
- •А.Д. Музафарова а.Г. Ковалева
- •Vocabulary practice section 1
- •Vocabulary practice section 2
- •Vocabulary practice section 3
- •This week: software
- •Vocabulary practice section 1
- •Vocabulary practice section 2
- •Internet: Voice recognition takes off
- •Programming languages.
- •Vocabulary practice section 1
- •Vocabulary practice section 2
- •Int — international organization
- •Vocabulary practice section 3
- •The 15 enemies of the Internet
- •Internet crime
- •Vocabulary practice section 1
- •Vocabulary practice section 2
- •Vocabulary practice section 3
- •How a virus infects a program
- •Vocabulary practice section 1
- •Video Games
- •Vocabulary practice section 2
- •Vocabulary practice setion 3
- •Vocabulary practice setion 4
- •Twitter's transmitters
- •Vocabulary practice section 1
- •Good Web Design? What Is It?
- •Vocabulary practice section 2
- •Vocabulary practice section 3
- •Top Five Ways to Make Your Site More Popular
- •1. Strong Hosting
- •2. Optimize Your Website
- •3. Take Advantage of Social Media Optimization
- •4. Get Your Visitors Involved
- •5. Emphasize Usability in Your Design
- •You’ve been in graphics too long if…
- •Internet
- •Web design
Vocabulary practice section 2
1. Match the malware with the damage.
|
1. virus |
a. collects and sends private information from the infected computer to a third party |
|
|
2. spyware |
b. an undesirable program which can replicate itself across a network | |
|
3. trojan horse |
c. allows a hacker to access private information when he/she wishes | |
|
4. keystroke logger or keylogger |
d. a program which adds itself to an executable file, and can cause considerable damage to the data on the infected computer | |
|
5. worm |
e. records characters that are typed into a computer |
|
2. Decide what these kinds of computer crime are and match them to the descriptions which follow.
|
1. Salami Shaving |
A. Leaving, within a completed program, an illicit program that allows unauthorised - and unknown - entry. |
|
2. Denial of Service attack |
B. Using another person’s identification code or using that person’s files before he or she has logged off. |
|
3. Trojan Horse |
C. Adding concealed instructions to a computer program so that it will still work but will also perform prohibited duties. In other words, it appears to do something useful but actually does something destructive in the background. |
|
4. Trapdoors |
D. Tricking a user into revealing confidential information such as an access code or a credit-card number. |
|
5. Mail bombing |
E. Inundating an email address with thousands of messages, thereby slowing or even crashing the server. |
|
6. Software Piracy
|
F. Manipulating programs or data so that small amounts of money are deducted from a large number of transactions or accounts and accumulated elsewhere. The victims are often unaware of the crime because the amount taken from any individual is so small. |
|
7. Piggybacking |
G. Unauthorised copying of a program for sale or distributing to other users. |
|
8. Phishing |
H. Swamping a server with large numbers of requests. |
|
9. Defacing |
I. Redirecting anyone trying to visit a certain site elsewhere. |
|
10. Hijacking |
J. Changing the information shown on another person's website. |
KEY INFORMATION SECTION 3
|
|
|
|
The anatomy of a virus
A biological virus is a very small, simple organism that infects living cells, known as the host, by attaching itself to them and using them to reproduce itself. This often causes harm to the host cells.
Similarly, a computer virus is a very small program routine that infects a computer system and uses its resources to reproduce itself. It often does this by patching (attaching and integrating into) the operating system to enable it to detect program files, such as COM (command) or EXE (executable) files. It then copies itself into those files. This sometimes causes harm to the host computer system.
When the user runs an infected program, it is loaded into memory carrying the virus. The virus uses a common programming technique to stay resident in memory. It can then use a reproduction routine to infect other programs. This process continues until the computer is switched off.
|
The virus may also contain a payload that remains dormant until a trigger event activates it, such as the user pressing a particular key. The payload can have a variety of forms. It might do something relatively harmless such as displaying a message on the monitor screen or it might do something more |
|
destructive such as deleting files on the hard disk.
When it infects a file, the virus replaces the first instruction in the host program with a command that changes the normal execution sequence. This type of command is known as a JUMP command and causes the virus instructions to be executed before the host program. The virus then returns control to the host program which then continues with its normal sequence of instructions and is executed in the normal way. Crackers don't always use the same segment of an operating system's initializing sequence, which makes detection tricky for the average user.
To be a virus, a program only needs to have a reproduction routine that enables it to infect other programs. Viruses can, however, have four main parts. A misdirection routinethat enables it to hide itself; areproduction routinethat allows it to copy itself to other programs; atriggerthat causes the payload to be activated at a particular time or when a particular event takes place; and apayloadthat may be a fairly harmless joke or may be very destructive. A program that has a payload but does not have a reproduction routine is known as aTrojan. Each virus is given a name e.g. Love Bug and can be classified as a particular type of virus. Virus types include:logic bombsthat destroy data when triggered;boot sector virusesthat store themselves in the boot sector of a disk (the part of a disk containing the programs used to start up a computer);file virusesthat attach themselves to COM files;macro virusesthat are small macro programs that attach themselves to word processor files and use the macro programming facilities provided in some word processor programs.
Preventative tips
|
|
|
The golden rule to avoid being phished is to never ever click the links within the text of the e-mail. Always delete the e-mail immediately. Once you have deleted the e-mail then empty the trash box in your e-mail client as well. This will prevent "accidental" clicks from happening as well.
To protect your computer system from this type of malicious code, install and use an antivirus program. This utility scans hard disk drives for viruses, worms and Trojan horses and removes, fixes or isolates any threats that are found. Most antivirus programs include an auto-update feature that enables the program to download profiles of new viruses so that it can check for the new viruses on your system as soon as they are discovered.
Install spam filter and security software that keeps an eye on you while you browse the web.
Make backup copies of your files regularly.
Don't accept files from high-risk sources.
Use a digital certificate, an electronic way of proving your identity, when you are doing business on the Internet. Avoid giving credit card numbers.
Don't believe everything you read on the Net. Have a suspicious attitude toward its contents.
Avoid keeping passwords stored on your computer and disclosing them to anybody.
If you are accessing banking details from a computer that is used by other people, ensure you do not click on "save" password, as another user could gain access.
Check your bank statements and receipts carefully to ensure there are no fraudulent transactions.
Set your browser and operating system security level to at least the medium setting (or higher) for best results. You may see a few more warning messages, but it's a small price to pay for security.
Don't click on any pop-up or advertisement for free anti-spyware software. These are almost always fake, even if they carry the name and logo of a well-known publisher. Ironically, this is a very popular method used to distribute spyware and other malware. If you're looking for anti-virus software, go directly to the company's Web site and be sure you're where you think you are.
Avoid questionable Web sites. If you visit a site that seems strange, there's a good chance you shouldn't be there.
When you do download software, read the end user license agreement before committing to the installation. When in doubt, do not install the software.
Don't download shareware (or anything else for that matter) from unknown sources. Seek out reliable providers of free utilities.
Make sure you use a firewall- a program designed to prevent spyware from gaining access to the internal network, its job is similar to a physical firewall that keeps a fire from spreading from one area to the next.
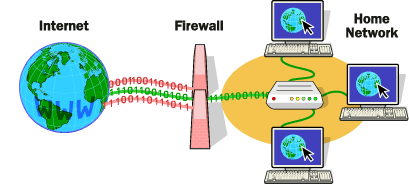
Firewalls use one or more of three methods to control traffic flowing in and out of the network:
Packet filtering- Packets (small chunks of data) are analyzed against a set of filters. Packets that make it through the filters are sent to the requesting system and all others are discarded.
Proxy service- Information from the Internet is retrieved by the firewall and then sent to the requesting system and vice versa.
Stateful inspection- A newer method that doesn't examine the contents of each packet but instead compares certain key parts of the packet to a database of trusted information. Information traveling from inside the firewall to the outside is monitored for specific defining characteristics, then incoming information is compared to these characteristics. If the comparison yields a reasonable match, the information is allowed through. Otherwise it is discarded.
If your computer has already been infected and turned into a zombie computer, there are only a few options open to you. If you have access to tech support who can work on your computer for you, that would be the best option. If not, you can try to run a virus removal program to kill the connection between your computer and the cracker. Unfortunately, sometimes the only option you have is to erase everything on your computer and reload its operating system, then starting from scratch.
Your computer is a great resource. Sadly, crackers think the same thing - they want to make your computer their own resource. If you practice careful Internet habits and follow the abovementioned tips, your chances of your computer remaining secure are very good.







