
- •Product Overview
- •System Specifications
- •Installation
- •Adding a User Name and Password for CodeSeeker
- •Installing ISAPI Filter into IIS 5 for Windows 2000
- •CodeSeeker Management Console Overview
- •Policy Information
- •Customizing Security Policies
- •Reports
- •Analyzing and Customizing CodeSeeker
- •Servers
- •Dot Detector
- •Hidden file detector
- •HT Configuration File Detector
- •Common Command Detectors
- •Cmd.com Script Detector
- •Null Byte Detector
- •Unicode Detector
- •Buffer Overflow Detector
- •Multiple SQL Statements Detector
- •/etc/passwd File Detector
- •/etc/shadow File Detector
- •/etc/hosts File Detector
- •Summary of Regular-Expression Constructs
- •Backslashes, escapes, and quoting
- •Line terminators
- •Unicode support
- •HTTP Status Codes
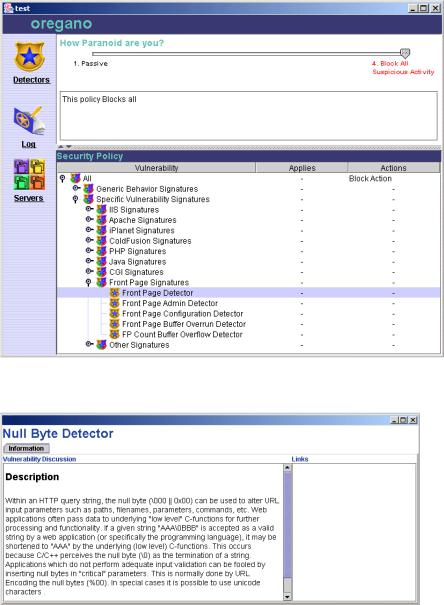
Customizing Security Policies
You may need to customize the actions of security policies depending on the applications running on your web server. Security policies are grouped by Generic Behavior and Specific Vulnerability. Based on the log files provided by CodeSeeker, you might need to change or disable certain security policies so that CodeSeeker security will not adversely affect your web application by over-securing it.
Double-click a policy name to learn more about it.
Applies To and Actions
CodeSeeker allows you to adjust each specific policy and the action it takes. To make administration easier, any policy changes you make affect all policies down the tree from the change you have made. If you make a change to the Front Page Signatures group, all of the detectors within that group are affected. Furthermore, if you change the FrontPage Admin Detector all of the FrontPage detectors below the Admin Detector will be affected.
Butterfly Security CodeSeeker Application Security Solution Help
12

Changing Security Policy Applications – Single-click the Security Policy in the Applies column to edit what area of the web server a security policy applies to. Adjusting what the
Detector applies to can range from a subdirectory or file to a complex URL pattern script. For more information on arguments and expressions, please read Summary of regular – expression constructs at the end of this document.
Some examples of syntax for directories and file inclusion or exclusion:
/scripts/.* /scripts/billing.*
/scripts/billing.pl
Use a line break (return) for multiple arguments / files.
Changing Security Policy Actions – There are two different types of actions that take place when an event happens -- Notification and Navigation. Single-click the Security Policy in the Actions column to edit the action a policy will take.
Notification:
Mail Action – Allows you to e-mail an event notification – See Notification Tokens below for variables you can add to your e-mail.
Syslog Action – Allows you to log the event to a Unix Syslog
NT Event Log Action – Allows you to log the event into the NT event log
Log To File Action – Allows you to log the event to a custom log file.
You may use Notification Tokens for additional log information. Place a trailing return at the end of the log item you have create so that each log item appears on a different line in the log file.
Butterfly Security CodeSeeker Application Security Solution Help
13

Notification Tokens – Notification Tokens can be used like tokens in Microsoft Word. You can wrap text around them and space several on a single line.
&url; -- The URL (just the part after the host... i.e. for the url above its really /whois/index.html) &method; -- The HTTP Method
&hostname; -- the hostname portion of the URL
&protocolspec; -- what protocol the client is using (HTTP/1.0, HTTP/1.1) &localport; -- the local port handling the connection
&remoteport; -- the remote port handling the connection &localaddr; -- the local address for the connection &remoteaddr; -- the remote address for the connection &getqa; -- Raw query string for args that are part of the url &postqa; -- Raw query string from a post
&detector -- the detector that fired
&detectorurl; -- a url that points to descriptive info about the detector &headers; -- all the http headers
Navigation:
Block Action – Blocking an action allows you to send the HTTP response code of your choice and an accompanying message. There is a list of HTTP response definitions and codes at the end of this document.
Redirect Action – Allows you to redirect the attacker to a website of your choice.
Ex: http://www.fbi.gov/
Butterfly Security CodeSeeker Application Security Solution Help
14

Reports
Built into CodeSeeker is a powerful reporting tool that allows you to view activity from a very high-level graph to an individual request. CodeSeeker may take some time to retrieve report information if you have a large number of servers in a Policy or have had a large attack. The pie charts will appear gray while CodeSeeker is compiling report information.
You can click the pie graphs Top Level Domains, Detectors, and URL’s, for more information on the attacks. The Total Requests pie graph is only an overview of the graphs below and cannot be clicked on for more information.
Butterfly Security CodeSeeker Application Security Solution Help
15

To get specific information on the type of attack on your servers, click a section of the overview pie chart shown above.
Click an individual type of attack to get a list of specific times, dates, and information on who has been attacking your server for the type of attack you chose above.
Butterfly Security CodeSeeker Application Security Solution Help
16
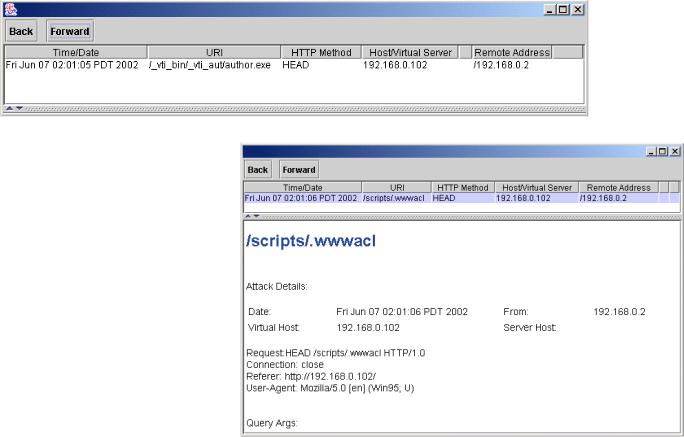
You can then click an item within the list to get detail of the specific attack you are interested in.
You can always use the Back and Forward buttons at the top of the report window to scroll back and forward through the reports you have viewed.
Butterfly Security CodeSeeker Application Security Solution Help
17
