
- •Exploiting Software How to Break Code
- •Table of Contents
- •Copyright
- •Praise for Exploiting Software
- •Attack Patterns
- •Foreword
- •Preface
- •What This Book Is About
- •How to Use This Book
- •But Isn't This Too Dangerous?
- •Acknowledgments
- •Greg's Acknowledgments
- •Gary's Acknowledgments
- •Bad Software Is Ubiquitous
- •The Trinity of Trouble
- •The Future of Software
- •What Is Software Security?
- •Conclusion
- •Chapter 2. Attack Patterns
- •A Taxonomy
- •An Open-Systems View
- •Tour of an Exploit
- •Attack Patterns: Blueprints for Disaster
- •An Example Exploit: Microsoft's Broken C++ Compiler
- •Applying Attack Patterns
- •Attack Pattern Boxes
- •Conclusion
- •Into the House of Logic
- •Should Reverse Engineering Be Illegal?
- •Reverse Engineering Tools and Concepts
- •Approaches to Reverse Engineering
- •Methods of the Reverser
- •Writing Interactive Disassembler (IDA) Plugins
- •Decompiling and Disassembling Software
- •Decompilation in Practice: Reversing helpctr.exe
- •Automatic, Bulk Auditing for Vulnerabilities
- •Writing Your Own Cracking Tools
- •Building a Basic Code Coverage Tool
- •Conclusion
- •Chapter 4. Exploiting Server Software
- •The Trusted Input Problem
- •The Privilege Escalation Problem
- •Finding Injection Points
- •Input Path Tracing
- •Exploiting Trust through Configuration
- •Specific Techniques and Attacks for Server Software
- •Conclusion
- •Chapter 5. Exploiting Client Software
- •Client-side Programs as Attack Targets
- •In-band Signals
- •Cross-site Scripting (XSS)
- •Client Scripts and Malicious Code
- •Content-Based Attacks
- •Conclusion
- •Chapter 6. Crafting (Malicious) Input
- •The Defender's Dilemma
- •Intrusion Detection (Not)
- •Partition Analysis
- •Tracing Code
- •Reversing Parser Code
- •Misclassification
- •Audit Poisoning
- •Conclusion
- •Chapter 7. Buffer Overflow
- •Buffer Overflow 101
- •Injection Vectors: Input Rides Again
- •Buffer Overflows and Embedded Systems
- •Database Buffer Overflows
- •Buffer Overflows and Java?!
- •Content-Based Buffer Overflow
- •Audit Truncation and Filters with Buffer Overflow
- •Causing Overflow with Environment Variables
- •The Multiple Operation Problem
- •Finding Potential Buffer Overflows
- •Stack Overflow
- •Arithmetic Errors in Memory Management
- •Format String Vulnerabilities
- •Heap Overflows
- •Buffer Overflows and C++
- •Payloads
- •Payloads on RISC Architectures
- •Multiplatform Payloads
- •Prolog/Epilog Code to Protect Functions
- •Conclusion
- •Chapter 8. Rootkits
- •Subversive Programs
- •A Simple Windows XP Kernel Rootkit
- •Call Hooking
- •Trojan Executable Redirection
- •Hiding Files and Directories
- •Patching Binary Code
- •The Hardware Virus
- •Low-Level Disk Access
- •Adding Network Support to a Driver
- •Interrupts
- •Key Logging
- •Advanced Rootkit Topics
- •Conclusion
- •References
- •Index

Reversing Parser Code
A parser breaks apart a raw string of bytes into individual words and statements. This activity is called parsing. Standard parsing usually requires "punctuation" characters, often called meta-characters because they have special meaning. Many times, target software will parse
• Table of Contents
through an input string looking for these special characters.
•Index
MetaExploiting-charactersSoftwareareHowoftento BreakpointsCodeof interest for an attacker. Many times important decisions
rely directly on the presence of these special characters. Filters also tend to rely on meta-
ByGreg Hoglund,Gary McGraw characters for proper operation.
Publisher: Addison Wesley
Meta-characters are often quite easy to spot in a dead listing. Spotting them can be as simple
Pub Date: February 17, 2004
as looking for code that compares a byte value against a hard-coded character. Use an ASCII chart toISBN:determine0-201-78695the-8hex values for a given character.
Pages: 512
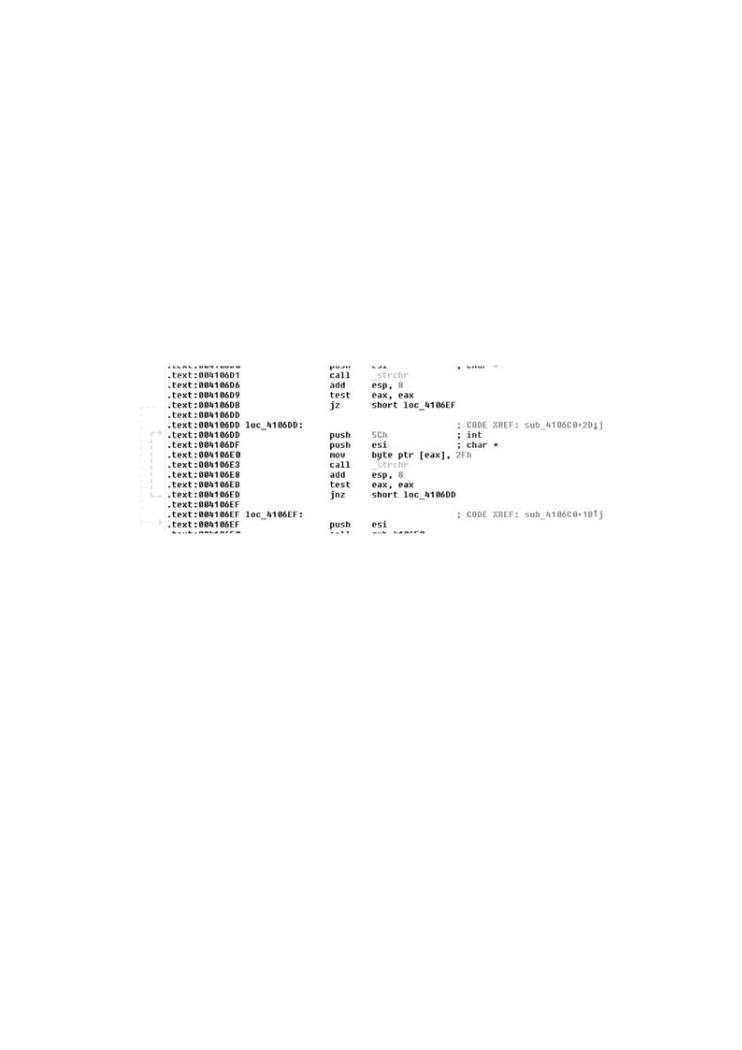
In the IDA screen shot shown in Figure 6-9, we can see two locations where data are being compared with the forward slash and back slash characters—2F and 5C, which map to / and \ respectively. These kinds of comparisons tend to crop up in file system filters, and thus make interesting starting places for an attack.
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys?
What tools can be used to break software? This book provides the answers.
Figure 6-9. An IDA disassembly of a common FTP server showing the
comparison for slash characters 2F and 5C.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
[View full size image]
This must-have book may shock you—and it will certainly educate you.Getting beyond the script kiddie
 Why
Why
 When
When
 Attack
Attack
 Classic
Classic
 The
The
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
Charactersoftware. Conversion
Character conversions sometimes occur as a system prepares itself to make an API call. For example, although a system call may expect a file system path to be supplied using forward slashes, the program may accept both back slashes and forward slashes to mean the "same thing." So, the software coverts back slashes to forward slashes before making the call. This kind of transformation results in equivalent characters. It doesn't matter which kinds of slashes you supply, they will be treated as forward slashes to the system call.
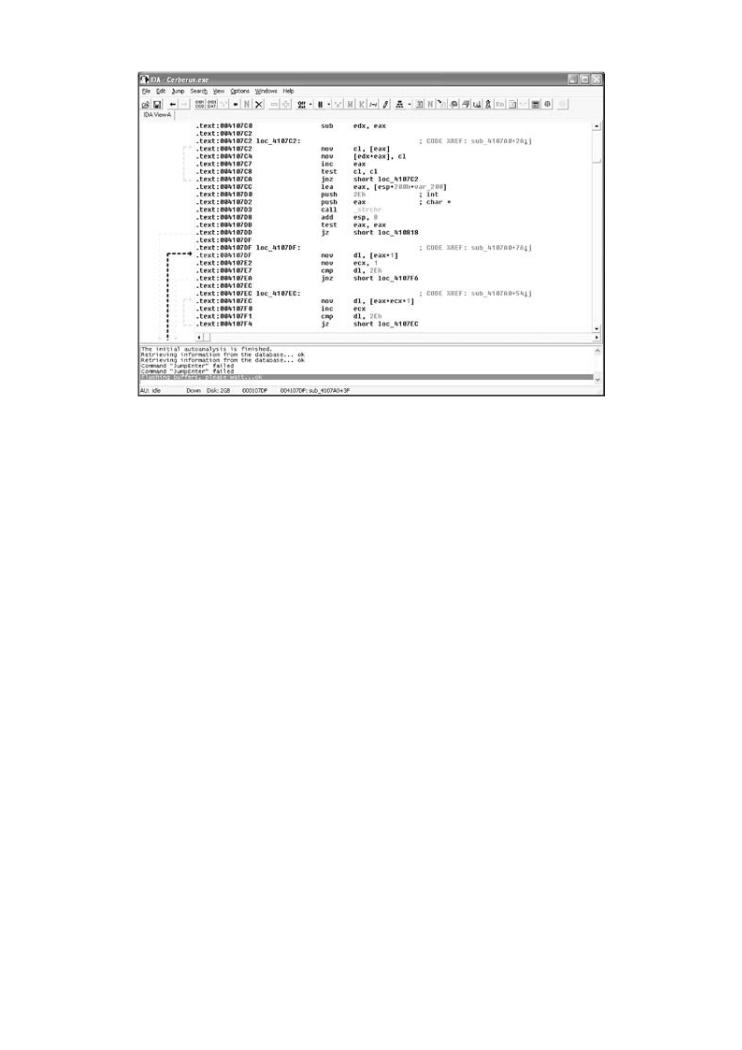
Why is this important? Consider what happens if the programmer wants to make sure the user can't supply slashes in a filename. This might be the case when the programmer is trying to prevent a relative path traversal bug, for example. The programmer may filter out forward slashes and believe that the problem is solved. But if an attacker can insert a back slash, then the problem may not have been properly handled. In situations in which characters are converted, an excellent opportunity exists to evade simple filters and IDSs. Figure 6-10 shows code that converts back slashes to forward slashes.
•Table of Contents
•Index
Exploiting Software How to Break Code
Figure 6-10. The code here is using an API call strchr to find
ByGreg Hoglund,Gary McGraw
character5Ch (\) in a string. Once the character is found, the code
usesmov byte ptr [eax], 2Fh to replace the back slash with character
Publisher: Addison Wesley
2Fh (/). This loops until no more back slashes are found (via the test
Pub Date: February 17, 2004 |
|
|
eax, eax and subsequent jnz, which jumps [if not zero] back to the |
||
ISBN: 0-201-78695-8 |
beginning of the loop). |
|
Pages: 512 |
|
|
|
|
|
|
[View full size image] |
|
How does |
|
are |
firewalls, |
|
guys? |
What tools |
|
|
Exploiting |
|
and |
techniques |
|
from |
attack, |
|
|
This must |
|
the |
script kiddie treatment found in many hacking books, you will learn about |
|
|
Why software exploit will continue to be a serious problem
Byte Operations
 When network security mechanisms do not work
When network security mechanisms do not work
Parsers built into most programs usually deal with single characters. A single character is generallyAttackencodedpatternsas a single byte (the clear exception to this rule being multibyte/unicode characters). Because characters are usually represented as bytes, identifying single-byte
Reverse engineering
operations in a reverse assembly is a reasonable undertaking. Single-byte operations are
easy to spot because they use the notation "al," "bl," and so forth. Most registers today are
Classic attacks against server software
32 bits in size. This notation indicates that operations are being performed on the lowest 8
bits of the register—a single byte.
 Surprising attacks against client software
Surprising attacks against client software
There is a classic "gotcha" here to keep in mind when debugging a running program.
Techniques for crafting malicious input
Remember that only a single byte is being used with notations like al and bl, regardless of
what exists in the rest of the register. If the register has the value 0x0011222F (as shown in
 The technical details of buffer overflows
The technical details of buffer overflows
Figure 6-11), and the byte notation is being used, the actual value processed is 0x2F, the
lowest 8 bits.  Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
Figure 6-11. A single byte (2F) as represented in a 32-bit register.

•Table of Contents
•Index
Exploiting Software How to Break Code
Pointer Operations
ByGreg Hoglund,Gary McGraw
Strings are often too large to be stored in a register. Because of this, a register will usually
Publisher: Addison Wesley
contain the address of the string in memory. This is called a pointer. Note that pointers are
Pub Date: February 17, 2004
addresses that can point to almost anything, not just strings. One nice trick is to find pointers
ISBN: 0-201-78695-8
that increment by a single byte, or operations that use a pointer to load a single byte.
Pages: 512
Byte operations with pointers are easy to spot. Pointer operations follow the [XXX] notation (for example, [eax], [ebx], and so on) in combination with the al, bl, cl, and so forth, notation.
Pointer arithmetic has the notation
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the script kiddie treatment found in many hacking books, you will learn about
[eax + 1], [ebx + 1], etc.
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
 When network security mechanisms do not work
When network security mechanisms do not work
Moving bytes around in memory ends up looking something like this:
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
mov dl,The technical[eax+1] details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
In some cases, the register where the pointer is stored is modified directly, like this:

inc eax
•Table of Contents
•Index
Exploiting Software How to Break Code
NULL Terminators
ByGreg Hoglund,Gary McGraw
Because strings are typically NULL terminated (especially when C is being used), looking for
Publisher: Addison Wesley
code that compares with a 0 byte can also be useful. Tests for the NULL character tend to
Pub Date: February 17, 2004
look something like this:
ISBN: 0-201-78695-8
Pages: 512
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
test al, al
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
techniques used by bad guys to break software. If you want to protect your software from test cl, cl
attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the script kiddie treatment found in many hacking books, you will learn about
and so forth.
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
Figure 6-12 includes several single-byte operations:
 When network security mechanisms do not work
When network security mechanisms do not work
 cl, byte notation
cl, byte notation
 Attack patterns
Attack patterns
 [eax], a pointer
[eax], a pointer
 Reverse engineering
Reverse engineering
 inc eax, increment pointer
inc eax, increment pointer
 Classic attacks against server software
Classic attacks against server software
 test cl,cl, looking for NULL
test cl,cl, looking for NULL
 Surprising attacks against client software
Surprising attacks against client software
 [eax+1], pointer + 1 byte
[eax+1], pointer + 1 byte
 Techniques for crafting malicious input
Techniques for crafting malicious input
 mov dl,[eax+1], moving a single byte
mov dl,[eax+1], moving a single byte
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Figure 6-12. Code with several interesting 1-byte operations
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break software. included.
[View full size image]
•
•
Exploiting
ByGreg
Publisher
Pub Date
ISBN
Pages
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? TheseWhat toperationsolscan bemayusedindicateto breakthatsoftheware?programThis bookis parsingprovidesor otherwiseanswersprocessing. input.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the script kiddie treatment found in many hacking books, you will learn about
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.

Example: Reversing I-Planet Server 6.0 through the Fro
Door
Like most server software, Sun Microsystems I-Planet 6.0 software uses a "detect the bad" blac
•approach toTablesecurityof Contents. As we have made clear, such an approach is easily defeated. Using call tr and• GDB (describedIndex in Chapter 3), we locate several function calls meant to filter user-supplied InsteadExploitingofSoftwaresimplyHowrejectingto BreakmaliciousCode input, the I-Planet server attempts to "correct" malicious s
of data by removing the "bad" parts.
ByGreg Hoglund,Gary McGraw
In this particular case, the most effective approach to find these functions involves break points
Publisher: Addison Wesley
"outside-in" approach. Remember from Chapter 3 that going outside-in means beginning a trac
Pub Date: February 17, 2004
user input is accepted, and attempting to move forward into the program.
ISBN: 0-201-78695-8
Working outside-in, we discover an often-used function called
Pages: 512
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
__0fJCHttpUtilTCanonicalizeURIPathPCciRPcRiT
techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the
script kiddie treatment found in many hacking books, you will learn about
The name of the function is certainly mangled, but we can see that it's used to canonicalize (or standard form) the user-supplied URI string. As we have mentioned, this function is designed to "bad"Whyinputsoftwarestrings.exploitUsingGDBwillctontinueset a breaktobe apointseriousat theproblembeginning of this function, we can exa the data that are being supplied:
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
(gdb) break __0fJCHttpUtilTCanonicalizeURIPathPCciRPcRiT
Techniques for crafting malicious input
Breakpoint 6 at 0xff22073c
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting(gdb) contSoftwareis filled with the tools, concepts, and knowledge necessary to break
software.
Continuing..
A break point is now set, but we still need to issue a request to determine which data arrive at function. We issue a Web request to the target and the break point promptly fires. We examine registers with the command info reg to determine which data are supplied:

•Table of Contents
Breakpoint• Index6, 0xff22073c in __0fJCHttpUtilTCanonicalizeURIPathPCciRPcRiT ()
Exploiting Software How to Break Code
from /usr/local/iplanet/servers/bin/https/lib/libns-httpd40.so
ByGreg Hoglund,Gary McGraw
(gdb) info reg
Publisher: Addison Wesley
g0 |
Pub Date: February 17, 2004 |
0 |
|
|
0x0 |
||
|
ISBN: 0-201-78695-8 |
|
|
g1 |
Pages: 512 |
0x747000 |
7630848 |
|
|||
g2 |
|
0x22 |
34 |
g3 |
|
0x987ab0 |
9992880 |
How does software break? How do attackers make software break on purpose? Why are
g4firewalls, intrusion0x98da28detection |
10017320systems, and antivirus software not keeping out the bad guys? |
|
What tools can be used to break software? This book provides the answers. |
||
g5 |
0x985a18 |
9984536 |
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
g6 0x0 0
techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
g7 0xf7641d78 -144433800
This must-have book may shock you—and it will certainly educate you.Getting beyond the o0script kiddie treatment0x985a8cfound9984652in many hacking books, you will learn about
o1 |
|
0x15 |
21 |
|
|
Why software exploit will continue to be a serious problem |
|||
o2 |
|
0xf7641bec |
-144434196 |
|
|
When network security mechanisms do not work |
|||
o3 |
|
0xf7641ad4 |
-144434476 |
|
|
Attack patterns |
|
|
|
o4 |
Reverse engineering0x0 |
0 |
|
|
o5 |
Classic attacks0x987ab0against server9992880software |
|||
sp |
Surprising attacks0xf7641a48against client software-144434616 |
|||
o7 |
Techniques for0xff21ae08crafting malicious-input14569976 |
|||
l0 |
The technical details of buffer overflows |
|||
|
0x985390 |
9982864 |
|
|
l1 |
Rootkits |
0xff2d80d0 |
-13795120 |
|
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break |
|||
l2 |
0x987aa0 |
9992864 |
|
software. |
|
|
|
l3 |
0x336d38 |
3370296 |
|
l4 |
0x985a28 |
9984552 |
|
l5 |
0xff2d7b38 |
-13796552 |
|
l6 |
0x987aa0 |
9992864 |
|

l7 |
0x987ab0 |
9992880 |
i0 |
0x985a88 |
9984648 |
i1 |
0x2000 |
8192 |
i2 |
0x9853ac |
9982892 |
•Table of Contents
i3 |
0x987ab0 |
9992880 |
•Index
Exploiting Software How to Break Code |
|
|
|||
i4 |
|
0x985584 |
9983364 |
|
|
ByGreg Hoglund,Gary McGraw |
|
|
|
||
i5 |
|
0x1 |
1 |
|
|
Publisher: Addison Wesley |
|
|
|
||
fp Pub Date: February0xf7641bf017, 2004 |
-144434192 |
|
|||
|
ISBN: 0-201-78695-8 |
|
|
|
|
i7 |
Pages: 512 |
0xff21938c |
-14576756 |
|
|
y |
|
0x0 |
0 |
|
|
psr |
|
0xfe901001 |
-24113151 |
icc:N--C, pil:0, s:0, ps:0, et:0 |
|
How does software break? How do attackers make software break on purpose? Why are |
|||||
wim |
|
0x0 |
0 |
|
|
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? |
||
What tools can be used to break software? This book provides the answers. |
||
tbr |
0x0 |
0 |
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and |
||
pc |
0xff22073c |
-14547140 |
techniques used by bad guys to break software. If you want to protect your software from |
||
attack, you must first learn how real attacks are really carried out. |
||
npc |
0xff220740 |
-14547136 |
This must-have book may shock you—and it will certainly educate you.Getting beyond the fpsr 0x420 1056 rd:N, tem:0, ns:0, ver:0, ftt:0, qne:0, fcc:<,
script kiddie treatment found in many hacking books, you will learn about
|
|
cexc:0 |
cpsr |
Why software exploit will continue to be a serious problem |
|
0x0 |
0 |
|
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
Next weReverseexamineengineeringeach register with the x command. A convenient trick is to use the "x/" notati
dump the memory around the address in question. The command x/8s $g3, for example, dum
Classic attacks against server software
strings around the memory pointed to by register g3:
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
(gdb) x/8s $g3 software.
0x987ab0: |
"GET /knowdown.class%20%20 HTTP/1.1" |
0x987ad3: "unch.html"
0x987add: ""
0x987ade: ""

0x987adf: ""
0x987ae0: ""
0x987ae1: ""
0x987ae2:
•Table of Contents
•Index
Exploiting Software How to Break Code
ByGreg Hoglund,Gary McGraw
Our supplied URI is stored in a memory location pointed to by the g3 register. We can now begi
stepping forward and taking notes in IDA.
Publisher: Addison Wesley
ThisPuboutsideDate: Febru-in approachry 17, 2004is particularly well suited to finding parsing tricks. Usually input data a
"frobbed" and otherwise modified by the time they reach an interesting system call. By starting
ISBN: 0-201-78695-8
outside, we can determine what the parser logic is doing to the data. For example, extra slashe
Pages: 512
be stripped from a filename. The request might not be forwarded if certain character sequences
present (such as our redirection-invoking string ../..).
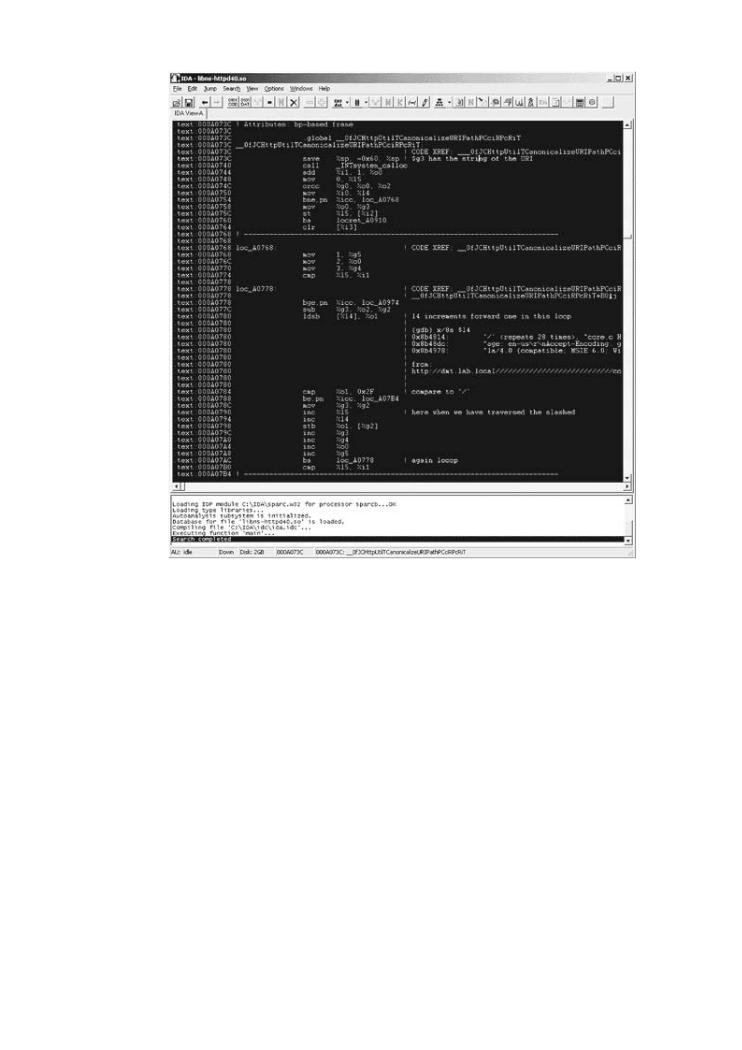
Figure 6-13 shows an IDA screen shot with notes appended to interesting locations. The output
GDB can be directly pasted into the IDA disassembly. Pressing the semicolon key in IDA allows
How does software break? How do attackers make software break on purpose? Why are repeatable comments to be entered. By tracking the call, we find that many characters are strip
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? and that the filename is in this (broken) way "cleaned up."
What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
techniques used by bad guys to break software. If you want to protect your software from
Figure 6-13. An IDA screen with notes appended to the code. Keeping
attack, you must first learn how real attacks are really carried out.
of work in IDA is essential.
This must-have book may shock you—and it will certainly educate you.Getting beyond the
script kiddie treatment found in many hacking books, you will learn about
[View full size image]
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
•
•
Exploiting Software
ByGreg Hoglund,
Publisher:
Pub Date:
ISBN: 0-
Pages: 512
How does firewalls, intrusion What tools can
Exploiting
techniques used attack, you
This must-have script kiddie
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
Diving a bit deeper into the program, we find another function that is used to check the format
 When network security mechanisms do not work
When network security mechanisms do not work
"cleaned" request. As if the idea of looking for bad input isn't ridiculous enough on its own, this
function is actually named INTutil_uri_is_evil_internal (what fun!). This additional functio
 Attack patterns
Attack patterns
supposed to trap malicious hackers who are attacking the system. The call should return TRUE
FALSE depending on whether the URI is determined to be "evil." This is greatly amusing, so let' Reverse engineering
reverse engineering this call. Obviously, we must be able to get past this call during any real at
The IDA reverse of the function looks something like this:
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
.text:00056140 ! ||||||||||||||| S U B R O U T I N E

.text:00056140
.text:00056140
.text:00056140 .global INTutil_uri_is_evil_internal
.text:00056140 INTutil_uri_is_evil_internal:
• |
Table of Contents |
ldsb |
[%o0], %o1 |
.text:00056140• Index |
|||
Exploiting Software How to Break Code |
|
|
|
By.text:00056144Greg Hoglund,Gary McGraw |
mov |
1, %o3 |
|
.text:00056148 |
mov |
2, %o4 |
|
|
Publisher: Addison Wesley |
|
|
|
Pub Date: February 17, 2004 |
cmp |
%o1, 0 |
.text:0005614C |
|||
|
ISBN: 0-201-78695-8 |
|
|
.text:00056150Pages: 512 |
be,pn |
%icc, loc_561F4 |
|
.text:00056154 |
mov |
%o0, %o5 |
|
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the script.text:00056158kiddie treatment found in manymovhacking b%o2,oks,%o0you will learn about
.text:0005615C |
mov |
0, %o2 |
Why software exploit will continue to be a serious problem |
||
.text:00056160 |
cmp |
%o1, 0x2F |
When network security mechanisms do not work |
||
.text:00056164 |
|
|
Attack patterns |
|
|
.text:00056164Reverse engineeringloc_56164: |
|
|
.text:00056164Classic attacks against server softwarebne,a |
%icc, loc_561DC |
|
... Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
We set a break point and examine the data going into this call as follows:  Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
(gdb) x/8s $o0
0x97f030: "/usr/local/iplanet/servers/docs/test_string.greg///"

0x97f064: |
|
"ervers/docs" |
0x97f070: |
|
"/usr/local/iplanet/servers/docs" |
0x97f090: |
|
"" |
0x97f091: |
|
"\2272\230" |
• |
Table of Contents |
|
• |
Index |
"" |
0x97f095: |
|
|
Exploiting Software How to Break Code
0x97f096:ByGreg Hoglund,Gary McGraw""
0x97f097: ""
Publisher: Addison Wesley Pub Date: February 17, 2004 ISBN: 0-201-78695-8
Pages: 512
In this example, our break point fires after we supplied the following URL:
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from
attack, you must first learn how real attacks are really carried out. http://172.16.10.10/test_string.greg/%2F//.
This must-have book may shock you—and it will certainly educate you.Getting beyond the script kiddie treatment found in many hacking books, you will learn about
At this point we can see that the hex-encoded characters in the URI have already been converte
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
the time it has reached this point. Through some further probing, we also note that the "evil" ch
never made for the following URL:
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
Techniques for crafting malicious input
http://172.16.10.10/../../../../../../etc/passwd
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
That is, when we directly access the password file, some check occurs in the program that denie Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
request before the "evil" check even runs. We never make it to the "evil" check! Clearly, there a software.
multiple points in the program that are checking our input for hostility.
Interestingly, when the path is prefixed with a subdirectory, we do land in the "evil" check:

•Table of Contents
•Index
Exploiting Software How to Break Code
ByGreg Hoglund,Gary McGraw
Publisher: Addison Wesley
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
Pages: 512
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
http://172.16.10.10/sassy/../../../../../../etc/passwd
techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the
script kiddie treatment found in many hacking books, you will learn about
The subdirectory "sassy" in this case is not required to exist. The critical insight is that we are confusing the logic of the program. By placing a bogus subdirectory in the path, the logic branc differentlyWhy softwarethanif exploitdirect requestwill continueis madeto beforatheseriouspasswordproblemfile.
This meansWhen networkwe havesecuridefeatedy mechanismsthe first checkdo noton ourworkinput. When multiple checks and branches
to be occurring like this, this is a good indication that you will eventually find a way into the pro
Attack patterns
A better designed program will usually have a single cohesive point where a check or set of che
occurs. (Note that in a few interesting cases, no checks are needed because the target program
Reverse engineering
CHROOTed or uses some other security mechanism.)
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
