20411B-ENU-TrainerHandbook
.pdf
Administering Windows Server® 2012 |
MCT |
|
9-13 |
|
|
Considerations for DHCP enforcement |
|
|
When considering the DHCP NAP enforcement method, consider the following points: |
|
|
• DHCP enforcement is easy to implement, and can apply to any computer with a dynamic IP address. |
||
• |
DHCP enforcement is easy to circumvent. A client can circumvent DHCP enforcement by using a |
USE |
|
||
|
static IP address. Additionally, a noncompliant computer could add static host routes to reach servers |
|
|
that are not remediation servers. |
|
• DHCP enforcement is not possible for IPv6 clients. If computers on your network use IPv6 addresses |
||
|
to communicate, DHCP enforcement is ineffective. |
PROHIBITED USE STUDENT .ONLY |
|
|
|

9-14 Implementing Network Access Protection
Lesson 3 |
MCT |
|
Configuring NAP |
||
USE |
||
If you want your NAP deployment to work optimally, it is important that you understand what each of |
||
the NAP components does, and how they interact to protect your network. If you want to protect your |
||
|
network by using NAP, you need to understand the configuration requirements for the NAP client, as well as how to configure NPS as a NAP health policy server, configure health policies and network policies, and configure the client and server settings. It also is important to test the NAP before using it.
Lesson Objectives
After completing this lesson, you will be able to:
• Describe System Health Validators (SHVs). |
.ONLY |
||||
• |
Explain the use of a health policy. |
||||
|
|
||||
• Discuss the use of remediation server groups. |
|
|
|||
• Describe the NAP client-configuration requirements. |
|
|
|||
• Explain how to enable and configure NAP. |
|
STUDENT |
|||
What Are System Health Validators? |
|
||||
System Health Agents (SHAs) and System |
|
|
|||
|
|
||||
Health Validators (SHVs) are NAP infrastructure |
|
|
|||
components that provide health-state status |
|
|
|||
and validation. Windows 8 includes a Windows |
|
|
|||
Security Health Validator SHA that monitors the |
|
|
|||
Windows Security Center settings. Windows Server |
|
|
|||
2012 includes a corresponding Windows Security |
|
|
|||
|
|
USE |
|||
Health Validator SHV. |
|
|
|||
The design of NAP makes it very flexible and |
|
|
|||
extensible, and it can interoperate with any |
|
|
|||
vendor’s software that provides SHAs and |
|
|
|||
SHVs that use the NAP API. An SHV receives a |
|
||||
PROHIBITED |
|||||
statement of health (SoH), and then compares the system health-status information in the SoH with the |
|||||
required system health state. For example, if the SoH is from an antivirus SHA, and it contains the last |
|||||
version number for the virus-signature file, then the corresponding antivirus SHV can check with the |
|||||
antivirus health requirement server for the latest version number to validate the NAP client’s SoH. |
|||||
The SHV returns a SoH response (SoHR) to the NAP Administration Server. The SoHR can contain |
|||||
remediation information about how the corresponding SHA on the NAP client can meet current system- |
|||||
health requirements. For example, the SoHR that the antivirus SHV sends could instruct the NAP client’s |
|||||
antivirus SHA to request the latest version, by name or IP address, of the antivirus signature file from a |
|||||
specific antivirus signature server. |
|||||
|
|
|
|||



Administering Windows Server® 2012 9-17
Enable and Disable NAP Enforcement Clients |
|
||
You can use the Enable and Disable NAP Enforcement Clients procedure to enable or disable one or more |
|||
NAP enforcement clients on NAP-capable computers. These clients can include: |
MCT |
||
USE |
|||
• |
DHCP Enforcement Client |
||
• Remote Access Enforcement Client |
|||
• |
EAP Enforcement Client |
||
|
|
||
• IPsec Enforcement Client (also used for DirectAccess connections) |
ONLY |
||
• Terminal Services Gateway (TS Gateway) Enforcement Client |
|||
To enable and disable NAP Enforcement Clients: |
|||
|
|
||
1.Open the NAP Client Configuration console (NAPCLCFG.MSC).
2.Click Enforcement Clients. In the details pane, right-click the enforcement client that you want to enable or disable, and then click Enable or Disable.
|
|
. |
|
|
Note: To perform this procedure, you must be a member of the Administrators group on |
STUDENT |
|
|
|||
|
|
||
the local computer, or you must have been delegated the appropriate authority. If the computer |
|
||
is joined to a domain, members of the Domain Admins group might be able to perform this |
|
||
procedure. As a security best practice, consider performing this procedure by using the Run as |
|
||
command. |
|
||
Demonstration: Configuring NAP |
|
||
This demonstration shows how to: |
|
||
• |
Install the NPS server role. |
|
|
• |
Configure NPS as a NAP health policy server. |
USE |
|
• |
Configure health policies. |
||
|
|||
• |
Configure network policies for compliant computers. |
|
|
• |
Configure network policies for noncompliant computers. |
|
|
• |
Configure the DHCP server role for NAP. |
PROHIBITED |
|
• |
Configure client NAP settings. |
||
|
|||
• |
Test NAP. |
|
|
Demonstration Steps |
|
||
Install the NPS server role |
|
||
1. |
Switch to LON-DC1, and sign in as a domain administrator. |
|
|
2. |
Open Server Manager, and then install the Network Policy and Access Services role. |
|
|
Configure NPS as a NAP health policy server |
|
||
1. |
Open the Network Policy Server console. |
|
|
2. |
Configure the Windows Security Health Validator to require that all Windows 8 computers are |
|
|
|
running a firewall. |
|
|


Administering Windows Server® 2012 9-19
Lesson 4 |
MCT |
||||
Monitoring and Troubleshooting NAP |
|||||
|
|
||||
Troubleshooting and monitoring NAP is an important administrative task because of different technology |
|||||
levels, including varied expertise and prerequisites, for each NAP enforcement method. Trace logs are |
USE |
||||
available for NAP, but are disabled by default. These logs serve two purposes: troubleshooting and |
|||||
evaluating a network’s health and security. |
|||||
|
|
|
|||
Lesson Objectives |
|
|
|||
After completing this lesson, you will be able to: |
.ONLY |
||||
• Describe how NAP tracing can help monitor and troubleshoot NAP. |
|||||
• Explain how to configure NAP Tracing. |
|||||
• Troubleshoot NAP with Netsh. |
|||||
• |
Use the NAP event log to troubleshoot NAP. |
||||
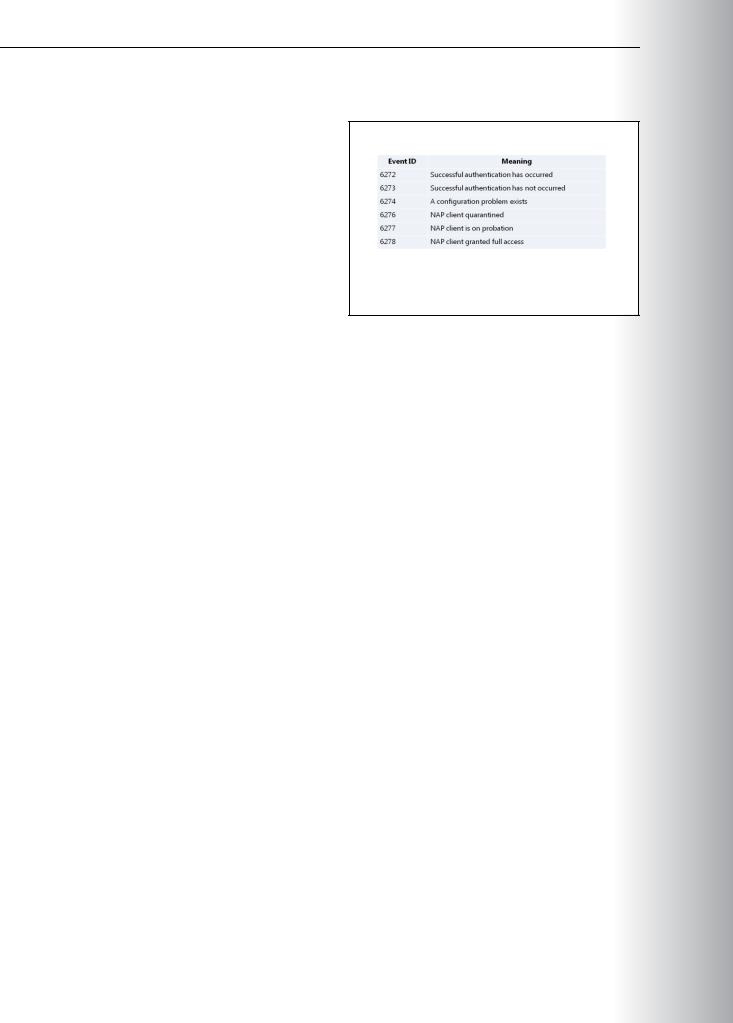
What Is NAP Tracing? |
|
|
|||
Aside from the preceding general guidelines, |
|
|
|
||
|
STUDENT |
||||
you can use the NAP Client Configuration |
|
||||
console to configure NAP tracing. Tracing |
|
||||
records NAP events in a log file, and is useful for |
|
||||
troubleshooting and maintenance. Additionally, |
|
||||
you can use tracing logs to evaluate your |
|
||||
network’s health and security. You can configure |
|
||||
three levels of tracing: Basic, Advanced, and |
|
||||
Debug. |
|
||||
Enable NAP tracing when: |
|
|
|
||
• |
Troubleshooting NAP problems. |
|
|
|
|
|
USE |
||||
• |
Evaluating the overall health and security of your organization’s computers. |
||||
|
|
||||
In addition to trace logging, you can view NPS accounting logs. These logs could contain useful NAP information. By default, NPS accounting logs are located in %systemroot%\system32\logfiles.
The following logs might contain NAP-related information:
•IASNAP.LOG. This contains detailed data about NAP processes, NPS authentication, and NPS authorization.
•IASSAM.LOG. This contains detailed data about user authentication and authorization.
Two tools are available for configuring NAP tracing. The NAP Client Configuration console is part of the Windows user interface, and netsh is a command-line tool.
PROHIBITED