
malware_report_vimal_kumar
.pdf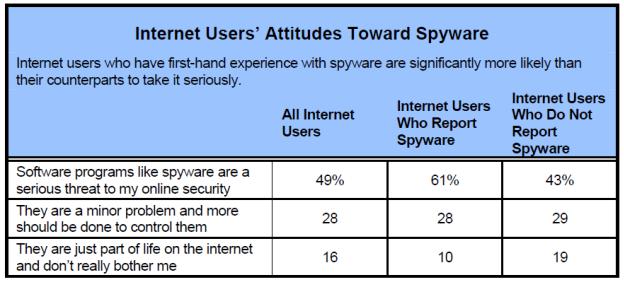
The study done by AOL/NCSA [12] found that, of all the people who had spyware on their computers only 5% had given the permission for their installation. Of course, the statement is not entirely correct as most of the spyware is mentioned in the EULAs. It should be said that only 5% of the people knowingly consented for the installation while the rest although unknowingly but still consented for its installation. This behavior stems from the unawareness and ignorance towards the ways of spyware. For reference I present a table below from the study in [7]. The table shows that people who have had experiences with spyware are more likely to be aware of it and thus are more likely to take preventive and corrective measures. If we can educate people about spyware and replace the experience with knowledge we can prevent spyware infections to a certain extent. Awareness of spyware and a little knowledge about its modus operandi, in my opinion can go a long way in helping to handle this menace.
Figure 5. Internet user's attitude toward spyware [7]
A second front would be the legal side of it. Spyware is thriving because of the laxity and the ambiguity of laws which exist. Also, because the definition of spyware is so hazy and merges with legal advertisement on its edges, it is difficult to identify and counter spyware without hurting legitimate businesses. A number of laws already exist to prevent the spyware and more and more states are crafting new laws but the need to protect legitimate businesses always leaves loopholes in such laws which can be exploited by the illegitimate ones. The efficiency of such laws is questionable; nevertheless these are steps in the positive direction. What is required in the future is a stricter definition of spyware and laws which can strongly prosecute the offenders. The implementation of these laws is possible in the United States and a few other countries in the world but there are no international boundaries on the internet. Thus, along with the stronger laws, there is a need for a global collaboration to deal with spyware.
The third and final part of the solution is the technical side of it. Recent advances in antispyware technologies are certainly helping to protect people against spyware. The focus is now shifting to proactive measures which detect and prevent spyware installation rather than the reactive measures for detection and removal after they have been installed. Real time protection, EULA analyzers [4] and interest based detection [17] are a few of those technologies which detect spyware before they start working and do not wait until they are done. A number of people in the academia and the industry have spotted the potential danger and a number of researchers are directing their attention towards this area of the malware industry. The emergence of companies like Microsoft, McAfee and Norton in the antispyware business is a harbinger of better things to come to the protection of people from this nuisance.
To conclude the report I would say that this growing dark cloud can only be prevented by a collective effort and collaboration from the internet users, researchers, corporations and the lawmakers alike. Spyware needs to be attacked from all sides possible to prevent it from owning the internet and everybody will have to do their bit. Aware internet users, stringent laws and advanced antispyware technologies are the answer to this growing threat.
11.References
[1]Lavasoft spyware study
http://www.lavasoft.com/support/spywareeducationcenter/spyware_statistics.php
[2]Plymouth Computer Doctor study http://www.plycomp.co.uk/virus-statistics-worldwide.html
[3]Baskin, Brian, and Tony Piltzecker. Combating spyware in the enterprise. 2006.
[4]Boldt, M, A Jacobsson, N Lavesson, and P Davidsson. "Automated Spyware Detection Using End User License Agreements." Information Security and Assurance, 2008. ISA 2008. International Conference on . Busan, 2008. 445-452.
[5]Boldt, Martin, and Bengt Carlsson. "Analysing privacy-invasive software using computer forensic methods." Detection of Intrusions and Malware & Vulnerability Assessment. 2006.
[6]eSoft. White Paper: Spyware Security and Privacy Protection. eSoft.
[7]Fox, Susannah. The threat of unwanted software programs is changing the way people use the internet. Pew Internet and American Life Project, 2005.
[8]Gibson, Steve. "Spyware was inevitable." Spyware, 2005: 37-39.
[9]Gralla, Preston. How Personal & Internet Security Works. Que, 2006.
[10]Hinde, Stephen. "Spyware: the spy in the computer." Computer Fraud and Security, 2004: 15-16.
[11]Moshchuk, E, Tanya Bragin, Steven D Gribble, and Henry M Levy. "A crawler-based study of spyware on the Web." 2006.
[12]NCSA, AOL and. "AOL/NCSA Online Safety Study." 2004.
[13]Omniquad. A white paper on Combating the Spyware menace: Solutions for the enterprise.
Omniquad, 2005.
[14]Poston, Robin, Thomas Stafford, and Amy Hennington. "Spyware: a view from the (online) street." Spyware, 2005: 96-99.
[16]Walker, Andy. Absolute Beginner's Guide to Security, Spam, Spyware & Viruses . 2005.
[17]Wang, Xiaoqiao, and Juanjuan Chen. "Interests-Based Spyware Detection." International forum on Computer Science-Technology and Applications, 2009: 175-178.
[18]Rasch, Mark. "Is deleting spyware a crime?" http://www.securityfocus.com/columnists/328, 2005 [19]EULAlyzer, http://www.javacoolsoftware.com/eulalyzer.html
