
Английскй учебник
.pdf
1. as white as … |
a. a mule |
2. as red as … |
b. a hunter |
3. as ugly as … |
c. honey |
4. as hungry as … |
d. a mouse |
5. as light as … |
e. hills |
6. as firm as … |
f. a feather |
7. as obstinate as … |
g. a sin |
8. as old as … |
h. a sheet |
9. as quiet as … |
i. a rock |
10. as sweet as … |
j. a lobster |
7. , $# -
.
1. as …. as a lion |
a. good |
|
2. as … as ice |
b. black |
|
3. as …. as a berry |
c. pale |
|
4. as … as a picture |
d. sober |
|
5. as …. as |
a judge |
e. brave |
6. as … as a peacock |
f. brown |
|
7. as … as gold |
g. pretty |
|
8. as … as pitch |
h. proud |
|
9. as … as |
a bat |
i. cold |
10. as … as |
a ghost |
j. blind |
8. , . -
. ! &.
Copy & Paste Plagiarism: Any time you lift a sentence or significant phrase intact from a source, you must use quotations marks and reference the source.
Word Switch Plagiarism: If you take a sentence from a source and change around a few words, it is still plagiarism. If you want to quote a sentence, then you need to put it in quotation marks and cite the author and article.
Style Plagiarism: When you follow a Source Article sentence-by-sentence or paragraph-by- paragraph, it is plagiarism, even though none of your sentences is exactly like those in the Source Article or even in the same order. What you are copying in this case, is the author's reasoning style.
Metaphor Plagiarism: Metaphors are used either to make an idea clearer or give the reader an analogy that touches the senses or emotions better than a plain description of the object or process. If you cannot come up with your own metaphor to illustrate an important idea, then use the metaphor in the Source Article, but give the author credit for it.
351


Author |
Author |
Plagiarism |
Author |
Author intent |
identification |
characterization |
detection |
discrimination |
determination |
|
|
|
|
|
4. , . -
. ,
, # .
AUTHOR |
CODE |
PROGRAM |
5. , & $ .
1. Viruses are ……..
2.Trojan horses are …….
3.Logic bombs are ……..
4.Credit card cloning is ………
5.Cyber attacks are …………
6.! -. # # .
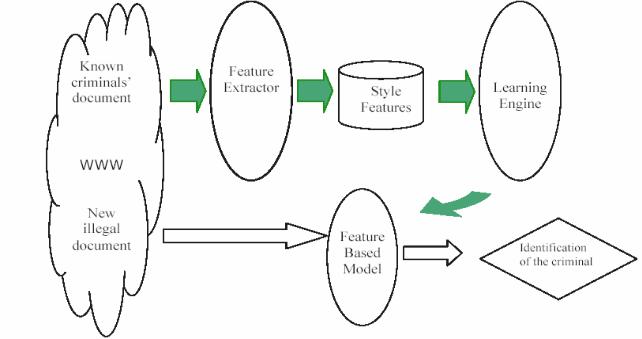
AUTHORSHIP ANALYSIS IN CYBERCRIME INVESTIGATION
The development of networking (") and the Internet in particular, has created a new way to share (# ) across ( ). While computer ( ) have enhanced ( &) in many aspects, they have also opened a ( # $" -$ ). These activities have spawned the ( ) of cybercrime, which ( ) to illegal computer-mediated activities that can be conducted through ( % ), such as the Internet. One predominant type of cybercrime is distribution of ( $ -) in cyber space. Such materials include pirate software, ( #), stolen properties, etc. Cyber criminals have been using various Web-based ( , $) illegal materials such as Email, websites, Internet newsgroups, Internet chat rooms, etc. One common characteristic of these channels is ( $). People usually do not need to provide their real identity information, such as ( , , ), in order to participate in cyber activities. Compared to conventional ( ), cybercrime conducted through such ( -) imposes unique challenges for law enforcement agencies in criminal identity tracing. The situation is further (&) by the sheer amount of cyber ( $ ") and activities, making the manual approach to criminal identity tracing impossible for meeting cybercrime investigation requirements.
355

) , ", % , , :
•& $- " ;
•$ & ;
• : # ( -$ $ , , # ", . .)?
|
'- , ) , $ # |
|
|
, $ $ " - |
|
|
" . @ ( ) - |
|
"- |
, & " - |
|
$ |
, - " % - |
|
$" .
UNIT 5. A FORENSIC LINGUISTIC REPORT
1. .
TEXT
DOCUMENTING AND REPORTING
Principle: The examiner is responsible for completely and accurately reporting his or her findings and the results of the forensic examination. Documentation is an ongoing process throughout the examination. It is important to accurately record the steps taken during the examination.
Procedure: All documentation should be complete, accurate, and comprehensive. The resulting report should be written for the intended audience.
Examiner's notes
Documentation should be contemporaneous with the examination, and retention of notes should be consistent with departmental policies. The following is a list of general considerations that may assist the examiner throughout the documentation process.
-Take notes when consulting with the case investigator and/or prosecutor.
-Maintain a copy of the search authority with the case notes.
-Maintain the initial request for assistance with the case file.
-Maintain a copy of chain of custody documentation.
-Make notes detailed enough to allow complete duplication of actions.
-Include in the notes dates, times, and descriptions and results of actions taken.
-Document irregularities encountered and any actions taken regarding the irregularities during the examination.
The structure of the linguist’s statement will follow the report style of the empirical sciences, something along these lines:
1. Summary (equivalent to the abstract of an academic paper).
360
