
- •Exploiting Software How to Break Code
- •Table of Contents
- •Copyright
- •Praise for Exploiting Software
- •Attack Patterns
- •Foreword
- •Preface
- •What This Book Is About
- •How to Use This Book
- •But Isn't This Too Dangerous?
- •Acknowledgments
- •Greg's Acknowledgments
- •Gary's Acknowledgments
- •Bad Software Is Ubiquitous
- •The Trinity of Trouble
- •The Future of Software
- •What Is Software Security?
- •Conclusion
- •Chapter 2. Attack Patterns
- •A Taxonomy
- •An Open-Systems View
- •Tour of an Exploit
- •Attack Patterns: Blueprints for Disaster
- •An Example Exploit: Microsoft's Broken C++ Compiler
- •Applying Attack Patterns
- •Attack Pattern Boxes
- •Conclusion
- •Into the House of Logic
- •Should Reverse Engineering Be Illegal?
- •Reverse Engineering Tools and Concepts
- •Approaches to Reverse Engineering
- •Methods of the Reverser
- •Writing Interactive Disassembler (IDA) Plugins
- •Decompiling and Disassembling Software
- •Decompilation in Practice: Reversing helpctr.exe
- •Automatic, Bulk Auditing for Vulnerabilities
- •Writing Your Own Cracking Tools
- •Building a Basic Code Coverage Tool
- •Conclusion
- •Chapter 4. Exploiting Server Software
- •The Trusted Input Problem
- •The Privilege Escalation Problem
- •Finding Injection Points
- •Input Path Tracing
- •Exploiting Trust through Configuration
- •Specific Techniques and Attacks for Server Software
- •Conclusion
- •Chapter 5. Exploiting Client Software
- •Client-side Programs as Attack Targets
- •In-band Signals
- •Cross-site Scripting (XSS)
- •Client Scripts and Malicious Code
- •Content-Based Attacks
- •Conclusion
- •Chapter 6. Crafting (Malicious) Input
- •The Defender's Dilemma
- •Intrusion Detection (Not)
- •Partition Analysis
- •Tracing Code
- •Reversing Parser Code
- •Misclassification
- •Audit Poisoning
- •Conclusion
- •Chapter 7. Buffer Overflow
- •Buffer Overflow 101
- •Injection Vectors: Input Rides Again
- •Buffer Overflows and Embedded Systems
- •Database Buffer Overflows
- •Buffer Overflows and Java?!
- •Content-Based Buffer Overflow
- •Audit Truncation and Filters with Buffer Overflow
- •Causing Overflow with Environment Variables
- •The Multiple Operation Problem
- •Finding Potential Buffer Overflows
- •Stack Overflow
- •Arithmetic Errors in Memory Management
- •Format String Vulnerabilities
- •Heap Overflows
- •Buffer Overflows and C++
- •Payloads
- •Payloads on RISC Architectures
- •Multiplatform Payloads
- •Prolog/Epilog Code to Protect Functions
- •Conclusion
- •Chapter 8. Rootkits
- •Subversive Programs
- •A Simple Windows XP Kernel Rootkit
- •Call Hooking
- •Trojan Executable Redirection
- •Hiding Files and Directories
- •Patching Binary Code
- •The Hardware Virus
- •Low-Level Disk Access
- •Adding Network Support to a Driver
- •Interrupts
- •Key Logging
- •Advanced Rootkit Topics
- •Conclusion
- •References
- •Index

Decompiling and Disassembling Software
Decompilation is the process of transforming a binary executable—that is, a compiled program—into a higher level symbolic language that is easier for humans to understand. Usually this means turning a program executable into source code in a language like C. Most
• |
Table of Contents |
systems for decompiling can't directly convert programs into 100% source code. Instead, |
|
• |
Index |
they usually provide an "almost there" kind of intermediate representation. Many reverse
ExploitingcompilersSoftwareare actuallyHow todisassemblersBreak Code that provide a dump of the machine code that makes a
program work.
ByGreg Hoglund,Gary McGraw
Probably the best decompiler available to the public is called IDA-Pro. IDA starts with a
Publisher: Addison Wesley
disassembly of program code and then analyzes program flow, variables, and function calls.
Pub Date: February 17, 2004
IDA is hard to use and requires advanced knowledge of program behavior, but its technical
ISBN: 0-201-78695-8
level reflects the true nature of reverse engineering. IDA supplies a complete API for manipulatingPages: 512the program database so that users can perform custom analysis.
Other tools exist as well. A closed-source but free program called REC provides 100% C source code recovery for some kinds of binary executables. Another commercial disassembler is called WDASM. There are several decompilers for Java byte code that render Java source
code (a process far less complicated than decompiling machine code for Intel chips). These How does software break? How do attackers make software break on purpose? Why are
systems tend to be very accurate, even when simple obfuscation techniques have been firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys?
applied. There are open-source projects in this space as well, which interested readers can What tools can be used to break software? This book provides the answers.
look up. It is always a good idea to keep several decompilers in your toolbox if you are
interested in understanding programs.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and
techniques used by bad guys to break software. If you want to protect your software from
Decompilers are used extensively in the computer underground to break copy protection attack, you must first learn how real attacks are really carried out.
schemes. This has given the tools an undeserved black eye. It is interesting to note that
computer hacking and software piracy were largely independent in the early days of the This must-have book may shock you—and it will certainly educate you.Getting beyond the
computer underground. Hacking developed in UNIX environments, where software was free script kiddie treatment found in many hacking books, you will learn about
and source code was available, rendering decompiling somewhat unnecessary. Software
piracy, on the other hand, was mainly developed to crack computer games, and hence was
confinedWhymainlysoftwareto Apexples,oit willDOS,continueand Windows,to be a forseriouswhichproblemsource code was usually not
available. The virus industry developed along side the piracy movement. In the late 1990s,
When netwocrackingsecurity mechanisms do not work
the hacking and disciplines merged as more network software became available for
Windows and hackers learned how to break Windows software. The current focus of
Attack patterns
decompiling is shifting from cracking copy protection to auditing software for exploitable
bugs. The same old tricks are being used again, but in a new environment.  Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
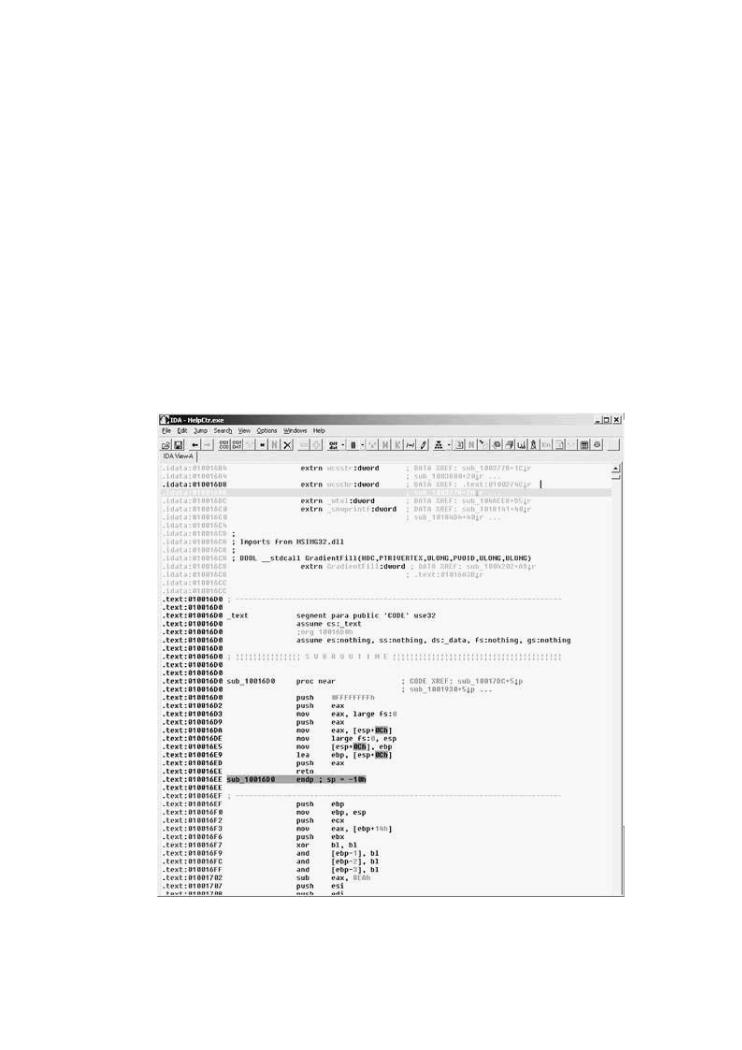
Decompilation in Practice: Reversing helpctr.exe
The following example illustrates a reverse engineering session against helpctr.exe, a Microso program provided with the Windows XP OS. The program happens to have a security vulnerabil known as a buffer overflow. This particular vulnerability was made public quite some time ago,
• |
Table of Contents |
revealing it here does not pose a real security threat. What is important for our purposes is |
|
• |
Index |
describing the process of revealing the fault through reverse engineering. We use IDA-Pro to
ExploitingdisassembleSoftwarethe targetHow to softwareBreak Code. The target program produces a special debug file called a Dr.
Watson log. We use only IDA and the information in the debug log to locate the exact coding er
ByGreg Hoglund,Gary McGraw
that caused the problem. Note that no source code is publicly available for the target software.
Figure 3-4 shows IDA in action.
Publisher: Addison Wesley
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
Pages: 512
Figure 3-4. A screen shot of IDA-Pro reverse assembling the progra helpctr.exe, which is included as part of the Microsoft Windows XP OS. an exercise, we explore helpctr.exe for a buffer overflow vulnerability
How does software break? How do attackers make software break on purpose? Why are
[View full size image]
firewalls, |
guys? |
What tools
Exploiting techniques attack, you
This must- |
the |
script kiddie |
|
Why |
|
When |
|
Attack |
|
Reverse |
|
Classic |
|
Surprising |
|
Techniques |
|
The |
|
Rootkits |
|
Exploiting |
|
software. |
|
Bug Report

We learned of this vulnerability just like most people did, by reading a bug report posted to bugtraq, an industry mailing list forum where software problems and security issues are discuss The report revealed only minor details about the problem. Most notably, the name of the executable and the input that caused the fault. The report revealed that the URL hcp://w.w.w.w.w.w.w.w.w.w.w.w.w.w.w.w.w.w.w.w.w.w.w.w.w.w.w.w., when supplied to Inte Explorer, caused helpctr.exe to launch. The URL does this by causing an application exception (which can be tickled remotely through a Web browser).
•Table of Contents
We recreate the fault by using the URL as input in a Windows XP environment. A debug log is
• Index
created by the OS and we then copy the debug log and the helpctr.exe binary to a separate
Exploiting Software How to Break Code
machine for analysis. Note that we used an older Windows NT machine to perform the analysis BythisGregbugHoglund. The,originalGary McGrawXP environment is no longer required once we induce the error and gathe data we need.
Publisher: Addison Wesley
Pub Date: February 17, 2004
The DebugISBN: 0-201Log-78695-8
Pages: 512
A debug dump is created when the program crashes. A stack trace is included in this log, giving a hint regarding the location of the faulty code:
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
0006f8ac 0100b4ab 0006f8d8 00120000 00000103 msvcrt!wcsncat+0x1e
This must-have book may shock you—and it will certainly educate you.Getting beyond the script0006fae4kiddie0050004ftreatment00120000found in many00279b64hacking00279b44books, youHelpCtr+0xb4abwill learn about
0054004b 00000000 00000000 00000000 00000000 0x50004f
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
The culprit appears to be string concatenation function called wcsncat. The stack dump clearly
shows our (fairly straightforward) URL string. We can see that the URL string dominates the sta Reverse engineering
space and thereby overflows other values:
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.

*---- |
> Raw Stack Dump <---- |
* |
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
000000000006f8a8 03 |
01 |
00 00 |
e4 |
fa 06 |
00 |
- ab b4 |
00 |
01 |
d8 |
f8 |
06 |
00 |
............ |
|||||
000000000006f8b8 00 |
00 |
12 |
00 |
03 |
01 |
00 |
00 |
- |
d8 |
f8 |
06 |
00 |
a8 |
22 |
03 |
01 |
............ |
|
• |
Table of Contents |
00 |
00 |
b4 |
20 |
03 |
01 |
- |
cc |
9b |
27 |
00 |
c1 |
3e |
c4 |
77 |
..... ....'. |
|
000000000006f8c8 f9 |
00 |
|||||||||||||||||
•Index
Exploiting000000000006f8d8Software How43to Break00 3aCode00 5c 00 57 00 - 49 00 4e 00 44 00 4f 00 C.:.\.W.I.N.
ByGreg Hoglund,Gary McGraw
000000000006f8e8 57 00 53 00 5c 00 50 00 - 43 00 48 00 65 00 61 00 W.S.\.P.C.H.
Publisher: Addison Wesley
000000000006f8f8 6c 00 74 00 68 00 5c 00 - 48 00 65 00 6c 00 70 00 l.t.h.\.H.e.
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
000000000006f908 43 00 74 00 72 00 5c 00 - 56 00 65 00 6e 00 64 00 C.t.r.\.V.e.
Pages: 512
000000000006f918 6f 00 72 00 73 00 5c 00 - 77 00 2e 00 77 00 2e 00 o.r.s.\.w...
000000000006f928 77 00 2e 00 77 00 2e 00 - 77 00 2e 00 77 00 2e 00 w...w...w...
000000000006f938 77 00 2e 00 77 00 2e 00 - 77 00 2e 00 77 00 2e 00 w...w...w...
How does software break? How do attackers make software break on purpose? Why are
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys?
000000000006f948 77 00 2e 00 77 00 2e 00 - 77 00 2e 00 77 00 2e 00 w...w...w...
What tools can be used to break software? This book provides the answers.
000000000006f958Exploiting So tware77is 00loaded2e 00with77examples00 2e 00of real- 77attacks,00 2e attack00 77 patterns,00 2e 00tools,w...andw...w...
techniques used by bad guys to break software. If you want to protect your software from
000000000006f968attack, you must first77learn00 2ehow00real77attacks00 2e are00 really- 77 carried00 2e out00 .77 00 2e 00 w...w...w...
This000000000006f978must-have book77may00shock2e 00you77—and00 2eit will00 certainly- 77 00 educate2e 00 77you00.Getting2e 00beyondw...w...thew...
script kiddie treatment found in many hacking books, you will learn about
000000000006f988 77 00 2e 00 77 00 2e 00 - 77 00 2e 00 77 00 2e 00 w...w...w...
Why software exploit will continue to be a serious problem
000000000006f998 77 00 2e 00 77 00 2e 00 - 77 00 2e 00 77 00 2e 00 w...w...w...
 When network security mechanisms do not work
When network security mechanisms do not work
000000000006f9a8 77 00 2e 00 77 00 2e 00 - 77 00 2e 00 77 00 2e 00 w...w...w...
 Attack patterns
Attack patterns
000000000006f9b8 77 00 2e 00 77 00 2e 00 - 77 00 2e 00 77 00 2e 00 w...w...w...
 Reverse engineering
Reverse engineering
000000000006f9c8 77 00 2e 00 77 00 2e 00 - 77 00 2e 00 77 00 2e 00 w...w...w...
 Classic attacks against server software
Classic attacks against server software
000000000006f9d8 77 00 2e 00 77 00 2e 00 - 77 00 2e 00 77 00 2e 00 w...w...w...
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
The technical details of buffer overflows
Knowing that wcsncat is the likely culprit, we press onward with our analysis. Using IDA, we ca
see that wcsncat is called from two locations:  Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
.idata:01001004 |
extrn wcsncat:dword |
; DATA XREF: sub_100B425+62 1/3r |
.idata:01001004 |
; sub_100B425+771/3r ... |
The behavior of wcsncat is straightforward and can be obtained from a manual. The call takes
three parameters:
•Table of Contents
•1. A destinationIndex buffer (a buffer pointer)
Exploiting Software How to Break Code
2. A source string (user supplied)
ByGreg Hoglund,Gary McGraw
3. A maximum number of characters to append
Publisher: Addison Wesley
ThePubdestinationDate: Februarybuffer17, 2004is supposed to be large enough to store all the data being appended. (Bu
note that in this case the data are supplied by an outside user, who might be malicious.) This is
ISBN: 0-201-78695-8
why the last argument lets the programmer specify the maximum length to append. Think of th
Pages: 512
buffer as a glass of a particular size, and the subroutine we're calling as a method for adding liq to the glass. The last argument is supposed to guarantee that the glass does not overflow.
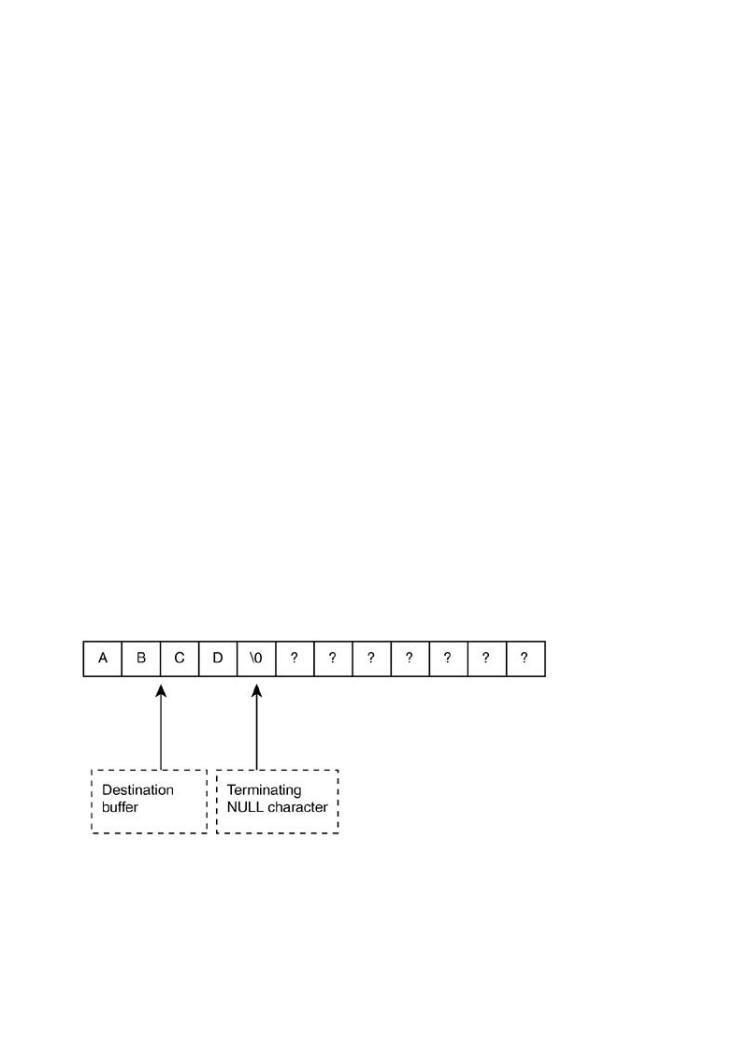
Inhelpctr.exe, a series of calls are made to wcsncat from within the broken subroutine. The following diagram illustrates the behavior of multiple calls to wcsncat. Assume the destination
How does software break? How do attackers make software break on purpose? Why are
buffer is 12 characters long and we have already inserted the string ABCD. This leaves total of
firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? eight remaining characters including the terminating NULL character.
What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the script kiddie treatment found in many hacking books, you will learn about
wcsncat(target_buffer, "ABCD", 11);
Why software exploit will continue to be a serious problem
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
to break
software.
We now make a call to wcsncat() and append the string EF. As the following diagram illustrate the string is appended to the destination buffer starting at the NULL character. To protect the destination buffer, we must specify that a maximum of seven characters are to be appended. If terminating NULL character is included, this makes a total of eight. Any more input will write of end of our buffer and we will have a buffer overflow.
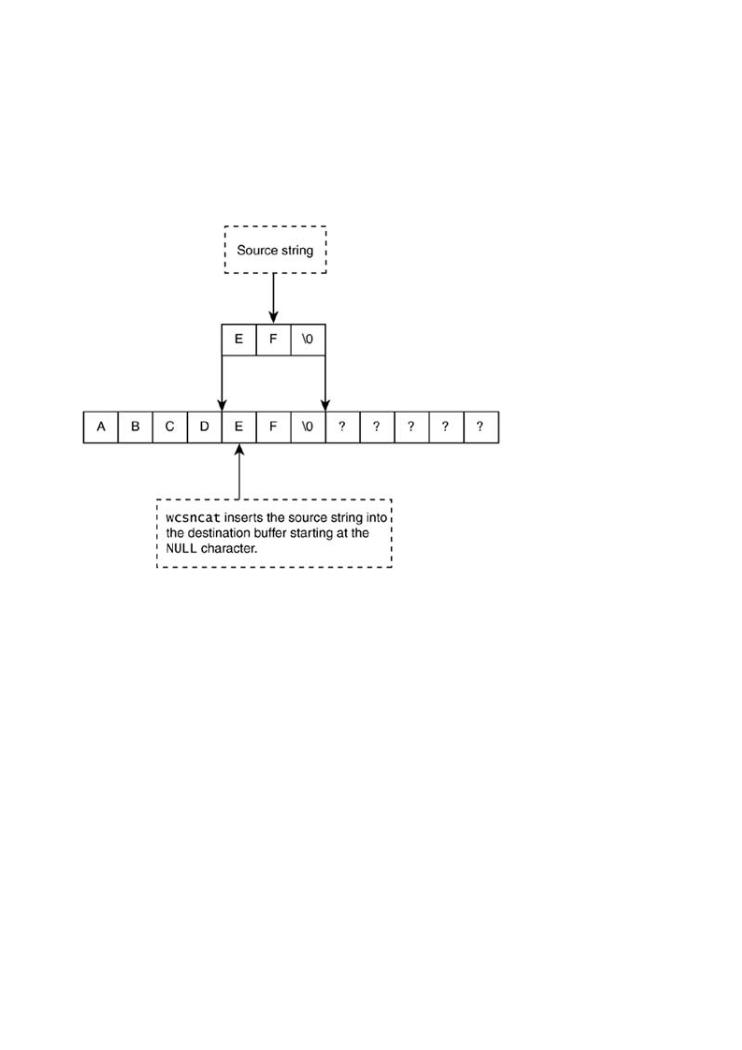
wcsncat(target_buffer, "EF", 7);
•Table of Contents
•Index
Exploiting Software How to Break Code
purpose? Why are keeping out the bad guys? answers.
patterns, tools, and your software from
you.Getting beyond the about
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
Unfortunately, in the faulty subroutine within helpctr.exe, the programmer made a subtle but fatal mistakeWhennetwork.Multiples curitycallsaremechanismsmade to wscncat()do not workbut the maximum-length value is never
recalculated. In other words, the multiple appends never account for the ever-shrinking space
Attack patterns
remaining at the end of the destination buffer. The glass is getting full, but nobody is watching
more liquid is poured in. In our illustration, this would be something like appending EFGHIJKLM
Reverse engineering
our example buffer, using the maximum length of 11 characters (12 including the NULL). The
correct value should be a maximum of seven characters, but we never correct for this and we
 Classic attacks against server software append past the end of our buffer.
Classic attacks against server software append past the end of our buffer.
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
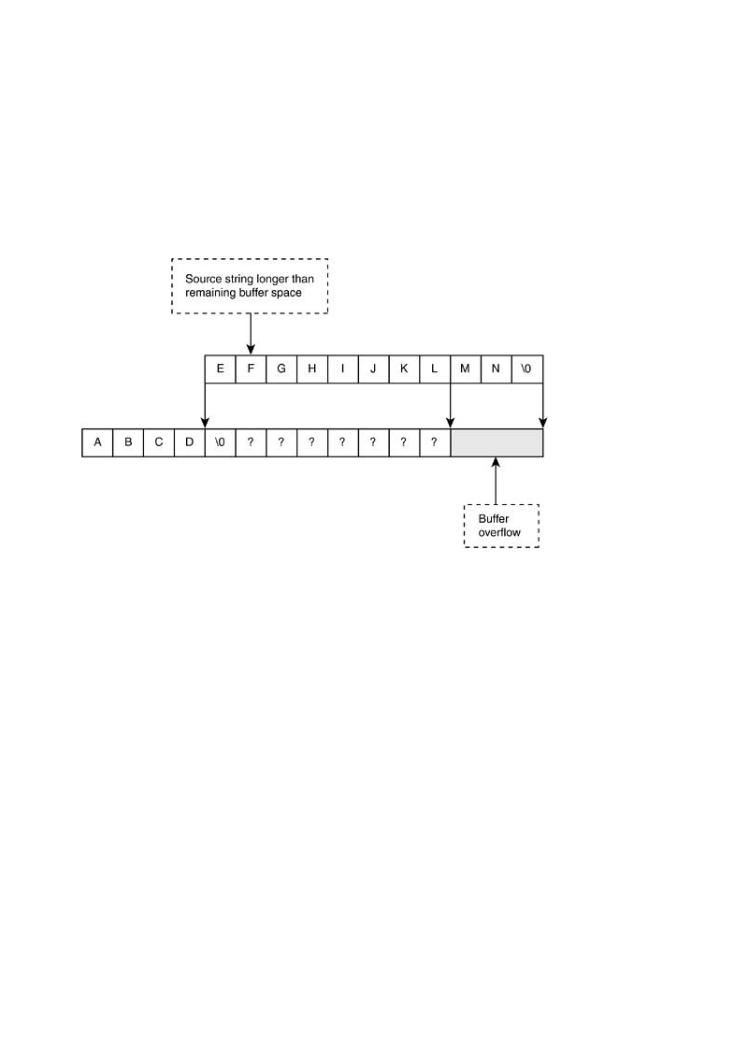
wcsncat(target• Table_ofbuffer,Cont nts "EFGHIJKLMN", 11);
•Index
Exploiting Software How to Break Code
ByGreg Hoglund,Gary McGraw
Why are
out the bad guys?
tools, and
software from
beyond the
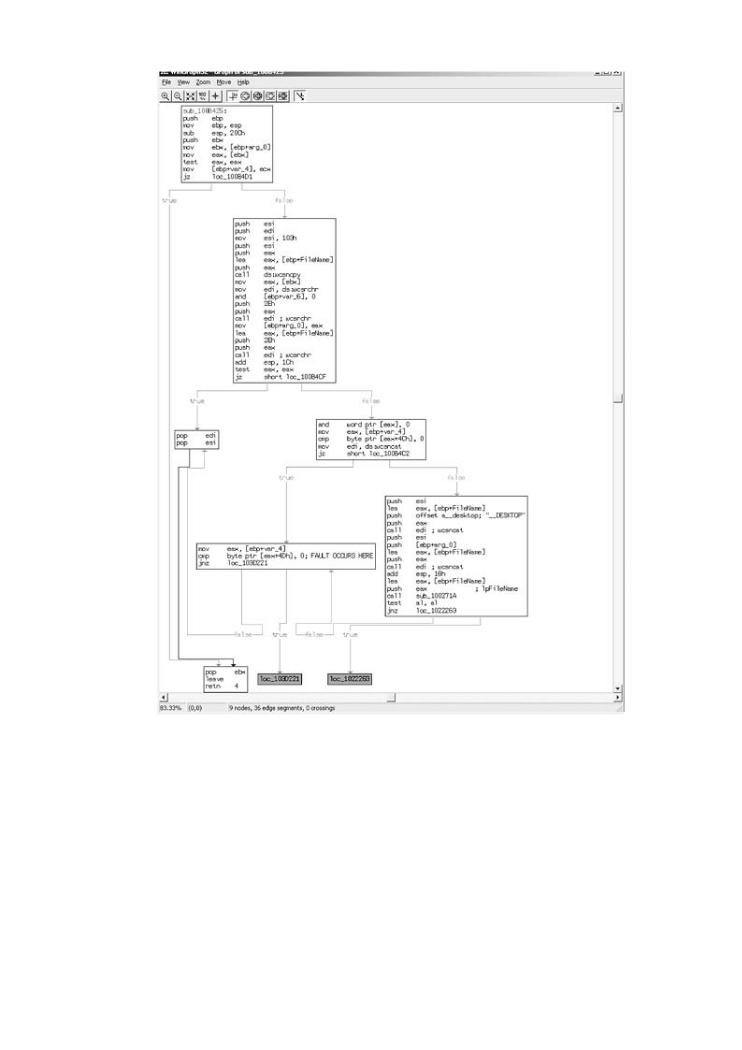
A graph of the subroutine in helpctr.exe that makes these calls is shown in Figure 3-5.  Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
 When network security mechanisms do not work
When network security mechanisms do not work
Figure 3-5. A simple graph of the subroutine in helpctr.exe that make
Attack patterns
calls to wcsncat().
 Reverse engineering
Reverse engineering
Classic attacks against server software
[View full size image]
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break software.
•
•
Exploiting
ByGreg Hoglund
Publisher:
Pub Date:
ISBN: 0
Pages:
How does
firewalls, |
guys? |
What tools
Exploiting techniques attack, you
This must- |
the |
script kiddie |
|
Why |
|
When |
|
Attack |
|
Reverse |
|
Classic |
|
Surprising attacks against client software |
|
 Techniques for crafting malicious input
Techniques for crafting malicious input
A very good reverse engineer can spot and decode the logic that causes this problem in 10 to 1
minutes. An average reverse engineer might be able to reverse the routine in about an hour. Th
The technical details of buffer overflows
subroutine starts out by checking that it has not been passed a NULL buffer. This is the first JZ
branch. If the buffer is valid, we can see that 103h is being set in a register. This is 259 Rootkits
decimal—meaning we have a maximum buffer size of 259 characters.[13] And herein lies the bu
We see that this value is never updated during successive calls to wcsncat. Strings of character Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
softwareappended. to the target buffer multiple times, but the maximum allowable length is never appropriately reduced. This type of bug is very typical of parsing problems often found in code. Parsing typically includes lexical and syntax analysis of user-supplied strings, but it unfortunate often fails to maintain proper buffer arithmetic.
[13] The actual buffer size is double (518 bytes), because we are working with wide characters. This is not
important to the current discussion, however.
What is the final conclusion here? A user-supplied variable—in the URL used to spawn helpctr.exe—is passed down to this subroutine, which subsequently uses the data in a buggy

series of calls for string concatenation.
Alas, yet another security problem in the world caused by sloppy code. We leave an exploit resulting in machine compromise as an exercise for you to undertake.
•Table of Contents
•Index
Exploiting Software How to Break Code
ByGreg Hoglund,Gary McGraw
Publisher: Addison Wesley
Pub Date: February 17, 2004
ISBN: 0-201-78695-8
Pages: 512
How does software break? How do attackers make software break on purpose? Why are firewalls, intrusion detection systems, and antivirus software not keeping out the bad guys? What tools can be used to break software? This book provides the answers.
Exploiting Softwareis loaded with examples of real attacks, attack patterns, tools, and techniques used by bad guys to break software. If you want to protect your software from attack, you must first learn how real attacks are really carried out.
This must-have book may shock you—and it will certainly educate you.Getting beyond the script kiddie treatment found in many hacking books, you will learn about
 Why software exploit will continue to be a serious problem
Why software exploit will continue to be a serious problem
 When network security mechanisms do not work
When network security mechanisms do not work
 Attack patterns
Attack patterns
 Reverse engineering
Reverse engineering
 Classic attacks against server software
Classic attacks against server software
 Surprising attacks against client software
Surprising attacks against client software
 Techniques for crafting malicious input
Techniques for crafting malicious input
 The technical details of buffer overflows
The technical details of buffer overflows
 Rootkits
Rootkits
Exploiting Softwareis filled with the tools, concepts, and knowledge necessary to break
software.
