. The library /usr/lib64/libETPkcs11.so is part of Aladdin's PKI Client 5.00 client software.
Each certificate that is found is then translated into a serialized ID that is unique for each token and for each certificate found. The serialized ID for the token used in this recipe is:
Aladdin\x20Ltd\x2E/eToken/001a01a9/Cookbook/20100703
This can be read as follows:
The token manufacturer is Aladdin\x20Ltd\x2E. The code \x20 is the hexadecimal representation of the space character. Similarly, the code \x2E is the hexadecimal representation of the character '.' (period).
The token model is eToken.
The token serial number is 001a01a9. This serial number is unique for each Aladdin eToken token.
The token name is Cookbook. The token name is usually chosen when the token is initialized.
The certificate ID to use is 20100703. This is the same ID that was used to copy the private key and X509 certificate to the token in the previous recipe.
 132
132

Chapter 5
There's more...
In this section, we will address the automatic selection of a certificate on a hardware token and on the choice of the PKCS#11 library.
What about automatic selection?
A logical question to ask is whether it is possible to automatically choose a certificate on a hardware token. Currently, this is not possible, mostly due to security concerns. Automatically choosing a certificate on the first hardware token that is entered is considered a bad security practice. As we are attempting to improve security using two-factor authentication, this is
not allowed.
PKCS#11 libraries
The library /usr/lib64/libETPkcs11.so is part of Aladdin's PKI Client 5.00 client software for 64-bit Linux. For a 32-bit Linux architecture, the library would have been /usr/ lib/libeTPkcs11.so. On Windows, this library is usually found in '%windir%\system32\
etpkcs11.dll or C:\WINDOWS\system32\etpkcs11.dll.
Other hardware token middleware can also be used. For example, the PKCS#11 library that is supplied by the OpenSC project is /usr/lib64/opensc-pkcs11.so (64-bit Linux). However, note that a PKCS#11 library from one project or vendor is usually incompatible when used with hardware tokens that have been initialized using the client software from another vendor. The choice of hardware device and the choice of the driver software for the hardware device depends greatly on which operating systems will be used and whether the same hardware device is used on different operating systems. For Windows users, the driver supplied with the hardware token often works better, but it also comes with licensing costs. If the driver software for a particular device is not available for Mac OS X or Linux, then the OpenSC driver is a better choice.
Using a hardware token
This recipe will demonstrate how to use a hardware token as a replacement for an X509 certificate and the corresponding private key.
133

Two-factor Authentication with PKCS#11
Getting ready
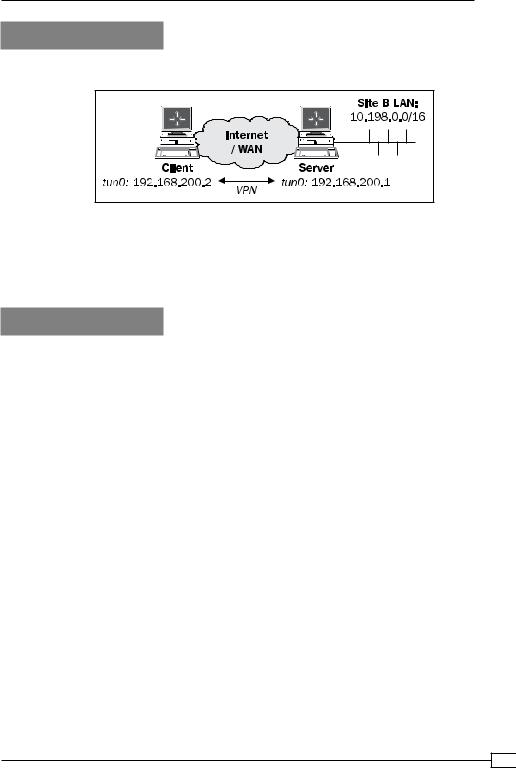
We use the following network layout:
Keep the hardware token from the first recipe at hand. For this recipe, the server computer was running CentOS 5 Linux and OpenVPN 2.1.1. The client was running Fedora 12 Linux and OpenVPN 2.1.1. Keep the server configuration file basic-udp-server.conf from the
Chapter 2 recipe Server-side routing at hand.
How to do it...
1.Start the server using the configuration file basic-udp-server.conf:
[root@server]# openvpn --config basic-udp-server.conf
2.Next, create the client configuration file:
client proto udp
remote openvpnserver.example.com port 1194
dev tun nobind
ca /etc/openvpn/cookbook/ca.crt tls-auth /etc/openvpn/cookbook/ta.key 1
ns-cert-type server
pkcs11-providers /usr/lib64/libeTPkcs11.so
pkcs11-id 'Aladdin\x20Ltd\x2E/eToken/001a01a9/Cookbook/20100703'
The last directive pkcs11-id and the serialized ID Aladdin\x20… need to be specified on a single line. Save it as example5-3-client.conf.
 134
134

Chapter 5
3.Start the client:
[root@client]$ openvpn --config example5-3-client.conf
The client connection log is shown below:
After entering the hardware token password (Enter the Cookbook token password), the connection is established.
How it works...
We configure OpenVPN to make use of a PKCS#11 provider:
pkcs11-providers /usr/lib64/libeTPkcs11.so
Note that on a 32-bit system, we would have used:
pkcs11-providers /usr/lib/libeTPkcs11.so
With the serialized ID from the previous recipe, we instruct OpenVPN to use the certificate we copied to the token in the first recipe:
pkcs11-id 'Aladdin\x20Ltd\x2E/eToken/001a01a9/Cookbook/20100703'
This enables OpenVPN to make use of the certificate and private key stored on the hardware token, allowing it to establish a connection to the OpenVPN server.
135

Two-factor Authentication with PKCS#11
There's more...
In this section, we will explain in more detail what is different when using a hardware token and what to be aware of when using the alternate OpenSC PKCS#11 driver in combination with OpenVPN.
What is different?
The major difference between using a hardware token and using a regular certificate and private key pair is in how security is established between the client and the peer. When a regular certificate and private key are used OpenVPN has full access to the private key using the OpenSSL library. The SSL handshake between client and server is performed entirely by OpenVPN itself by creating the session encryption keys using the private key.
When a hardware token is used, OpenVPN does not have access to the private key. The SSL handshake is performed in parts by OpenVPN and in parts by the hardware token. Especially, the session encryption keys are computed by the hardware token itself.
Using the OpenSC driver
When the PKCS#11 driver opensc-pkcs11.so from the OpenSC package is used, it is convenient to add the following to the OpenVPN configuration file, even if no scripts are used:
script-security 2 system
There is a bug in OpenVPN up to 2.1.4 when this line is not present, which causes rekeying to fail. This means that the OpenVPN session will stop functioning after the rekeying interval, which is normally set to 1 hour. The previous line of code is a work-around for this bug.
Using the management interface to list
PKCS#11 certificates
This recipe will demonstrate how to list the available certificates using the management interface on the client side. Although no particular network layout is required, we have to set up a working VPN connection before we can fully use the management interface.
 136
136
Chapter 5
Getting ready
We use the following network layout:
Keep the hardware token from the first recipe at hand. For this recipe, the server computer was running CentOS 5 Linux and OpenVPN 2.1.1. The client was running Fedora 12 Linux and OpenVPN 2.1.1. Keep the server configuration file basic-udp-server.conf from the Chapter 2 recipe, Server-side routing at hand.
How to do it...
1.Start the server using the configuration file basic-udp-server.conf:
[root@server]# openvpn --config basic-udp-server.conf
2.Next, create the client configuration file:
client proto udp
remote openvpnserver.example.com port 1194
dev tun nobind
ca /etc/openvpn/cookbook/ca.crt tls-auth /etc/openvpn/cookbook/ta.key 1
ns-cert-type server
pkcs11-providers /usr/lib64/libeTPkcs11.so
pkcs11-id 'Aladdin\x20Ltd\x2E/eToken/001a01a9/Cookbook/20100703'
management 127.0.0.1 23000 stdin
Save it as example5-4-client.conf.
137
Two-factor Authentication with PKCS#11
3.Start the client:
[root@client]$ openvpn --config example5-4-client.conf
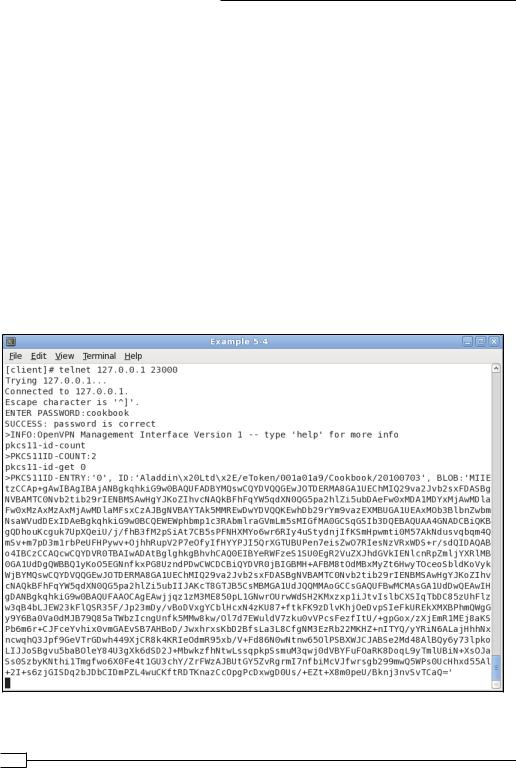
After the connection is established, telnet to the management interface from another terminal window on the client:
[client]$ telnet 127.0.0.1 23000
4.The first management command to try is:
pkcs11-id-count
This will return the number of certificates found on the hardware token.
5.The second command will return the first certificate on the hardware token that is configured for use in OpenVPN (counting starts at zero!):
pkcs11-id-get 0
This will output the serialized ID and the X509 certificate as a BASE64-encoded blob. This might not be very useful to an end-user but the management interface is also intended to be accessed programmatically. The results of the previous two commands are shown in the following figure:
 138
138
