
- •Exploiting Software How to Break Code
- •Table of Contents
- •Copyright
- •Praise for Exploiting Software
- •Attack Patterns
- •Foreword
- •Preface
- •What This Book Is About
- •How to Use This Book
- •But Isn't This Too Dangerous?
- •Acknowledgments
- •Greg's Acknowledgments
- •Gary's Acknowledgments
- •Bad Software Is Ubiquitous
- •The Trinity of Trouble
- •The Future of Software
- •What Is Software Security?
- •Conclusion
- •Chapter 2. Attack Patterns
- •A Taxonomy
- •An Open-Systems View
- •Tour of an Exploit
- •Attack Patterns: Blueprints for Disaster
- •An Example Exploit: Microsoft's Broken C++ Compiler
- •Applying Attack Patterns
- •Attack Pattern Boxes
- •Conclusion
- •Into the House of Logic
- •Should Reverse Engineering Be Illegal?
- •Reverse Engineering Tools and Concepts
- •Approaches to Reverse Engineering
- •Methods of the Reverser
- •Writing Interactive Disassembler (IDA) Plugins
- •Decompiling and Disassembling Software
- •Decompilation in Practice: Reversing helpctr.exe
- •Automatic, Bulk Auditing for Vulnerabilities
- •Writing Your Own Cracking Tools
- •Building a Basic Code Coverage Tool
- •Conclusion
- •Chapter 4. Exploiting Server Software
- •The Trusted Input Problem
- •The Privilege Escalation Problem
- •Finding Injection Points
- •Input Path Tracing
- •Exploiting Trust through Configuration
- •Specific Techniques and Attacks for Server Software
- •Conclusion
- •Chapter 5. Exploiting Client Software
- •Client-side Programs as Attack Targets
- •In-band Signals
- •Cross-site Scripting (XSS)
- •Client Scripts and Malicious Code
- •Content-Based Attacks
- •Conclusion
- •Chapter 6. Crafting (Malicious) Input
- •The Defender's Dilemma
- •Intrusion Detection (Not)
- •Partition Analysis
- •Tracing Code
- •Reversing Parser Code
- •Misclassification
- •Audit Poisoning
- •Conclusion
- •Chapter 7. Buffer Overflow
- •Buffer Overflow 101
- •Injection Vectors: Input Rides Again
- •Buffer Overflows and Embedded Systems
- •Database Buffer Overflows
- •Buffer Overflows and Java?!
- •Content-Based Buffer Overflow
- •Audit Truncation and Filters with Buffer Overflow
- •Causing Overflow with Environment Variables
- •The Multiple Operation Problem
- •Finding Potential Buffer Overflows
- •Stack Overflow
- •Arithmetic Errors in Memory Management
- •Format String Vulnerabilities
- •Heap Overflows
- •Buffer Overflows and C++
- •Payloads
- •Payloads on RISC Architectures
- •Multiplatform Payloads
- •Prolog/Epilog Code to Protect Functions
- •Conclusion
- •Chapter 8. Rootkits
- •Subversive Programs
- •A Simple Windows XP Kernel Rootkit
- •Call Hooking
- •Trojan Executable Redirection
- •Hiding Files and Directories
- •Patching Binary Code
- •The Hardware Virus
- •Low-Level Disk Access
- •Adding Network Support to a Driver
- •Interrupts
- •Key Logging
- •Advanced Rootkit Topics
- •Conclusion
- •References
- •Index

The Privilege Escalation Problem
Certain components of a system have trust relationships (sometimes implicit, sometimes explicit) with other parts of the system. Some of these trust relationships offer "trust elevation" possibilities—that is, these components can escalate trust by crossing internal
• |
Table of Contents |
boundaries from a region of less trust to a region of more trust. To understand this, think |
|
• |
Index |
about what happens when a kernel-level system call is made by a simple application. The
Exploitingkernel is Softwareclearly trustedHow to Breakto a muchCode greater extent than the application, because if the kernel
misbehaves, really bad things happen, whereas the application can usually be killed with far
ByGreg Hoglund,G ry McGraw from drastic consequences.
Publisher: Addison Wesley
When we talk about trusted parameters we should think in terms of trust elevation in the
Pub Date: February 17, 2004
system. Where is a trusted parameter being input and where is it being used? Does the point
ISBN: 0-201-78695-8
of use belong to a region of higher trust than the point of input? If so, we have uncovered a privilegePages:escalation512 path.
Process-Permissions Equal Trust
How does software break? How do attackers make software break on purpose? Why are The permissions of a process place an effective upper limit on the capabilities of an exploit,
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? but an exploit is not bound by a single process. Remember that you are attacking a system.
What tools can be used to break software? This book provides the answers.
Account for situations when a low-privilege process communicates with a higher privilege
process. Synchronous communication may be carried out via procedure calls, file handles, or Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
sockets. Interestingly, communication via a data file is free from most normal time techniques used by bad guys to break software. If you want to protect your software from
constraints. So are many database entries. This means you can place "logic bombs" or "data attack, you must first learn how real attacks are really carried out.
bombs" in a system that go off some time in the future when a certain state is reached.
This must-have book may shock you—and it will certainly educate you.Getting beyond the
Links between programs can be extensive and very hard to audit. For the developer, this script kiddie treatment found in many hacking books, you will learn about
means that natural cracks will exist in the design. Thus, opportunity exists for the attacker.
System boundaries often present the greatest areas of weakness in a target. Vulnerabilities
also exist where multiple system components communicate. The connections can be Why software exploit will continue to be a serious problem
surprising. Consider a log file. If a low-privilege process can create log entries and a high-
privilegeWhenprocessnetworeadsk securitythe logmechanismsfile, there existsdo notaworkclear communication path between the two
programs. Although this may seem far fetched, there have been published exploits leveraging
vulnerabilitiesAttack patternsof this nature. For example, a Web server will log user-supplied data from
page requests. An anonymous user can insert special meta-characters into the page request,
Reverse engineering
thus causing the characters to be saved in a log file. When a root-level user performs normal
system maintenance on the log file, the meta-characters can cause data to be appended to
Classic attacks against server software the password file. Problems ensue.
 Surprising attacks against client software
Surprising attacks against client software
If WeTechniquesDon't Runfor crasftingAdministrator,mal cious input Everything Breaks!
The technical details of buffer overflows
Secure programming guides are full of references to the principle of least privilege (see
Building Secure Software [Viega and McGraw, 2001], for example). The problem is that most
 Rootkits
Rootkits
code is not designed to work with least privilege. Often times the code will fail to operate
properly if access restrictions are placed on it. The sad thing is that many such programs Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
could very likely be written without requiring Administrator or root access, but they aren't. As software.
a result, today's software runs with way too much systemwide privilege.
Thinking about privilege requires adjusting your viewpoint to a panoramic, systemwide view. (This is an excellent attacker trick that you should internalize.) Often the OS is the essential service providing privilege and access control checks, but many programs do not properly adhere to the least-privilege concept, so they abuse the OS and request too much privilege (often without being told "no"). Furthermore, the user of the program may or may not notice this issue, but you can be assured that an attacker will. One very interesting technique is to run a target program in a sandbox and examine the security context of each call and
operation (something that is made easier in advanced platforms like Java 2). Privilege
problems are very likely to surface during this exercise, and thus provide one of the richest
forms of attack.
•Attack Pattern:T ble of ContentsTarget Programs That Write to Privileged OS
• Index
Resources
Exploiting Software How to Break Code
ByGreg Hoglund,Gary McGraw
Look for programs that write to the system directories or registry keys (such as HKLMPublisher:whichAddisstoresn Wesleya number of critical Windows environment variables). These arePubtypicallyDate: Februnarywith17, 2004elevated privileges and have usually not been designed with securityISBN:in0mind-201-78695. Such-8 programs are excellent exploit targets because they yield
lots of power when they break.
Pages: 512
Elevated Processes That Read Data from Untrusted Sources
How does software break? How do attackers make software break on purpose? Why are
Once remote access to a system has been obtained, an attacker should begin looking for files firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys?
and registry keys that can be controlled. Likewise, the attacker should begin looking for local What tools can be used to break software? This book provides the answers.
pipes and system objects. Windows NT, for example, has an object manager and a directory
ofExploitingsystem objectsSoftwarethatisincludeloadedmemorywith examplessectionsof(actualreal attacks,memoryattacksegmentspatterns,thattools,can haveand rtechniquesad/write access),used by openbad guysfile handlto breaks, pipes,softwareand. Ifmutexesyou want. Alltotheseprotectareyourpotentialsoftwareinputfrompoints whereattack,anyouattackermust firstcanletakern howthe nextreal stepattacksintoarethereallymachinecarried. Onceoutthe. border of the software system has been penetrated, the attacker will usually want to obtain further access into the Thiskernelmustor server-have boprokcessmay. Anyshockdatayouinput—andpointit willcancertainlybe usededucateas anotheryou.toGeholdttingtobeyondclimb the scfurtheript kiddieinto privilegedtreatm ntmemoryfound inspacesmany.hacking books, you will learn about
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
 When network security mechanisms do not work
When network security mechanisms do not work
Attack Pattern: Use a User-Supplied Configuration File to
Attack patterns
Run Commands That Elevate Privilege
 Reverse engineering
Reverse engineering
A setuid utility program accepts command-line arguments. One of these
Classic attacks against server software
arguments allows a user to supply the path to a configuration file. The
configuration file allows shell commands to be inserted. Thus, when the utility
Surprising attacks against client software
starts up, it runs the given commands. One example found in the wild is the UUCP
(or UNIX-to-UNIX copy program) set of utilities. The utility program may not have
Techniques for crafting malicious input
root access, but may belong to a group or user context that is more privileged
than that of the attacker. In the case of UUCP, the elevation may lead to the
 The technical details of buffer overflows
The technical details of buffer overflows
dialer group, or the UUCP user account. Escalating privilege in steps will usually
lead an attacker to a root compromise (the ultimate goal).  Rootkits
Rootkits
Some programs will not allow a user-supplied configuration file, but the
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
systemwide configuration file may have weak permissions. The number of software.
vulnerabilities that exist because of poorly configured permissions is large. A note of caution: As an attacker, you must consider the configuration file as an obvious detection point. A security process may monitor the target file. If you make changes to a configuration file to gain privilege, then you should immediately clean the file when you are finished. You can also run certain utilities to set back file access dates. The key is not to leave a forensic trail surrounding the file you exploited.

Processes That Use Elevated Components
Some processes are smart enough to execute user requests as a low-privilege thread. These requests, in theory, cannot be used in attacks. However, one underlying assumption is that the low-privilege accounts used to control access cannot read secret files, and so forth. The fact is that many systems are not administered very well, and even low-privilege accounts can• walk rightTablethroughof Contentsthe file system and process space. Also note that many approaches to least• privilegeIndexhave exceptions. Take the Microsoft IIS server, for example. If IIS is not
configured properly, user-injected code can execute the RevertToSelf() API call and cause
Exploiting Software How to Break Code
the code to become administrator level again. Furthermore, certain DLLs are always executed
ByGreg Hoglund,Gary McGraw
as administrator, regardless of the user's privilege. The moral of the story here is that if you
audit a target long enough, you are very likely to find a point of entry where least privilege is
Publisher: Addison Wesley
not being applied.
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
Pages: 512
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the script kiddie treatment found in many hacking books, you will learn about
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
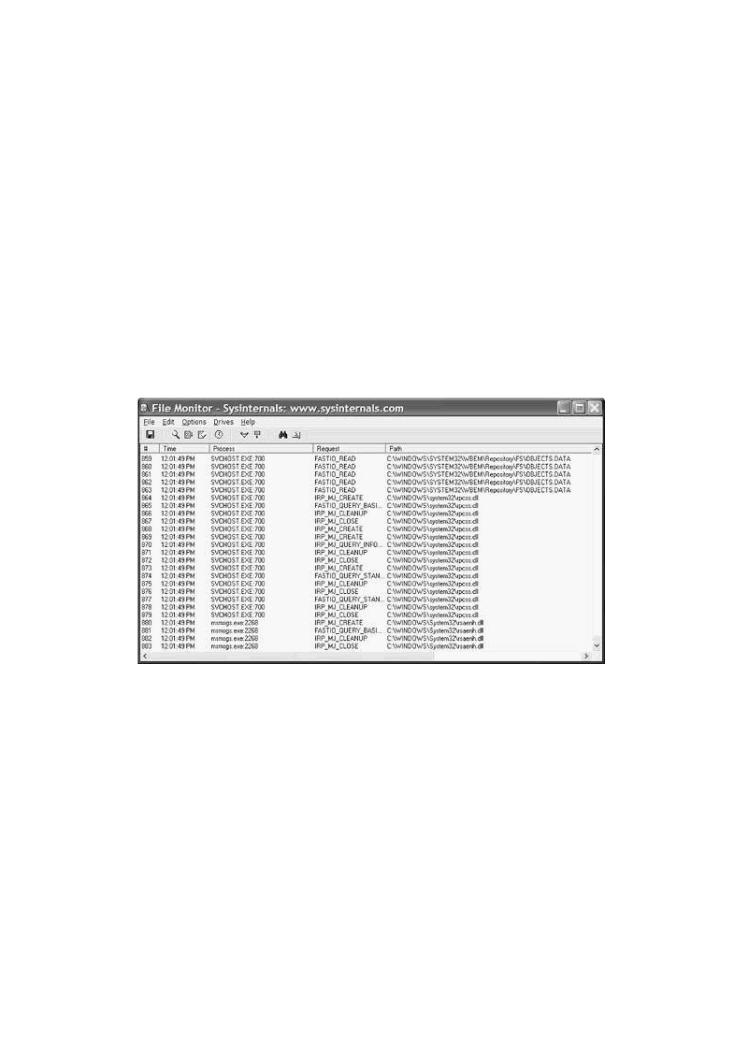
Finding Injection Points
There are several tools that can be used to audit the system for files and other injection points. In the case of Windows NT, the most popular tools for watching the registry or file system are available from http://www.sysinternals.com. The tools called filemon and regmon
• |
Table of Contents |
are good for tracking files and registry keys. These are fairly well-known tools. Other tools |
|
• |
Ind x |
that provide these kinds of data make up a class of programs called API monitors.Figure 4-1
Exploitingshows oneSoftwarepopularHowtool BreakcalledCodefilemon. Monitor programs hook certain API calls and allow you
to see what arguments are being passed. Sometimes these utilities allow the calls to be
ByGr g Hoglund,Gary McGraw
changed on the fly—a primitive form of fault injection.
Publisher: Addison Wesley
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
Figure 4-1. This is a screen shot of filemon, a file system snooping
Pages: 512
tool available at www.sysinternals.com. This program is useful when reverse engineering software to find vulnerabilities.
|
[View full size image] |
How does |
are |
firewalls, |
guys? |
What tools |
|
Exploiting |
and |
techniques |
from |
attack, |
|
This must |
the |
script kiddie |
|
Why |
|
When |
|
Attack |
|
Reverse |
|
 Classic attacks against server software
Classic attacks against server software
Cigital's Failure Simulation Tool (FST) does just this (Figure 4-2). FST interposes itself betweenSurprisingan applicationattacks andgainstthe DLLsclientbysoftwarerewriting the interrupt address table. In this way, the API monitor can see exactly which APIs are being called and which parameters are being
Techniques for crafting malicious input |
[1] |
passed. FST can be used to report interesting sorts of failures to the application under test. |
|
Tools like filemon and FST demonstrate the use of interposition as a critical injection point. |
|
The technical details of buffer overflows |
|
[1] For more on FST, see the publication by Schmid and Ghosh [1999].
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
softwaFiguree. 4-2. Cigital's FST in action. FST uses interposition to simulate
failed system calls.
[View full size image]

•
•
Exploiting
ByGreg
Publisher: Addison Wesley
Pub Date: February 17, 2004
WatchingISBN: 0-201Input-78695Files-8
Pages: 512
Look for files that are used for input. During startup, a program may read from several configuration points including the often-overlooked environment variables. Also look for directory access or file access where a file is not found. A program may look for a configuration file in several locations. If you see a location where the file cannot be found,
this presents an opportunity for attack.
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
techniques used by bad guys to break software. If you want to protect your software from
Attack Pattern: Make Use of Configuration File Search Paths
attack, you must first learn how real attacks are really carried out.
If you place a copy of the configuration file into a previously empty location, the
This must-have book may shock you—and it will certainly educate you.Getting beyond the
target program may find your version first and forgo any further searching. Most script kiddie treatment found in many hacking books, you will learn about
programs are not aware of security, so no check will be made against the owner of the file. The UNIX environment variable for PATH will sometimes specify that a programWhy shouldoftwarelookexploitin multiplewill continuedirectoriesbefora seriousa givenproblemfile. Check these
directories to determine whether you can sneak a Trojan file into the target.  When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
