
Professional ASP.NET Security - Jeff Ferguson
.pdf
Configuring IIS for Security
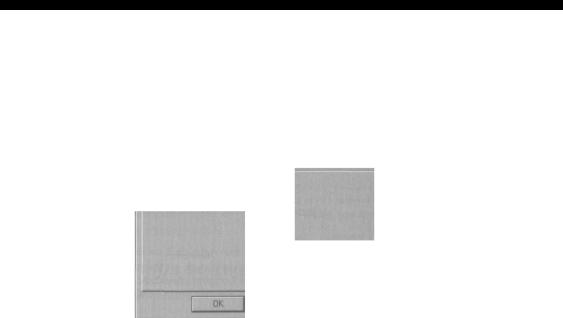
[Application Configuration
App Mappings App Options | App Debugging |
Application Configuration P"
Enable session state
Session timeout: |2Q minutes
P" Enable buffering P"
Enable patent paths
; Default ASP language: [VBScript i
ASP Script timeout: (90 |
" •- |
Help
Apply
Cancel
Removing IIS Samples
When IIS is installed, it conies with few sample applications that demonstrate how to set up and use the technology. As I have already suggested, it is highly advisable to remove these IIS samples from the production server. These samples leave the server vulnerable to attack, because a hacker will know where they are located, and how they may be utilized in mounting an attack. For example, suppose we've installed the IIS Admin Web Site. If the hacker knows about this, they can try to break into the system and start controlling IIS from there.
It is also highly recommended that you consider removing the other virtual directories that are no longer in use. You might also consider removing the IIS Administration virtual directory, unless it is absolutely necessary to keep it. The following table lists samples that you should remove from the server before going live.
IIS Sample |
Virtual Directory |
IIS Samples |
\IISSamples |
IIS Documentation |
\IISHelp |
Data Access |
\MSADC |
The IIS 4 server includes the IISADMPWD virtual directory that allows the users to reset the Windows password. If you've upgraded to IIS 5 from IIS 4 then this IISADMPWD virtual directory is not removed. The IISADMPWD virtual directory is only suitable for an intranet scenario, and it should be removed if the IIS server has an Internet presence.
3RQ
For more information about the security threads associated with the IISADMPWD virtual directory, refer to the Microsoft support article Q] 84619.
Disabling Unused COM Components
For many web applications, not every COM component installed on the server is required. The unused COM components, such as File System Object, should be removed, since they can be used to attack the server. We can use the Regsvr32 utility with /u command line switch to un-register COM components.
Enabling Logging
Logging the HTTP requests received at IIS is a good option to configure, since the logging enables us to validate what the server is doing at any given time, including how the security scheme that we've configured is working.
Logging can be enabled using IIS MMC. Start IIS MMC and right-click on the web site or the virtual directory where you want the logging to be enabled, then right-click on the tree node and select the Properties option. In the Web Site tab, check the Enable Logging checkbox. When enabling the logging make sure you select the W3C Extended Log File Format in IIS MMC and filter the Extended Properties tab with the following options checked:
a Client IP Address
a User Name
a Method
a URI Stem
a HTTP Status
Q Win32 Status
Q User Agent
a Server IP Address
a Server Port
These log entries will provide comprehensive information about the incoming requests to IIS. The IIS log files can come under attack, or a hacker might even try to delete the IIS log file in order to conceal any tampering that they've been doing. So it is very important that we protect the IIS log files by configuring our ACL appropriately. Make sure the IIS log files generated at %systemroot%\system32\LogFiles have the following ACLs: this will prevent the hacker from deleting the IIS log files and covering their tracks.
a Administrators (Full Control) a
System (Full Control) a
Everyone (RWC)
390
Configuring IIS for Security
The IIS log file can also be visited and exposed to the world by web bots, spiders, crawlers, and other programs trying to index the entire Web. We don't want the log files to be exposed to the entire world, so we should also protect our log file from the indexing programs using the robots . txt file. This will prevent web spiders from indexing the file into their search engine content. So if someone searches for the log file, our log files will not be shown in the search results.
The robots . txt file can be used to turn off all indexing by using the following two lines.
# Discourage all web indexing User-agent: * Disallow: /
For more information about the robots, txt file, visit the following URLs:
http://www.robotstxt.org/wc/exclusion.htmlttrobotstxt
http://www.google.com/bot.html
Installing Anti-virus software
Installing anti-virus software on the server and updating it everyday is essential to protect the IIS server. Many of the anti-virus softwares, such as Norton's Anti-virus Corporate and Professional Editions, allow automatic update via the Internet or from some other source.
Microsoft Data Access Components Security
One of the most common attacks against IIS is exploding the DataFactory object of Remote Data Services (or RDS), a part of MDAC. This object exposes unsafe methods to execute shell commands on IIS. It can also enable an unauthorized user to connect to any secure private backend data source, and execute any SQL statements using the ODBC drivers, and grants access to the secured non-published files on the IIS server. The .NET Framework installs MDAC 2.7 as part of .NET installation.
We should consider undertaking the following steps in order to secure the MDAC components:
D To prevent any kind of attack using the MDAC components, first disable anonymous access to the mdac virtual directory in IIS.
G If your web applications are not using RDS functionality, then you should remove the following registry keys:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W3SVC\Parameters\
ADCLaunchXRDSServer.DataFactory
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W3SVC\Parameters\
ADCLaunch\AdvancedDataFactory
G Remove all unused ODBC drivers from the Windows server, especially the Microsoft Text Driver. Then apply the tight ACLs to provide access to trusted user accounts.

If using SQL Server, then run it with a user account that has few privileges, and do not allow extended stored procedures.
Locking Down IIS
Microsoft provides a free tool called IIS Lockdown Wizard that can make life easier when configuring IIS for maximum protection. The IIS Lockdown Wizard automates many of the points that we've already discussed. For example, if we use the wizard correctly, it can remove the unwanted file extensions such as . idc, itr, .printer, and so on, from IIS file mapping. The wizard also includes a tool called UrIScan. This is an ISAPI filter that screens and analyzes all the HTTP requests IIS receives. When there is a restricted character, or a restricted string of characters (which we can set using UrIScan), IIS will reject the HTTP request.
The IIS lockdown wizard can be downloaded at: http://www.microsoft.com/technet/security/tools/locktool.asp. The IIS lockdown wizard provides multiple templates to configure IIS in the way that best suits your current needs.
Server Templates
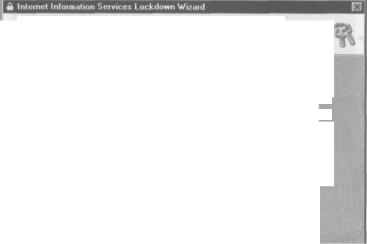
The lockdown wizard comes with a few predefined templates for common uses of IIS. The first step in the lockdown wizard is the select a template that matches your use of IIS. When you use the IIS Lockdown Wizard, it'll guide you through the removal of all the features that you don't need. Removing these will decrease the possibility of an attack.
m Internet Information Set vices Lockdown Wizard
Select Server Template
You can easily configute this server by selecting the template that most closely matches its role.
Select the template that most closely matches the role o? this server. To view the settings for this template, select the View template settings check box, and then click Nest.
Seivei templates:
Small Business Server 2000
E xchange S erver 5.5 (0 utlook Web Access]
Exchange Server 2000 (OWA, PF Management, I .SMTP.NNTP)
SharePoint Portal Server
FrontPage Server Extensions
SharePoint Team Services
BizTalk Server 2000
Commerce Server 2000
Proxy Server |
|
S tatic Web server |
_____________________ |
it-firr (Server that does not match any of the listed roles)
MP, fhaf rin^t nnf rpni HIP- 11^
'View template setthgs
< Back |
I |
Help |
Next > |
|
|
392
Configuring IIS for Security
If your web application simply hosts files necessary for a dynamic web applications, such as . asp and .aspx related files, then select Dynamic Web Server (ASP enabled) and click Next. If you check the View template settings checkbox, you'll be able to tailor the options that you want to enable or disable, rather than simply sticking with the default setting of the selected template.
If you don't see a template that fits best for your IIS role then you can select Other (Server that does not match any of the listed roles) and this will give you full control over how IIS should be configured.
Internet Services
If you've checked the View template settings option on the first screen, you'll see the Internet Services screen:
Internet Services
Services that are already selected are recommended for this server template
;t the internet services to enable cm this server. Services not selected wiH be disabled
P7 Web service (HTTP)
This service uses HTTP to respond to Web dent requests on a TCP/IP network.
f~ Fife Transfer service (FTP)
This service supports the creation of Fie Transfer Protocol JFTP) sites used to transfer fifes to and from the Internet.
F E-mail service (SMTP)
This service uses the Simple Mail Transfer Protocol (SMTP) to send and receive e-mail
r
1 Remove unseleeted services
Nex» |
Cancel |
Help |
This screen allows us to enable and disable various options. For example, if you're not going to use FTP, SMTP, or NNTP services, then you can disable them.
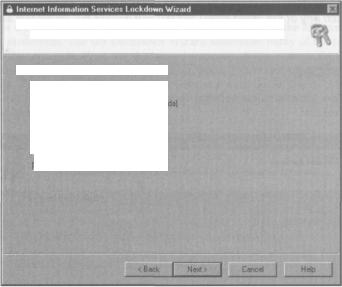
Script Maps
The next screen in the wizard enables us to customize the types of script mapping that you're using. Note that on this screen, unlike the previous screen, we have to select those things that we wish to disable.
Script Maps
Because script maps can pose a security risk, you can disable them on this server
Disable support rot the selected script maps:
I"~ Active Soever Pages (. asp}
p Index Server
p Savetskfe includes (.sbtrcl .sHnx .stm) p inteinel Data Connector (.&dc)
p .NIB scripting (.Mr)
7 Inteinei printing (.priiitef)
When IIS receives a request for a file type that is mapped, the call is handled by the DLL to which it is mapped. If you don't use these file types, it is better to remove their mapping from IIS. This will reduce security threats.
Additional Security Settings
The next screen enables us to configure additional security settings. By default, it'll remove the sample applications that come with IIS. Optionally, we can remove the following:
Q IIS Help options
Q The ability to run system commands such as Cmd. exe and Tf tp. exe with anonymous user privileges
Q The ability to write content to the web site or virtual directories
Q The ability to author content to the web server using WebDEV in a distributed environment
394

Configuring IIS for Security
Remove the selected virtual directories from tNs setvef (items that appear unavailable have already been removed]:
Additional Security
You can make additional changes to this server for added security.
p tIS Samples |
(7 Scripts |
|7 MSADC |
P " U S A * * * |
17 IISHeip |
|
Set fi!e permissions to prevent anonymous IIS users from performing these actions: [•? Running system utilities (for example, Cmd.exe, Tftp.exeJ 17 Writing to content directories
p" D isabte Web D istributed Authoring and Versioning (V-/ebDAV]
If you're not going to use any of the options from the production server, it is better to disable them.
UrIScan
The next screen enables us to install the UrIScan utility. UrIScan is an ISAPI filter that monitors and analyzes incoming HTTP requests to IIS. When the UrIScan utility is configured properly, it can function as an effective tool in reducing potential attacks against IIS.
For instance, the UrIScan utility can be configured to reject HTTP requests, depending on the following criteria:
Q The HTTP request verb, such as GET or POST Q The extension of the requested resource
Q Suspicious characters in the URL encoding format (for example, suspicious characters such as < or > could be rejected)
Q Non-ASCII characters in the requested URL
Q Specified character sequences or specified headers in the HTTP request
The UrIScan parameters are configurable by the administrator in the UrIScan. ini file in the %Windir%\System32 folder. The lockdown wizard includes several versions of the UrIScan. ini file. The version that is installed will depend on which template is selected. The UrIScan. ini file has sections for each of the configuration options. The UrIScan utility generates a log file, UrIScan. log, which gives information about the status of the utility, including the HTTP requests it rejected.
For example, if we only want to allow HTTP HEAD and POST methods to be used, we would enable the UseAllowVerbs setting to 1 and specify the allowed HTTP methods (HEAD and POST) in the AllowVerbs section:
[options]
UseAllowVerbs=l
[AllowVerbs] HEAD
POST
If we only want to allow .aspx, .ascx, .asax, .htm, .html, .jpg, . jpeg, and .gif file types, we would use the following:
[options]
UseAllowExtensions=l
[AllowExtensions]
.aspx
.ascx
. asax
.htm
.html
•jpg
•jpeg
.gif
If we want to deny certain extensions, such as . com, . exe, . bat, and . cmd from the URL, we can use the following settings:
[options]
UseAllowExtensions=0
[DenyExtensions]
. exe
.bat
.cmd
.com
After installing and configuring the UrlScan utility, you might find that you cannot debug ASP.NET applications from VS.NET. Information about how to fix this might be found in the Microsoft Support Article PRB: Security Toolkit Breaks ASP.NET Debugging in Visual Studio .NET (Q310588) at: http://support.microsoft.com/default.aspx?scid=kb;EN-US;q310588&GSSNB=1.
Final Points
The Lockdown Wizard installation will present us with a list of all the security settings we've selected, before configuring our server.
396
Configuring lib tor security
After using the IIS Lockdown Wizard to configure the IIS server, make sure you test the application before putting it in production. If you find the configuration is not working for you, re-run the IIS Lockdown Wizard again and it will undo the changes that were made.
Securing Telnet
If you are planning to include the Telnet service where IIS resides, consider restricting the users who can access the Telnet service. We can secure the Telnet service by creating a new Windows group called TelnetClientS, and add the appropriate Windows user accounts to the group. When the TelnetClientS group exists, the Telnet service will allow only those users defined in the group.
Summary
In this chapter, we went through a detailed tour of Windows OS and IIS security. We started this chapter with where security starts, and its evolution. Then we went through the details of security planning: how to secure Windows and Telnet services.
We have investigated a few tips to secure IIS, such as:
Q Configuring access control lists
Q Disabling parent path browsing
Q Removing IIS samples
G Removing or disabling unused COM components
Q Enabling logging
Q Installing anti-virus software
We have also looked at the security threat exposed by RDO, and how to use the IIS Lockdown Wizard and UrlScan utility.
397
