
Учебник по НТП
.pdf
sponsored by Stanford University. The mouse was originally referred to as an X-Y Position Indicator for a Display System. Xerox later applied the mouse to its revolutionary Alto computer system in 1973.
Mechanical mice require that the mouse be set on a flat surface. The distance and the speed of the rollers inside the mouse determine how far the mouse cursor moves on the screen depending on the software configuration.
Optical mice require a special mouse pad which has a grid pattern. A sensor inside the mouse determines the movement by reading the grid as the mouse passes over it while emitting a light from an LED or sometimes a laser. This type of mouse is much more accurate than the ordinary optical mechanical mouse which relies on the traction between the mouse ball and the rollers. One drawback to optical mice is they can have problems in bright lights. Optical mice feature no moving wheel on the bottom to get dirty and clog up over time. The best optical mice are those with three buttons and a wheel control which is very useful for moving up and down documents without dragging your mouse all over the page.
Atouch pad which is also known as a «glidepad», is a touch-sensi- tive pad used on a large majority of portable computers as a mouse device. A touch pad is operated by using your finger and dragging it across a flat surface, as you move your finger on the surface the mouse cursor will move in that same direction. Some modern keyboards have touch pads built-in or as separate serial devices.
Ajoystick is a peripheral input device that looks similar to a joystick used in a gaming system. A computer joystick is built into the center of the keyboard and allows an individual to easily navigate an object (i.e. a cursor while typing). The harder you push on it, the faster the pointer moves. This device (pioneered by the IBM Thinkpad) is used in many notebooks.
Atrackball is a type of input device that looks like an upside-down mouse. The onscreen pointer is moved by the trackball with a thumb or finger. A trackball requires less arm and wrist motion that a regular mouse takes. With a trackball, you move the cursor by rolling the ball with your thumb or index finger.
Many models, particularly those from Kensing-ton, provide multiple programmable buttons. Each button can be programmed to, say, launch a particular application, perform a double click, and so on. This reduces the amount of clicks you must make. And fewer clicks mean less strain on your hands. Another advantage: Trackballs require less space than mice. A mouse needs to be moved around, while a trackball sits in a holder.
The only disadvantage:
Dust and grime can accumulate in the trackball chamber (the area the ball sits in). When that happens, simply take the ball out, blow or wipe out the dust, and get right back to work.
73

A track point is a type of mouse solution used with portable computers that is a small isometric joystick resembling a pencil eraser head and is located between the «G», «H» and «B» keys on the keyboard. This technology enables a user to keep his hands on the keyboard and still be able to control the mouse. The buttons for this mouse are commonly located under the space bar.
Lightpens are an early and inexpensive technology that enables one to use a stylus directly on a display. Something not generally appreciated about lightpens is that they work with rear screen projection systems as long as the data projector uses cathode beam technology. (That is, they do not work with LCD projectors, for example.) Hence, lightpens provide an extremely cost effective means to convert a rear projection system into an interactive electronic whiteboard. This is especially interesting since some of the vendors provide lightpens that work with high resolution workstation displays which gives lightpens a potential whole new lease on life. On the other hand, in some situations where one needs to operate directly on the display with a stylus, the lightpen is losing ground to other technologies. These include where the stylus must be cordless, pressure sensitive, high resolution, or work with an LCD.
X. Organizing Ideas
Make a concept map on Computer Hardware and fill it with basic notions, associated words and phrases you’ve learned in this unit.
74

Unit II
Software
I. Getting Started
Read the text Computer Viruses. Divide it into several key parts and compose 3-5 questions to the each part. Put your questions to class.
II. Working With Vocabulary
Place the words and phrases below into the “Word“ column and complete the table:
Word |
English |
Examples |
Russian |
|
definition |
of usage |
translation |
||
|
self-replicating program, executable code, termed infection, host, benign, payload, time bomb, logic bomb, computer resources, removable disk, file system, common parlance, malware, multi-headed worm, backdoor, remote access, zombie computer, junk e-mail, to cloak website’s address, spammer, network traffic, slowdown, Trojan horse, legitimate software, to log keystrokes, spyware, adware, surreptitiously, pop-up window, to route HTTP request, software package, banner ad, binary executable file, hard disk partition, batch file, booting process, macro script.
III. Practising Translation Techniques
Make a written translation of the following text:
Computer Viruses
In computer security technology, a virus is a self-replicating program that spreads by inserting copies of itself into other executable code or documents. A computer virus behaves in a way similar to a biological virus, which spreads by inserting itself into living cells. Extending the analogy, the insertion of the virus into a program is termed infection, and the infected file (or executable code that is not part of a file) is called a host. While some viruses can be intentionally destructive (for example, by destroying data), many other viruses are fairly benign or merely annoying. Some viruses have a delayed payload, which is sometimes called a
75
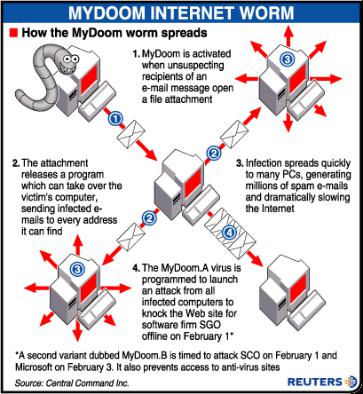
bomb. For example, a virus might display a message on a specific day or wait until it has infected a certain number of hosts. A time bomb occurs during a particular date or time, and a logic bomb occurs when the user of a computer takes an action that triggers the bomb.
However, the predominant negative effect of viruses is their uncontrolled self-reproduction, which wastes or overwhelms computer resources. A virus can only spread from one computer to another when its host is taken to the uninfected computer, for instance by a user sending it over a network or carrying it on a removable disk. Additionally, viruses can spread to other computers by infecting files on a network file system or a file system that is accessed by another computer.
In common parlance, the term virus is one of the several types of malware, or malicious software, including those that are more properly classified as worms and trojans. A worm can spread itself to other computers without needing to be transferred as part of a host. Many personal computers are now connected to the Internet and to local-area networks, facilitating their spread.
76
More recent worms may be multi-headed and carry other executables as a payload. A common payload is for a worm to install a backdoor (a method of bypassing normal authentication or obtaining remote access to a computer, while intended to remain hidden to casual inspection) in the infected computer, as was done by “Mydoom”. An infected, or zombie computer—mostly Windows PCs—is attached to the Internet that performs malicious tasks such as sending junk e-mail or cloaking the spammer’s website’s address, under the direction of the hacker. Many owners of zombie computers are unaware that their systems are zombies or that any hacker attack ever occurred. Between 50% to 80% of all spam worldwide is now sent by zombie computers.
However, even in the absence of such a payload, a worm can wreak havoc just with the network traffic generated by its reproduction. “Mydoom”, for example, caused a noticeable worldwide Internet slowdown at the peak of its spread in January, 2004.
A Trojan horse, or just a Trojan for short, is a malicious program disguised as legitimate software with the useful, or seemingly useful, functions serving as camouflage for undesired, harmful functions, such as erasing, corrupting or overwriting data on a computer, logging keystrokes to steal information such as passwords and credit card numbers, spreading other malware and installing a backdoor on a computer system.
Other types of malware can include spyware and adware programs. Spyware is a broad category of malicious software intended to intercept or take partial control of a computer’s operation without the user’s informed consent. While the term taken literally suggests software that surreptitiously monitors the user, it has come to refer more broadly to software that subverts the computer’s operation for the benefit of a third party. Spyware differs from viruses and worms in that it does not usually self-replicate. Like many recent viruses, spyware is designed to exploit infected computers for commercial gain. Typical tactics furthering this goal include delivery of unsolicited pop-up advertisements; theft of personal information (including financial information such as credit card numbers); monitoring of Web-browsing activity for marketing purposes; or routing of HTTP requests to advertising sites.
Adware, or advertising-supported software is any computer program or software package in which advertisements or other marketing material are included with or automatically loaded by the software and displayed or played back after installation or in which information about the computer or its users activities is uploaded automatically when the user has not requested it. These applications often present banner ads in pop-up windows or through a bar that appears on a computer screen.
Viruses can infect different types of hosts. The most common targets are binary executable files that contain application software or parts of the operating system (e.g. .COM and .EXE files in MS-DOS;
77

.DLL, .OBJ and other file types in Microsoft Windows). Viruses can also infect the executable boot sectors of floppy disks and hard disk partitions, general purpose script files of application programs (.BAT and .CMD, especially AUTOEXEC.BAT which is a special batch file executed during the booting process of a computer), and documents that can contain macro scripts (such as Microsoft Word documents, Microsoft Excel spreadsheets, Microsoft Office files and Microsoft Access database files). Additionally, viruses can infect files in other ways than simply inserting a copy of their code into the code of the host program. For example, a virus can overwrite its host with the virus code, or it can use a trick to ensure that the virus program is executed when the user wants to execute the (unmodified) host program.
Symantec issued an apology to Micro-soft after the security software maker’s AntiVirus Research Center issued an alert for a «widespread and lethal virus known to cause system crashes and data loss» that turned out to be the Windows 2000 operating system. Symantec CEO John Thompson called it a «regrettable but understandable» mistake.
IV. Knowing Ins And Outs
”Ware” is a suffix of instrumentality. It typically describes articles of the same general kind (giftware), products made of a specified material (silverware) or used in a specific application, such as software in computer science. Some -ware terms have fixed Russian equivalents, i.e. hardware—
аппаратные средства; shareware—условно-бесплатное программное обеспечение; etc., while others, being either red-hot or specific, represent the broad scope of translators’ activities.
Study the definitions given to the terms below. Then translate of the listed types of freeware into Russian. Try to use no more than three words for the Russian equivalent of the each term.
Types of freeware
Freeware is a computer software which is made available gratis. Typically freeware is proprietary and usually carries a license that permits redistribution but may have other restrictions, such as limitations on its commercial use. For example, a license might allow the software to be freely copied, but not sold, or might forbid use by government agencies or armed forces. There are many variations on the freeware model:
78

Abandonware—the commercial software, especially a video game, that has not been sold for a long time or whose copyright holder is defunct; it has been “abandoned”. The licenses of most such software forbid redistribution or require payment, so distributing it violates the author’s copyright (even if the author does not or cannot enforce it). “Legal abandonware” is a misnomer for commercial software that has been rereleased by the copyright holder as freeware.
Baitware—the very limited or defective freeware software, released to deceptively attract users and drive them to commercial products.
Beerware—a term that originally referred to a software license similar to shareware but more layed-back. It provides the end user with the right to use a particular program (or obtain the source code) in exchange for providing some money to the author so that they could buy beer. The first software distributed using the Beerware licensing model was uploaded to a number of BBSs (including Center of the Universe, The Boss, Executive Network, and PCExec) in 1987 and 1988. Lunchboxware is pretty much the same, except that you are required to show up at the software designer’s place of work with a boxed lunch.
Careware or Charityware—the shareware for which either the author suggests that some payment be made to a nominated charity or a levy directed to charity is included on top of the distribution charge.
Crippleware or Hostageware—the shareware or demoware that is functional enough for you to evaluate most features, but is “crippled” by disabling the more advanced or desirable features. This is intended to introduce you to the program and to whet your appetite for the better version. Often if you register or buy the full version, you will get a code which will un-cripple the program.
Demoware or Trialware—the shareware concept has become so popular with the growth of the Internet that many of the large commercial software publishers are releasing “trial” versions of their products for download and personal use. These “trial” versions are usually limited in some fashion (such as they only work for a specified length of time, or some features are disabled).
Donationware or Beggarware—the authors of donationware ask that anyone using their software make a donation to the authors or to some third party such as a charity. Because the donation is optional, donationware may also be freeware.
Guiltware—distributed freely, and the user is usually allowed or encouraged to distribute it personally. Where guiltware differs is in the methodology involved in actually inducing the user to remunerate the author. Guiltware, as its name suggests, attempts to guilt the user into paying by getting personal and telling the story of those that depend on the money it generates for survival. Guiltware can easily overlap donationware.
79

Liteware—a free version of the program is made that leaves out features that would make it more attractive to frequent or heavy users. For example, an HTML editor might have a Find and Replace feature. In the liteware version it would work for only one page at a time. In the full version you could apply Find and Replace to a whole project or a folder and its subfolders. So for infrequent users the lite version is just fine.
Nagware—the shareware or demoware that frequently displays screens to remind you to purchase the fully registered version. Apart from the extra key strokes required to cancel the reminder screen, it is usually fully functional.
Postcardware—the software similar to shareware, distributed by the author on the condition that users send the author a postcard expressing thanks and providing feedback. The concept was first used by Aaron Giles, author of JPEGView. E-mailware uses the same approach with requiring to send the author an e-mail.
Scareware—a class of freeware designed only to cause anxiety in the unsuspecting user. One example is a small program that puts up a dialog box saying “Erase everything on hard drive?” with two buttons, labeled “OK” and “OK”. Regardless which button is chosen, nothing is destroyed other than the user’s composure. This class of program tries to increase its perceived value by bombarding the user with constant warning messages that do not increase its effectiveness in any way.
Shareware—distributed similarly to freeware except that it requires payment after some trial period. The concept of shareware—Try It Before You Buy It!—is one of the better marketing ideas of modern times. If you try a shareware program and continue using it after a reasonable evaluation period, you are expected to register. With registration, you get anything from the simple right to continue using the software to an updated program with printed manual.
V. Enhancing Skills In English-Russian Interpretation
Render orally the following text:
Cryptography
Cryptography is concerned with keeping information, usually sensitive one like credit-card information, social security numbers, bank-account codes, etc., in secrecy. Information is encrypted to make it private and decrypted to restore it to human-readable form. Encryption is performed using an algorithm, which takes some input, called the plaintext, and converts it to ciphertext. A key is applied to
the algorithm that affects the ciphertext output.
One of the most well-known encryption algorithms is the U.S. gov-
80

ernment—endorsed DES (Data Encryption Standard). It uses a 56-bit key and an algorithm that scrambles and obscures a message by running it through multiple iterations or of an obfuscation algorithm. DES is a block cipher because it takes the plaintext and divides it up into blocks that are processed individually in multiple rounds (iterations). There are also symmetrical (single-key) and asymmetrical (two-key) ciphers. Symmetric schemes are also called private-key or secret-key encryption schemes. A single key is used for both encrypt and decrypt messages. If you send a decrypted message to someone, you must get them a copy of the key.
This is a problem in some environments, especially if you don’t know the recipient and need to transport or transmit the key using untrusted people or channels. How can you be sure the key has not been compromised? Asymmetric public-key schemes solve this problem.
In this scheme, everybody gets a set of keys. One key, called the public key, is made freely available. The other, called the private key, is held secretly. Sending encrypted messages to someone is simple. You obtain a copy of their public key, either directly from the person or from a public-key server, and use it to encrypt the message. This message can only be decrypted with the recipient’s private key. The private key is never made publicly available. The public-key scheme is revolutionizing computer security by providing ways to enable electronic commerce, authenticate users, validate and timestamp documents and programs, exchange secure electronic messages, and more.
81
There is another important encryption scheme called the one-way function. With this scheme, there is often no intention of ever deciphering the text. Encrypting with a one-way function is easy and takes little computer processing power. Reversing the encryption is considered impossible. Why encrypt something that never gets decrypted? Suppose you want to send a business partner a message and provide some proof that the message contents have not been altered in transit. The first step is to encrypt the message with a one-way function to produce a hash (also called a message digest). The hash represents the original document as a unique set of numbers. You then send the document to your business partner, encrypting it with his or her public key. Upon receipt, he or she runs the same one-way function on the contents of the document. The resulting hash should be the same as the one you sent. If not, the document is suspect. One-way functions are also used to store passwords. Actually, the technique doesn’t store the password, but its hash, and that is why it is secure. When a user logs on, a hash of the password is created and compared to the hash in the password file. If they compare, the user is considered authentic.
A cryptosystem can be analyzed either to verify its integrity (by cryptanalysts), or to find its weaknesses and thus to gain illegal access to documents (by hackers). Successful attacks usually take place under optimal conditions, i.e., using million dollar computer systems that are run by expert cryptanalysts (such as people at the National Security Agency) or by coordinating many interconnected network computers.
One method is called the brute force attack. This method was used to break DES. Every possible key is tried in an attempt to decrypt the ciphertext. Often, a dictionary of common passwords (freely available on the Internet) is used. This type of attack is often successful if weak passwords, such as common names, dictionary words and regular abbreviations, are used. Brute force attacks are difficult if long keys are used and if the keys consist of mixed numbers and characters in a nonsense pattern. It is estimated that a 100-bit key could take millions to billions of years to break. However, a weakness in a system might reduce the number of keys that need to be tried, thus making an attack feasible.
Another possibility is that the cryptanalyst can analyze the original plaintext, the algorithm, and the resulting ciphertext to find some pattern or weakness in the system. Message content is often not hard to figure out. Documents created in popular word processors often have hidden formatting codes and header information. Invoices or other business documents have a company’s name and address. The names of persons or systems may be repeated throughout a document. The cryptanalyst might even find a way to get some text inserted into a sensitive document before it is encrypted, then use the techniques described above to look for the message in the ciphertext.
82
