
Network Plus 2005 In Depth
.pdf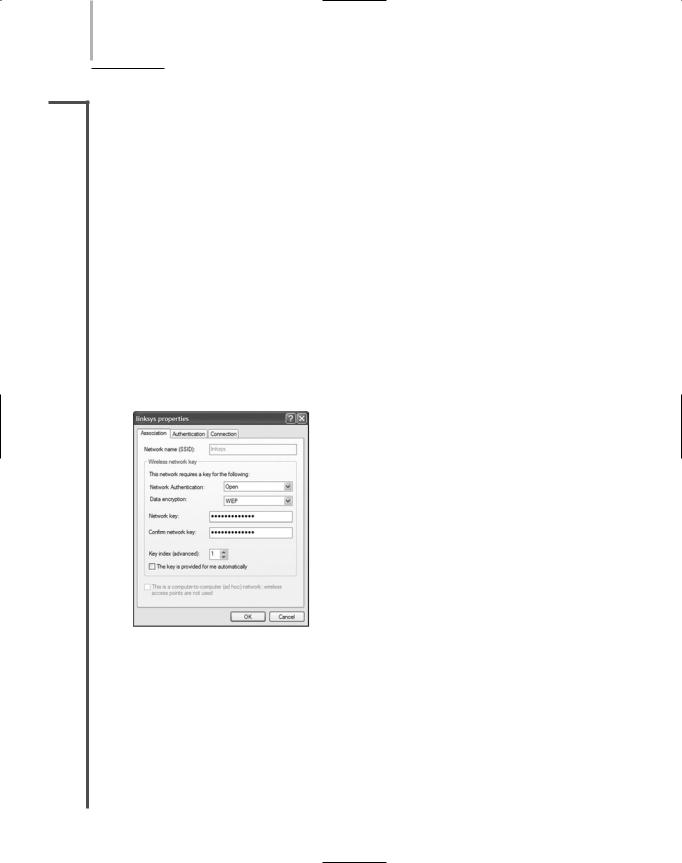
652 Chapter 14 NETWORK SECURITY
NET+ To edit or add a WEP key for a wireless connection on your Windows XP client:
2.171. Click Start, and then click My Network Places. The My Network Places window opens.
2.Under Network Tasks, click View network connections. The Network Connections window opens.
3.Right-click the Wireless Network Connection icon, and then choose Properties from the shortcut menu. The Wireless Network Connection Properties dialog box opens.
4.Select the Wireless Networks tab.
5.Under Preferred networks, click the network (or the SSID) for which you want to establish a WEP key, then click Properties. Your wireless network’s properties dialog box opens, with the Association tab selected by default.
6.In the drop-down menu next to Data encryption, choose WEP.
7.Enter your WEP key in the Network key text box. You must enter precisely the same key that your AP is configured to use, in either ASCII or hexadecimal form.
8.Enter your WEP key again in the Confirm network key text box. As shown in Figure 14-12, the network key will not appear on the screen, so that anyone peering over your shoulder cannot discover it.
FIGURE 14-12 Entering a WEP key in the wireless network properties dialog box
9.Click OK to save your changes and close the wireless network properties dialog box.
10.Click OK again to close the Wireless Network Connection Properties dialog box.
The first implementation of WEP allowed for 64-bit network keys, which, as you know, are not highly secure. Consequently, many early wireless networks were susceptible to brute force attacks, even though they used the best possible encryption. Current versions of WEP allow for more secure, 128-bit network keys. Still, WEP’s use of the shared key for authenticating all users and for exchanging data makes it more susceptible to discovery than a dynamically
CHAPTER SUMMARY Chapter 14 653
NET+ |
generated, random, or single-use key. Moreover, because WEP operates in the Physical and |
2.17Data Link layers of the OSI Model, it does not offer end-to-end data transmission security. A better wireless security technique is 802.11i, which is discussed next.
IEEE 802.11i and WPA (Wi-Fi Protected Access)
Because of WEP’s relative insecurity, IEEE devised a new wireless security protocol, called 802.11i, that uses EAP (discussed previously in this chapter) with a strong encryption scheme and that dynamically assigns every transmission its own key. As you can imagine, EAP makes logging on to a wireless network more complex than it is with WEP. In 802.11i, a wireless station first issues a request to the AP. The AP acts as a proxy between the remote access server and station until the station has successfully authenticated with a remote access server. Meanwhile, the AP prevents any direct exchange of data between the two. After obtaining data from an unknown station, the AP repackages the data and then transmits it to the remote access server. It also repackages data from the remote access server before issuing it to the station. Thus, 802.11i requires mutual authentication—the station authenticates with the remote access server, and also, the remote access server authenticates with the station. After mutual authentication, the remote access server instructs the AP to allow traffic from the client into the network without first having to be repackaged. Next, the client and server agree on the encryption key that they will use with the encryption scheme. Following that, they exchange data that has been encrypted through the mutually agreed-upon method. 802.11i specifies the AES encryption method and mixes each packet in a data stream with a different key. Because of its impressive security, 802.11i is poised to replace the less-secure WEP as the preferred means for protecting wireless transmissions from intruders.
WPA (Wi-Fi Protected Access) is a subset of the 802.11i standard endorsed by the Wi-Fi Alliance, an international nonprofit organization dedicated to ensuring the interoperability of 802.11-capable devices. In fact, the Wi-Fi Alliance released WPA before 802.11i was ratified to quickly provide a more secure alternative to WEP. In WPA, authentication follows the same mechanism specified in 802.11i. The main difference is that WPA specifies RC4 encryption rather than AES. Since the 802.11i standard was approved, the Wi-Fi Alliance has released an updated version called WPA2. WPA2 includes support for the previously released WPA protocol. In all other ways, it is identical to 802.11i.
To support 802.11i, WPA, and WPA2, most currently installed APs and wireless NICs require driver, if not firmware, upgrades.
Chapter Summary
Every organization should assess its security risks by conducting a security audit, at least annually and preferably quarterly. For each threat, your security audit should rate the severity of its potential consequences, as well as its likelihood.

654Chapter 14 NETWORK SECURITY
One of the most common methods by which an intruder gains access to a network is to simply ask a user for his password. This strategy is commonly called social engineering because it involves manipulating social relationships to gain access.
Security risks that a network administrator must guard against include: incorrectly configuring user accounts or groups, and their privileges; overlooking security flaws in topology or hardware configuration; overlooking security flaws in operating system or application configuration; improperly documenting or communicating security policies; and leaving system settings (such as a program’s administrator user name or the administrator’s password on a router) at their default values.
Some risks inherent in network transmission and design include: leased public lines that may allow for eavesdropping; hubs that broadcast traffic over the entire segment, making transmissions more vulnerable to sniffing; unused hub, router, or server ports that can be exploited and accessed by hackers if not disabled; a router’s configuration port, accessible by Telnet, that may not be adequately secured; routers that may not be properly configured to mask internal subnets; modems attached to network devices that may be configured to accept incoming calls; and dial-in access servers used by telecommuting or remote staff that may not be carefully secured and monitored.
Some risks pertaining to networking protocols and software include the following: inherent TCP/IP security flaws; trust relationships between one server and another; NOS “back doors” or security flaws; an NOS that allows server operators to exit to a command prompt; administrators who accept default operating system security; and transactions that take place between applications left open to interception.
A security policy identifies an organization’s security goals, risks, levels of authority, designated security coordinator and team members, responsibilities for each team member, responsibilities for each employee, and strategies for addressing security breaches.
A security policy should: ensure that authorized users have appropriate access to the resources they need; prevent unauthorized users from gaining access to the network and its resources; protect sensitive data from unauthorized access; prevent accidental damage to hardware or software; prevent intentional damage to hardware or software; create an environment in which the network and systems can withstand and quickly recover from any type of threat; and communicate each employee’s responsibilities with respect to maintaining data integrity.
At the very least, computer rooms should allow access only to authorized networking personnel. If computer rooms or wiring closets remain unlocked, intruders may easily enter and steal equipment, or sabotage software and hardware.
A firewall is a specialized device (typically a router, but possibly only a desktop computer running special software) that selectively filters or blocks traffic between networks. It may be placed between two interconnected private networks or, more typically, between a private network and a public network (such as the Internet).

CHAPTER SUMMARY Chapter 14 655
The most common form of firewall is a packet-filtering firewall, which examines the header of every packet of data that it receives to determine whether that type of packet is authorized to continue to its destination.
A proxy service is a software application on a network host that acts as an intermediary between the external and internal networks, screening all incoming and outgoing traffic. The host that runs the proxy service is known as a proxy server. A proxy server appears to external machines as a network server, but it is actually another filtering device for the internal LAN.
A secure remote access server package includes at least the following features: user name and password authentication; the ability to log all dial-up connections, their sources, and their connection times; the ability to perform callbacks to users who initiate connections; and centralized management of dial-up users and their rights on the network.
Every NOS provides at least some security by allowing you to limit users’ access to files and directories on the network. In addition, network administrators can constrain how those with different types of user IDs can use the network by setting restrictions on, for example, time of day, total time logged on, source address, and number of unsuccessful logon attempts.
Choosing secure passwords is one of the easiest and least expensive ways to guard against unauthorized access. The following guidelines for selecting passwords should be part of your organization’s security policy: Do not use the familiar types of passwords; do not use any word that can be found in a dictionary; make the password longer than eight characters; choose a combination of letters and numbers; add special characters, such as exclamation marks or hyphens, if allowed; use uppercase and lowercase letters, if the password is case sensitive; do not write down your password or share it with others; do not reuse passwords; and change your password at least every 60 days.
Encryption is the use of an algorithm to scramble data into a format that can be read only by reversing the algorithm—or decrypting the data—to keep the information private. Many forms of encryption exist, with some being more secure than others.
The most popular kind of encryption algorithm weaves a key (a random string of characters) into the original data’s bits, sometimes several times in different sequences, to generate a unique data block. The longer the key, the less easily the encrypted data can be decrypted by an unauthorized system.
Key encryption comes in two forms: public and private key encryption. Popular private (symmetric) key encryption algorithms include DES (Data Encryption Standard), Triple DES (3DES), and AES (Advanced Encryption Standard). Popular public (asymmetric) key encryption algorithms include Diffie-Hellman, RSA, and RC4.

656Chapter 14 NETWORK SECURITY
Popular methods of encryption include PGP (Pretty Good Privacy), SSL (Secure Sockets Layer ), SSH (Secure Shell ) and OpenSSH, and IPSec (Internet Protocol Security). IPSec is the protocol used on many modern VPNs.
SCP (Secure CoPy) and SFTP (Secure File Transfer Protocol) are ways of copying files securely via SSH or OpenSSH.
Authentication protocols used with PPP connections include RADIUS (Remote Authentication Dial-In User Service), TACACS (Terminal Access Controller Access Control System), PAP (Password Authentication Protocol), CHAP (Challenge Handshake Authentication Protocol), and MS-CHAP (Microsoft Challenge Handshake Authentication Protocol). Other authentication protocols include EAP (Extensible Authentication Protocol) and Kerberos.
Wireless networks can use the WEP (Wired Equivalent Privacy) method of encrypting data in transit between stations and APs. WEP allows for keys as long as 128 bits. However, because WEP uses the same key for all stations attaching to an AP and for all transmissions, it is not very secure.
A better wireless security solution than WEP is provided by IEEE’s 802.11i standard. In 802.11i, the EAP authentication method is combined with AES encryption. Also, each 802.11i transmission is dynamically assigned its own key for encryption.
The Wi-Fi Alliance has released two wireless security standards: WPA and WPA2. WPA follows the same authentication and encryption processes as 802.11i, but uses RC4 encryption. WPA2 is identical to 802.11i, but provides backward compatibility for clients running WPA.
Key Terms
3DES—See Triple DES.
802.11i—The IEEE standard for wireless network encryption and authentication that uses the EAP authentication method, strong encryption, and dynamically assigned keys, which are different for every transmission. 802.11i specifies AES encryption and weaves a key into each packet.
Advanced Encryption Standard—See AES.
AES (Advanced Encryption Standard)—A private key encryption algorithm that weaves keys of 128, 160, 192, or 256 bits through data multiple times. The algorithm used in the most popular form of AES is known as Rijndael. AES has replaced DES in situations such as military communications, which require the highest level of security.
AH (authentication header)—In the context of IPSec, a type of encryption that provides authentication of the IP packet’s data payload through public key techniques.
application gateway—See proxy server.

KEY TERMS |
Chapter 14 657 |
Application layer gateway—See proxy server.
AS (authentication service)—In Kerberos terminology, the process that runs on a KDC (key distribution center) to initially validate a client who’s logging on. The authentication service issues session keys to the client and the service the client wants to access.
asymmetric encryption—A type of encryption (such as public key encryption) that uses a different key for encoding data than is used for decoding the ciphertext.
authentication header—See AH.
authentication protocol—A set of rules that governs how servers authenticate clients. Several types of authentication protocols exist.
authentication service—See AS.
authenticator—In Kerberos authentication, the user’s time stamp encrypted with the session key. The authenticator is used to help the service verify that a user’s ticket is valid.
bio-recognition access—A method of authentication in which a device scans an individual’s unique physical characteristics (such as the color patterns in his iris or the geometry of his hand) to verify the user’s identity.
brute force attack—An attempt to discover an encryption key or password by trying numerous possible character combinations. Usually, a brute force attack is performed rapidly by a program designed for that purpose.
challenge—A random string of text issued from one computer to another in some forms of authentication. Used, along with the password (or other credential), in a response to verify the computer’s credentials.
Challenge Handshake Authentication Protocol—See CHAP.
CHAP (Challenge Handshake Authentication Protocol)—An authentication protocol that operates over PPP and that requires the authenticator to take the first step by offering the other computer a challenge. The requestor responds by combining the challenge with its password, encrypting the new string of characters and sending it to the authenticator. The authenticator matches to see if the requestor’s encrypted string of text matches its own encrypted string of characters. If so, the requester is authenticated and granted access to secured resources.
ciphertext—The unique data block that results when an original piece of data (such as text) is encrypted (for example, by using a key).
client_hello—In the context of SSL encryption, a message issued from the client to the server that contains information about what level of security the client’s browser is capable of accepting and what type of encryption the client’s browser can decipher (for example, RSA or DiffieHellman). The client_hello message also establishes a randomly generated number that uniquely identifies the client, plus another number that identifies the SSL session.
cracker—A person who uses his knowledge of operating systems and utilities to intentionally damage or destroy data or systems.

658 Chapter 14 NETWORK SECURITY
Data Encryption Standard—See DES.
denial-of-service attack—A security attack caused by a deluge of traffic that disables the victimized system.
DES (Data Encryption Standard)—A popular private key encryption technique that was developed by IBM in the 1970s.
dictionary attack—A technique in which attackers run a program that tries a combination of a known user ID and, for a password, every word in a dictionary to attempt to gain access to a network.
Diffie-Hellman—The first commonly used public, or asymmetric, key algorithm. Diffie-Hell- man was released in 1975 by its creators, Whitfield Diffie and Martin Hellman.
digital certificate—A password-protected and encrypted file that holds an individual’s identification information, including a public key and a private key. The individual’s public key is used to verify the sender’s digital signature, and the private key allows the individual to log on to a third-party authority who administers digital certificates.
DNS spoofing—A security attack in which an outsider forges name server records to falsify his host’s identity.
EAP (Extensible Authentication Protocol)—A Data Link layer protocol defined by the IETF that specifies the dynamic distribution of encryption keys and a pre-authentication process in which a client and server exchange data via an intermediate node (for example, an access point on a wireless LAN). Only after they have mutually authenticated can the client and server exchange encrypted data. EAP can be used with multiple authentication and encryption schemes.
Encapsulating Security Payload—See ESP.
encryption—The use of an algorithm to scramble data into a format that can be read only by reversing the algorithm—decrypting the data—to keep the information private. The most popular kind of encryption algorithm weaves a key into the original data’s bits, sometimes several times in different sequences, to generate a unique data block.
ESP (Encapsulating Security Payload)—In the context of IPSec, a type of encryption that provides authentication of the IP packet’s data payload through public key techniques. In addition, ESP also encrypts the entire IP packet for added security.
Extensible Authentication Protocol—See EAP.
flashing—A security attack in which an Internet user sends commands to another Internet user’s machine that cause the screen to fill with garbage characters. A flashing attack causes the user to terminate her session.
hacker—A person who masters the inner workings of operating systems and utilities in an effort to better understand them. A hacker is distinguished from a cracker in that a cracker attempts to exploit a network’s vulnerabilities for malicious purposes.

KEY TERMS |
Chapter 14 659 |
handshake protocol—One of several protocols within SSL, and perhaps the most significant. As its name implies, the handshake protocol allows the client and server to authenticate (or introduce) each other and establishes terms for how they securely exchange data during an SSL session.
HTTP over Secure Sockets Layer—See HTTPS.
HTTP Secure—See HTTP over Secure Sockets Layer.
HTTPS (HTTP over Secure Sockets Layer)—The URL prefix that indicates that a Web page requires its data to be exchanged between client and server using SSL encryption. HTTPS uses the TCP port number 443, rather than port 80 (the port that normal HTTP uses).
IKE (Internet Key Exchange)—The first phase of IPSec authentication, which accomplishes key management. IKE is a service that runs on UDP port 500. After IKE has established the rules for the type of keys two nodes use, IPSec invokes its second phase, encryption.
Internet Key Exchange—See IKE.
Internet Protocol Security—See IPSec.
IPSec (Internet Protocol Security)—A Layer 3 protocol that defines encryption, authentication, and key management for TCP/IP transmissions. IPSec is an enhancement to IPv4 and native to IPv6. IPSec is unique among authentication methods in that it adds security information to the header of all IP packets.
IP spoofing—A security attack in which an outsider obtains internal IP addresses, then uses those addresses to pretend that he has authority to access a private network from the Internet.
KDC (Key Distribution Center)—In Kerberos terminology, the server that runs the authentication service and the Ticket-granting service to issue keys and tickets to clients.
Kerberos—A cross-platform authentication protocol that uses key encryption to verify the identity of clients and to securely exchange information after a client logs on to a system. It is an example of a private key encryption service.
key—A series of characters that is combined with a block of data during that data’s encryption. To decrypt the resulting data, the recipient must also possess the key.
Key Distribution Center—See KDC.
key management—The method whereby two nodes using key encryption agree on common parameters for the keys they will use to encrypt data.
key pair—The combination of a public and private key used to decipher data that was encrypted using public key encryption.
Microsoft Challenge Handshake Authentication Protocol—See MS-CHAP.
Microsoft Challenge Handshake Authentication Protocol, version 2—See MS-CHAPv2.

660 Chapter 14 NETWORK SECURITY
MS-CHAP (Microsoft Challenge Handshake Authentication Protocol)—An authentication protocol offered by Microsoft with its Windows clients and servers. Similar to CHAP, MS-CHAP uses a three-way handshake to verify a client’s credentials and encrypts passwords with a challenge text.
MS-CHAPv2 (Microsoft Challenge Authentication Protocol, version 2)—An authentication protocol provided with Windows XP, 2000, and Server 2003 operating systems that follows the CHAP model, but uses stronger encryption, uses different encryption keys for transmission and reception, and requires mutual authentication between two computers.
mutual authentication—An authentication scheme in which both computers verify the credentials of each other.
network key—A key (or character string) required for a wireless station to associate with an access point using WEP.
OpenSSH—An open source version of the SSH suite of protocols.
packet-filtering firewall—A router that operates at the Data Link and Transport layers of the OSI Model, examining the header of every packet of data that it receives to determine whether that type of packet is authorized to continue to its destination. Packet-filtering firewalls are also called screening firewalls.
PAP (Password Authentication Protocol)—A simple authentication protocol that operates over PPP. Using PAP, a client issues its credentials in a request to authenticate, and the server responds with a confirmation or denial of authentication after comparing the credentials to those in its database. PAP is not very secure and is therefore rarely used on modern networks.
Password Authentication Protocol—See PAP.
PGP (Pretty Good Privacy)—A key-based encryption system for e-mail that uses a two-step verification process.
port forwarding—The process of redirecting traffic from its normally assigned port to a different port, either on the client or server. In the case of using SSH, port forwarding can send data exchanges that are normally insecure through encrypted tunnels.
Pretty Good Privacy—See PGP.
principal—In Kerberos terminology, a user or client.
private key encryption—A type of key encryption in which the sender and receiver use a key to which only they have access. DES (data encryption standard), which was developed by IBM in the 1970s, is a popular example of a private key encryption technique. Private key encryption is also known as symmetric encryption.
proxy—See proxy server.
proxy server—A network host that runs a proxy service. Proxy servers may also be called gateways.

KEY TERMS |
Chapter 14 661 |
proxy service—A software application on a network host that acts as an intermediary between the external and internal networks, screening all incoming and outgoing traffic and providing one address to the outside world, instead of revealing the addresses of internal LAN devices.
public key encryption—A form of key encryption in which data is encrypted using two keys: One is a key known only to a user, and the other is a key associated with the user and can be obtained from a public source, such as a public key server. Some examples of public key algorithms include RSA (named after its creators, Rivest, Shamir, and Adleman), Diffie-Hellman, and Elliptic-curve cryptography. Public key encryption is also known as asymmetric encryption.
public key server—A publicly available host (such as an Internet host) that provides free access to a list of users’ public keys (for use in public key encryption).
RADIUS (Remote Authentication Dial-In User Service)—A protocol that runs over UDP and provides centralized network authentication and accounting for multiple users. RADIUS is commonly used with dial-up networking, VPNs, and wireless connections.
RADIUS server—A server that offers centralized authentication services to a network’s access server, VPN server, or wireless access point via the RADIUS protocol.
RC4—An asymmetric key encryption technique that weaves a key with data multiple times as a computer issues the stream of data. RC4 keys can be as long as 2048 bits. In addition to being highly secure, RC4 is fast.
Remote Authentication Dial-In User Service—See RADIUS.
Rijndael—The algorithm used for AES encryption.
RSA—An encryption algorithm that creates a key by randomly choosing two large prime numbers and multiplying them together. RSA is named after its creators, Ronald Rivest, Adi Shamir, and Leonard Adleman. RSA was released in 1977, but remains popular today for e- commerce transactions.
SCP (Secure CoPy)—A method for copying files securely between hosts. SCP is part of the OpenSSH package, which comes with most modern UNIX-type of operating systems. Thirdparty SCP applications are available for Windows-based computers.
screening firewall—See packet-filtering firewall.
Secure CoPy—See SCP.
Secure Shell—See SSH.
Secure Sockets Layer—See SSL.
security audit—An assessment of an organization’s security vulnerabilities. A security audit should be performed at least annually and preferably quarterly—or sooner if the network has undergone significant changes. For each risk found, it should rate the severity of a potential breach, as well as its likelihood.
