
Cisco Secure VPN Exam Certification Guide - Cisco press
.pdf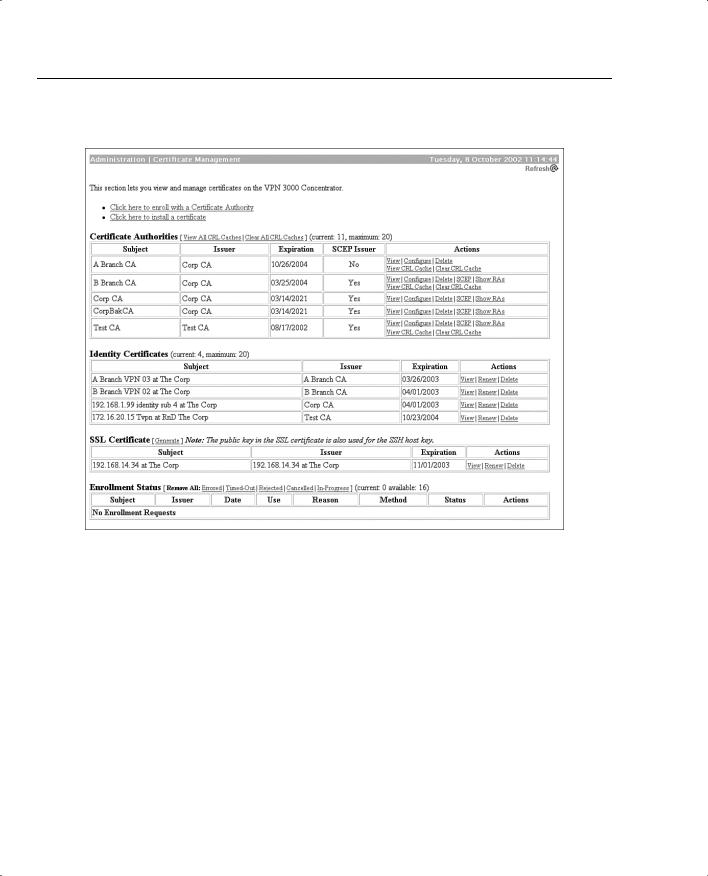
238 Chapter 5: Configuring Cisco VPN 3000 for Remote Access Using Digital Certificates
Figure 5-16 Administration | Certificate Management
You can also select to enable CRL caching from the Administration | Certificate Management | Configure CA Certificate screen. With caching enabled, the first time the VPN concentrator retrieves a CRL from a distribution point, it stores the CRL in volatile memory. The concentrator looks first in memory for the CRL it needs. If the CRL is found in memory, the concentrator checks for the subject certificate’s serial number. The VPN concentrator looks for a new CRL if the cached CRL has expired or if the refresh time you established has elapsed. Caching can save network resources on busy networks and can minimize timeout problems during IKE negotiations while waiting to retrieve the latest CRL.

Digital Certificate Support Through the VPN 3000 Concentrator Series Manager 239
Figure 5-17 Administration | Certificate Management | Configure CA Certificate
IKE Configuration
Now that you have the digital certificate portion of the VPN concentrator configured, you must set up the concentrator to use the certificates during IKE negotiations. You need to tweak just two places to use digital certificates: the IKE proposal that you will use and the IPSec SA that you will use.
Figure 5-18 shows the screen used to modify IKE proposal configurations. You can modify an existing proposal, as is shown here, or create a new one.

240 Chapter 5: Configuring Cisco VPN 3000 for Remote Access Using Digital Certificates
Figure 5-18 Configuration | System | Tunneling Protocols | IPSec | IKE Proposals | Modify
Notice the shaded Authentication Mode area on this form. That is the field used to determine whether you are using preshared keys, digital certificates, or some other authentication method.
Click the Authentication Mode drop-down menu button, and choose RSA Digital Certificate from the available options. Include the name of this IKE proposal into the IPSec Security Association that you will be using. Figure 5-19 shows the IPSec SA screen.
Notice the highlighted area in the IKE Parameters section at the bottom of the screen. Select the identity certificate in the Digital Certificate field that you want this IPSec SA to use during IKE Phase 1 negotiations. The drop-down box displays the certificates that you have installed on the VPN concentrator. You can then select from these certificates.
In this same area, enter the name of the IKE proposal that you modified on the IPSec IKE Proposals screen in Figure 5-18. You can select this proposal from the drop-down box.
You also have the option of which certificates to send to the peer during negotiations. You can select to send only the identity certificate (default action) or to send the entire certificate chain, which would be the identity, root, and any subordinate CA certificates the VPN concentrator holds.
That concludes the configuration of the VPN concentrator to support digital certificates. The next step is to configure the VPN Client for digital certificate support, as described in the next section.

Configuring the VPN Client for CA Support 241
Figure 5-19 Configuration | Policy Management | Traffic Management | Security Associations | Modify
Configuring the VPN Client for CA Support
18 Configuring the Cisco VPN 3000 Concentrator Series for CA support
Because you will now be using digital certificates for authentication on the VPN concentrator, you must modify the configuration of your user’s VPN Client connection entries from using a preshared key to using a digital certificate. All your clients must have a root certificate and an identity certificate installed in the browser application of their VPN client system.
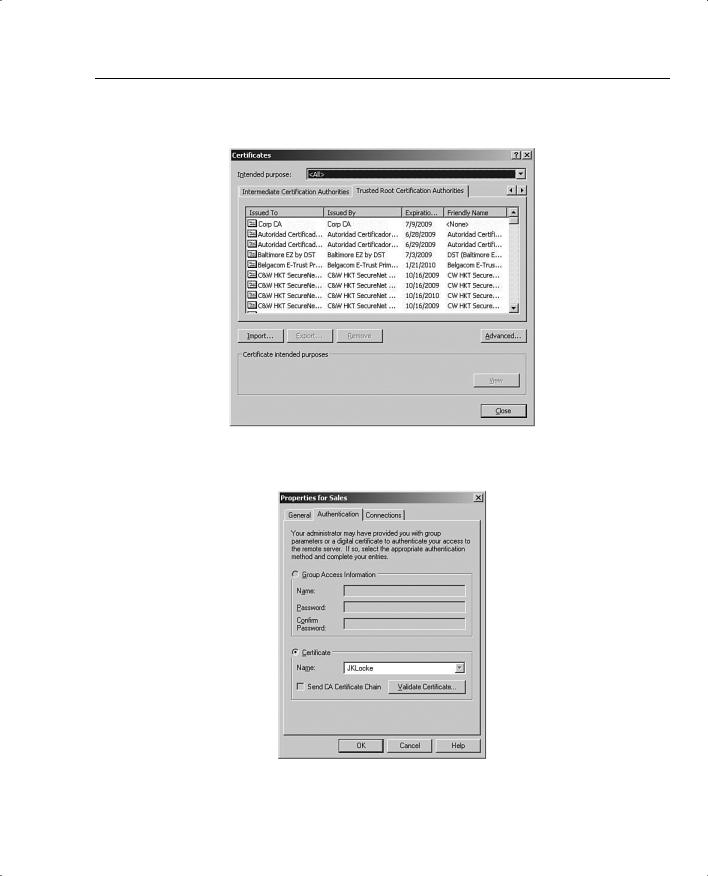
As the system administrator, you can manually enroll each of your users and copy the identity certificate and the issuing root CA certificate for them to floppy disk. These can then be imported into the browser. Figures 5-20 and 5-21 show the user’s personal identity certificate and the root certificate in Microsoft’s Internet Explorer.

242 Chapter 5: Configuring Cisco VPN 3000 for Remote Access Using Digital Certificates
NOTE When you generate the PKCS #10 certificate request for your users, the OU field must match the group name you defined for them on the VPN concentrator. You might also need to mark the keys as exportable. The enrollment process is not depicted in Figures 5-20 and 5-21.
To complete the process, modify the VPN connection in the VPN Client software to use the identity certificate shown in Figure 5-20. To do that, start the VPN Client by choosing Start,
Programs, Cisco Systems VPN Client, VPN Dialer. Select the correct connection entry, and click the Options button. Select Properties from the Options menu, and click the Authentication tab, as shown in Figure 5-22.
Now that you have digital certificates installed, the Certificate area is no longer grayed out. Select the Certificate button, and then select your identity certificate from the Name drop-down box.
You can check the Send CA Certificate Chain option to have your VPN Client send the identity, subordinate CA, and root certificates instead of just the identity certificate during IKE negotiations. This option is disabled by default.
Figure 5-20 Personal Certificates—Internet Explorer
Configuring the VPN Client for CA Support 243
Figure 5-21 Trusted Root Certification Authorities—Internet Explorer
Figure 5-22 Authentication Selection—VPN Client

244 Chapter 5: Configuring Cisco VPN 3000 for Remote Access Using Digital Certificates
You can also check to see if the certificate is still valid by clicking the Validate Certificate button. A report is generated that lets you know if the certificate is still valid.
Once you have completed the changes on the Authentication tab, click OK to save the changes and return to the VPN Dialer screen, where you can now connect to the VPN concentrator using digital certificates instead of preshared keys.

X.509 Identity Certificate Fields 245
Foundation Summary
The Foundation Summary is a collection of tables and figures that provides a convenient review of many key concepts in this chapter. For those of you who are already comfortable with the topics in this chapter, this summary could help you recall a few details. For those who just read this chapter, this review should help solidify some key facts. For anyone doing his or her final preparation before the exam, these tables and figures can be a convenient way to review the material the day before the exam.
PKCS #10 Certificate Request Fields
The following list outlines the VPN concentrator’s PKCS #10 Certificate Request fields:
•
•
•
•
•
•
•
•
Common Name (CN)
Organization Unit (OU)
Organization (O)
Locality (L)
State/Province (SP)
Country (C)
Subject Alternative Name (FQDN)
Key Size
X.509 Identity Certificate Fields
The following list outlines the X.509 Identity Certificate fields:
•
•
•
•
•
•
•
•
•
Certificate Format Version
Certificate Serial Number
Signature Algorithm
Issuer’s X.500 Distinguished Name
Validity Period
Subject’s X.500 Distinguished Name
Subject’s Public Key Information
Extensions
CA Signature

246 Chapter 5: Configuring Cisco VPN 3000 for Remote Access Using Digital Certificates
Types of Digital Certificates
The types of digital certificates are as follows:
•Root—Identifies the overarching authority in the CA network.
•Identity—Required by every device, these are signed by either the root CA or by a subordinate CA. The root CA must self-sign its own identity certificate.
•Issuing (or subordinate)—Serves the same purpose as the root certificate, but is issued by a subordinate CA instead of the root CA. Subordinate CAs do not self-sign their own identity certificate.
Types of CA Organization
The types of CA organizations are as follows:
•Central CA—The root CA issues certificates directly to all clients.
•Hierarchical CA—The root CA delegates signature authority to subordinate CAs. Subordinate CAs can further delegate signature authority to additional subordinates.
Certificate Validation and Authentication Process
The following list outlines the certificate validation and authentication process:
Step 1 Certificate signed by trusted CA? Has a CA certificate been installed on the concentrator for this CA?
Step 2 Certificate still valid? Does the current date fall within the start and end dates of the certificate?
Step 3 Certificate revoked? Does the certificate’s serial number exist on the CA’s CRL?
Step 4 Certificate authenticated? Reasonable assurance that the certificate has not been altered.
(a)Calculate hash of signature.
(b)Retrieve CA’s original hash of signature.
•Decrypt digital signature on certificate.
•Use root CA’s key from root certificate.
(c)Do the two hash values match? Certificate authenticated.

Certificate Management Applications 247
Internet-Based Certificate Authorities
The Cisco VPN 3000 Concentrator series works with the following Internet-based CAs:
•
•
•
Entrust Technologies (www.entrust.com)
VeriSign, Inc. (www.verisign.com)
Baltimore Technologies (www.baltimoretechnologies.com)
Certificate Management Applications
Certificate management applications are as follows:
•Microsoft Certificate Services for Windows 2000
•RSA Keon Certificate Authority for Solaris, Windows 2000, and Windows NT
•Netscape Certificate Management System for Solaris, Windows 2000, and Windows NT
