CHAPTER 4
GENERAL DESCRIPTION OF THE PPS SUBSYSTEMS
4.1. Engineered physical protection features
As mentioned above, a better understanding of a system is achieved through decomposing it. Separate systems are described below as subsystems of a system of engineered physical protection features (SEPPF) [1, 2].
Security alarm system
Essential to the construction and operation of the PPS is acquisition of information on the committed (attempted) unauthorized activity. This function is performed by detection sensors, which are part of the security alarm system (SAS).
A detection sensor is a device designed for automatic signal generation in the event of an unauthorized activity within its responsibility area.
A security alarm system is a combination of detection sensors, call alarms and the PPS data acquisition, handling and display system.
The following detection sensor classes may be identified. By conditions of application:
∙outdoor (perimeters, local areas);
∙indoor (buildings and rooms). By action:
∙electric-contact;
∙optical (including infrared);
∙capacitive;
∙inductive;
∙vibration;
∙seismic;
∙acoustic (including subsonic);
∙radio beam;
∙radar;
∙leaky-wave;
∙combined;
∙others.
The physical classification of detection sensors is based on interactions of the detection object (attacker) with different physical fields.
Essential to the SEPPF design are characteristics of its individual components, including detection sensors.
The following is normally chosen as the major detection sensor characteristics:
∙detection probability;
∙mean operating time to false response;
∙mean operating time to failure;
∙mean time to recovery;
∙cost.
Probability of detection is what determines the efficiency of the PPS as the whole.
Operating time to false response or frequency thereof is the performance characteristic defining to what extent the SEPPF causes nuisance to the guard personnel. Psychologically, an important point is also a decrease in confidence in signals and a lower level of alert as the result of frequent false alarms.
Operating time to failure and time to recovery are the robustness characteristics also determining the efficiency and operability of the SEPPF.
Cost is an important characteristic to be taken into account in the SEPPF design.
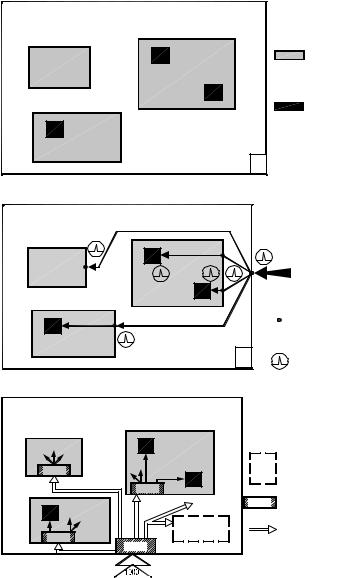
Fig. 4.1 presents simple examples of detection sensor applications on the NI site perimeter and inside the NI.
|
Electric-contact sensor |
Into |
|
Mesh fencing |
Door |
Vibration |
Wind |
Radio beam |
|
EZ |
|
|
Ultrasonic sensor |
|
Radar sensor |
Fig. 4.1. Examples of detection sensor applications: a) – on the NI perimeter; b)
– inside the NI.
The signals from the detection sensors installed for various NI applications (perimeter, outdoor, indoor) are sent over the communication lines to the physical protection system control panel (panels). The panel operators analyze the signals, after which the person responsible for decision-making chooses the algorithm for the response force actions to suppress the attackers and protect NM and the NF.
The combination of detection sensors, communication lines and control panels (that handle and display information from centers) forms the security alarm system.
Situation assessment subsystem
The false response problem leads us to thinking about how to raise the level of confidence in the DS response signals. One proven but outdated technique is the arrangement of exclusion zones (EZ) around the NI site on which the intruder’s traces will be left. Seals are used for indoor alarm acknowledgement.
A more recent alarm acknowledgement technique is application of video monitors and video surveillance systems (VSS).
All of the above features, both old and new, may be collectively viewed as a collection of situation assessment features and systems that improve reliability of primary data from detection sensors, as well as, in some cases (TV), make it possible to obtain more information on the intruder (number, intruder movement direction and so on) so that adequate countermeasures could be undertaken.
Seal designs are also improved (barcodes, optic seals, etc.).
Access control subsystem
The NI operations require authorized personnel and vehicle admission into the installation site and its separate areas, so each NI has a special subsystem established to identify “friends” (NI per sonnel, authorized visitors and so on) and “foes” (intruders) using a set of specific features.
Here are some of the definitions concerned with this.
Clearance: a duly issued permit for a person or a vehicle to enter any guarded area for the purpose of carrying out activities or receive any documents or data.
Access: realization of the possibility to stay in a guarded area, obtain information and documents, operate nuclear materials and so on.
One example of this subsystem’s element is a guard who performs the access-related functions. A recent trend is to use automatic devices instead of guards.
Essential elements of the access control system (ACS) are also devices that prevent prohibited items (weapons, explosives, nuclear material, etc.) from being taken into or out of the NI.
The access control system is a PPS subsystem that supports the NI protected area access control tasks.
To perform all these functions, external and internal access control points are established for the NI.
The access control systems and facilities are designed for the following applications:
∙external personnel access control points;
∙external vehicle and railway access control points;
∙internal personnel access control points;
∙entrances to restricted rooms;
∙storage rooms for physical protection articles (safes, etc.). Examples of personal identification techniques:
∙based on the features assigned:
coded pass; digital code;
∙ based on personal features: hand geometry;
eye structure; voice;
signature dynamics;
appearance (a computer photograph); others.
Examples of the ACS elements:
∙man traps for external (local area entrance) and internal access control points;
∙turnstiles at entrances to detached guarded areas;
∙door terminals for control of access to guarded rooms.
Also, access control points may include devices to prevent introduction of prohibited items as listed above.
The devices to be installed and the installation points thereof within the facility site are determined in the process of the PPS design.
Examples of the major ACS characteristics are as follows:
∙probability of detecting an admission procedure violation (identification features, etc.);
∙probability of a false detection of said violation;
∙mean operating time to failure;
∙mean time to recovery;
∙cost.
The first characteristic is what the efficiency of the PPS as the whole depends on.
The second characteristic determines the ACS maintainability. Of note is the ACS capability to regulate access to the installation’s separate guarded areas and segregate human and vehicle flows between these. The ACS ensures authorized access of personnel exactly to those areas they are permitted to enter.
The same can be said about the last three of the presented characteristics as with respect to detection sensors.
The ACS also has roles in countering insider actions.
Thanks to a great deal of capabilities opened up by advanced computer technology, a trend is observed towards integrating the ACS with security alarm systems and building integrated access control and security alarm systems (IACSAS).
Tendencies are also showing up towards integrating the PPS with NM accounting and control systems. The ACS is the major “interface” element in such integrated systems.
There are also other access control devices to consider in detail. These are, primarily, controlled locks that can be used in the ACS components, e.g. in cabins, or installed separately (door locks). In the latter case, these are to be logically viewed as controlled physical barriers to be described below.
Special communication system
A communication system is a facility for controlling the response force (RF) and ensuring communication within the NI and with the outside (relative to the installation): superior organizations, police stations, etc.
Regulatory documentation contains the requirement that there should be two communication channels (wire telephone and radio facilities).
Thanks to modern computer capabilities, it is possible to organize a communication network and control it in a flexible manner depending on the situation at hand.
The term “special communication” is used chiefly be cause of the need to protect information in the communication system.
Supporting systems
The term “supporting systems” gives a good notion o f what these systems are.
One illustrative example is the power supply system which is essential for operations of all the systems discussed above.
Another example is the lighting system which supports operations of the video surveillance system components (TV cameras).
More examples of supporting facilities and systems are the system of cable ducts that connect individual components in the above key systems, and structural elements (zone cabinets, etc.).
4.2. Physical barriers and organizational subsystem of the PPS
Physical barriers
Physical barriers (PB) have an important role in the PPS. A physical barrier is a physical obstacle that ensures the intruder delay to slow down the attacker’s movement to the target within the protected area.
In fact, it is not enough to receive an unauthorized action signal from a detection sensor or a component of the ACS. Another condition needs to be fulfilled to make so that the attacker action time (Тa) be longer than the response force action time (Тrf). It is important that the response force has a slack margin, that is, that the condition Тa > Тrf or Тrf = Тa – Тrf > 0 is fulfilled, where Тrf is the response force slack time.
Physical barriers have the purpose of delaying the attacker in every way possible and increasing Тa.
Physical barriers may be fixed and controlled.
Specifically, the following classes of physical barriers may be identified:
∙existing onsite physical barriers:
structural elements of buildings (walls, ceilings, doors); elements of the terrain and vegetation;
∙ artificial physical barriers: perimeter and local area fencing;
locks, meshes and reinforced doors in buildings and rooms; anti-ram facilities at vehicle access control points;
special physical barriers (sound-and-light, smoke-discharge, foaming, etc.).
There are also techniques of influencing the intruder (electric shock, gas discharge and others), though onsite uses of these are subject to authorization by respective law.
Response force
The response force (RF) is responsible for the ultimate suppression of the intruder actions. This means that the RF starts to act as information is received from facilities or the guard on duty about an attempted intrusion into the site or into some of its protected areas. The choice of the response tactics depends so on respective regulatory requirements and on the situation at hand.
The RF comprises several units, each of which is assigned to the task of its own. Thus, the alarm unit moves to the DS response point, the reinforcement unit heads for the site’s most vulnerable points to tighten security thereof and so on.
As will be shown below, time relations depend on the tactics chosen. Thus, we reduce Тrf by redeploying the RF and getting it closer the potential action points.
Organizational arrangements
Lastly, it is very important that all PPS components act coherently. We shall dwell on how to build and operate the PPS below, when consideration will be given to design and optimization of physical protection systems. Now just a note should be made that the order should be kept within the installation in the course of the PPS operation as established earlier through organizational arrangements. These arrangements include:
∙NI personnel actions in standard and emergency situations;
∙interactions among the onsite PP-related services and of these with the “outside world” (municipal authorities, superior or ganizations and security agencies);
∙maintenance of engineered physical protection features.
The arrangements taken should be governed by regulations (bylaws, instructions, etc.). This makes the PPS operations less dependent on subjective factors. For example, where no regulatory documents exist, the decision in some situations will be made by an executive officer at the respective level, that is, the decisions taken will be much determined by his/her personal qualities. A hard and adamant security service leader will
447
create a great deal of problems to the normal site operations, while, in contrast, an excessively mild leader will cause poorer control of the NI, which will ultimately make it less physically protected.
A note should be made that modern physical protection systems have an increasingly great number of organizational functions vested nowadays in their hardware. Thus, modern AC systems rely on a “ two-person rule” based on a collective responsibility principle (including with respect to the opening of rooms and the activation of security modes for these) when a person watches the actions of another person to reduce the probability of unauthorized activities.
Here is one more example. A timer is built in the data acquisition and processing system, which is triggered the moment the alarm unit (AU) responds to an alarm. When reaching the destination, the AU should report so to make it possible to know the exact guard personnel movement times and, accordingly, the final time of Тrf.
References
1.Глебов В.Б., Измайлов А.В., Румянцев А.Н. Введение в системы учета, контроля и физической защиты ядерных материалов. М.:
МИФИ, 2001.
2.Измайлов А.В. Методы проектирования и анализа эффективности систем физической защиты ядерных материалов и установок. М.: МИФИ, 2002.
CHAPTER 5
GENERAL CONCEPTS OF THE PPS DESIGN
The creation of complex systems is based on general concepts representative of systems of any nature, as well as on a number of specific principles that reflect the features of the given class of systems. The PPS features, as discussed hereinabove, define the set of specific concepts which are set forth below [1].
Zoning – defense in depth. This concept suggests the esta blishment of a system of guarded onsite areas enclosed one into another: a protected area, an inner area and a vital area (Fig. 5.1).
The protected area (PA) means the whole of the NI territory surrounded by physical barriers subject to continuous guarding and surveillance with access thereto being restricted and controlled. The inner area is inside the protected area (there may be more than one inner area). The inner area respectively includes the vital area (there may be also several vital areas). Safeguard measures become tougher from the outside to the physically protected items (PPI).
Here are some examples of such areas. If, as mentioned above, the protected area is the entire installation territory, the inner area (IA) may consist of buildings or separate parts of buildings within this territory, while rooms (clusters of rooms) inside buildings may be viewed as the vital area (VA).
The boundaries of the areas are equipped with engineered features with dedicated passages (drives) arranged therein for the authorized personnel access to the site. Clearly, requirements differ for the equipment of the areas and the boundaries thereof with engineered features and organizationally. Depending on the category of the physically protected item, this should be held within a particular area. For example, regulations require HEU to be held within the IA or the VA.
Of note is that areas may include additional EPPF-equipped barriers that are not on the area boundary and do not change the area status.
|
Защищённая зона |
|
|
|
Protected area |
|
|
|
|
|
Внутренняя зона |
|
|
|
|
Inner area |
|
|
|
|
Особо важная зона |
|
|
|
|
Vital area |
|
|
|
a) |
|
|
Защищённая зона |
|
|
|
|
Protected area |
|
|
|
|
|
Нарушитель |
|
|
|
|
Intruder |
|
|
|
|
Engineered physical |
|
|
|
|
Инженерно-технические |
|
|
|
|
средства физической |
|
|
|
|
protection features |
|
|
b) |
|
защиты |
|
|
|
Сигнал тревоги |
|
|
|
|
Alarm |
|
Защищённая зона |
|
|
|
Protected area |
|
|
250 |
|
|
|
Administrative |
|
20 |
|
|
|
|
|
Административное |
ÊÏ Ï |
200 |
30 |
|
здание |
250 |
ÊÏ Ï |
|
|
building |
|
|
|
Контрольно-пропускной |
|
|
|
|
|
250 |
100 |
ÊÏ Ï Access control point |
175 |
|
|
|
пункт |
|
|
|
Personnel flow |
25 |
200 |
|
|
|
30 |
Поток персонала |
|
|
|
ÊÏ Ï |
ÊÏ Ï |
|
|
200 |
|
|
|
NI personnel |
c) |
Персонал ЯО |
|
Fig. 5.1. PPS zoning principle: a) – guarded areas;
b) – defense-in-depth barriers; c) – differentiated personnel access to guarded areas
450