
- •Contents
- •Preface to second edition
- •1 Introduction
- •1.2 Applying technology in an environment
- •1.3 The human role in systems
- •1.4 Ethical issues
- •1.7 Common practice and good practice
- •1.8 Bugs and emergent phenomena
- •1.10 Knowledge is a jigsaw puzzle
- •1.11 To the student
- •1.12 Some road-maps
- •2 System components
- •2.2 Handling hardware
- •2.3 Operating systems
- •2.4 Filesystems
- •2.5 Processes and job control
- •2.6 Networks
- •2.7 IPv4 networks
- •2.8 Address space in IPv4
- •2.9 IPv6 networks
- •3 Networked communities
- •3.1 Communities and enterprises
- •3.2 Policy blueprints
- •3.4 User behavior: socio-anthropology
- •3.5 Clients, servers and delegation
- •3.6 Host identities and name services
- •3.8 Local network orientation and analysis
- •4 Host management
- •4.1 Global view, local action
- •4.2 Physical considerations of server room
- •4.3 Computer startup and shutdown
- •4.5 Installing a Unix disk
- •4.6 Installation of the operating system
- •4.7 Software installation
- •4.8 Kernel customization
- •5 User management
- •5.1 Issues
- •5.2 User registration
- •5.3 Account policy
- •5.4 Login environment
- •5.5 User support services
- •5.6 Controlling user resources
- •5.7 Online user services
- •5.9 Ethical conduct of administrators and users
- •5.10 Computer usage policy
- •6 Models of network and system administration
- •6.5 Creating infrastructure
- •6.7 Competition, immunity and convergence
- •6.8 Policy and configuration automation
- •7.2 Methods: controlling causes and symptoms
- •7.4 Declarative languages
- •7.6 Common assumptions: clock synchronization
- •7.7 Human–computer job scheduling
- •7.9 Preventative host maintenance
- •7.10 SNMP tools
- •7.11 Cfengine
- •8 Diagnostics, fault and change management
- •8.1 Fault tolerance and propagation
- •8.2 Networks and small worlds
- •8.3 Causality and dependency
- •8.4 Defining the system
- •8.5 Faults
- •8.6 Cause trees
- •8.7 Probabilistic fault trees
- •8.9 Game-theoretical strategy selection
- •8.10 Monitoring
- •8.12 Principles of quality assurance
- •9 Application-level services
- •9.1 Application-level services
- •9.2 Proxies and agents
- •9.3 Installing a new service
- •9.4 Summoning daemons
- •9.5 Setting up the DNS nameservice
- •9.7 E-mail configuration
- •9.8 OpenLDAP directory service
- •9.10 Samba
- •9.11 The printer service
- •9.12 Java web and enterprise services
- •10 Network-level services
- •10.1 The Internet
- •10.2 A recap of networking concepts
- •10.3 Getting traffic to its destination
- •10.4 Alternative network transport technologies
- •10.5 Alternative network connection technologies
- •10.6 IP routing and forwarding
- •10.7 Multi-Protocol Label Switching (MPLS)
- •10.8 Quality of Service
- •10.9 Competition or cooperation for service?
- •10.10 Service Level Agreements
- •11 Principles of security
- •11.1 Four independent issues
- •11.2 Physical security
- •11.3 Trust relationships
- •11.7 Preventing and minimizing failure modes
- •12 Security implementation
- •12.2 The recovery plan
- •12.3 Data integrity and protection
- •12.5 Analyzing network security
- •12.6 VPNs: secure shell and FreeS/WAN
- •12.7 Role-based security and capabilities
- •12.8 WWW security
- •12.9 IPSec – secure IP
- •12.10 Ordered access control and policy conflicts
- •12.11 IP filtering for firewalls
- •12.12 Firewalls
- •12.13 Intrusion detection and forensics
- •13 Analytical system administration
- •13.1 Science vs technology
- •13.2 Studying complex systems
- •13.3 The purpose of observation
- •13.5 Evaluating a hierarchical system
- •13.6 Deterministic and stochastic behavior
- •13.7 Observational errors
- •13.8 Strategic analyses
- •13.9 Summary
- •14 Summary and outlook
- •14.3 Pervasive computing
- •B.1 Make
- •B.2 Perl
- •Bibliography
- •Index
Chapter 10
Network-level services
Networks are usually presented as an invention of the post Second World War cold war climate, but the first wired communication networks were built by the Victorians in the 1800s. Sir Francis Ronald was the first person to appreciate the need for telegraphic communication. In the first publication on the subject in 1823, he proposed a method for locating faults on a telegraph line. W.F. Cooke and Charles Wheatstone, professor of Physics at King’s College, London produced their first telegraph patent in June 1837 and tested it over the mile-long line between two London railway stations. Samuel Finley Breese Morse had the idea for electrical communication in 1832 but did not produce a working telegraph in the United States until 1836 [66].
The first attempt to lay an underwater cable was begun in 1850, when a steam tug drew a single copper wire from Dover out across the ocean to Cap Gris-Nez. Unfortunately after only a day the cable broke around the French coast. Politics and rivalry intervened until it was left to Lord Kelvin (William Thomson) to show how low-power signals could be transmitted effectively over huge distances. Many failures were encountered before finally, on the 27th of July 1866, the steamboat Great Eastern delivered a cable from England’s Valentia Bay to Heart’s Content in North America. On the first day of operation the cable earned one thousand pounds. This was the birth of Internet commerce.
10.1 The Internet
One of the false myths about the Internet was that it was developed by the American military as a communications system that could survive a nuclear attack. In 1964, a researcher at the RAND corporation, Paul Baran, wrote a paper describing how different network topologies would be robust to failure (see chapter 8). This included many ideas that would eventually be incorporated into current networking technologies, but the idea was not taken up. Later, the American Department of Defence’s Advanced Research Project Agency (DARPA) began a project to find ways of gaining access to expensive computing machinery remotely; the cost of duplicating computing services, at the time, was insurmountable so the logical solution was to find a way of accessing the services remotely.
392 |
CHAPTER 10. NETWORK-LEVEL SERVICES |
The invention of packet switching was key in allowing networks to share bandwidth between multiple computers. The strength of the Internet Protocol was in being able to integrate many existing technologies for point to point connections (like X.25) that were deployed in Europe. Unix was instrumental in the spread of the Internet Protocol suite (nowadays referred to as TCP/IP). The fact that the Internet has developed into many of the things that Baran foresaw is a testament to his foresight, rather than a feat of planning. Internet development has meandered through differing technologies, driven by commercial forces such as telecom companies and standardizing bodies such as the IETF.
10.2 A recap of networking concepts
Here is a summary of what we assume understood at the beginning of this chapter:
•Computers communicate by sending electrical or optical signals over wires or fibers.
•Short cables can only ‘hold’ one bit at a time. A bit floods a cable or fiber like signaling Morse code with a torch, and has a physical size normally equal to the fundamental wavelength of the binary signal. The signal spreads through the medium in all directions at anything up to the speed of light in the medium.
•Each computer has a hardware interface at layer 1 of the OSI model.
•Each interface has a Media Access Control (MAC) address at layer 2, e.g. an Ethernet address such as 00:90:27:A2:47:7B.
•All hosts connected to the same cable see all the signals passing through it, but messages are framed using a protocol that incorporates a MAC address, and only the host with the correct MAC address normally bothers to read a message with its address. (A computer that listens to all traffic is said to be in promiscuous mode.)
•MAC addresses are ‘flat’; they have no structure, so the only way to find a host with a given MAC address is to either direct the message over a dedicated path, or send a message to every computer and wait for the right one to respond. This is impractical in large networks, so we need another layer of addressing: layer 3.
•A message sent to one computer from another is called a unicast.
•A message sent from one computer to all computers on a Local Area Network (LAN) is called a broadcast.
•When multiple cables are joined together as part of an Internetwork, they must be joined by a router. If the cables are part of the same logical IP network, they are joined by a switch (or a bridge, which is an old name for a primitive switch).
10.3. GETTING TRAFFIC TO ITS DESTINATION |
393 |
10.3 Getting traffic to its destination
How do data get ‘here’ from ‘there’ and from ‘there’ to ‘here’? This is a complex question that flirts with a number of quite independent issues, making its answer seem often unnecessarily opaque. We shall try to approach the answer in a number of stages. Two particular problems lie at the heart of getting traffic to its destination:
1.Directing packets to their proper destination.
2.Scheduling packets for transmission over a shared channel.
These two, obviously independent, issues become entwined because the hardware and software that deal with delivery are also forced to deal with the sharing. System administrators are barraged with technical specifications and explanations of these issues when purchasing and installing network infrastructure. A basic understanding of the issues is important.
10.3.1Multiplexing
As with many problems in computing, we begin with resource sharing. Cable technologies have in-built limitations: only one user can send data at a time, so we use a form of packet switching. A contiguous Ethernet, for instance, can only span a distance of, at most, 5000m with a minimum packet size of 64 bytes. This value is normally halved to 2500m to allow a wide margin for error (see section 10.4.3). If these limits are exceeded, the expected collision rate leads to thrashing of the scheduling algorithm and network gridlock.
Even if it were possible, it would never be practical to build such a network covering the world: with hosts broadcasting to every other machine in order to find one another, the number of collisions would be enormous – why should a host in Norway be prevented from using the network by a host in the United States, or vice versa? Clearly, one must devise a way of structuring the flow of traffic to avoid unnecessary contention.
This can be done by packet switching. Switching uses essentially two strategies to form multiple channels from a single resource:
•Time Division Multiplexing: interleaving packets in time-slots (scheduling).
•Wave Division Multiplexing: choosing different wavelengths or frequencies to encode signals. This is sometimes referred to as Lambda (λ) Switching in fiber optic networks.
10.3.2From bridges to switches
Directing traffic in a Local Area Network (LAN) is simple. In older Ethernet networks, cables were simply spliced by hubs, and occasionally broken up by bridges that would stop traffic from crossing a boundary unless it needed to. Today, bridges and hubs have been combined into star-topology LAN switches (figure 10.1).
394 |
CHAPTER 10. NETWORK-LEVEL SERVICES |
LAN switch
To router
Figure 10.1: A LAN switch normally offers a separate channel to each host on the LAN, though it is still possible for a few hosts to share a channel using a cable splitter or hub. Traffic is switched from channel to channel and hosts that do not need to see it, do not see it. Switching is fast and efficient. The switch prevents a router from being exposed to LAN ‘chit-chat’.
LAN switches are very successful in passing traffic from one host to another without creating unnecessary contention elsewhere in the network.
LAN switching is straightforward, but to cover a large area it is not enough to tap into a single cable, we must also have crossroads and intersections (see figure 10.2). At each junction, a decision has to be made about which way traffic will be forwarded. We thus have to multiplex not only single cables, but junctions. This traffic flow control at junctions is exactly what happens in a star topology, but what happens when two stars are connected?
Can packets now find their way to their destination? Can this model scale to any number of hosts? It can scale to some extent, but not indefinitely: the limitations of Ethernet prevent us from growing Ethernet indefinitely, but even with a better link layer, a flat address space would be extremely inefficient. One must therefore place something in between Ethernets that can span larger distances: Wide Area Networks (WAN). This now involves the IP address of hosts in a more important way, and we need a new kind of hardware: a router.
The terms switch and router are becoming increasingly mixed up as technologies evolve. These two devices seem to perform similar tasks, but at different layers of the puzzle.
•A switch is a device that forwards packets according to a forwarding table using MAC addresses of the interfaces that it is connected to as an index. Switching is so simple that it can be completely hardwired, if necessary, so it is quite efficient to switch packets. This lack of intelligence has a price however: a switch needs help in order to build a forwarding table – i.e. to
10.3. GETTING TRAFFIC TO ITS DESTINATION |
395 |
C1
C2
I1
|
|
I2 |
|
I4 |
|
|
I3 |
C3 |
|
|
|
|
|
I5 |
|
|
I6 |
C4 |
|
C5 |
|
|
i/ |
|
|
C6 |
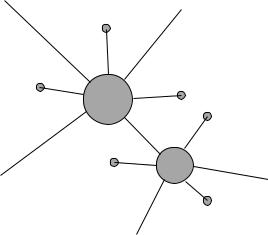
Figure 10.2: Junctions of |
cables are required to create a non-trivial network topol- |
|
ogy. The blobs represent ‘forwarding agents’ or switches that can receive data from a cable C1 . . . C6 attached to an incoming interface I 1 . . . I 7 and pass it to a different cable attached to a different interface. This is how traffic can be passed around a network with junctions.
find out how it can reach a particular computer MAC address along one of its interfaces. In some cases, this task is very simple: simple Ethernet star-formation networks attach each computer to a single interface of a switch, so it is easy to build a table of associations. Other technologies, such as ATM, Frame Relay and MPLS (see section 10.5) are less easily defined than this: they do not work in the same way as Ethernet, and they allow more complicated switching over wide areas, through several switches, but they help in order to assemble the information in their forwarding tables. This help can be manually added by a system administrator, or it can be automated by linking the layer 2 switching to a layer 3 routing algorithm. In the latter case, some manufacturers are starting to talk about ‘layer 3 switches’.
•A router is a specialized computer, running on software, that probes and determines the global topology of the network and decides how to forward packets. It can replace, supplement or assist a switch in forwarding packets. In order to succeed at this, a router needs to understand OSI layer 3, or the IP layer, and sometimes has occasion to examine levels 4–7 in making decisions. The IP layer is based on an address structure that is hierarchical and can therefore be navigated automatically.
Confusion arises between routing and switching when one begins to discuss the methods and algorithms for forwarding packets. A router matches hierarchical IP address prefixes (layer 3) in order to determine the right forwarding path. A
396 |
CHAPTER 10. NETWORK-LEVEL SERVICES |
switch uses layer 2 addresses in a flat table for forward packets. Today, the market uses expressions like ‘layer 3 switch’ to talk about hybrid devices that optimize tasks by caching the information from a layer 3 router in the forwarding table of a layer 2 switch for improved efficiency. However, fully-blown routers perform functions other than forwarding, such as access control and filtering of packets.
10.3.3Virtual circuits and wide area switching
In Wide Area Networks (WAN), and moderately sized areas, often called Metropolitan Area Networks (MAN), it is possible to direct traffic by switching alone. Although Ethernet is limited in its coverage, other transport technologies like Frame Relay and ATM can be transported by fibers over larger areas. Frame Relay and ATM lie somewhere in the gray area between layer 2 and layer 3 of the OSI Model, because they can be forwarded by switching alone using virtual circuits. (They do not ‘need’ the IP layer to get traffic from here to there, but they draw assistance from it.)
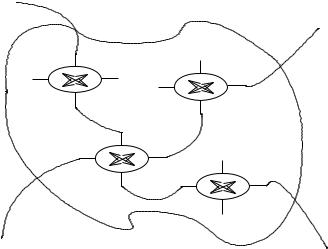
Virtual circuits have their origin in telephony and come in two forms: Permanent Virtual Circuits (PVC) and Switched Virtual Circuits (SVC). They are predetermined routes through a number of switches (see figure 10.3). The distinction refers to the way the circuits are administered. A permanent circuit is set up by an administrator for long-term usage; it is not expected to be rerouted. A switched circuit is established automatically by ‘signaling’; this requires the assistance of a protocol that understands the topology of the network, such as IP routing.
IN1
OUT2
SW1 SW2
SW3
SW4
IN2
OUT
Figure 10.3: An assembly of switches, connected by semi-permanent internal wiring (not shown), can be used to establish virtual circuits (dotted lines). In simple regions, this can be managed manually, or with assistance from routing protocols. Each separate virtual circuit can be switched using simple labels, without having to bother with level 3 IP addresses.
