
Network Plus 2005 In Depth
.pdf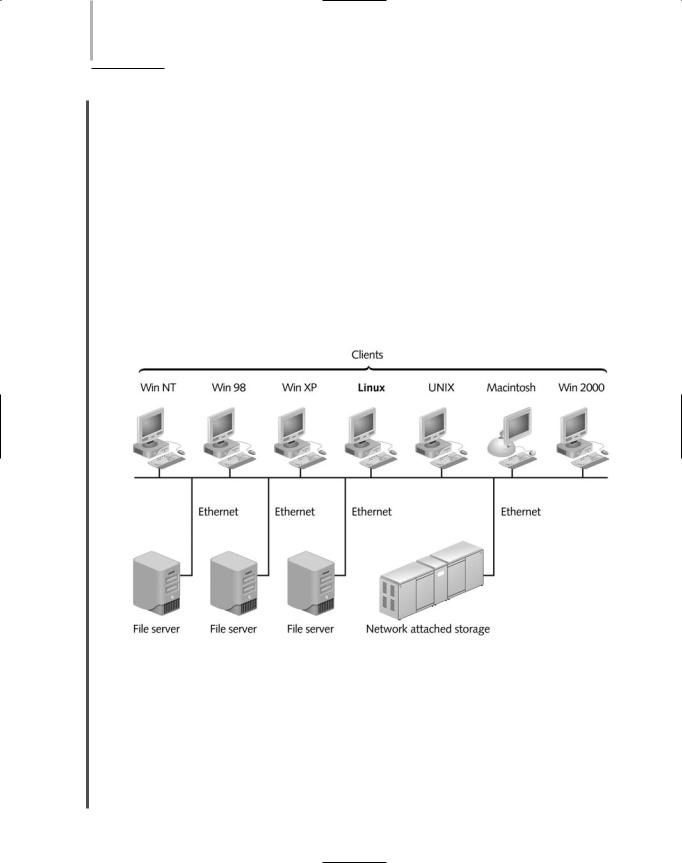
592 Chapter 13 ENSURING INTEGRITY AND AVAILABILITY
NET+ |
Another advantage to using NAS is that it can be easily expanded without interrupting ser- |
3.11vice. For instance, if you purchased a NAS device with 400 GB of disk space, then six months later realized you need three times as much storage space, you could add the new 800 GB of disk space to the NAS device without requiring users to log off the network or taking down the NAS device. After physically installing the new disk space, the NAS device would recognize the added storage and add it to its pool of available reading and writing space. Compare this process to adding hard disk space to a typical server, for which you would have to take the server down, install the hardware, reformat the drive, integrate it with your NOS, and then add directories, files, and permissions as necessary.
Although NAS is a separate device with its own file system, it still cannot communicate directly with clients on the network. When using NAS, the client requests a file from its usual file server over the LAN. The server then requests the file from the NAS device on the network. In response, the NAS device retrieves the file and transmits it to the server, which transmits it to the client. Figure 13-10 depicts how a NAS device physically connects to a LAN.
FIGURE 13-10 Network attached storage on a LAN
NAS is appropriate for enterprises that require not only fault tolerance, but also fast access for their data. For example, an ISP might use NAS to host its customers’ Web pages. Because NAS devices can store and retrieve data for any type of client (providing it can run TCP/IP), NAS is also appropriate for organizations that use a mix of different operating systems on their desktops.
The two major vendors of network attached storage are Network Appliance, Inc., and EMC Corporation. In addition, computer manufacturers such as Hewlett-Packard and Dell offer their own NAS solutions.

FAULT TOLERANCE |
Chapter 13 593 |
NET+ |
Large enterprises that require even faster access to data and larger amounts of storage might |
3.11prefer storage area networks over NAS. You will learn about storage area networks in the following section.
SANs (Storage Area Networks)
As you have learned, NAS devices are separate storage devices, but they still require a file server to interact with other devices on the network. In contrast, SANs (storage area networks) are distinct networks of storage devices that communicate directly with each other and with other networks. In a typical SAN, multiple storage devices are connected to multiple, identical servers. This type of architecture is similar to the mesh topology in WANs, the most faulttolerant type of topology possible. If one storage device within a SAN suffers a fault, data is automatically retrieved from elsewhere in the SAN. If one server in a SAN suffers a fault, another server steps in to perform its functions.
Not only are SANs extremely fault-tolerant, but they are also extremely fast. Much of their speed can be attributed to the use of a special transmission method that relies on fiber-optic media and its own, proprietary protocols. One popular SAN transmission method is called Fibre Channel. Fibre Channel connects devices within the SAN and also connects the SAN to other networks. Fibre Channel is capable of up to 2-Gbps throughput. Because it depends on Fibre Channel, and not on a traditional network transmission method (for example, 100BASE-TX), a SAN is not limited to the speed of the client/server network for which it provides data storage. In addition, because the SAN does not belong to the client/server network, it does not have to contend with the normal overhead of that network, such as broadcasts and acknowledgments. Likewise, a SAN frees the client/server network from the traffic-intensive duties of backing up and restoring data.
Figure 13-11 shows a SAN connected to a traditional Ethernet network.
Another advantage to using SANs is that a SAN can be installed in a location separate from the LAN it serves. Being in a separate location provides added fault tolerance. For example, if an organization’s main offices suffered a fire or flood, the SAN and the data it stores would still be safe. Remote SANs can be kept in an ISP’s data center, which can provide greater security and fault tolerance and also allows an organization to outsource the management of its storage, in case its own staff don’t have the time or expertise.
Like NAS, SANs provide the benefit of being highly scalable. After establishing a SAN, you can easily add further storage and new devices to the SAN without disrupting client/server activity on the network. Finally, SANs use a faster, more efficient method of writing data than do both NAS devices and typical client/server networks.
SANs are not without drawbacks, however. One noteworthy disadvantage to implementing SANs is their high cost. A small SAN can cost $100,000, while a large SAN costs several millions of dollars. In addition, because SANs are more complex than NAS or RAID systems, investing in a SAN means also investing in long hours of training for technical staff before

594 Chapter 13 ENSURING INTEGRITY AND AVAILABILITY
NET+
3.11
FIGURE 13-11 A storage area network
installation, plus significant administration efforts to keep the SAN functional (that is, unless an organization outsources its storage management).
Due to their very high fault tolerance, massive storage capabilities, and speedy data access, SANs are best suited to environments with huge quantities of data that must always be quickly available. Usually, such an environment belongs to a very large enterprise. A SAN is typically used to house multiple databases—for example, inventory, sales, safety specifications, payroll, and employee records for an international manufacturing company.
Data Backup
NET+ |
You have probably heard or even spoken the axiom, “Make regular backups!” A backup is a |
3.12copy of data or program files created for archiving or safekeeping. Without backing up your data, you risk losing everything through a hard disk fault, fire, flood, or malicious or accidental erasure or corruption. No matter how reliable and fault-tolerant you believe your server’s hard disk (or disks) to be, you still risk losing everything unless you make backups on separate media and store them off-site.


596 Chapter 13 ENSURING INTEGRITY AND AVAILABILITY
NET+ |
To help you answer these questions for your own situation, the following sections compare the |
3.12most popular backup media and methods available today.
Optical Media
A simple way to save data is by copying it to optical media, which is a type of media capable of storing digitized data and that uses a laser to write data to it and read data from it. Examples of optical media include all types of CD-ROMs and DVDs. Backing up data to optical media requires only a computer with the appropriate recordable CD or DVD (digital versatile disc) drive and a utility for writing data to the media. Such utilities often come with a computer’s operating system. If not, they are inexpensive and easy to find. A CD-R (compact disc -recordable) can be written to once and can store up to 650 MB of data. A CD-RW (compact disc - rewriteable) also stores up to 650 MB of data, but can be used more than once for backing up data. Besides being simple to create, CD backups are simple to restore from, because their formats are standard and can be read by any computer with a matching drive. However, they suffer from a relatively low storage capacity.
A recordable DVD can hold up to 4.7 GB on one single-layered side, and both sides of the disc can be used. In addition, each side can have up to two layers. Thus, in total, a double-layered, two-sided DVD can store up to 17 GB of data. Recordable DVDs, which are not the same as the video DVD that you rent from a movie store, come in several different formats. DVD manufacturers, such as Dell, Hewlett-Packard, Hitachi, Panasonic, Philips, Pioneer, and Sony, are competing to make their version of the recordable DVD format the most popular. Therefore, if you decide to back up media to DVDs, be sure to standardize on one manufacturer’s equipment.
One potential disadvantage to using CD-R and recordable DVDs for backups is that writing your data to these optical media usually takes longer than saving your data to another type of media, such as a tape or disk drive. In addition, this method requires more human intervention than other backup methods, such as tape backups, which are discussed next.
Tape Backups
In the early days of networking, the most popular method for backing up networked systems was tape backup, or copying data to a magnetic tape. Now this method, which is relatively simple, capable of storing very large amounts of data, and at least partially automated, is making a comeback. Tape backups require the use of a tape drive connected to the network (via a system such as a file server or dedicated, networked workstation), software to manage and perform backups, and, of course, backup media. The tapes used for tape backups resemble small cassette tapes, but they are a higher quality, specially made to reliably store data. Figure 13-12 depicts typical tape backup media.
On a relatively small network, standalone tape drives may be attached to each server. On a large network, one large, centralized tape backup device may manage all of the subsystems’ backups. This tape backup device usually is connected to a computer other than a busy file server to reduce the possibility that backups might cause traffic bottlenecks. Extremely large environments (for example, global manufacturers with several terabytes of inventory and product information to safeguard) may require robots to retrieve and circulate tapes from a tape storage library, also known as a vault, that may be as large as a warehouse.

DATA BACKUP |
Chapter 13 597 |
NET+
3.12
FIGURE 13-12 Example of tape backup media
Examples of tape backup software include Computer Associates’ ARCserve, Dantz Development Corporation’s Retrospect, Hewlett-Packard’s Colorado and OmniBack, NovaStor Corporation’s NovaBACKUP, and Veritas Software Corporation’s Backup Exec. Popular tape drive manufacturers include Exabyte, Hewlett-Packard, IBM, Quantum, Seagate, and Sony. Consult the software and hardware specifications to determine whether a particular backup system is compatible with your network.
External Disk Drives
Another option for backing up data is to use an external disk drive, a storage device that can be attached temporarily to a computer via its USB, PCMCIA, FireWire, or CompactFlash port. External disk drives are also known as removable disk drives. Small external disk drives are frequently used by laptop or desktop computer users to save and share data. These contain circuit boards with attached chips that can store up to 4 GB of data. After being connected to the computer, the external disk drives appear as any other drive, and the user can copy files directly to them. For backing up large amounts of data, however, network administrators are likely to use an external disk drive with backup control features, higher storage capacity, and faster read-write access. One example is the Iomega REV drive, which uses a cartridge containing a small hard disk that can hold up to 90 GB of data. The REV drive operates faster than tape backups or optical media. It can connect to a computer via several bus types and comes with proprietary software that automates the backup, manages the backup schedule, identifies data to be backed up, compresses files, and verifies that the backup completed successfully. Another disk manufacturer, LaCie, makes external drives that can hold up to 500 GB of data.
One advantage to using external disk drives is that they are simple to use. Also, they provide faster data transfer rates than optical media or tape backups. However, on most networks, backing up data to a fixed disk elsewhere on the network, as explained in the next section, is faster.
598 Chapter 13 ENSURING INTEGRITY AND AVAILABILITY
NET+ Network Backups
3.12Instead of saving data to a removable disk or media, you might choose to save data to another place on the network. For example, you could copy all the user data from your organization’s mail server to a different server on the network. If you choose this option, be certain to back up data to a different disk than where it was originally stored, because if the original disk fails, you will lose both the original data and its backup. (Although disk locations on workstations are typically obvious, on a network they might not be.) If your organization operates a WAN, it’s best to back up data to disks at another location. That way, if one location suffers an outage or catastrophe, the data will remain safe at the other location on the WAN. A sophisticated network backup solution would use software to automate and manage backups and save data to a SAN or NAS storage device. Most network operating systems provide utilities for automating and managing network backups.
If your organization does not have a WAN or a high-end storage solution, you might consider online backups. An online backup saves data across the Internet to another company’s storage array. Usually, online backup providers require you to install their client software. You also need a (preferably high-speed) connection to the Internet. Online backups implement strict security measures to protect the data in transit, as the information must traverse public carrier links. Most online backup providers allow you to retrieve your data at any time of day or night, without calling a technical support number. Both the backup and restoration processes are entirely automated. In case of a disaster, the online backup company may offer to create CD-ROMs containing your servers’ data. When evaluating an online backup provider, you should test its speed, accuracy, security, and, of course, the ease with which you can recover the backed-up data. Be certain to test the service before you commit to a long-term contract for online backups.
Backup Strategy
After selecting the appropriate tool for performing your servers’ data backups, devise a backup strategy to guide you and your colleagues in performing reliable backups that provide maximum data protection. This strategy should be documented in a common area where all IT staff can access it. The strategy should address at least the following questions:
What data must be backed up?
What kind of rotation schedule will backups follow?
At what time of day or night will the backups occur?
How will you verify the accuracy of the backups?
Where and for how long will backup media be stored?
Who will take responsibility for ensuring that backups occurred?
How long will you save backups?
Where will backup and recovery documentation be stored?
Different backup methods provide varying levels of certainty and corresponding labor and cost. An important concept to understand before learning about different backup methods is the

DATA BACKUP |
Chapter 13 599 |
NET+ |
archive bit. An archive bit is a file attribute that can be checked (or set to “on”) or unchecked |
3.12(or set to “off ”) to indicate whether the file must be archived. When a file is created or changed, the operating system automatically sets the file’s archive bit to “on.” Various backup methods use the archive bit in different ways to determine which files should be backed up, as described in the following list:
Full backup—All data on all servers is copied to storage media, regardless of whether the data is new or changed. After backing up the files, a full backup unchecks—or turns “off ”—the files’ archive bits.
Incremental backup—Only data that has changed since the last full or incremental backup is copied to a storage medium. An incremental backup saves only files whose archive bit is checked. After backing up files, an incremental backup unchecks the archive bit for every file it has saved.
Differential backup—Only data that has changed since the last backup is copied to a storage medium, and that information is then marked for subsequent backup, regardless of whether it has changed. In other words, a differential backup does not uncheck the archive bits for files it backs up.
When managing network backups, you need to determine the best possible backup rotation scheme—you need to create a plan that specifies when and how often backups will occur. The aim of a good backup rotation scheme is to provide excellent data reliability without overtaxing your network or requiring a lot of intervention. For example, you might think that backing up your entire network’s data every night is the best policy because it ensures that everything is completely safe. But what if your network contains 2 TB of data and is growing by 100 GB per month? Would the backups even finish by morning? How many tapes would you have to purchase? Also, why should you bother backing up files that haven’t changed in three weeks? How much time will you and your staff need to devote to managing the tapes? How would the transfer of all of the data affect your network’s performance? All of these considerations point to a better alternative than the “tape-a-day” solution—that is, an option that promises to maximize data protection but reduce the time and cost associated with backups.
When planning your backup strategy, you can choose from several standard backup rotation schemes. The most popular of these schemes, called grandfather-father-son, uses daily (son), weekly (father), and monthly (grandfather) backup sets. As depicted in Figure 13-13, in the grandfather-father-son scheme, three types of backups are performed each month: daily incremental (every Monday through Thursday), weekly full (every Friday), and monthly full (last day of the month).
In this scheme, backup tapes are reused regularly. For example, week 1’s Monday tape also serves as week 2’s and week 3’s Monday tape. One day each week, a full backup, called “father,” is recorded in place of an incremental one and labeled for the week to which it corresponds—for example, “week 1,” “week 2,” and so on. This “father” tape is reused monthly—for example, October’s week 1 tape is reused for November’s week 1 tape. The final set of media is labeled “month 1,” “month 2,” and so on, according to which month of the quarter the tapes are used. This “grandfather” medium records full backups on the last business day of each month and is

600 Chapter 13 ENSURING INTEGRITY AND AVAILABILITY
NET+
3.12
FIGURE 13-13 The “grandfather-father-son” backup rotation scheme
reused quarterly. Each of these media may consist of a single tape or a set of tapes, depending on the amount of data involved. A total of 12 media sets are required for this basic rotation scheme, allowing for a history of two to three months.
After you have determined your backup rotation scheme, you should ensure that backup activity is recorded in a backup log. Information that belongs in a backup log includes the backup date, tape identification (day of week or type), type of data backed up (for example, Accounting Department spreadsheets or a day’s worth of catalog orders), type of the backup (full, incremental, or differential), files that were backed up, and site at which the tape is stored. Having this information available in case of a server failure greatly simplifies data recovery.
Finally, after you begin to back up network data, you should establish a regular schedule of verification. From time to time (depending on how often your data change and how critical the information is), you should attempt to recover some critical files from your backup media. Many network administrators attest that the darkest hour of their career was when they were asked to retrieve critical files from a backup tape, and found that no backup data existed because their backup system never worked in the first place!
Disaster Recovery
NET+ |
Disaster recovery is the process of restoring your critical functionality and data after an enter- |
3.12prise-wide outage that affects more than a single system or a limited group of users. Disaster recovery must take into account the possible extremes, rather than relatively minor outages, failures, security breaches, or data corruption.
DISASTER RECOVERY |
Chapter 13 601 |
NET+ Disaster Recovery Planning
3.12A disaster recovery plan accounts for the worst-case scenarios, from a far-reaching hurricane to a military or terrorist attack. It should identify a disaster recovery team (with an appointed coordinator) and provide contingency plans for restoring or replacing computer systems, power, telephony systems, and paper-based files. Sections of the plan related to computer systems should include the following:
Contact names and phone and pager numbers for emergency coordinators who will execute the disaster recovery response in case of disaster, as well as roles and responsibilities of other staff.
Details on which data and servers are being backed up, how frequently backups occur, where backups are kept (off-site), and, most important, how backed up data can be recovered in full.
Details on network topology, redundancy, and agreements with national service carriers, in case local or regional vendors fall prey to the same disaster.
Regular strategies for testing the disaster recovery plan.
A plan for managing the crisis, including regular communications with employees and customers. Consider the possibility that regular communications modes (such as phone lines) might be unavailable.
Having a comprehensive disaster recovery plan lessens the risk of losing critical data in case of extreme situations, and also makes potential customers and your insurance providers look more favorably on your organization.
Disaster Recovery Contingencies
An organization can choose from several options for recovering from a disaster. The options vary by the amount of employee involvement, hardware, software, planning, and investment each involves. They also vary according to how quickly they will restore network functionality in case a disaster occurs. As you would expect, every contingency necessitates a site other than the building where the network’s main components normally reside. An organization might maintain its own disaster recovery sites—for example, by renting office space in a different city—or contract with a company that specializes in disaster recovery services to provide the site. Disaster recovery contingencies are commonly divided into three categories: cold site, warm site, and hot site.
A cold site is a place where the computers, devices, and connectivity necessary to rebuild a network exist, but they are not appropriately configured, updated, or connected. Therefore, restoring functionality from a cold site could take a long time. For example, suppose your small business network consists of a file and print server, mail server, backup server, Internet gateway/DNS/DHCP server, twenty-five clients, four printers, a router, a switch, two access points, and a connection to your local ISP. At your cold site, you might store four server computers on
