
CCNP 642-811 BCMSN Exam Certification Guide - Cisco press
.pdf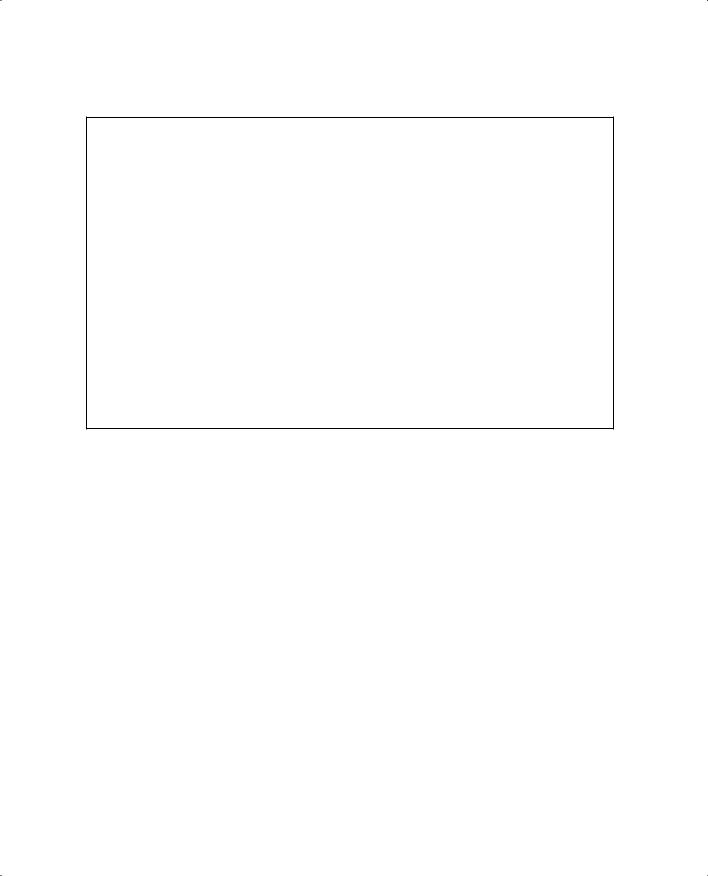
446 Chapter 18: IP Telephony
Example 18-6 Displaying Queuing Strategies for a Switch Port
Switch# show int fas 0/1 cap
FastEthernet0/1 |
|
|
||
|
Model: |
WS-C3550-24-PWR |
||
|
Type: |
10/100BaseTX |
||
|
Speed: |
10,100,auto |
||
|
Duplex: |
half,full,auto |
||
|
Trunk encap. type: |
802.1Q,ISL |
||
|
Trunk mode: |
on,off,desirable,nonegotiate |
||
|
Channel: |
yes |
||
|
Broadcast suppression: |
percentage(0-100) |
||
|
Flowcontrol: |
rx-(off,on,desired),tx-(none) |
||
|
Fast Start: |
yes |
||
|
|
|
|
|
|
QOS scheduling: |
|
rx-(1q0t),tx-(4q0t), |
tx-(1p3q0t) |
|
CoS rewrite: |
|
yes |
|
|
ToS rewrite: |
yes |
||
|
UDLD: |
yes |
||
|
Inline power: |
yes |
||
|
SPAN: |
source/destination |
||
|
PortSecure: |
yes |
||
|
Dot1x: |
yes |
||
Switch# |
|
|
||
To verify how the CoS values map packets into the egress port queues, use one of the following EXEC commands:
Switch# show mls qos interface type mod/num queueing
Switch# show queueing interface type mod/num
The first command is used on a Catalyst 3550, while the second command is used on a Catalyst 6500.
Example 18-7 shows some sample output from the show mls qos interface queueing command. Notice that the strict-priority queue (also called the expedite queue) is enabled. Here, queues 1 through 3 are the standard queues, and queue 4 is the strict-priority queue. CoS value 3 (used for voice call control packets) is mapped into the medium-priority standard queue, while CoS 5 (used for voice bearer packets) goes into the highest-priority standard queue. Preferably, CoS 5 should be mapped to the strict-priority queue. The CoS-to-queue mapping can be reconfigured, if necessary.

Verifying Inline Power, Voice VLANs, and Voice QoS 447
Example 18-7 Determining How CoS Values Map Packets to Egress Port Queues
Switch# show mls qos interface fast 0/1 queueing
FastEthernet0/1
Egress expedite queue: ena
wrr bandwidth weights: qid-weights
1 - 25
2 - 25
3 - 25
4 - 25 when expedite queue is disabled Cos-queue map:
cos-qid 0 - 1 1 - 1 2 - 2
3 - 2
4 - 3
5 - 3
6 - 4
7 - 4
Switch#

448 Chapter 18: IP Telephony
Foundation Summary
The Foundation Summary is a collection of information that provides a convenient review of many key concepts in this chapter. If you are already comfortable with the topics in this chapter, this summary could help you recall a few details. If you just read this chapter, this review should help solidify some key facts. If you are doing your final preparation before the exam, this summarized information is a convenient way to review the day before the exam.
Table 18-3 Commands for Configuring IP Telephony on a Catalyst Switch
Task |
Command Syntax |
|
|
Set inline power behavior. |
power inline {auto | never} |
|
|
Define the trunking on a port to a |
switchport voice vlan {vlan-id | dot1p | untagged | none} |
Cisco IP Phone. |
|
|
|
Define trust relationship of the IP |
switchport priority extend {cos value | trust} |
Phone. |
|
|
|
You can use the commands in Table 18-4 to verify or troubleshoot IP Telephony on a Catalyst switch.
Table 18-4 Commands for Troubleshooting IP Telephony on a Catalyst Switch
Task |
Command Syntax |
|
|
Show inline power status. |
show power inline [type mod/num] |
|
|
Verify the voice VLAN. |
show interface type mod/num switchport |
|
|
Show how QoS trust is extended to |
show mls qos interface type mod/num |
phone. |
|
|
|
Show queuing strategy of a port. |
show interface type mod/num capabilities |
|
|
See how CoS values are mapped into |
show mls qos interface type mod/num queueing |
port queues. |
|
|
|

Q&A 449
Q&A
The questions and scenarios in this book are more difficult than what you should experience on the actual exam. The questions do not attempt to cover more breadth or depth than the exam; however, they are designed to make sure that you know the answers. Rather than allowing you to derive the answers from clues hidden inside the questions themselves, the questions challenge your understanding and recall of the subject. Hopefully, these questions will help limit the number of exam questions on which you narrow your choices to two options and then guess.
The answers to these questions can be found in Appendix A.
1.How does a Catalyst switch detect that a connected device is capable of using inline power?
2.What type of trunk can be used between a Catalyst switch port and a Cisco IP Phone?
3.When a trunk is used on an IP Phone, on which VLAN is the data from an attached PC carried?
4.What is the difference between the VVID and the PVID?
5.Can the CoS information from the voice traffic be passed when the switchport voice vlan untagged command is used? If so, how?
6.What is the advantage of using the switchport voice vlan dot1p command?
7.By default, does a Cisco IP Phone trust QoS information from an attached PC?
8.The command switchport priority extend cos 5 is entered for a switch port. Is this a good decision? Why or why not?
9.How can a switch classify VoIP voice bearer packets that are carried by RTP?
10.The show power inline command is used to check the power status on each switch port. If the output is as shown here, what can you assume about interface fastethernet 0/1?
Interface |
Admin |
Oper |
Power |
Device |
|
|
|
(Watts) |
|
---------- |
----- |
---------- ------- |
------------------- |
|
Fa0/1 |
auto |
off |
0 |
n/a |
Fa0/2 |
auto |
on |
6.3 |
Cisco IP Phone 7960 |
11.What command can verify the QoS trust relationship between an IP Phone and its attached PC?

This chapter covers the following topics that you need to master for the CCNP BCMSN exam:
■Switch Authentication, Authorization, and Accounting (AAA)—This section discusses methods that you can use to control switch management access to users.
■Port Security Using MAC Addresses—
This section explains how to configure switch ports to allow network access to only hosts with specific or learned MAC addresses.
■Port-based Security Using IEEE 802.1x—
This section discusses a method you can use to require user authentication before network access is offered to a client host.

C H A P T E R 19
Securing Switch Access
Traditionally, users have been able to connect a PC to a switched network and gain immediate access to enterprise resources. As networks grow and as more confidential data or restricted resources become available, it is important to limit the access that users receive.
Catalyst switches have a variety of methods that can secure or control user access. Users can be authenticated as they connect to or through a switch, and authorized to perform certain actions on a switch. User access can be recorded as switch accounting information. The physical switch port access can also be controlled based on the user’s MAC address or authentication.
“Do I Know This Already?” Quiz
The purpose of the “Do I Know This Already?” quiz is to help you decide what parts of this chapter to use. If you already intend to read the entire chapter, you do not necessarily need to answer these questions now.
The quiz, derived from the major sections in the “Foundation Topics” portion of the chapter, helps you determine how to spend your limited study time.
Table 19-1 outlines the major topics discussed in this chapter and the “Do I Know This Already?” quiz questions that correspond to those topics.
Table 19-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping
Foundation Topics Section |
Questions Covered in This Section |
|
|
Switch AAA |
1–3 |
|
|
Port Security |
4–7 |
|
|
Port-based Authentication |
8–12 |
|
|
|
|
CAUTION The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark this question wrong. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.

452Chapter 19: Securing Switch Access
1.If the username command is used in a switch configuration, what method of authentication is implied?
a.Remote
b.Local
c.RADIUS
d.TACACS+
2.Which one of the following commands should be used to configure a vty line to use the “myservers” authentication method list?
a.line authentication myservers
b.authentication myservers
c.authentication method myservers
d.login authentication myservers
3.If a user needs to be in the privileged EXEC or enable mode, which part of AAA must succeed?
a.Authentication
b.Authorization
c.Accounting
d.Administration
4.Which switch feature can grant access through a port only if the host with MAC address 0005.0004.0003 is connected?
a.SPAN
b.MAC address ACL
c.Port security
d.Port-based authentication
5.Port security is being used to control access to a switch port. Which one of these commands will put the port into the errdisable state if an unauthorized station connects?
a.switchport port-security violation protect
b.switchport port-security violation restrict
c.switchport port-security violation errdisable
d.switchport port-security violation shutdown

“Do I Know This Already?” Quiz 453
6.If port security is left to its default configuration, how many different MAC addresses can be learned at one time on a switch port?
a.0
b.1
c.16
d.256
7.The following commands are configured on a Catalyst switch port. What happens when the host with MAC address 0001.0002.0003 tries to connect?
switchport port-security switchport port-security maximum 3
switchport port-security mac-address 0002.0002.0002 switchport port-security violation shutdown
a.The port shuts down.
b.The host is allowed to connect.
c.The host is denied a connection.
d.The host can connect only when 0002.0002.0002 is not connected.
8.What protocol is used for port-based authentication?
a.802.1D
b.802.1Q
c.802.1x
d.802.1w
9.When 802.1x is used for a switch port, where must it be configured?
a.Switch port and client PC
b.Switch port only
c.Client PC only
d.Switch port and a RADIUS server

454Chapter 19: Securing Switch Access
10.When port-based authentication is globally enabled, what is the default behavior for all switch ports?
a.Authenticate users before enabling the port.
b.Allow all connections without authentication.
c.Do not allow any connections.
d.There is no default behavior.
11.After port-based authentication is enabled, what method is available for a user to authenticate?
a.Web browser
b.Telnet session
c.802.1x client
d.DHCP
12.The users in a department are using a variety of host platforms, some old and some new. All of them have been approved with a user ID in a RADIUS server database. Which one of these features should be used to restrict access to the switch ports in the building?
a.AAA Authentication
b.AAA Authorization
c.Port security
d.Port-based authentication
The answers to the “Do I Know This Already?” quiz are found in Appendix A, “Answers to Chapter ‘Do I Know This Already?’ Quizzes and Q&A Sections.” The suggested choices for your next step are as follows:
■10 or less overall score—Read the entire chapter. This includes the “Foundation Topics,” “Foundation Summary,” and “Q&A” sections.
■11 or 12 overall score—If you want more review on these topics, skip to the “Foundation Summary” section and then go to the “Q&A” section at the end of the chapter. Otherwise, move to Chapter 20, “Securing with VLANs.”

Switch AAA 455
Foundation Topics
Switch AAA
You can manage user activity to and through a switch with authentication, authorization, and accounting (AAA) features. AAA uses standardized methods to challenge users for their credentials before access is allowed or authorized. Accounting protocols can also record user activity on a switch.
Authentication
Switch or network access can be granted only after a user’s identity has been validated. User authentication is commonly used on switches and routers to limit Telnet access to the network administration staff. In this case, when someone uses Telnet to log on to a switch, that individual is first challenged with a username and password. The individual’s credentials are then submitted to a device that can grant the user access.
User authentication can be handled by several methods:
■Usernames and passwords configured locally on the switch
■One or more external Remote Authentication Dial-In User Service (RADIUS) servers
■One or more external Terminal Access Controller Access Control System+ (TACACS+) servers
Any combination of these methods can be used. In fact, authentication must be defined by grouping the desired methods into a method list. The list contains the types or protocols that will be used, in the sequential order that they will be tried.
To use authentication on a Catalyst switch, you must configure several things in the following order:
Step 1 Enable AAA on the switch.
By default, AAA is disabled. Therefore, all user authentication is handled locally, by configured usernames and passwords. To enable AAA, use the following global configuration command:
Switch(config)# aaa new-model
The new-model refers to the use of method lists, where authentication methods and sources can be grouped or organized. The new model is much more scalable than the “old model,” where the authentication source was explicitly configured.
