- •А.Д. Музафарова а.Г. Ковалева
- •Vocabulary practice section 1
- •Vocabulary practice section 2
- •Vocabulary practice section 3
- •This week: software
- •Vocabulary practice section 1
- •Vocabulary practice section 2
- •Internet: Voice recognition takes off
- •Programming languages.
- •Vocabulary practice section 1
- •Vocabulary practice section 2
- •Int — international organization
- •Vocabulary practice section 3
- •The 15 enemies of the Internet
- •Internet crime
- •Vocabulary practice section 1
- •Vocabulary practice section 2
- •Vocabulary practice section 3
- •How a virus infects a program
- •Vocabulary practice section 1
- •Video Games
- •Vocabulary practice section 2
- •Vocabulary practice setion 3
- •Vocabulary practice setion 4
- •Twitter's transmitters
- •Vocabulary practice section 1
- •Good Web Design? What Is It?
- •Vocabulary practice section 2
- •Vocabulary practice section 3
- •Top Five Ways to Make Your Site More Popular
- •1. Strong Hosting
- •2. Optimize Your Website
- •3. Take Advantage of Social Media Optimization
- •4. Get Your Visitors Involved
- •5. Emphasize Usability in Your Design
- •You’ve been in graphics too long if…
- •Internet
- •Web design
Vocabulary practice section 2
1. Look at Key information section 2 and find the following.
1. the most common extensions for graphics files
2. the most common text formats
3. three popular video formats
4. three common file formats for storing audio data
5. the distribution of audio and/or video signals which transmit programs to an audience
6. to copy or move programs or information into a computer's memory, especially from the Internet or a larger computer
7. attempts to simulate an abstract model of a particular system
8. a computer terminal that provides information access via electronic methods
9. a computer-based simulated environment
10. the process of becoming aware of various physiological functions
2. Complete texts with words from boxes.
|
coding technical terms cable schedule decoding |
|
|
The sequencing of content in a broadcast is called a (1) … . As with all technological endeavours, a number of (2) … and slang have developed. A list of these terms can be found at List of broadcasting terms. Television and radio programs are distributed through radio broadcasting or (3) …, often both simultaneously. |
By (4) … signals and having (5) … equipment in homes, the latter also enables subscription-based channels and pay-per-view services. Broadcasting focuses on getting one message out and it is up to the general public to do what they wish with it.
|
programming tool standard software |
|
|
Multimedia presentation (1) … is known for incorporating sound,animationeffects and cinematic-like special effects into presentations. It is a (2) … thatcomputerusers of varying industries and backgrounds use to dynamically present information |
to an audience.
It differs from (3) … presentation software in its features and its interactivity potential.
An advantage of working with multimedia presentation software is that it doesn't require that a user have any detailed knowledge of (4) … or code writing. The software usually comes with tutorials that are easy to follow and command functions that are self-explanatory and intuitive.
|
features web pages palette links sounds |
Images, documents, text, and (1) … like MP3and WAV files can all be manipulated and combined using the software to create a presentation. Even complete or pieces of (2) …, videos and animations can be added to a multimedia presentation. Active (3) …, special characters and other (4) … can be added later using the software's editing (5) … or paint-like application. When using these editing tools, animating, rotating — creating smooth transitions between images — and making timelines can be done easily and quickly.
|
emailed copy downloaded convert published import |
Multimedia presentation software can have the ability to (1) … other presentation software file formats into the program and (2) … them into their own propriety file formats or into universal formats like EXE filesorAVI/QuickTime videos. Screen savers and CD menus can even be created from these files. Completed presentations may be (3) … as attachments and some can even be played automatically through the recipient's browser.
|
They can also be (4) … on the Internet, (5) … directly onto a computer's hard driveor burned onto a CD-ROM orDVD. The mobile user who desires to show their presentation at a different location may find it necessary to (6) … their presentation onto a portablememory sticklike a flash drive so that they can simply insert the stick into another computer and access the file at the new location. |
|
|
controlled multiplayer computerized issued animated |
A virtual world is an (1) … three-dimensional world created with computergraphics imagining (CGI) and other rendering software. One of the hallmarks of avirtual world is that a user can interact within the environment by virtue of an avatar, or a (2) … character that represents the user. The avatar manipulates and interacts with objects in thevirtual world by mouse movements and keystrokes (3) … by the user. In simple terms, the avatar is a remote (4) … character or proxy.
In addition to graphics, a virtual world also provides sound effects and may offer streaming sound for listing to music, radio or scripts issuing from within the virtual environment. In (5) … games and environments, chat and instant messagingallowavatarsto communicate with each other in thevirtual world.
KYE INFORMATION SECTION 3
|
|
|
|
A computer network, often simply referred to as a network, is a collection of computers and devices connected by communications channels that facilitates communications among users and allows users to share resources and peripherals with other users. The main purposes of the networks are:
Facilitating communications. Using a network, people can communicate efficiently and easily via e-mail, instant messaging, chat rooms, telephony, video telephone calls, and videoconferencing.
Sharing hardware. In a networked environment, each computer on a network can access and use hardware on the network. Suppose several personal computers on a network each requires the use of a laser printer. If the personal computers and a laser printer are connected to a network, each user can then access the laser printer on the network, as they need it.
Sharing files, data, and information. In a network environment, any authorized user can access data and information stored on other computers on the network. The capability of providing access to data and information on shared storage devices is an important feature of many networks.
Sharing software. Users connected to a network can access application programs on the network.
Common types of computer networks may be identified by their scale.
|
|
A personal area network (PAN) is a computer network used for communication among computer and different information technological devices close to one person. Some examples of devices that are used in a PAN are personal computers, printers, fax machines, telephones, PDAs, scanners, and even video game consoles. |
A PAN may include wired and wireless connections between devices. The reach of a PAN typically extends to 10 meters. Wired PAN network is usually constructed with USB and Firewire while wireless with Bluetooth and Infrared.
Local area networks (LANs) are usually placed in the same building. They can be built with two main types of architecture: peer-to-peer, where the two computers have the same capabilities, or client-server, where one computer acts as the server containing the main hard disk and controlling the other workstations or nodes, all the devices linked in the network (e.g. printers, computers, etc.).
Computers in a LAN need to use the same protocol, or standard of communication. Ethernet is one of the most common protocols for LANs. A router, a device that forwards data packets, is needed to link a LAN to another network, e.g. to the Net.
A home area network is a residential LAN which is used for communication between digital devices typically deployed in the home, usually a small number of personal computers and accessories, such as printers and mobile computing devices. An important function is the sharing of Internet access, often a broadband service through a CATV or Digital Subscriber Line (DSL) provider.
A campus network is a computer network made up of an interconnection of local area networks (LANs) within a limited geographical area. The networking equipments (switches, routers) and trasmission media (optical fiber, copper plant) are almost entirely owned (by the campus tenant / owner: an enterprise, university, government etc.).
In the case of a university campus-based campus network, the network is likely to link a variety of campus buildings including academic departments, the university library and student residence halls.
A metropolitan area network (MAN) is a network that connects two or more local area networks or campus area networks together but does not extend beyond the boundaries of the immediate town/city. Routers, switches and hubs are connected to create a metropolitan area network.
|
A wide area network (WAN) is a computer network that covers a large geographic area such as a city, country, or spans even intercontinental distances, using a communications channel that combines many types of media. They are usually linked through telephone lines, fibre-optic cables or satellites. The main transmission paths within a WAN are high-speed lines called backbones. (The |
|
part of a network that handles the major traffic, may also run the longest distances. Smaller networks are attached to the backbone, and networks that directly connect to the end user or customer are called "access networks.")
Wireless WANs use mobile telephone networks. The largest WAN in existence is the Internet.
A global area network (GAN) is a network used for supporting mobile communications across an arbitrary number of wireless LANs, satellite coverage areas, etc. The key challenge in mobile communications is handing off the user communications from one local coverage area to the next. Wi-Fi, wireless fidelity, technologies allow the creation of WLANs, where cables or wires are replaced by radio waves. To build a WLAN you need access points, radio-based receiver-transmitters that are connected to the wired LAN, and wireless adapters installed in your computer to link it to the network. Hotspots are WLANs available for public use in places like airports and hotels, but sometimes the service is also available outdoors (e.g. university campuses, squares, etc.).
|
|
Beginning with the digitalisation of telecommunication networks started in the 70's in the USA and propelled by the growth in computer systems availability and demands private networks have been built for decades without the need to append the term private to them. The networks were operated over telecommunication networks and as per voice |
communications a certain amount of security and secrecy was expected and assumed.
But with the Internet in the 90's came a new type of network built over this Public infrastructure, using encryption to protect the data traffic from eaves-dropping (VPN). So the enterprise networks are now commonly referred to Enterprise Private Network in order to clarify that these are private networks (in opposition to public networks).
A virtual private network (VPN) is a computer network in which some of the links between nodes are carried by open connections or virtual circuits in some larger network (e.g. the Internet) instead of by physical wires. The data link layer protocols of the virtual network are said to be tunneled through the larger network when this is the case. One common application is secure communications through the public Internet, but a VPN need not have explicit security features, such as authentication or content encryption. VPNs, for example, can be used to separate the traffic of different user communities over an underlying network with strong security features.
A VPN may have best-effort performance, or may have a defined service level agreement (SLA) between the VPN customer and the VPN service provider.
An Internetwork is the connection of two or more private computer networks via a common switching or routing technology and owned by separate entities (public or private). The result is called an internetwork. The Internet is an aggregation of many Internetworks hence its name was shortened to Internet.
Any interconnection between public, private, commercial, industrial, or governmental networks may also be defined as an internetwork or (more often) an extranet.
The Internet is a global system of interconnected governmental, academic, corporate, public, and private computer networks. It is based on the networking technologies of the Internet Protocol Suite.
|
|
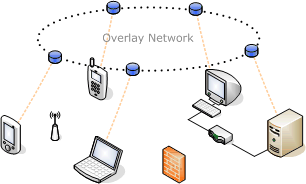
An overlay network is a computer network that is built on top of another network. Nodes in the overlay can be thought of as being connected by virtual or logical links, each of which corresponds to a path, perhaps through many physical links in the underlying network. For example, many peer-to-peer networks are overlay |
networks because they run on top of the Internet. Internet was built as an overlay upon the telephone network.
Overlay networks have been around since the invention of networking when computer systems were connected over telephone lines using modem, before any data network existed. Nowadays the Internet is the basis for many overlaid networks than can be constructed in order to permit routing of messages to destinations not specified by an IP address. For example, distributed hash tables can be used to route messages to a node having a specific logical address, whose IP address is not known in advance. Overlay networks have also been proposed as a way to improve Internet routing, such as through quality of service guarantees to achieve higher-quality streaming media.