
- •Exploiting Software How to Break Code
- •Table of Contents
- •Copyright
- •Praise for Exploiting Software
- •Attack Patterns
- •Foreword
- •Preface
- •What This Book Is About
- •How to Use This Book
- •But Isn't This Too Dangerous?
- •Acknowledgments
- •Greg's Acknowledgments
- •Gary's Acknowledgments
- •Bad Software Is Ubiquitous
- •The Trinity of Trouble
- •The Future of Software
- •What Is Software Security?
- •Conclusion
- •Chapter 2. Attack Patterns
- •A Taxonomy
- •An Open-Systems View
- •Tour of an Exploit
- •Attack Patterns: Blueprints for Disaster
- •An Example Exploit: Microsoft's Broken C++ Compiler
- •Applying Attack Patterns
- •Attack Pattern Boxes
- •Conclusion
- •Into the House of Logic
- •Should Reverse Engineering Be Illegal?
- •Reverse Engineering Tools and Concepts
- •Approaches to Reverse Engineering
- •Methods of the Reverser
- •Writing Interactive Disassembler (IDA) Plugins
- •Decompiling and Disassembling Software
- •Decompilation in Practice: Reversing helpctr.exe
- •Automatic, Bulk Auditing for Vulnerabilities
- •Writing Your Own Cracking Tools
- •Building a Basic Code Coverage Tool
- •Conclusion
- •Chapter 4. Exploiting Server Software
- •The Trusted Input Problem
- •The Privilege Escalation Problem
- •Finding Injection Points
- •Input Path Tracing
- •Exploiting Trust through Configuration
- •Specific Techniques and Attacks for Server Software
- •Conclusion
- •Chapter 5. Exploiting Client Software
- •Client-side Programs as Attack Targets
- •In-band Signals
- •Cross-site Scripting (XSS)
- •Client Scripts and Malicious Code
- •Content-Based Attacks
- •Conclusion
- •Chapter 6. Crafting (Malicious) Input
- •The Defender's Dilemma
- •Intrusion Detection (Not)
- •Partition Analysis
- •Tracing Code
- •Reversing Parser Code
- •Misclassification
- •Audit Poisoning
- •Conclusion
- •Chapter 7. Buffer Overflow
- •Buffer Overflow 101
- •Injection Vectors: Input Rides Again
- •Buffer Overflows and Embedded Systems
- •Database Buffer Overflows
- •Buffer Overflows and Java?!
- •Content-Based Buffer Overflow
- •Audit Truncation and Filters with Buffer Overflow
- •Causing Overflow with Environment Variables
- •The Multiple Operation Problem
- •Finding Potential Buffer Overflows
- •Stack Overflow
- •Arithmetic Errors in Memory Management
- •Format String Vulnerabilities
- •Heap Overflows
- •Buffer Overflows and C++
- •Payloads
- •Payloads on RISC Architectures
- •Multiplatform Payloads
- •Prolog/Epilog Code to Protect Functions
- •Conclusion
- •Chapter 8. Rootkits
- •Subversive Programs
- •A Simple Windows XP Kernel Rootkit
- •Call Hooking
- •Trojan Executable Redirection
- •Hiding Files and Directories
- •Patching Binary Code
- •The Hardware Virus
- •Low-Level Disk Access
- •Adding Network Support to a Driver
- •Interrupts
- •Key Logging
- •Advanced Rootkit Topics
- •Conclusion
- •References
- •Index

Finding Potential Buffer Overflows
One naive approach for finding buffer overflows is simply to supply long arguments to a program and see what happens. Some of the "application security" tools use this simplistic approach. You too can do this by typing in long requests to a Web server or an FTP server, or
• |
Table of Contents |
crafting weird e-mail headers and submitting them to a sendmail process. This kind of black |
|
• |
Index |
box testing can be effective at times, but it is very time-consuming.
Exploiting Software How to Break Code
A much better way to test for buffer overflows is to find API calls that are vulnerable by using
ByGreg Hoglund,Gary McGraw
static analysis techniques. Using either source code or disassembled binary, this scanning can
be performed in an automated fashion. Once you find some potential vulnerabilities with
Publisher: Addison Wesley
static analysis, you can use black box testing to attempt to exercise them.
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
Pages: 512
Exception Handling Hides Errors
One thing you should be aware of when dynamically testing for possible overflows is that exception handlers may be in use. Exception handlers will intercept some violations, and thus
it may not be apparent even if you do cause an interesting overflow. If the program appears
How does software break? How do attackers make software break on purpose? Why are
to recover from a possible attempt to cause an overflow, and there is no external indication
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? of the event, then determining whether your probing is having any effect is difficult.
What tools can be used to break software? This book provides the answers.
Exception handlers are special blocks of code that are called when an error occurs during
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and processing (which is precisely what happens when a buffer overflow occurs). On the x86
techniques used by bad guys to break software. If you want to protect your software from processor, exception handlers are stored in a linked list and they are called in order. The top
attack, you must first learn how real attacks are really carried out.
of the exception handler list is stored at an address pointed to by FS:[0]. That is, the FS
register points to a special structure called the thread information block, and the first element This must-have book may shock you—and it will certainly educate you.Getting beyond the
of the structure (FS:[0]) is the exception handler.
script kiddie treatment found in many hacking books, you will learn about
You can determine whether an exception handler is being set up by using the following
instructions (the order of these instructions may vary depending on the phase of the moon, Why software exploit will continue to be a serious problem
so your mileage will vary with this trick):
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
mov eax, fs:[0]
 Techniques for crafting malicious input
Techniques for crafting malicious input
push SOME_ADDRESS_TO_AN_EXCEPTION_HANDLER
 The technical details of buffer overflows
The technical details of buffer overflows
push eax
Rootkits
mov dword ptr fs:[0], esp
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break software.
If you believe that an exception handler might be masking an error you have caused, you can
always attach to the process with a debugger and set a break point on the exception handler
address.

Using a Disassembler
A superior approach to probing around in the dark with dynamic testing methods is to use static analysis techniques to find overflow targets. One excellent place to start is with a disassembly of the binary. A quick look for static strings that contain formatting characters such as %s with a cross-reference back to where they are consumed provides plenty of attack fodder.
•Table of Contents
If• you approachIndexthings this way, you will usually see static strings referenced as an offset:
Exploiting Software How to Break Code
ByGreg Hoglund,Gary McGraw
Publisher: Addison Wesley
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
Pages: 512
push offset SOME_LOCATION
How does software break? How do attackers make software break on purpose? Why are
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys?
If you see this kind of code before a string operation, check to determine whether the address What tools can be used to break software? This book provides the answers.
points to a format string of some kind (indicated by %s). If the offset turns out to be a format
string, next check the source string to determine whether it happenspatterns,to be user-controlled Exploiting Softwareis loaded with examples of real attacks, attack tools, and
string. You can use boron tagging to help find these things out (see Chapter 6). If the offset techniques used by bad guys to break software. If you want to protect your software from
is used as the source of the string operation (and there is no user-supplied input), this attack, you must first learn how real attacks are really carried out.
location is most likely not vulnerable because the user cannot directly control the data. This must-have book may shock you—and it will certainly educate you.Getting beyond the
If the target of the string operation is on the stack, you might see it referenced as an offset script kiddie treatment found in many hacking books, you will learn about
from EBP. For example:
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software push [ebp-10h]
Classic attacks against server software push [ebp-10h]
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
This kindThe technicalofstructured tailsindicatesof bufferuse overflowsstack buffers. If the target of the operation is on the stack, then an overflow will be relatively easy to exploit. If there is a call to strncpy() or
Rootkits
something similar that specifies the size of the destination buffer, you might want to check
that the size is at least one less than the actual buffer length. We will explain this further
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break later, but the basic idea is that you might ferret out an off-by-one error where you can exploit
software.
the stack. Lastly, for any calculations made with reference to a length value, check for signed/unsigned conversion errors (which we will also explain further later).

Stack Overflow
Using buffer overflow against variables on the stack is sometimes called a stack overflow, and more often is called smashing the stack. Stack overflow is the first type of buffer overflow to be widely popularized and exploited in the wild. There are thousands of known stack
• |
Table of Contents |
overflows in commercial software, on almost every platform imaginable. Stack overflows are |
|
• |
Index |
mostly the result of poorly designed string handling routines found in the standard C
Exploitinglibraries.Software How to Break Code
ByGreg Hoglund,Gary McGraw
We cover the basic stack overflow here only for completeness because the subject has been
treatedad naseum in other works. If you're new to this kind of attack, you should read the
Publisher: Addison Wesley
buffer overflow chapter in Building Secure Software [Viega and McGraw, 2001]. In this
Pub Date: February 17, 2004
section we focus on some of the more esoteric string handling problems, providing detail
ISBN: 0-201-78695-8
often missing in standard treatments.
Pages: 512
Fixed-Size Buffers
The hallmark of a classic stack overflow is a fixed-size string buffer located on the stack and
How does software break? How do attackers make software break on purpose? Why are coupled with a string handling routine that depends on a NULL-terminated buffer. Examples
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? of such string handling routines include strcpy() and strcat() calls into fixed-size buffers,
What tools can be used to break software? This book provides the answers. andsprintf() and vsprintf() into fixed-size buffers using the %s format string. Other
variations exist, including scanf() into fixed-size buffers using the %s format string. An Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
incomplete list of the string handling routines that lead to stack overflows follows[9]: techniques used by bad guys to break software. If you want to protect your software from
attack, you must first learn how real attacks are really carried out.
[9] One nice place to look for exhaustive lists of vulnerable functions like these is in static analysis tools that scan for security problems. SourceScope (a Cigital tool) includes a database of rules used during the
This mustscanning-haveprocessbook. Clevermay attackersshock youknow—andthatitdefensivewill certainlytools caneducateeasily beyouturned.Gettinginto offensivebeyondweaponsthe . script kiddie treatment found in many hacking books, you will learn about
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering sprintf
Reverse engineering sprintf
 Classic attacks against server software wsprintf
Classic attacks against server software wsprintf
 Surprising attacks against client software
Surprising attacks against client software
wsprintfA
 Techniques for crafting malicious input
Techniques for crafting malicious input
wsprintfW
 The technical details of buffer overflows
The technical details of buffer overflows
strxfrm
 Rootkits
Rootkits
wcsxfrm
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
_tcsxfrm
lstrcpy
lstrcpyn
lstrcpynA
lstrcpyA

lstrcpyW
swprintf
_swprintf
gets
• |
Table of Contents |
• |
Index |
stprintf |
|
Exploiting Software How to Break Code
strcatByGreg Hoglund,Gary McGraw
strncat.html
Publisher: Addison Wesley
Pub Date: February 17, 2004
strcatbuff
ISBN: 0-201-78695-8
Pages: 512
strcatbuffA
strcatbuffW
StrFormatByteSize
How does software break? How do attackers make software break on purpose? Why are
StrFormatByteSizeAfirewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
StrFormatByteSizeW
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniqueslstrcat used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
wcscat
This must-have book may shock you—and it will certainly educate you.Getting beyond the
script kiddie treatment found in many hacking books, you will learn about mbscat
_mbscat
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
strcpy
 When network security mechanisms do not work
When network security mechanisms do not work
strcpyA
Attack patterns
strcpyW
Reverse engineering
wcscpyClassic attacks against server software
mbscpySurprising attacks against client software
Techniques for crafting malicious input
_mbscpy
The technical details of buffer overflows
_tcscpy
 Rootkits vsprintf
Rootkits vsprintf
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
vstprint software.
vswprintf
sscanf
swscanf
stscanf

fscanf
fwscanf
ftscanf
vscanf
•Table of Contents
vsscanf
•Index
Exploiting Software How to Break Code
vfscanf
ByGreg Hoglund,Gary McGraw
Publisher: Addison Wesley
Pub Date: February 17, 2004
Because they are so well-known and are now considered "low-hanging fruit" for attackers,
ISBN: 0-201-78695-8
classic stack overflows are becoming a thing of the past. An exploitable stack overflow is
Pages: 512
quickly published and almost as quickly fixed. However, many other problems exist that can lead to memory corruption and buffer overflow. For these reasons, understanding the basic case is useful.
How does software break? How do attackers make software break on purpose? Why are
Functions That Do Not Automatically NULL Terminate
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Buffer management is a much more extensive problem than some people realize. It is not Exploitingsimply the domainSoftwareaisfewloadeddelinquentwith examplesAPI callsofthatrealexpeattactks,NULLattack-terminatedpatterns,bufferstools, .andOften, techniquesbuffer arithmeticused bywillbadbe guysperformedto breakon stringoftwarelength. If youto helpwantthwato protectthe standardyour softwareoverflowfrom. attack,However,youcertainmust firstmeantlearn-to-behow-helpfulreal attacksAPI callsarehavereallyverycarriednonobviousout. behaviors, and are
therefore pretty easy to mess up.
This must-have book may shock you—and it will certainly educate you.Getting beyond the Onescriptsuchkiddieeasytreat-to-misuseentfoundAPI incallmanyis strncpy()ha king book.This,isyouan willinterlearnstingaboutcall because it is primarily used to prevent buffer overflows. The problem is that the call itself has a deadly
detail that is often overlooked: It will not place a NULL terminator on the end of the string if
Why software exploit will continue to be a serious problem
the string is too large to fit into the target buffer. This can result in raw memory being
"tacked" onto the end of the target string buffer. There is no buffer overflow in the classic
 When network security mechanisms do not work sense of the word, but the string is effectively unterminated.
When network security mechanisms do not work sense of the word, but the string is effectively unterminated.
Attack patterns
The problem is that any subsequent call to strlen() will return an incorrect (and
misleading) value. Remember that strlen expects a NULL-terminated string. So it will return
 Reverse engineering
Reverse engineering
at least the length of the original string, plus as many bytes as it takes until a NULL character
shows up in the raw memory that was accidentally appended on the end. This will usually Classic attacks against server software
return a value that is significantly larger than the actual string length. Any arithmetic
performed on the basis of this information will be invalid (and subject to attack). Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
Example: Address-Based Arithmetic Problem
 The technical details of buffer overflows
The technical details of buffer overflows
An example of this problem involves the following code.
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
strncpy(target, source, sizeof(target));

Iftarget is 10 characters, and source is 11 characters (or more) including the NULL, the 10 characters will not be properly NULL terminated!
Consider the FreeBSD UNIX distribution. BSD is often considered to be one of the most
secure UNIX environments; however, hard-to-spot bugs like the one described earlier have
been found with some regularity in BSD. The syslog implementation includes some code that |
|
• |
Table of Contents |
checks whether a remote host has permissions to log to syslogd. The code that performs this
• Index
check in FreeBSD 3.2 is as follows:
Exploiting Software How to Break Code
ByGreg Hoglund,Gary McGraw
Publisher: Addison Wesley
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
Pages: 512
strncpy(name, hname, sizeof name);
if (strchr(name, '.') == NULL) {
How does software break? How do attackers make software break on purpose? Why are
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? strncat(name, ".", sizeof name - strlen(name) - 1);
What tools can be used to break software? This book provides the answers.
strncat(name, LocalDomain, sizeof name - strlen(name) - 1);
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
techniques used by bad guys to break software. If you want to protect your software from
}
attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the script kiddie treatment found in many hacking books, you will learn about
In this case, if the hname variable is large enough to fill the name variable completely, no
NULL terminator will be placed on the end of the name variable. This is the common curse of Why software exploit will continue to be a serious problem
strncpy() use. In the subsequent arithmetic, the expression sizeof name – strlen(name),
results in a negative value. The function strncat takes an unsigned variable, which means When etwork security mechanisms do not work
that a negative number will be interpreted by the program as a very large positive number. Thus,Astrncattack patternsoverwrites past the end of the name buffer by a largish leap. Game over for syslogd.
 Reverse engineering
Reverse engineering
There are a number of functions that do not automatically place a NULL terminator on a
Classic attacks against server software buffer. They include
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
fread()
software.
read()
readv()
pread()
memcpy()
memccpy()
bcopy()
gethostname()
strncat()
•Table of Contents
•Index
Exploiting Software How to Break Code
ByGreg Hoglund,Gary McGraw
Vulnerabilities related to the misuse of strncpy (and friends) are a relatively untapped source of future exploits. As the low-hanging fruit represented by easier-to-spot errors is consumed,Publisher: lookAddisontoWesleymore subtle errors like the previous one to bubble to the surface.
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
FunctionsPages: 512with Off-By-One NULL Termination
Some string functions are designed to place a NULL terminator at the end of a string, always. This is probably better than leaving placement of the NULL up to the programmer, but problems are still possible. The arithmetic built into some of these functions can be confusing,
How does software break? How do attackers make softwareafterbreak on purpose? Why are and may in some cases result in the NULL being placed the end of the buffer. This is an
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? "off-by-one" situation in which a single byte of memory is overwritten. On the stack, this
What tools can be used to break software? This book provides the answers. seemingly small single-byte problem can leave the program completely exploitable.
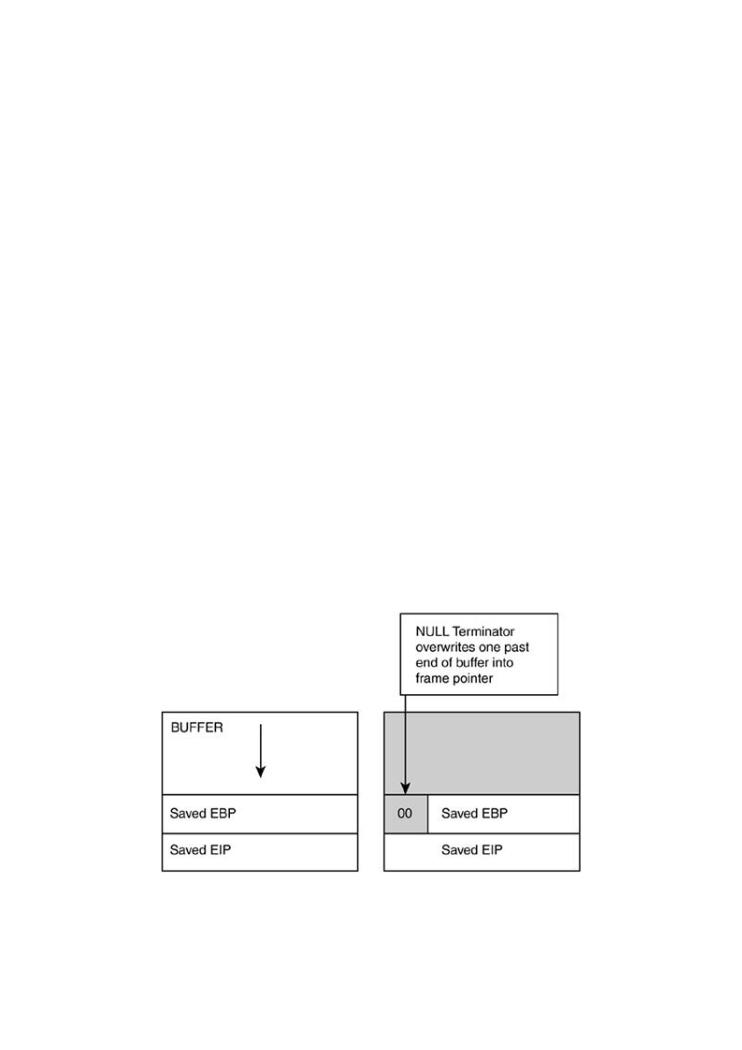
ExplA gooditingexampleSoftwareto consideris loadedis thewithstrncat()examplescall,of realwhichattacks,alwaysattackplacespatterns,NULLtools,after andthe last
techniques used by bad guys to break software. If you want to protect your software from byte of the string transfer and can thereby be used to overwrite the stack frame pointer. The
attack, you must first learn how real attacks are really carried out.
next function pulled from the stack moves the saved EBP into ESP, the stack pointer (Figure
7-6).
This must-have book may shock you—and it will certainly educate you.Getting beyond the script kiddie treatment found in many hacking books, you will learn about
Figure 7-6. Off-by-one problems are hard to spot. In this example,
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
the target BUFFER is used to overwrite into the Saved EBP.
When network security mechanisms do not work |
|
Attack |
|
Reverse |
|
Classic |
|
Surprising |
|
Techniques |
|
The |
|
Rootkits |
|
Exploiting |
to break |
software. |
|
Consider the following simple code:

1. void test1(char *p)
• |
Table of Contents |
2. { |
|
•Index
Exploiting Software How to Break Code
3. char t[12];
ByGreg Hoglund,Gary McGraw
4.strcpy(t, "test");
Publisher: Addison Wesley
5.strncat(t, p, 12-4);
Pub Date: February 17, 2004
6. } ISBN: 0-201-78695-8
Pages: 512
After line 4 has executed, the stack looks like this:
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the
script kiddie treatment found in many hacking books, you will learn about
0012FEC8 74 65 73 74 test <- character array
0012FECC 00 CC CC CC .ÌÌÌ <- character array
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
0012FED0 CC CC CC CC ÌÌÌÌ <- character array
 When network security mechanisms do not work
When network security mechanisms do not work
0012FED4 2C FF 12 00 ,ÿ.. <- saved ebp
Attack patterns
0012FED8 B2 10 40 00 2.@. <- saved eip
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
Notice that 10 bytes have been allocated for the character array t[10].  Techniques for crafting malicious input
Techniques for crafting malicious input
If we supply a short string xxx in p, the stack now looks like this:
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
0012FEC8 |
74 |
65 |
73 |
74 |
test |
0012FECC |
78 |
78 |
78 |
00 |
xxx. <- appended "xxx" |
0012FED0 |
CC CC CC CC |
ÌÌÌÌ |
|||

0012FED4 2C FF 12 00 ,ÿ..
0012FED8 B2 10 40 00 2.@.
• Table of Contents
Notice that xxx was appended, and a NULL terminator was placed right at the end.
•Index
ExploitingNow, whatSoftwarehappensHowiftoweBreaksupplyCodea very large string like xxxxxxxxxxx instead? The stack ends upByGreglookingHoglundlike,Garythis:McGraw
Publisher: Addison Wesley
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
Pages: 512
0012FEC8 74 65 73 74 test
How does software break? How do attackers make software break on purpose? Why are 0012FECCfirewalls, intrusion78 78 detection78 78 xxxxsystems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
0012FED0 78 78 78 78 xxxx
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques0012FED4 used00 FFby12bad00guys.ÿto..break<- noticesoftwareNULL. If youbytewantoverwriteto pro ct your software from attack, you must first learn how real attacks are really carried out.
0012FED8 |
B2 |
10 |
40 |
00 |
2.@. |
This must-have book may shock you—and it will certainly educate you.Getting beyond the script kiddie treatment found in many hacking books, you will learn about
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
When the function returns, the following opcodes are executed:
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
00401078 |
mov |
esp,ebp |
Techniques for crafting malicious input |
||
0040107A |
pop |
ebp |
 The technical details of buffer overflows
The technical details of buffer overflows
0040107B ret
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break software.
You can see that ESP is restored from the EBP that is stored in the register. This comes out just fine. Next we see that the saved EBP is restored from the stack, but the EBP on the stack is the value that we just munged. This means EBP has now been corrupted. When the next function on the stack returns, the same opcodes are repeated:

004010C2 |
mov |
esp,ebp |
004010C4 |
pop |
ebp |
• |
Table of Contents |
|
• |
Index |
|
004010C5 |
ret |
|
Exploiting Software How to Break Code
ByGreg Hoglund,Gary McGraw
Publisher: Addison Wesley
Here we see our freshly corrupted EBP ending up as a stack pointer.
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
Consider a more complex stack arrangement in which we control data in several places. The
Pages: 512
following stack has a string of ffffs that was placed there by the attacker in a previous call. The correct EBP should be 0x12FF28, but as you can see we have overwritten the value with
0x12FF00. The critical detail to notice here is that 0x12FF00 falls within the string of ffff charactersthat we control on the stack. This means we can force a return into a place that we control, and thus cause a successful buffer overflow attack:
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the
script kiddie treatment found in many hacking books, you will learn about
0012FE78 74 65 73 74 test
0012FE7C 78 78 78 78 xxxx
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
0012FE80 78 78 78 78 xxxx
When network security mechanisms do not work
0012FE84 78 78 78 78 xxxx
Attack patterns
0012FE88Reverse78engineering78 78 78 xxxx
0012FE8CClassic78attacks78 78against78 xxxxserver software
Surprising attacks against client software
0012FE90 00 FF 12 00 .ÿ.. <- note we overflow w/ a NULL
Techniques for crafting malicious input
0012FE94 C7 10 40 00 Ç.@.
 The technical details of buffer overflows
The technical details of buffer overflows
0012FE98 88 2F 42 00 ./B.
 Rootkits
Rootkits
0012FE9C 80 FF 12 00 .ÿ..
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
0012FEA0 00 00 00 00 ....
software.
0012FEA4 00 F0 FD 7F . .
.
0012FEA8 CC CC CC CC ÌÌÌÌ
0012FEAC CC CC CC CC ÌÌÌÌ
0012FEB0 CC CC CC CC ÌÌÌÌ

0012FEB4 |
CC CC CC CC |
ÌÌÌÌ |
|||
0012FEB8 |
CC CC CC CC |
ÌÌÌÌ |
|||
0012FEBC |
CC |
CC |
CC |
CC |
ÌÌÌÌ |
0012FEC0 |
CC |
CC |
CC |
CC |
ÌÌÌÌ |
•Table of Contents
0012FEC4 CC CC CC CC ÌÌÌÌ
• Index
Exploiting Software How to Break Code
0012FEC8 |
CC CC CC CC |
ÌÌÌÌ |
ByGreg Hoglund,Gary McGraw |
|
|
0012FECC |
CC CC CC CC |
ÌÌÌÌ |
Publisher: Addison Wesley |
|
|
Pub Date: February 17, 2004 |
ÌÌÌÌ |
|
0012FED0 |
CC CC CC CC |
|
ISBN: 0-201-78695-8 |
|
|
0012FED4Pages: 512CC CC CC CC |
ÌÌÌÌ |
|
0012FED8 |
CC CC CC CC |
ÌÌÌÌ |
0012FEDC |
CC CC CC CC |
ÌÌÌÌ |
How does software break? How do attackers make software break on purpose? Why are
0012FEE0 CC CC CC CC ÌÌÌÌ
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys?
What tools can be used to break software? This book provides the answers.
0012FEE4 CC CC CC CC ÌÌÌÌ
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
0012FEE8 66 66 66 66 ffff
techniques used by bad guys to break software. If you want to protect your software from
attack, you must first learn how real attacks are really carried out.
0012FEEC 66 66 66 66 ffff
This must-have book may shock you—and it will certainly educate you.Getting beyond the
0012FEF0 66 66 66 66 ffff
script kiddie treatment found in many hacking books, you will learn about
0012FEF4 66 66 66 66 ffff
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
0012FEF8 66 66 66 66 ffff
 When network security mechanisms do not work
When network security mechanisms do not work
0012FEFC 66 66 66 66 ffff
 Attack patterns
Attack patterns
0012FF00 66 66 66 66 ffff <- the corrupt EBP points here now
 Reverse engineering
Reverse engineering
0012FF04 46 46 46 46 FFFF
 Classic attacks against server software
Classic attacks against server software
0012FF08 CC CC CC CC ÌÌÌÌ
 Surprising attacks against client software
Surprising attacks against client software
0012FF0C CC CC CC CC ÌÌÌÌ
Techniques for crafting malicious input
0012FF10 CC CC CC CC ÌÌÌÌ
The technical details of buffer overflows
0012FF14RootkitsCC CC CC CC ÌÌÌÌ
Exploiting0012FF18 SoftwareCC CC CCisCCfilledÌÌÌÌwith the tools, concepts, and knowledge necessary to break
software.
0012FF1C |
CC CC CC CC |
ÌÌÌÌ |
|||
0012FF20 |
CC CC CC CC |
ÌÌÌÌ |
|||
0012FF24 |
CC |
CC |
CC |
CC |
ÌÌÌÌ |
0012FF28 |
80 |
FF |
12 |
00 |
.ÿ.. <- original location of EBP |
0012FF2C 02 11 40 00 ..@.
0012FF30 70 30 42 00 p0B.
Note that the attacker has placed FFFF into the string just after the new EBP location.
•Table of Contents
Because the epilog code issues a pop ebp command just before the return, the value stored
•Index
at the new EBP location gets popped from the stack. The ESP chunks forward one location, to
0x12FF04. If we place our injected EIP at 0x12FF04, the new EIP gets set to 0x46464646. A
ByGreg Hoglund,Gary McGraw successful attack.
Publisher: Addison Wesley
OverwritingPub Date: FebruaryException17, 2004 Handler Frames
ISBN: 0-201-78695-8
Pages: 512
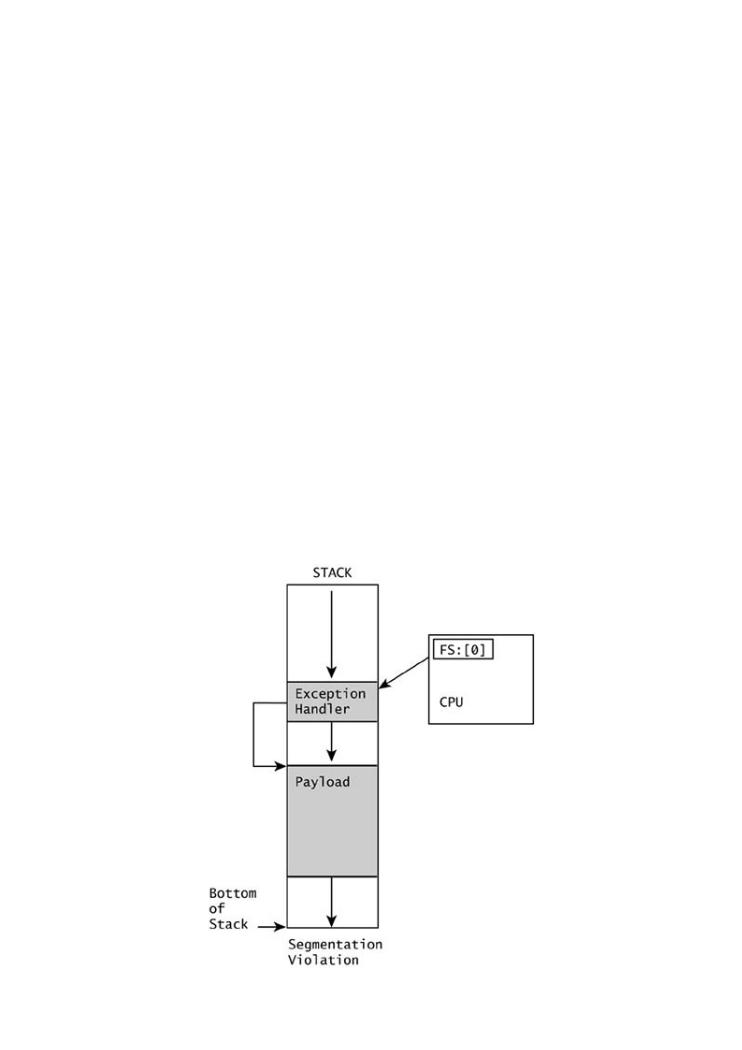
Pointers to exception handlers are also typically stored on the stack. This means that we can use a stack overflow to overwrite an exception handler pointer as a variation on stack smashing. Using a very large, naive overflow, we can overwrite past the end of the stack and intentionally cause an exception to occur. Then, because we have already overwritten the exception handler pointer, the exception will cause our payload to be executed (Figure 7-7). TheHowfollowingdoes softwdiaregrambreak?illustratesHow doanattackersinjected makebuffersoftwarethat ov rflowsbreak paston purpose?the end Whyof thearestack. Thefirewalls,attackerintrusionhas overwrittendetec ion systthe exceptionms, and antivirushandler record,softwarewhichnot keepingis itself storedout theonbadtheguys?stack. TheWhatnewtoolsrecordcan bepointsusedtotoanbreakattacksoftware?payloadThisso thatbookwhenprovidthesSEGVthe answersoccurs,.the processor jumps to the attack code and chugs merrily through it.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
Figure 7-7. Using exception handlers as part of a buffer overflow.
This must-have book may shock you—and it will certainly educate you.Getting beyond the
The exception handler points into the payload.
script kiddie treatment found in many hacking books, you will learn about
Why software |
|
When network |
|
Attack patterns |
|
Reverse engineering |
|
Classic attacks |
|
Surprising attacks |
|
Techniques for |
|
The technical |
|
Rootkits |
|
Exploiting Software |
necessary to break |
software. |
|

•Table of Contents
•Index
Exploiting Software How to Break Code
ByGreg Hoglund,Gary McGraw
Publisher: Addison Wesley
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
Pages: 512
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the script kiddie treatment found in many hacking books, you will learn about
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
