
- •Product Overview
- •System Specifications
- •Installation
- •Adding a User Name and Password for CodeSeeker
- •Installing ISAPI Filter into IIS 5 for Windows 2000
- •CodeSeeker Management Console Overview
- •Policy Information
- •Customizing Security Policies
- •Reports
- •Analyzing and Customizing CodeSeeker
- •Servers
- •Dot Detector
- •Hidden file detector
- •HT Configuration File Detector
- •Common Command Detectors
- •Cmd.com Script Detector
- •Null Byte Detector
- •Unicode Detector
- •Buffer Overflow Detector
- •Multiple SQL Statements Detector
- •/etc/passwd File Detector
- •/etc/shadow File Detector
- •/etc/hosts File Detector
- •Summary of Regular-Expression Constructs
- •Backslashes, escapes, and quoting
- •Line terminators
- •Unicode support
- •HTTP Status Codes
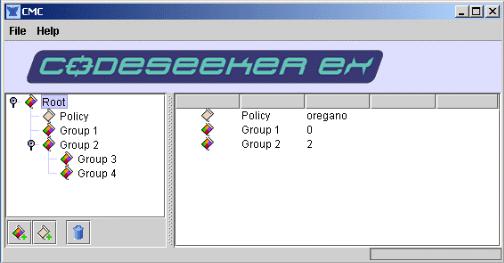
CodeSeeker Management Console Overview
The CodeSeeker Management Console allows you to monitor and adjust the security policies of your web servers. From a single console you can manage an infinite number of servers and their security policies by grouping policies and servers in a tree that is similar to Windows File
Explorer.
 Adding Policies – Policies are security rule sets for web servers. You may have as many servers as you want within a policy and they are not limited by physical or network location. Click the Add a Policy button to create a new policy. You will be prompted for a Policy Name (which can always be changed) and a Server Address. The Server Address is the primary server where the policy is kept, so you should choose a secure, stable server for the Server Address.
Adding Policies – Policies are security rule sets for web servers. You may have as many servers as you want within a policy and they are not limited by physical or network location. Click the Add a Policy button to create a new policy. You will be prompted for a Policy Name (which can always be changed) and a Server Address. The Server Address is the primary server where the policy is kept, so you should choose a secure, stable server for the Server Address.
 Adding Policy Groups - Policy Groups are simply folders that allow you to keep similar policies together. You can nest folders within folders to create an easy-to-manage hierarchical structure of your web servers.
Adding Policy Groups - Policy Groups are simply folders that allow you to keep similar policies together. You can nest folders within folders to create an easy-to-manage hierarchical structure of your web servers.
 Deleting Policies or Policy Groups – Please note that there is no undo with the delete button. Choose a policy or group from the left hand tree to delete and click the delete button.
Deleting Policies or Policy Groups – Please note that there is no undo with the delete button. Choose a policy or group from the left hand tree to delete and click the delete button.
Changing the name of a Policy or Policy Group – Double click the Policy or Policy Group that you want to rename.
Butterfly Security CodeSeeker Application Security Solution Help
8
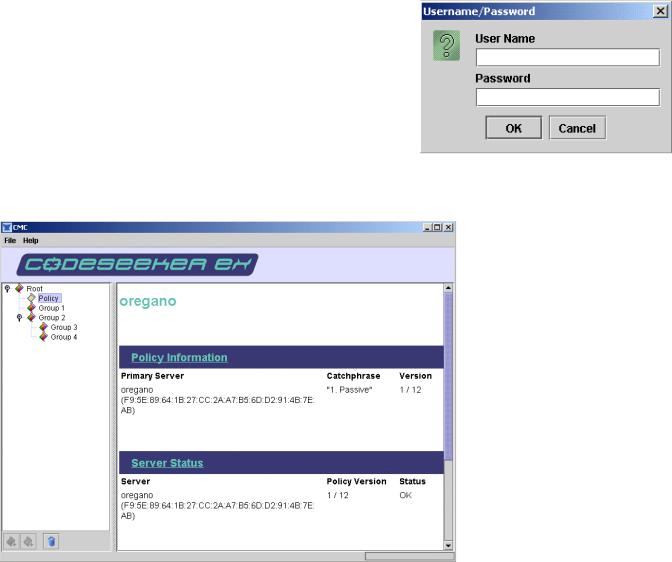
Viewing a Policy or Policy Group – Single-click the
Policy or Policy Group you want to view. If it is the first time you are viewing this group, you will be prompted to enter a User Name and Password. This is the username and password that was created by the CodeSeeker User
Password Utility.
Policy Overview – Policies are the rule sets used to manage the security of your servers. You may have as
many servers you want within a policy. However, it is suggested that the group of servers within a policy have similar software configurations and function within your infrastructure.
Policy Information / Primary Server – The Primary Server is the server that keeps policy information. It is suggested that this server be always available and secure. Single-click Policy Information for detailed information about the policy.
Server Status – This lists the servers within a Policy and their status. There are two version numbers listed with each server. The first is a Policy Version Number; the second is a
Signature Number.
Policy Version Number – Policy Version Numbers should all match within the same policy. If a server is offline when a new policy is pushed out it’s policy will no longer be synchronized with the other servers. Double click this server; you will be prompted to update its policy to the current one.
Signature Number – Butterfly Security is constantly updating its security signatures to help you pinpoint the specific type of attack against your web server. Attacks covered by the Specific Signatures are also covered by the Generic Signatures. With this in mind, you do not need to be up on the latest signature file to get quality protection with CodeSeeker.
Butterfly Security CodeSeeker Application Security Solution Help
9
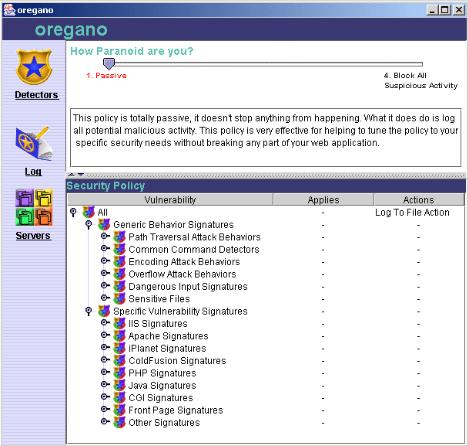
Policy Information
The Policy Information page allows you to view and alter any portion of a security policy for your servers. You can access this page by either single-clicking Policy Information on the Policy Overview page or by single-clicking the Detectors button on the left hand side of the
Information page.
Policy Slider Bar Mode Selector – At the top of the Policy Information page there is a horizontal slider bar that allows you to easily change the level of security for your web servers. When you first install CodeSeeker on a new set of servers, it is strongly suggested you set security in the Passive mode.
Passive – Passive mode is used to observe and log all questionable transactions on your web servers. The majority of these transactions will probably be malicious; however, there may be a particular type of transaction that is necessary for your server application to function normally. If this is a new install, or if you are making significant changes to the web servers, you will want to run CodeSeeker in the passive mode to monitor and collect data about the server transactions.
When testing the server in passive mode, be sure to hit the web server with every type of transaction possible in daily operation.
After running in Passive Mode, you will need to perform a quick analysis of the logs that have been collected so that you do not end up over-securing the server and crippling functionality.
Butterfly Security CodeSeeker Application Security Solution Help
10
Butterfly Security can assist with this analysis. This analysis and using it is covered in the
Analyzing and Customizing section of this document.
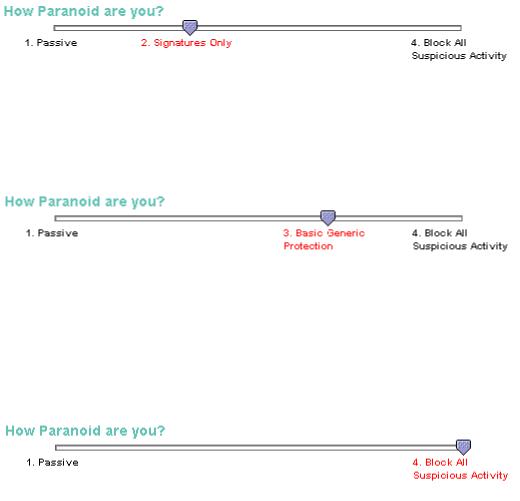
Signatures Only – The Signatures Only mode utilizes the CodeSeeker signature file to scan for known attacks only. Since no heuristics are used in this mode, it is important to maintain your signature updates to keep your site secure. Using signatures allows you to specifically see what type of malicious activity may be occurring on your web server. You may always customize your security by manually adding Generic Security items in addition to the Signatures Only.
Basic Generic Protection – Basic Generic Protection is using heuristics only to protect your web servers. Butterfly Security has compiled a database of methods of web server attacks.
CodeSeeker monitors web transactions and will take action when one of these methods occurs.
You may customize your security by manually selecting additional specific Signatures for
CodeSeeker to monitor.
Block All Suspicious Activity – In this mode, CodeSeeker will block all suspicious activity using both Signatures and Generic Protection. The combination of Signatures and Generic
Protection allows CodeSeeker to monitor and act on both known and unknown transactions on the web server. You may always customize your security by de-activating specific Signatures or types of Generic Protection. Once you have an assessment of what types of transactions your web server is running, it is suggested that you operate in this mode with customization to security policies as needed.
Butterfly Security CodeSeeker Application Security Solution Help
11
